2025 Updated Recommendations: Before, during and after ransomware attack
Current ransomware landscape in LATAM
Based on SCILabs telemetry and information gathered from public and private security feeds, attacks were observed in at least 19 countries in Latin America during 2024, carried out by at least 51 ransomware variants.
The top 5 variants with the most activity during 2024 represent 55.01 % of the total threats that affected the region, which are listed below:
- RansomHub: 17.69 %
- LockBit 3.0: 17.31 %
- Akira: 8.08 %
- Arcus Media: 7.31 %
- FunkSec: 4.62 %
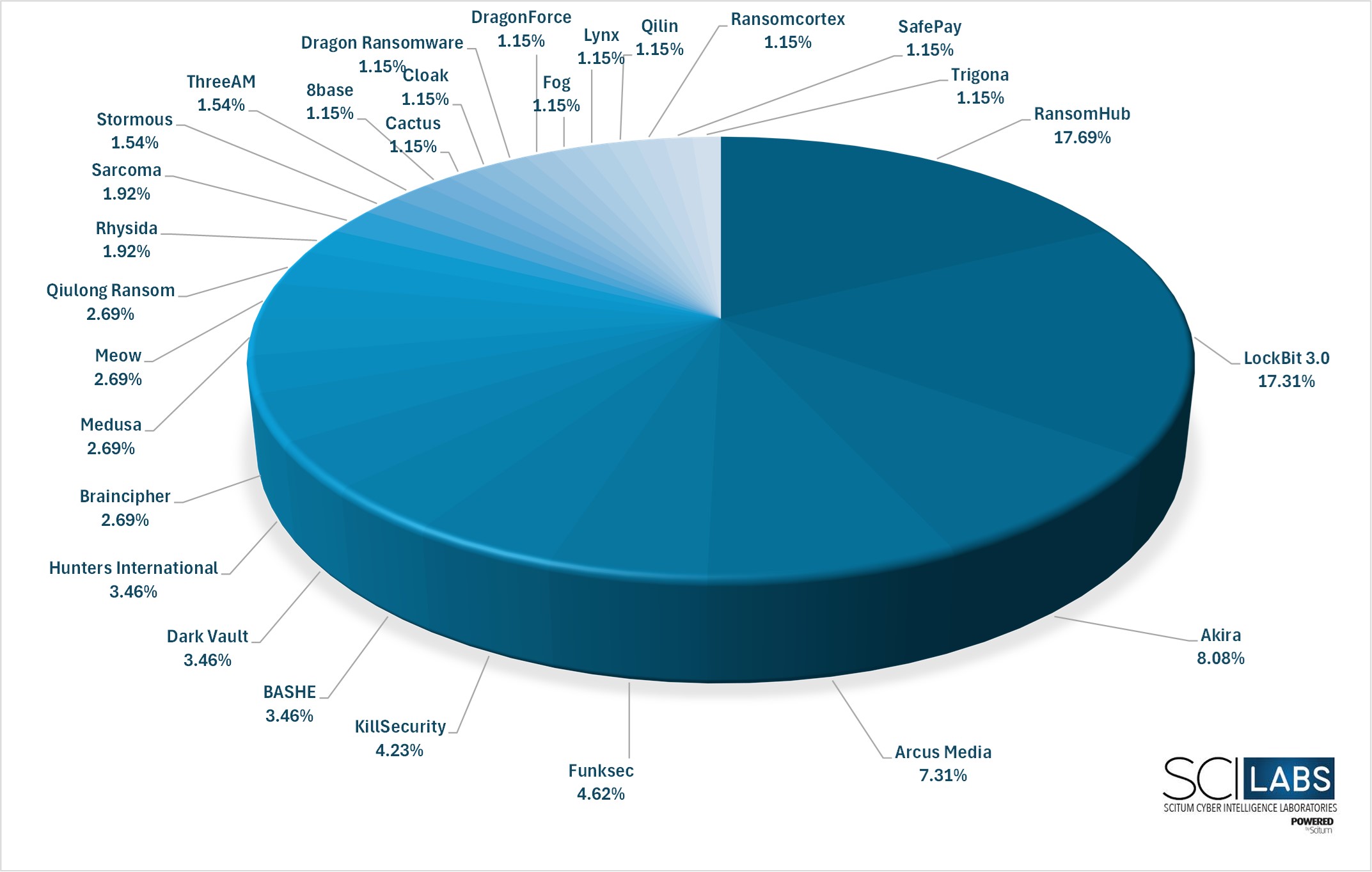
In 2024, RansomHub emerged as the most prominent variant in the region, with many attacks and a high success rate. LockBit 3.0 (currently LockBit 4.0 [1]) remains active in Latin America as one of the most significant threats; however, during this period, it was displaced to second place after having been the most impactful ransomware variant targeting organizations in Latin America for two consecutive years. Finally, another active variant, Akira, increased its number of attacks in the second half of the year.
