BumbleBee malware campaign targeting Mexico
Overview
BumbleBee is a complex malware used as a dropper/loader by various threat actors, mainly ransomware operators, with which some cybercriminals distribute Cobalt Strike beacons, the “Sliver” tool used for Red Team exercises, to deliver Metasploit/Meterpreter shellcodes, as well as the BlackGuard, IcedID and RedLine Stealer trojans.
BumbleBee is distributed via phishing emails, impersonating service companies or using the email services of previously compromised organizations. SCILabs identified this malware campaign the last week of June in Mexico.
In the identified campaign, the email used to distribute the threat indicates that a purchase order has been generated in the name of the victim and to obtain more details, the attached file must be opened with the password specified in the email. It is important to mention that the level of detection of the malware by commercial security solutions is medium, according to some public samples uploaded by third parties to VirusTotal.
How could it affect an organization?
The main objective of this campaign is to function as a dropper, then collect information from the infected device, send it to the command-and-control server, and then download additional malicious code, all through a complex evasion mechanism to evade malware analysis environments and sandbox-type tools.
If the attack is successful, the confidentiality, integrity and availability of organizations’ information could be affected. Additionally, according to public research, this malware is mainly used as an initial entry vector in ransomware attacks such as CONTI, LockBit, Diavol and AvosLocker. Therefore, if the entire attack cycle is completed, the impact on the victim’s operability can be high.
Analysis
Threat Context
During SCILabs’ threat monitoring in the region, we observed a suspicious email with an attachment, which was a supposedly a purchase order for an Oracle contract renewal, sent from an email account of the victim organization itself.
It is hypothesized that this account was previously compromised and that messages are being sent from it to other members of the organization, because when analyzing the email headers, we only found activity from SMTP users of the organization itself.
The analyzed email contains an attachment named 06-02-2022_34.zip, protected with a password, and inside is an ISO file with the same name.
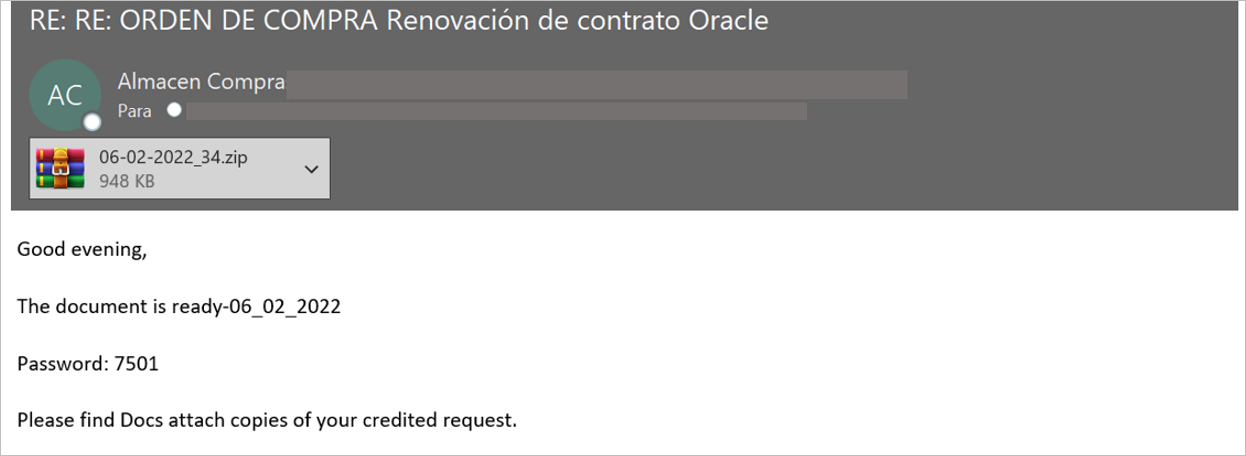
Figure 1 – Email used to distribute BumbleBee
Technical Summary
06-02-2022_34.iso
The ISO file contained within the zip file attached to the email contains two files called documents.lnk and taxep.dll, the latter with the “hidden” attribute. The ISO file does not have auto-execution methods or functions, so the user must mount the file on the device and double-click on the document’s shortcut icon for the device to be compromised.
