Threat actor activity using remote administration tools
This report provides information about a new technique used by threat actors, leveraging legitimate remote administration tools to infect computers with malware.
During the last months, SCILabs observed that some threat actors, mainly ransomware operators, have used legitimate remote administration tools for taking full control over infected computers, obtaining persistence, and distributing malware. This also allows them to continue with the next steps of their attacks, such as performing lateral movement and information exfiltration.
Between late 2024 and early 2025, research conducted by SCILabs indicates a rise in the use of remote administration tools (RATs) for malware distribution. This trend is largely driven by the ease with which these tools allow attackers to remotely access and control systems, enabling the deployment of malicious software and the exfiltration of sensitive information.
According to SCILabs research, some of the tools that have been used by threat actors are: Atera Agent, Splashtop, PDQ Connect, N-able Take Control, and ScreenConnect. Although SCILabs does not rule out the use of other similar tools.
The most relevant challenge for organizations facing this threat is that this type of software is legitimate, so controlling and keeping a record of authorized applications tends to be difficult. Therefore, threat actors exploit this feature to abuse these legit tools.
The campaigns analyzed by SCILabs have targeted all kinds of users, behaving more like opportunistic attacks targeting random victims. Very similar to how infostealer families or RAT operate.
The following section provides an analysis of the TTPs used by threat actors in campaigns where these tools are deployed.
Analysis
General context
SCILabs identified that, so far in 2025, there has been an increase in the use of remote administration tools in LATAM to carry out malicious activities. For example, infecting computers with banking trojans such as Mekotio; however, malicious actors can distribute other types of threats such as ransomware, since there are reports in open sources indicating that this is one of the vectors used by variants like LockBit, BlackCat or RansomHub, among others.
Technical overview
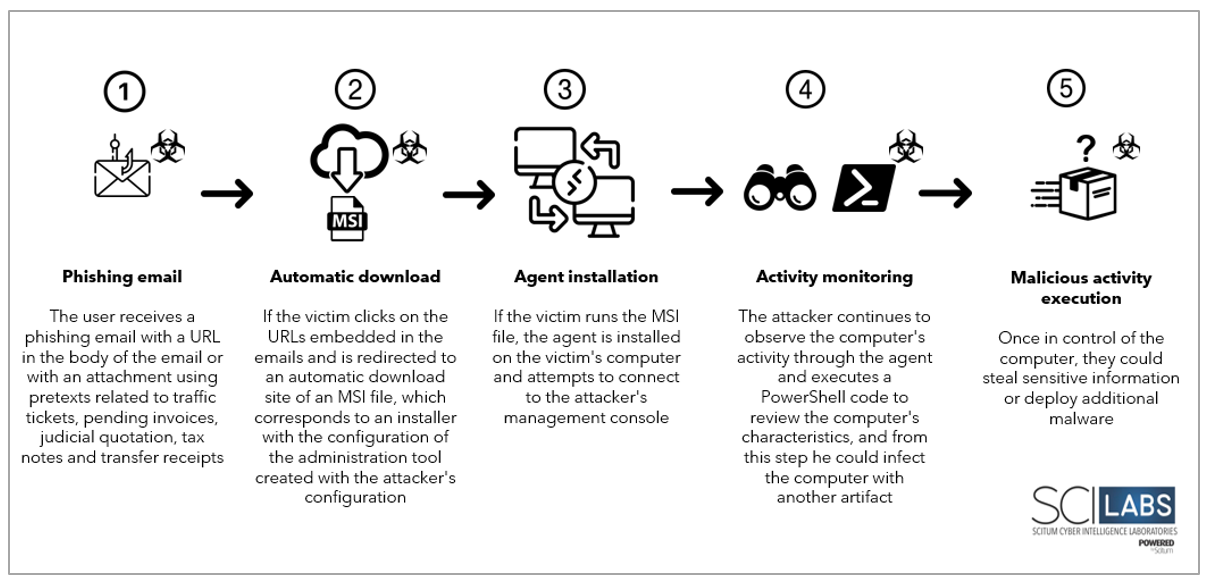
In November 2024, SCILabs identified in open sources a possible campaign targeting Peru using the PDQ Connect tool to distribute Mekotio.
Since then, SCILabs began to see an increased tendency in the distribution of this remote administration tool. However, it wasn’t until January 2025 that SCILabs detected a new campaign with at least four email samples directed to Argentina and Chile associated with traffic tickets and pending invoices, where the PDQ Connect agent was downloaded from these emails. As a result, SCILabs obtained the Mekotio variant used in the campaign, confirming what has been observed in open sources.