On the other hand, a significant increase was observed with new variants emerging, such as Arcus Media and FunkSec, which have intensified the frequency of their attacks in the region.
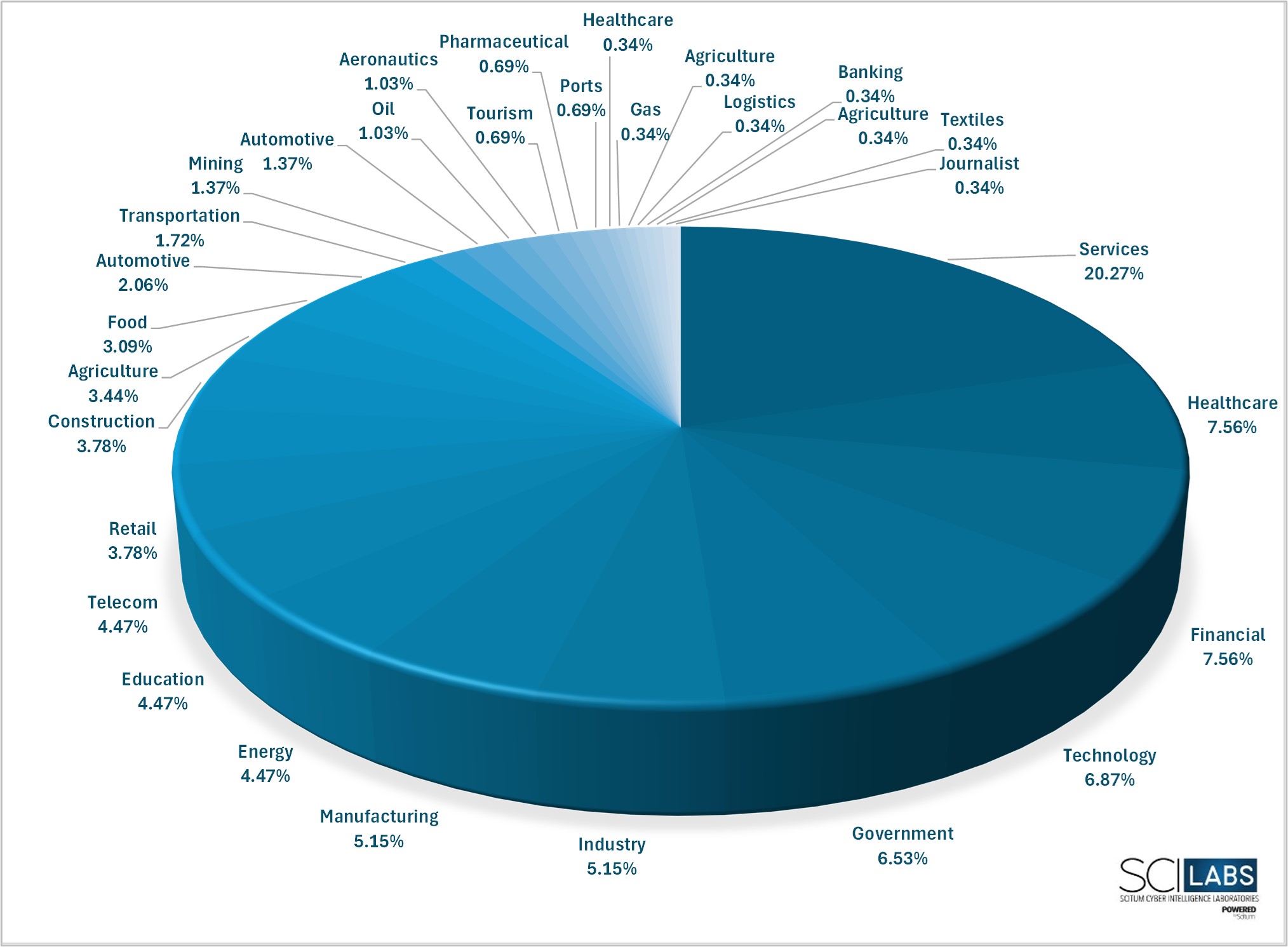
The following graph shows the sectors and industries most affected by these threats, according to SCILabs telemetry.