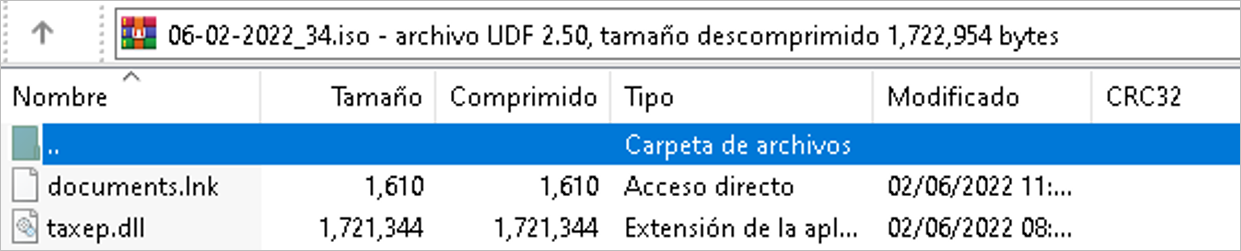
Figure 2 – ISO file content
documents.lnk
The direct access file uses the rundll32.exe tool to execute the DLL embedded in the ISO file. When the user clicks on the file, it will execute the main function of the malicious artifact and start the infection flow.
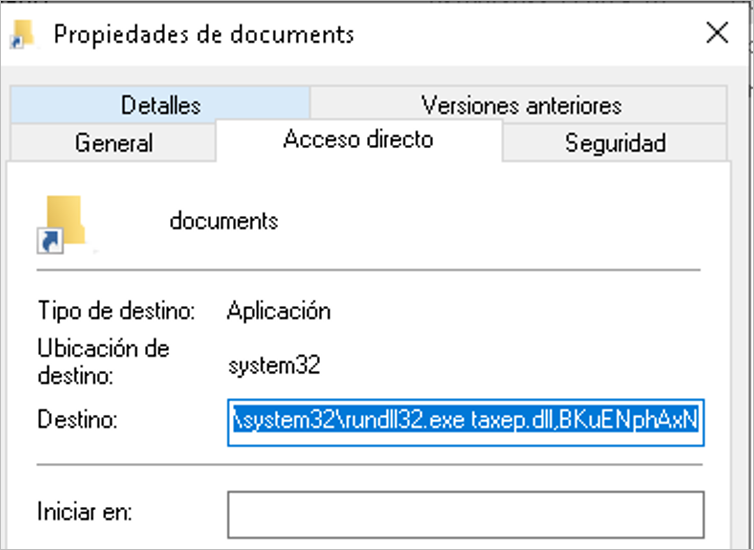
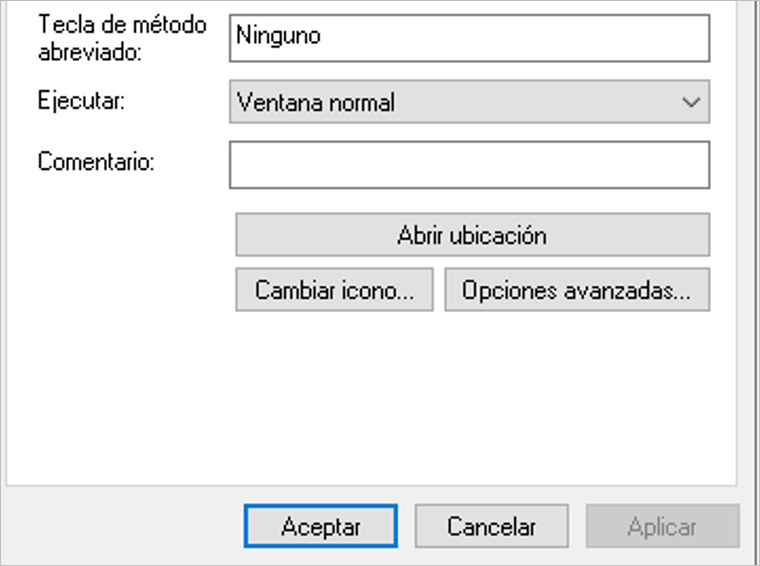
Figure 3 – DLL execution syntax
taxep.dll
When performing a static analysis of the artifact, it was observed that it has a function called BKuENphAxN, responsible for unpacking the malicious code in memory, triggering the environment verification and computer infection process.
![]()
Figure 4 – Main function of the artifact
Additionally, in the resource section of the artifact, no malicious elements, or the use of external resources for its execution were observed. SCILabs also found that the artifact is developed in C++ for 64-bit architectures and was compiled in early June this year, suggesting that it is a new version of the BumbleBee malware.