In addition, analyzed another campaign in March of this year, which targeted users in Brazil under the pretext of a judicial quotation. Although, in this case, the installation of the Atera Agent was observed, which only has administration capabilities through commands; unlike PDQ Connect or ScreenConnect, which allow access to the victim’s remote desktop. Once the agent enables interaction between the operators and the compromised device, the attackers remotely execute PowerShell code to install Splashtop, thereby gaining remote desktop access to the system; possibly to take control of the victim’s screen. During this analysis, the attacker did not deploy any other malware.
Another campaign under investigation was identified and analyzed by SCILabs in the first week of April this year. This campaign was targeted to Brazil, using the pretext of a pending tax note. In this case, an agent called N-able Take Control is downloaded and installed. With this, the attacker can obtain information about the device, such as the processor, components, and installed tools, and thus determine whether it can be infected with other malware. No additional phase was observed in this campaign either, which allows for the hypothesis, with medium confidence, that the attacker is trying to identify information that will help them decide whether to proceed with infecting the device or simply monitor it.
The most recent campaign observed by SCILabs, in the third week of April, targeted Mexico, posing as a wire transfer receipt, which installed a ScreenConnect agent. As in previous cases, this campaign did not deploy any other payloads and only constantly monitored the device. However, this campaign is still operating at the time of writing this report, so a future connection to another threat cannot be ruled out. Based on the analysis, there is high confidence that the attackers are using legitimate remote administration tools to obtain confidential information, monitor device activity, and deploy additional malware, thereby evading traditional security measures and providing a method for future malware deployment.
Based on the analysis, there is high confidence that the attackers are using legitimate remote administration tools to obtain confidential information, monitor device activity, and deploy additional malware, thereby evading traditional security measures and providing a method for future malware deployment.
Description of observed TTPs aligned to the MITRE ATT&CK® framework
TACTIC – RESOURCE DEVELOPMENT
T1588.002 – Obtain Capabilities: Tool
- One of the most essential steps in the campaigns analyzed is the acquisition of tools, which in this case tend to have trial periods within their sites. Once the threat actor obtains an account, they create agents that report to their management console with the objective of taking control over the infected systems.
T1583.008 – Acquire Infrastructure: Malvertising
- Based on our research, SCILabs identified some web templates for downloading or updating services such as WhatsApp. Although SCILabs did not identify malicious sites, there is medium confidence that the attackers could be using malvertising or BlackSEO.

T1583.006 – Acquire Infrastructure: Web Services
- Through intelligence and research, SCILabs identified the creation of websites specifically designed to download the remote administration tool agents. In one case targeting Brazil, we identified the use of IP geolocation to allow or block the download of the device, if the incoming request comes from another country. We also identified the use of Dropbox as malware repository.
TACTIC – INITIAL ACCESS
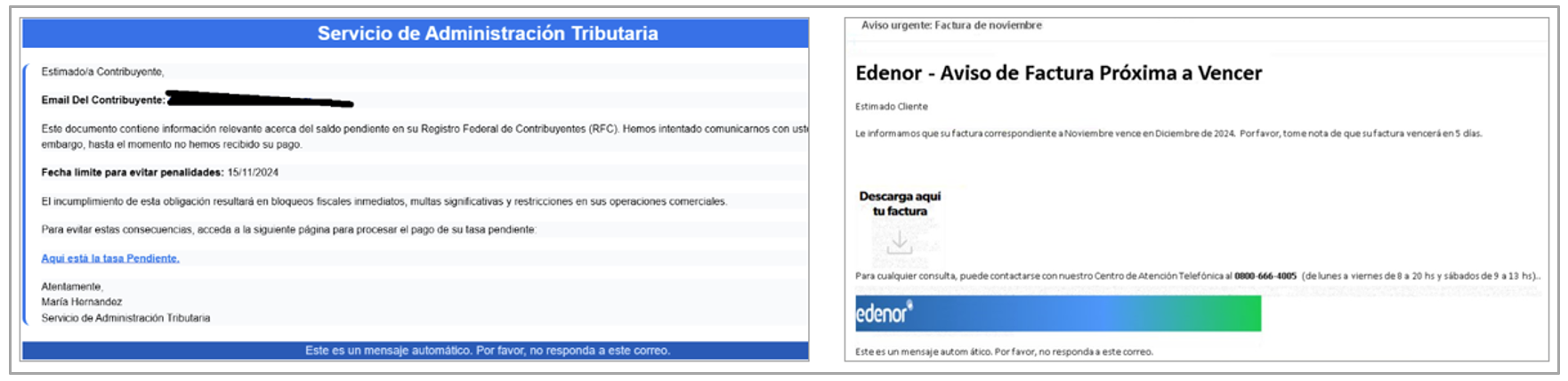
- Threat actors are dedicated to creating templates to deliver artifacts via email. In this case, the following pretexts have been identified:
- Traffic tickets
- Pending invoices
- Judicial quotations
- Pending tax notes
- Transfer receipts
T1566.001 – Phishing: Spearphishing Attachment
T1566.002 – Phishing: Spearphishing Link
- In the campaigns analyzed by SCILabs, we have identified that attackers use both attachments and links to automatically download artifacts. These are typically not classified as malicious and do not require any layer of obfuscation, as they are legitimate agents signed by remote administration tools.