How could a ransomware attack affect organizations?
If a ransomware attack is successful, threat actors could steal, encrypt, and leak information from affected organizations. This can lead to operational disruptions, financial losses, compromise of confidential data, and a significant loss of reputation and trust. The impact may include severe financial, legal or regulatory consequences, as well as the loss of trust among customers and partners.
Therefore, it is crucial for organizations to be aware of the TTPs (Tactics, Techniques, Procedures) associated with these threats and to implement recommended measures to reduce the risk of infection. They should also be prepared to respond effectively in the event of a ransomware compromise. It is important to remember that a ransomware attack is not only about data loss but it could jeopardize the very future of an organization.
How to prevent or reduce the impact of a ransomware attack?
Organizations must have proactive security strategies to prevent malware attacks or, in some instances, execute an appropriate response and subsequent recovery from a cybersecurity incident. SCILabs proposes the following recommendations to avoid or reduce the chances of suffering a ransomware attack:
Preparation focused on methodology for the response
- Establish a regulatory framework that outlines the policies must follow upon detecting a potential phishing email, along with clear guidelines for system administrators and third parties to ensure proper follow-up. This approach reduces the likelihood of a successful attack through these means, as multiple threats use phishing as their primary distribution method.
- Establish a business continuity plan that considers a “ransomware-based cyberattack” among its scenarios.
- Have an incident response process that includes a comprehensive communication plan tailored to all organizational levels, with a focus on crisis management during a security incident. The plan should outline how to communicate effectively with customers, employees, and the public if required. Customers and partners must be informed of the measures being taken to resolve the situation and protect their data, and guided on any actions they may need to take. It is essential to avoid scaremongering , provide regular updates, and ensure accuracy of all information to preserve the organization’s credibility.
- Conduct ransomware attack simulations to determine the organization’s incident response team’s capacity to address the threat. In case the organization does not have an internal incident response team, it is crucial to have an external one that aligns with its needs and ensures an intelligence-driven approach to the threat, understanding the threat actors behind the attack.
Improvements in the general strategy or processes
- Continually provide awareness courses to the organization’s employees on social engineering attacks and malware infection prevention to raise awareness of the threats to which they may be exposed and minimize the risk of being affected by a successful attack.
- Conduct ongoing awareness campaigns focused on educating users about ransomware, using targeted phishing tests to allow those individuals with a lower awareness of threats to receive specific training. The following basic recommendations are suggested based on SCILabs telemetry:
- Verify the sender of the received email.
- Verify that the email’s subject, sender, and content are consistent.
- Avoid opening suspicious links or attachments.
- Avoid sending sensitive or confidential information to unknown senders.
- Establish a well-defined alerting protocol, so that employees and coworkers can report unusual computer activity, or a potential cyberattack and know how to react in an emergency.
- Avoid opening links or downloading attachments from emails or unknown or suspicious websites, as they may be used to distribute malware.
- If possible, establish a strict policy through access control lists to prevent threat actors from using legitimate tools with potential malicious use (Potentially Unwanted Application – PUA).
- Keep all systems and software used in the organization updated with the latest security patches. It is important to conduct the necessary tests before applying changes to production environments so that they do not affect operations.
- Avoid using unauthorized or pirated software, as these may contain malicious artifacts that can be an initial attack vector against the organization.