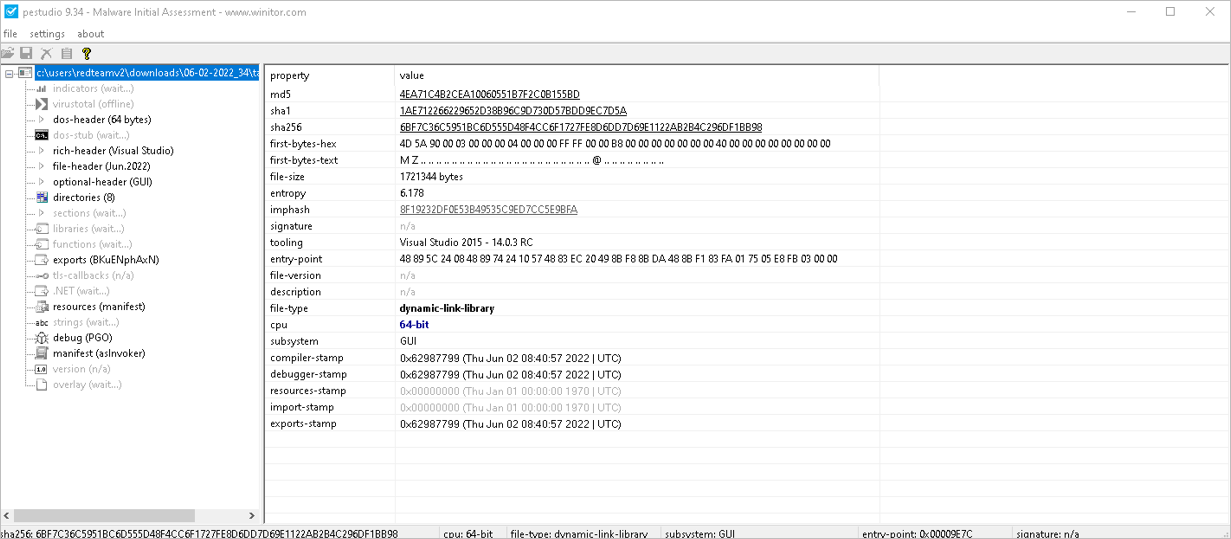
Figure 5 – Structure of the DLL file
On execution, the artifact begins by performing a series of complex anti-scanning checks in which it examines the execution environment for virtual machines or sandboxes, tools commonly used to perform malware analysis and connection monitoring software. The artifact terminates its execution if it identifies any of these processes on the victim’s machine.
In addition, the malware checks via the WMI utility, the username, domain name, operating system information, network adapter details and available hardware on the device. The collected information is shared with the command-and-control sites of the malware’s operators. Finally, it checks that the victim’s username does not match the list defined in the code, if the username matches, the execution will be stopped.
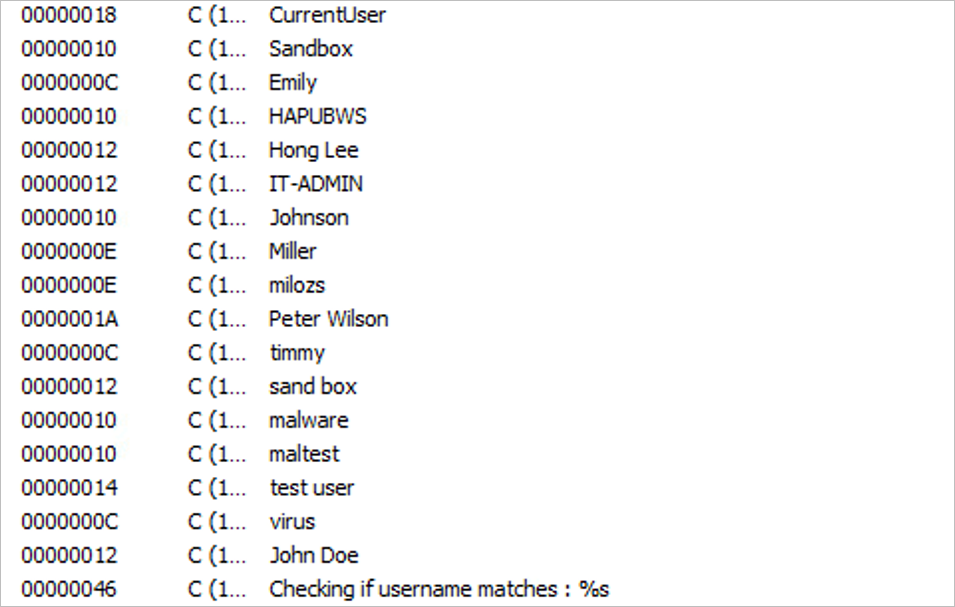
Figure 6 – Blacklist of users
BumbleBee Capabilities
Bumblebee uses multiple commands to carry out its malicious activities. Those observed in the malware analysis are listed below:
- dij/shi command (DLL and shellcode injection)
If the malware receives the “dij” or “shi” command, it will perform a memory injection of the DLL artifact or shellcode, both sent from the command-and-control site and encoded in base64. Additionally, malware can be embedded in some of the following legitimate operating system applications:
C:\Program Files (x86)\Windows Photo Viewer\ImagingDevices.exe
C:\Program Files (x86)\Windows Mail\wab.exe
C:\Program Files (x86)\Windows Mail\wabmig.exe
It is important to mention that unlike most other malware, which uses process flushing or DLL injection, this loader uses the asynchronous procedure call (APC) injection to launch the shellcode.