T1586.002 – Compromise Accounts: Email Accounts
- Based on one of the identified campaigns, there is medium confidence that attackers are using compromised organizational accounts to create tenants. This is due to some remote administration tools, such as Atera, only providing trial periods for corporate accounts. It’s important to note that trial periods vary from 7 days to 1 month depending on the administration tool, so campaigns can last up to this period.
TACTIC – EXECUTION
T1203 – Exploitation for Client Execution
- For these campaigns to be effective, threat actors require the user to install the administration agent on their computer by running the artifact provided by attackers, which already contains data to connect to the managed tenant.
T1059.001 – Command and Scripting Interpreter: PowerShell
T1059.003 – Command and Scripting Interpreter: Windows Command Shell
- During the analysis of these campaigns, SCILabs identified that threat actors leverage the capabilities of remote administration tools to conduct reconnaissance on computers and determine if they are potential victims. If the victim is of interest, they execute additional commands to install other tools or execute malware payloads.
T1072 – Software Deployment Tools
- In conjunction with the previous technique, in some cases attackers take advantage of the opportunity to install additional tools, such as Atera, that can work alongside Splashtop, which the attacker installs if they identify a potential victim to gain remote desktop access to the victim computer.
TACTIC – PERSISTENCE
T1133 – External Remote Services
- Because remote administration tools are installed, the attacker can access the victim computer at any time.
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
- Depending on the tool installed, such as PDQ Connect or Atera, they generally create persistence on the start of the operating system by using the registry key in the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. It is worth mentioning that this is a property that is configured and is not necessarily modified by the attacker.
T1543.003- Create or Modify System Process: Windows Service
- In the analyzed malware campaigns by SCILabs, involving the use of remote administration tools, it was observed that attackers seek to always create a service within the compromised assets as a persistence mechanism. This feature is configured by default by the tool developers, and this service is automatically started along the operating system.
TACTIC – DISCOVERY
T1082 – System Information Discovery
- According to the analyzed campaigns, threat actors use PowerShell code to scan a computer’s characteristics, such as the operating system, hard drive capacity, processor, and RAM, allowing them to identify whether it is a potential victim or if it is being run in a controlled environment.
TACTIC – COLLECTION
- Due to the features of remote administration tools, attackers can copy information from the clipboard and keystrokes and obtain information directly from the victim computer’s screen.
TACTIC – COMMAND AND CONTROL
T1219.002 – Remote Access Tools: Remote Desktop Software
- Through remote administration, a threat actor can gain control of the computer and send instructions to it, thereby injecting other types of malware or extracting information.
TACTIC – EXFILTRATION
T1041 – Exfiltration Over C2 Channel
- Remote administration tools have the capability of accessing information shared through an encrypted channel located within your own infrastructure, allowing attackers to access confidential information without being tampered with.