- If the organization has critical servers, legacy assets or unsupported equipment, it is highly recommended that they are kept on an isolated, monitored, and protected network to prevent them from being easily compromised.
- Plan and conduct periodic security tests on infrastructure and applications to identify and mitigate vulnerabilities before a threat actor exploits them.
- Establish a backup process, considering essential information and a schedule of dates to keep them protected on devices that are not part of the organization’s infrastructure and ensure business continuity.
- Limit user and application access to only what is strictly necessary (Principle of Least Privilege – PoLP).
- Avoid enabling content from suspicious documents or those not issued by trusted sources, as this is a valid application method and can easily be executed to carry out malicious activities on the operating system. One such example is Microsoft Office files that contain auto-execute macros.
- Disable Microsoft Office macros or allow only digitally signed macros to run through a Group Policy Object (GPO).
- Maintain an Out-of-band (OOB) management network to administer critical services so only specific users can access them.
- Separate IT and OT networks to prevent malware from spreading due to access between infrastructures. Disable unnecessary ports or functions.
Preparation focused on prevention
- Have an organization-wide vulnerability management plan, including those directly connected to the organization, so that vulnerabilities that attackers could exploit are detected on time, and the necessary remediation measures are implemented, minimizing the possibility of impact from these failures.
- Be able to detect advanced threats on the network using Machine Learning or algorithms that can detect malicious behavior, since network visibility is key to knowing when malware is moving laterally, either through an attempt to exploit vulnerability or through the reuse of weak passwords on administrative accounts.
- Be able to manage a comprehensive process that ensures that any server exposed to the Internet is appropriately protected.
- Limit access to device management interfaces, such as firewalls, to only a secure network
—preferably an internal, private network— to prevent exposure to the Internet.
- Establish the use of a second authentication factor for accessing critical services and infrastructure within the organization’s policies to minimize the possibility of unauthorized access.
- Continuously map devices that are being insecurely exposed to the Internet and take the necessary measures to protect them or disable services, paying special attention to web servers, mail servers, VPN services, or SSH.
Improvements to critical operational tools
- Maintain advanced monitoring on the most accessed devices to promptly identify when a suspicious event is occurring. Servers exposed to the Internet should be considered, for example:
- Web Servers
- Mail Servers
- VPN Servers
- If the organization has Citrix servers, it is recommended to validate that these are only accessible through VPN or the local network since they are an access point used by ransomware operators.
- Store logs on a centralized server for analysis during investigations or incident response, and ensure they include the originating IP address of each request.
- If remote access to RDP or terminal services is required, they should only be accessible through a secure VPN (with multi-factor authentication) to the corporate network or through a Zero Trust remote access gateway.
- Critical servers for general operation:
- Domain controllers
- Authentication Servers
- Hypervisors
- Backup Servers
- Backup Servers or Servers with privileged access to most of the infrastructure:
- Jump Servers
- Antivirus Servers
- Monitoring Servers
- Equipment for Server management
- File sharing Servers
Activities to perform in the operational tools
- Regularly update security patches for the software used in the organization to mitigate vulnerabilities and reduce the possibility of exploitation.
- Monitor changes or inclusion of unscheduled GPOs or those generated by unauthorized users to prevent them from being used to distribute malware or enable vulnerable services.
- Carry out additional hardening of Internet-exposed equipment and services:
- Implement elements such as multi-factor authentication (MFA): if a password is stolen, it would not be sufficient to gain access to the service.
- Implement a Web Application Firewall (WAF), which specializes in filtering to reduce the risk of an attack on the organization’s Web applications.
- To identify abnormal device behavior, use auditing tools, such as auditd or sysmon, and send logs to an SIEM (Security Information and Event Management) system.
- Ensure that data stored in operational tools is protected from unauthorized access.
Detection and response improvements
- Stay informed of threats affecting the region. If possible, consider acquiring a threat intelligence service specialized in Latin America that provides indicators of compromise, countermeasures, and recommendations for decision-making at the strategic, tactical, and operational levels.
- Enable encrypted traffic inspection features on perimeter security devices to improve detection and visibility.
- Use web filtering tools to restrict access to websites classified as malicious to reduce the possibility of a user entering.