- dex command (additional malicious code download)
When the malware receives the “dex” command, it downloads and executes additional payloads. The generated file will be named wab.exe and stored in the %APPDATA% folder.
To generate the artifact, the malware uses the CreateFileA() and WriteFile() functions, which are executed through the COM object.
- ins command (malware persistence)
If the malware receives the “ins” command, it will enable persistence by copying the malware DLL to the %APPDATA%/{UNIQUE_IDENTIFIER}/{RANDOM_NAME_FOLDER} directory and generate a VBS script that will load the malicious DLL via a scheduled task with a named random up to 7 characters.
- sdl command (malware uninstall)
The “sdl” command uses PowerShell to remove files from the infected system without needing victim interaction.
Communication with the Command-and-Control server
The choice of the command-and-control server used by the malware is dynamic. First, the loader chooses an IP address from the list defined in the malware code and sends a request via HTTPS using the GET method. The request includes the following information in JSON format (encrypted with the RC4 algorithm):
| Identifier | Identifier Description |
| client_id | Contains the Universally Unique Identifier (UUID) of the victim’s device in MD5 format |
| group_name | The key contains an encoded value, which represents the group to which the bot will be
added (compromised host) |
| sys_version | Contains the version of the victim’s operating system |
| client_version | The default value is set to 1 (possibly the malware version) |
| user_name | Victim’s username |
| domain_name | Domain to which the victim is associated |
| task_state | The value is set to 0 by default. The value is changed only when the ‘ins’ or ‘sdl’ commands
are executed. |
| task_id | The value is set to 0 by default. The value is changed only when the ‘ins’ or ‘sdl’ commands
are executed. |
Once the server receives the request, it responds with the following data in JSON format:
| Identifier | Identifier Description |
| response_status | Is Boolean value used to validate that the server successfully parsed the malware request.
In case of being successful, the command-and-control server will return the value 1 |
| tasks | An array containing a list of tasks |
| task | Name under which the task will be registered if persistence is set |
| task_id | ID of the received task (the malware operators will establish the value) |
| task_data | Data used for malware to execute. The information is encoded in Base64 |
| file_entry_point | We did not obtain more information related to this value |
In the artifact analysis, no additional malware download was observed, however, this could be due to a momentary interruption of the Command-and-Control servers.
TTPs observed aligned to MITRE’s ATT&CK framework
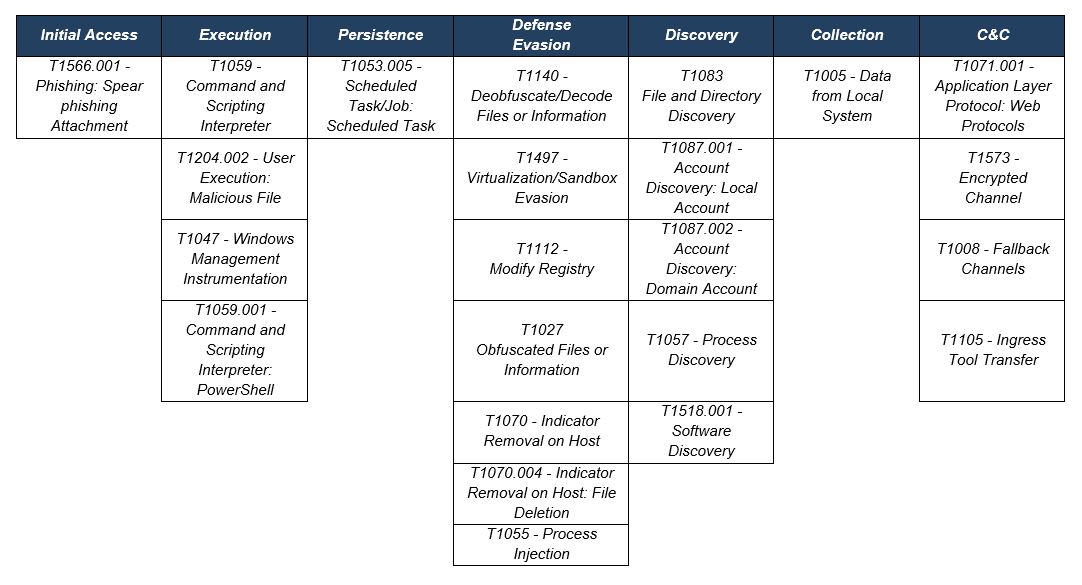
Table 1 – TTPs observed aligned to MITRE’s ATT&CK framework
Attack Flow

Figure 7 – BumbleBee infection flow
Assessment
BumbleBee is a malware that has been active since February 2022 and several modifications have been made to its code, including complex anti-analysis techniques and high obfuscation in its functions. The cybercriminals have also constantly modified the sites where they store their artifacts, to evade victims’ anti-spam filters; some of the services used by the attackers are TransferXL, TransferNow, WeTransfer and OneDrive.