Observed TTPs aligned to the MITRE ATT&CK® framework
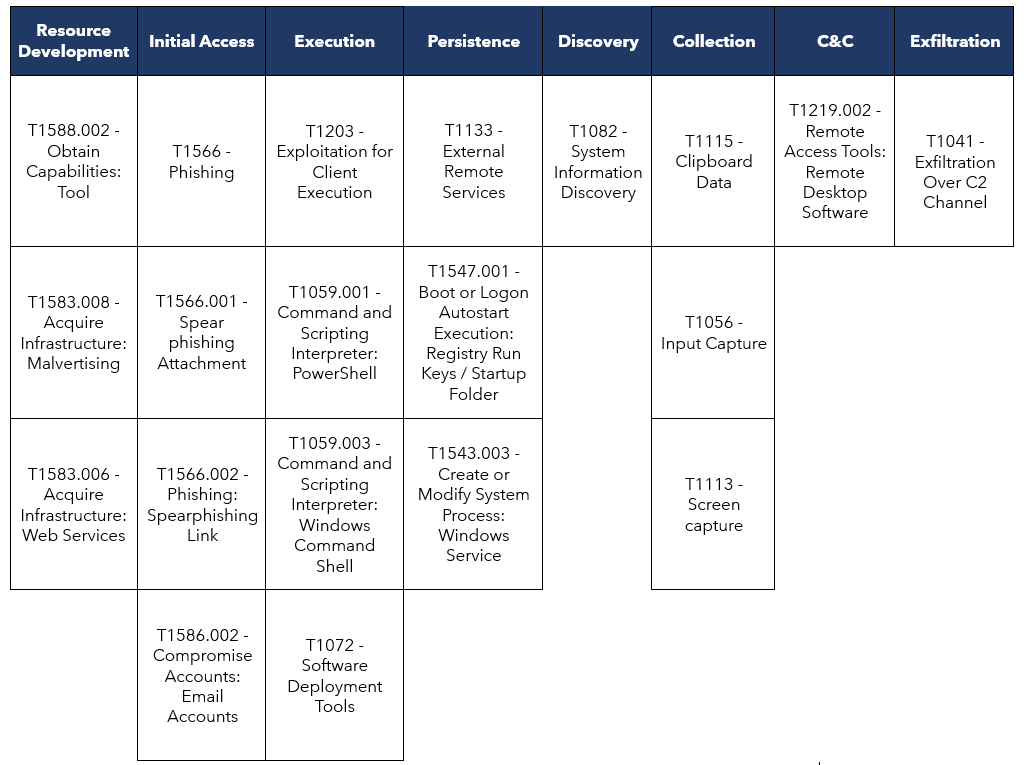
Given the wide variation in delivery methods, execution stages, and final targets across campaigns analyzed by SCILabs, this analysis focuses specifically on the activity of threat actors leveraging remote administration tools.
Next, a diamond model is presented, associated with the capabilities, infrastructure and victims of this threat.
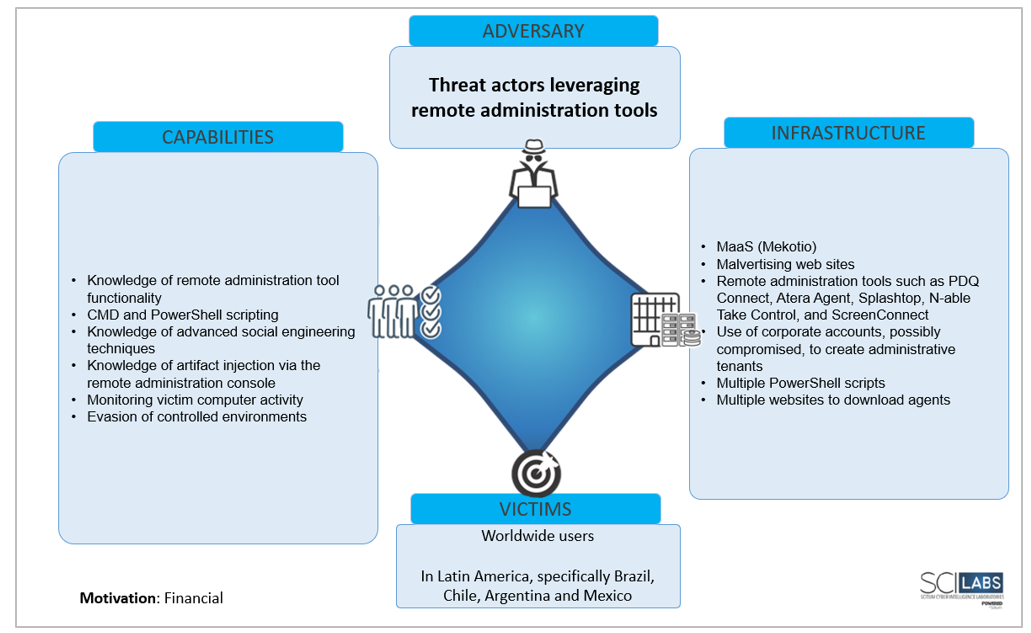
Strategic threat risk analysis
Challenges for organizations faced with this type of threat
Based on the information previously mentioned in this document, it is believed that there are two main challenges facing this type of threat.