- Carefully control and monitor traffic leaving the network to detect suspicious behavior and respond promptly to its analysis, checking the following in logs:
- Network traffic to malicious or suspicious addresses based on threat intelligence or anomalous behavior cataloged or identified by the organization.
- Network traffic from DMZ servers to computers or services outside the server’s operation.
- Name resolution requests from DMZ servers to domains outside the server’s operation.
- Verify non-service-related connection requests from the web, file transfer, or email servers.
- Be alert to communications with cloud storage services other than the company’s official ones and, if possible, block them.
- Review and validate files before downloading them from storage sites or cloud services such as Mega, Discord, Dropbox, Google Drive, OneDrive, Pastebin, and GitHub, among others. Malware operators often use these services to host their artifacts. In addition to awareness, a monitoring service could allow users to avoid downloading potentially malicious files.
- Configure security alerts that are triggered when a team sends a large amount of information to detect any type of information leak related to attacks.
- Have a quality XDR solution on every server or EndPoint in the organization. Not all XDR solutions are created equally, and many of those developed as antivirus solutions lack the necessary features to respond to a security incident. It is important to verify that the solution used in the organization has undergone thorough anti-tampering tests and includes a centralized monitoring console that is protected against possible encryption.
- Provide security devices with the most up-to-date indicators of compromise (IoC) as a proactive measure to detect and block attacks on the infrastructure.
- Disable Windows Script Host, if possible, as it can be used to interpret and execute JavaScript (.js files) and Visual Basic Script (.vbs and .vbe files), which can be dangerous during a cyberattack.
- Configure an anti-spam filter to block external and internal emails containing malicious content, links, or malware.
- Check access permissions on shared folders and the security of folders at the file system level. To prevent malicious files from being uploaded, it is suggested that you use “read-only sharing”.
- Configure organizational accounts using the principle of least privilege (PoLP), especially for accounts for services published on the Internet.
- Segment networks to prevent the spread of ransomware. Network segregation can help prevent the spread of ransomware by controlling traffic flows, access to multiple subnets, and restricting an adversary’s lateral movement.
- Enable system auditing to track login and logout events in Active Directory; this can be used to conduct in-depth investigations into unauthorized access.
- Perform credential compromise detection activities and implement alerts on privileged accounts if access attempts are detected from unusual locations.
- Perform threat-hunting activities on the organization’s infrastructure to identify unusual processes, unidentified scheduled tasks, suspicious executable files in system paths, and anomalous resource usage on the endpoint. For example, it is suggested that the logs be checked for using LOLbins, execution of PowerShell commands with suspicious behavior, connections via the SMB protocol to detect lateral movements, scheduled tasks to maintain persistence or programs that run when the operating system starts.
- Use DLP systems to reduce the likelihood of information leaks from the organization and detect anomalous behavior in transferring or deleting large volumes of information. It is advisable to pre-classify all the organization’s information to do this.
- Generate offline backups (magnetic tapes or similar, or cold storage in the cloud) in a different geographic location than the organization’s data center, as this provides additional security. In the event of a compromised infrastructure, off-site storage can help restore operations more quickly.
- Keep “golden images” (templates or system images) of critical systems offline. These can help quickly restore server functionality if the affected equipment cannot be immediately reconstructed. These images should have preconfigured operating systems and associated operating software.
- Keeping encrypted backups enhances confidentiality and helps prevent threat actors from accessing the data in the event of exfiltration.
- Maintain an active threat hunting program that allows for the identification of ransomware precursors such as downloaders and anomalous communications that may indicate communication with attackers within the network, among other things, according to the most common attack vectors detected by the Cyberintelligence team.
- Identify the types of ransomware most affecting other organizations in the same sector, along with their delivery, distribution, execution, and persistence techniques, in order to establish preventive measures.
- Collaborate with other organizations in the same sector to share information related to ransomware and other threats they have faced.
- Have a SOAR (Security Orchestration Automation and Response) solution to orchestrate detection, investigation, and response activities to security events in an automated manner based on use cases, especially those associated with ransomware.