According to the research conducted by SCILabs, depending on the type of cybercriminal distributing the malware, BumbleBee may download other types of malicious tools such as Cobalt Strike, Meterpreter, or another trojan to control the infected device remotely.
Based on multiple publications, in most of the attacks in which BumbleBee has been detected, the goal was to implant ransomware from different families such as CONTI, LockBit, Diavol or AvosLocker; therefore, it is important to detect this malware in its early stages, to avoid a major impact. SCILabs recommends using YARA rule-based detection, as some functions used by the malware remain the same since its first versions.
Finally, due to its complexity, constant updating and the similarities observed with other malicious code, BumbleBee is a malware with similar capabilities to Trickbot or BazarLoader, two multifunctional tools widely used by cybercriminals in Latin America to effectively deploy malware. SCILabs believes that this malware will be active for several months to come, infecting many devices.
IOC
328B54CC32BD231BA1960EECAF9BE1B5
7CA9DDFFAC63FC8F8AB4210230D1225A
6F9725B0842ED9D13BB8F7C64160E7AC
4EA71C4B2CEA10060551B7F2C0B155BD
367B6B238775DB64F5DB5A0D8FAF0D0F
96311317EB4A91F0919637A0FF9D8798
F04B1B5C47B7AA791006E106BA0256AE
185[.]156[.]172[.]123
64[.]44[.]101[.]250
103[.]175[.]16[.]121
146[.]19[.]173[.]224
145[.]239[.]30[.]26
194[.]37[.]97[.]135
103[.]175[.]16[.]117
37[.]120[.]198[.]248
146[.]19[.]173[.]139
185[.]62[.]56[.]201
192[.]236[.]161[.]191
192[.]236[.]249[.]68
193[.]239[.]84[.]247
154[.]56[.]0[.]221
192[.]236[.]192[.]85
193[.]239[.]84[.]254
192[.]236[.]194[.]136
192[.]119[.]64[.]21
64[.]44[.]102[.]6
103[.]175[.]16[.]107
64[.]44[.]135[.]250
103[.]175[.]16[.]59
54[.]38[.]136[.]187
176[.]107[.]177[.]124
192[.]236[.]160[.]254
68[.]233[.]238[.]105
198[.]98[.]57[.]91
63[.]141[.]248[.]253
79[.]110[.]52[.]56
185[.]62[.]58[.]238
180[.]23[.]251[.]29
194[.]135[.]33[.]16
115[.]239[.]67[.]202
53[.]96[.]32[.]99
141[.]98[.]168[.]70
58[.]10[.]55[.]201
103[.]175[.]16[.]107
18[.]215[.]29[.]142
174[.]150[.]214[.]40
102[.]109[.]16[.]255
162[.]144[.]249[.]150
210[.]251[.]188[.]194
112[.]110[.]146[.]153
83[.]142[.]26[.]147
35[.]17[.]203[.]69
31[.]215[.]170[.]180
146[.]70[.]124[.]77
79[.]133[.]212[.]60
192[.]21[.]12[.]118
133[.]133[.]249[.]24
165[.]158[.]204[.]41
137[.]253[.]55[.]69
140[.]208[.]107[.]161
115[.]103[.]22[.]1
213[.]203[.]201[.]199
154[.]56[.]0[.]100
108[.]28[.]254[.]44
28[.]78[.]74[.]145
119[.]177[.]224[.]146
180[.]184[.]129[.]160
70[.]77[.]209[.]88
126[.]68[.]7[.]249
65[.]95[.]20[.]151
144[.]52[.]138[.]51
149[.]57[.]112[.]159
65[.]254[.]82[.]66
57[.]156[.]134[.]113
143[.]117[.]20[.]123
TAXEP.DLL
DOCUMENTS.LNK
UPLAM.DLL
%APPDATA%/{UNIQUE_IDENTIFIER}/{RANDOM_NAME_FOLDER}
%APPDATA%/WAB.EXE