The first challenge is that many organizations are not prepared to control applications that are essential to their operations and those that are not recorded by the organization but that are relevant to fit the business needs. This represents a significant risk because, without these types of controls, adversaries can use these legitimate tools maliciously; however, threat actors misuse them, resulting in an effective compromise that cannot be easily stopped by traditional security tools such as an EDR, antivirus or firewalls.
It is necessary to begin reinforcing these types of policies in organizations and implement specific restrictions on authorized and unauthorized applications, preventing any user from running and installing applications on their computers. This effort can be significantly challenging depending on the number of computers and users within the organization, although it is possible to start with those users who have access to critical information and then work down to other levels of the organization.
To the extent that an organization’s applications are controlled, a more robust environment will be created that will prevent threats like these that use legitimate software to compromise information.
The second challenge relates to the security tools, their administrators, and the analysts who operate them. This is because, as this behavior may normally appear legitimate, many technologies lack the ability to identify this behavior and therefore fail to issue alerts about a potential threat, allowing it to go undetected.
Due to these factors, the challenges are significant, since it is necessary to acquire technology or create specific detection rules to observe this type of behavior and, in turn, pay attention to each of them to avoid blindness due to alerts. This also includes setting up appropriate environments to analyze campaign behavior.
Additionally, malware analysts may find that these threats can identify device characteristics and, therefore, detect whenever they are being analyzed in automated controlled environments such as sandboxes or manual environments such as virtual machines. This capability complicates the goal of each campaign, as operators may refrain from initiating malicious activities if noticing signs of analysis.
Observed metrics
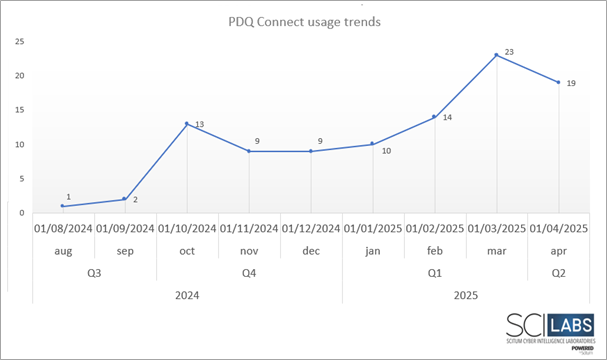
According to a study of SCILabs telemetry, where 100 samples associated with the remote administration tool (specifically PDQ Connect) obtained from public sandboxes were analyzed, it was found that PDQ Connect was used for the first time in August 2024 as part of the techniques described in this document, being the most important peak recorded in October with 13 hits. As a hypothesis, with medium confidence, SCILabs theorizes that the adversary finished the testing phases in August and began the proper deployment of the threat by October, maintaining constant activity from this date onward.
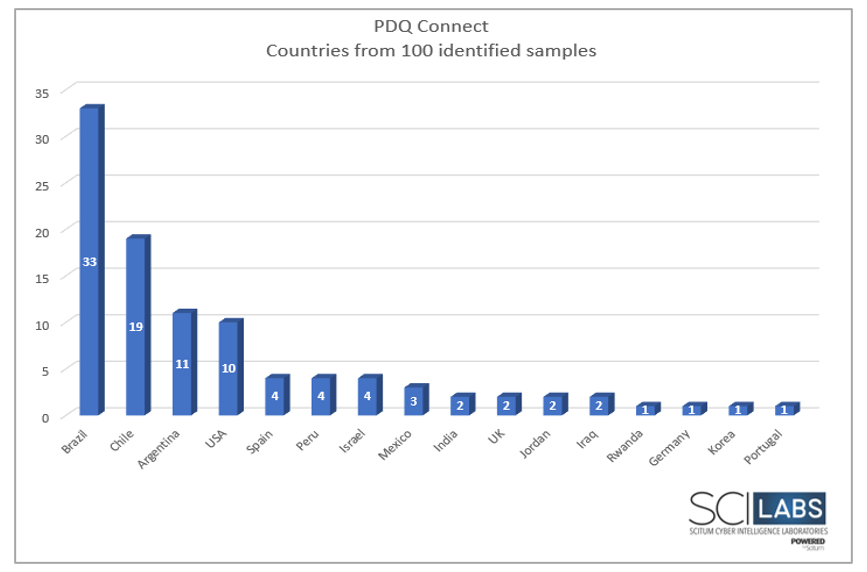
Based on our analysis of the samples, we identified that 33 attacks were targeted to Brazil, 19 to Chile, and 11 to Argentina. Based on our experience, we have a medium level of confidence that the threat operators are distributing banking malware, like Mekotio, which typically targets Latin America.