- Have an NDR (Network Detection and Response) solution to identify anomalous traffic, such as connections to C2 servers, anomalous data transfers on unusual dates or times, and identify port scans from compromised computers.
Remote administration recommendations
- Create a GPO policy in the Active Directory to disable remote access to computers via RDP; this prevents its misuse on network devices.
- Prevent the use of software for remote access to the organization’s devices and monitor its installation attempts. If remote administration is necessary, it is recommended to implement a VPN with two-factor authentication and to enable RDP on devices only as needed for this service. This measure reduces the risk of unauthorized access to these resources.
- Implement geolocation-defined blocks on remote access services such as VPNs to prevent access from countries where the organization does not operate.
- Create detection rules that alert you when VPN access occurs from two geographically distant points in a short period, known as impossible travel, to promptly identify and investigate if a user exhibits this behavior. Blocking the account upon detecting this behavior can help reduce the impact of an attack.
- Audit remote access activities to detect access from abnormal sources or access to critical services by users unrelated to such services, such as SSH.
- Change the default port for SSH connections (TCP/22 port) to a non-standard port and restrict access to authorized IP addresses only.
- If connecting to critical assets via SSH, implement SSH key-based authentication instead of passwords and configure a periodic password rotation.
- If the operation requires the use of remote access software, it is important to consider the following recommendations:
- Add the software to a whitelist or access control list only for the devices that require it, and disable it for the rest of the devices within the corporate network to ensure that only a controlled number of devices can access it with the application.
- Implement two-factor authentication in the remote management software. If the application being used doesn’t have this option, it’s suggested to use one with this functionality; this way, you reduce the possibility of an attacker guessing the password and taking control of the device.
- Enable all logs for monitoring in the applications; if possible, send them to the “correlator” and create detection rules when access is granted to audit whether access is authorized.
- Disable or uninstall the software when not required so it isn’t used inadvertently.
Recommendations related to PowerShell
- Create a GPO policy in Active Directory to disable PowerShell on computers where it is not required and only allow certain users with specific needs to run it.
- Implement Just Enough Administration (JEA) technology to delegate specific administrative tasks to users without granting them full administrative privileges.
- If PowerShell is required on some computers, consider the following:
- Update to the latest available version and remove previous versions to prevent attackers from exploiting vulnerabilities and executing their malicious code.
- Configure script execution unless they are signed or generated for internal use by organizational functions; this reduces the possibility of unauthorized command execution.
Recommendations related to SMB
- Create a GPO policy in Active Directory to prevent SMB from being enabled by default and suppress access to hard drives using this protocol through administrative accounts. Such configurations open the door to lateral movement.
- Consider using devices with SMB version 3, as ransomware attacks have compromised version 1 of this protocol. Additionally, if SMB version 2 are in use, isolate them within a segmented network.
- Disseminate and implement the use of strong passwords that are not easy to guess or decipher using techniques such as credential stuffing, brute force, dictionary attacks, password spraying or rainbow tables.
- Verify that devices do not have vulnerabilities such as EternalBlue, SMBleed or SMBGhost, also known as CoronaBlue, which attackers have exploited during ransomware incidents.
Recommendations for Active Directory
- Limit or restrict domain administrator access to any device other than a domain controller. If an administrator needs to use their credentials, it is advisable to grant access to an end-user device, audit access, and log activity in an SIEM.
- Acquire a dedicated solution for Active Directory protection. Deception solutions, malware traps, or honeypots can help detect an attack attempt early, not only in Active Directory but also on the operational network.
- Perform threat hunting on domain controllers, servers, workstations, and Active Directories, looking for new accounts or accounts whose creation is unrecognized or suspicious.
- Change the passwords on all computers periodically and use multi-factor authentication for all Active Directory user accounts.
- Never run unofficial services with high privileges or domain administrator accounts, as these could store credentials that could be used for malicious purposes.
- Limit the creation of domain administrator accounts and other privileged groups: The fewer accounts and groups there are, the more difficult it will be for an attacker to find administrative accounts.
- Protect the domain administrator account with strong passwords, MFA, and regular password changes.
- If possible, it is recommended to deactivate the built-in administrator account and remove users from the local administration group.
- Enable real-time auditing and correlation rules related to the modification of GPOs. Because some threat actors conduct malicious activities by abusing them.
- Restrict installation of additional software or configuration of server roles on domain controllers other than those defined by your organization’s security policies.
- Perform patch management and vulnerability scanning regularly.
- Use secure DNS services to block malicious domains.
- Enable and configure the Windows firewall with the rules defined in your organization’s security policies.
- Use an allowlist application to establish which applications are allowed to run in the active directory.
- If possible, implement a PAM (privileged access management solution).
- Use a secure management workstation (SAW).
Recommendations for hypervisors
- Keep virtualization software up to date with the latest patches released by the manufacturer.
- Disable access to root accounts, establishing unique accounts with the proper permissions.
- Set unique CLI permissions for only authorized users.
- Implement an XDR (Extended Detection and Response) tool to identify, detect, and prevent attacks on virtual machines running on hypervisors.
- Isolate the hypervisor and the resources necessary for its operation, such as vSANs and backups, from the network.
- Define rules for VEEAM, HYPERV, and VMWare (so that these platforms can only be accessed from specific management servers) and restrict access to those servers.
- Manage identity and access by decoupling ESXi, vCenter, and other hypervisors from Active Directory to protect the virtualization infrastructure in case of a compromise.
- Use dedicated accounts for infrastructure administration, enable multi-factor authentication (MFA), and securely manage credentials.
- Restrict only necessary services to hypervisors.
- Enable the local firewall to allow administrative access from trusted network segments or hosts.
- Send hypervisor logs to the organization’s central SIEM to provide visibility into security events.
- Maintain frequent backups that an attacker cannot delete. Offline backups or specialized services can achieve this.
Specific recommendations for vSphere and ESXi
- It is recommended to consider hardware that includes TPM 2.0 when installing virtualization software, which will automatically use the security chip to store authorization keys and ensure that system files have not been modified.
- Secure Boot: This ensures that the code executed at server startup is digitally signed and has not been modified, making it difficult for threat actors to persist and gain initial control.
- It can be enabled at the following link: /usr/lib/vmware/secureboot/bin/secureBoot.py -c
- execInstalledOnly: This feature of ESXi and vSphere restricts binary execution on the hypervisor, preventing a threat actor from deploying and executing their tools. To verify it’s active and to activate it, run the following:
- esxcli system settings kernel list -o execinstalledonly
- esxcli system settings kernel set -s execinstalledonly -v TRUE
IMPORTANT: The configurations mentioned above should be tested in a laboratory or UAT testing environment before being implemented in the production environment to avoid issues.
If organizationally feasible, it is highly recommended to restrict the use of the following tools, as SCILabs identified them through incident response activities. While some of these tools may have legitimate uses, monitoring their behavior and raising an alert if any unknown or suspicious installations are detected is important.
| Tool | Activity | Tool | Activity |
|---|---|---|---|
| ADRecon | Recognition | WinSCP | Exfiltration |
| PsExec | Lateral movement | NirCmd | Command execution/Defense evasion |
| Mimikatz | Credential access | Rclone | Exfiltration |
| Nirsoft password recovery tools | Command execution/Defense evasion | PCHunter | Recognition /Process manipulation |
| ExMatter | Exfiltration | GMER | Defense evasion |
| Bloodhound tool | Recognition | BazarLoader | Lateral movement |
| CrackMapExec | Lateral movement | GrabFF | Web browser credentials |
| Inveigh/InveighZero | Capture/Credential access | GrabChrome | Web browser credentials |
| MegaSync | Exfiltration | BrowserPassView | Web browser credentials |
| Adfind | Recognition/Lateral movement | KeeThief | Credential access |
| Rubeus | Credential access | FileGrab | Exfiltration |
| Stealbit | Exfiltration | CobaltStrike | Command and Control /Post Exploitation |
| ConnectWise/ScreenConnect | Persistence/Lateral movement | FileZilla | Exfiltration |
| Process Hacker | Recognition | Advanced Port Scanner | Recognition |
| RDPconnections | Persistence/Lateral movement | NetScan | Recognition/Lateral movement |
| ProxifierPE | Command and Control (Proxy) | Pcloud | Exfiltration |
| OpenChromeDumps | Credential access | WmiExecAgent | Lateral movement/Command execution |
| S3 Browser | Web Browsing | LaZagne | Credential access |
| Veeamp | Credential access | SoftPerfect | Recognition / Lateral movement |
| Ngrok | Recognition | TDSSKiller | Defense evasion |
What to do during a ransomware attack?