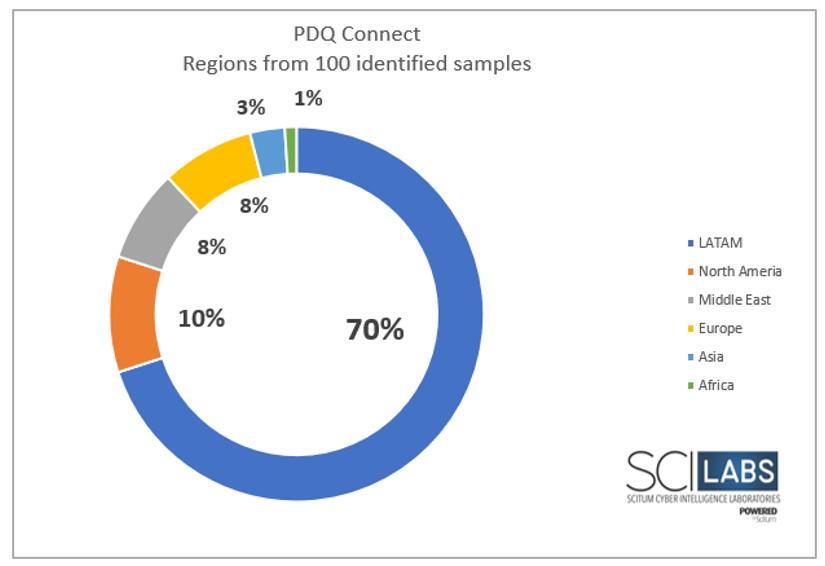
Based on the findings identified, SCILabs detected that this tool scope is global; however, its primary focus is on Latin America, with 70% of the total events; North America accounts with 10%; the Middle East and Europe account with 8% each; Asia accounts with 3%; and finally, Africa accounts with 1%.
We conclude that the tool PDQ Connect is the most used by threat actors to affect users in Latin America, so we have a low-confidence hypothesis that this may be due to weak application control policies.
In this case, we analyzed PDQ Connect, but the trend seems to spread to other tools such as Atera Agent, Splashtop, N-able Take Control, and Smart Connect, based on the samples SCILabs has analyzed. Additionally, attackers are likely to continue the use of other remote administration tools like those mentioned above.
Recommendations
- Conduct awareness campaigns about social engineering techniques used by cybercriminals to distribute malware, such as phishing emails using pretexts related to outstanding invoices and payment receipts.
- Conduct awareness campaigns about avoiding the installation or execution of software that is not explicitly authorized by the organization, especially if it is remotely administered.
- Integrate security policies at all levels of the organization, including the use of high-quality antivirus or EDR software, keeping them consistently updated to ensure they have the latest signatures released by the manufacturers, thereby significantly reducing the chances of infection.
- Evaluate the possibility of blocking the PDQ Connect tool on all the organization’s endpoints using application control software if it is not used in the operation due to its use by Mekotio and other threats.
- Have strict policies regarding the installation of remote administration tools such as Atera, Splashtop, PDQ Connect, N-able Take Control, ScreenConnect, and others, if it does not affect the organization’s operations.
- Monitor traffic to app.pdq.com, websocket.app.pdq.com, agent-api.atera.com, and my.splashtop.com, which could be an indicator of an attack if the use of PDQ Connect, Atera, or Splashtop is unauthorized.
- Consider blocking any remote administration tools, especially if they are free, using application control software. If the use of any remote administration technology is necessary, only allow the organization’s custom-agent hash.
- You can also replace remote administration tools with controlled access through VPN connections, with strict least-privilege policies so that only authorized users can access remotely.
- If you have remote administration software, it is recommended to enable MFA to reduce the possibility of malicious use. In addition, validate the ability to send logs to a SIEM.
- Educate users about avoiding storing login credentials in internet browsers and the risks involved.
- Create rules to detect the use of remote administration tools in the SIEM and always validate any new events to determine whether they are authorized or malicious activity.