When an organization has been compromised, it faces multiple questions, such as: Is there a free way to recover the information? What should be reported to senior management? How to initiate recovery efforts? Did an employee orchestrate the attack? Is it possible to clean the compromised devices? What needs to be blocked or isolated? Among many others, it is therefore recommended to focus on the following:
- Initiate an incident response process, which can be used in the BCP (Business Continuity Plan), in case of a cyberattack caused by ransomware. This will allow the organization to follow the previously defined plan and manage the crisis appropriately.
- If a BCP is not available, it is necessary to design a contingency plan that allows the business to continue operating, including a DRP (Disaster Recovery Plan), if possible, including a robust backup policy that includes (offline) backups of critical operating information, to prevent it from being compromised in the event of a ransomware attack.
- If you do not have an incident response process, it is crucial to consider the following:
- Involving an expert incident response team specializing in cyber intelligence will allow faster and more accurate action.
- Defining and communicating the organization’s position internally and externally will establish a unified version of the situation, avoiding panic and reducing media impact.
- Define a “war room” in which all who must participate in the incident response meet physically or virtually (as appropriate).
- Designate a person responsible for communicating the incident’s status to senior management and other areas of the organization.
- Define an incident leader who can make decisions that the rest of the organization’s teams should implement. Listed below are some activities the incident leader should perform during the event:
- Select the investigative sources that will provide information for investigating the incident.
- Determine whether “triage” of the teams involved is necessary.
- Generate hypotheses to guide the investigation, which can then be confirmed or refuted based on the evidence obtained.
- Generate recommendations for containment, eradication, and recovery from the incident.
- Designate a technical leader who can coordinate the group of specialists responsible for the various technological areas involved in the critical process affected and provide support during response activities so that specialists can act quickly.
- Remain calm and avoid jumping to conclusions immediately, as this can lead to hasty decisions that affect the response process and hinder the restoration of operations.
- Avoid searching for those internally responsible for the attack, as this can lead to confrontational situations with personnel that hinder the development of the incident response.
- Conduct an in-depth analysis, if artifact samples are available, to find indicators of compromise that will aid in detecting, containing, and possibly eradicating the threat.
- Establish procedures to block access, report incidents, and conduct forensic analysis after a successful attack attempt.
- Avoid disseminating information on social media and in the media about what happened to prevent false expectations from being generated about the situation. It is important to consider that, in the case of a publicly traded company, if messages are not correctly managed and the media does not convey calmly, the uncertainty created by the media could cause the stock to fall.
- Avoid uploading samples to public analysis tools, as other users could download them and disclose confidential organizational information.
If immediate containment activities are carried out, such as isolating an affected computer, it is recommended that the computer where the incident occurs is never shut down, but simply disconnected from the network, as shutting down could result in the loss of important information during the investigation of the incident.
Lateral movement prevention
- Implement internal firewalls and access control lists (ACLs) to block traffic between segments where it is not necessary, such as by restricting SMB and RDP protocols.
- Configure the Windows Firewall on all hosts to block widely used techniques, such as using PowerShell.exe or other scripts and binaries of Living-Off-the-Land.
- Pay special attention to the execution of tools such as wmic.exe, psexec, netuse, PaExec o crackmapexec, which threat actors frequently use to perform lateral movements.
- Restrict or prevent the use of remote administration tools, such as AnyDesk, GoToAssist, Atera, HOST, Team Viewer, and among others, which threat actors commonly used to perform lateral movements on the victim’s network.
- Segment the network and restrict unnecessary traffic. Segmentation using VLANs to separate systems into different segments, limiting communication between critical and non-critical devices. Implementing micro-segmentation with technologies like VMware NSX helps define more granular rules and reduces the attack surface.
- Apply least privilege policies to ensure that users and systems only have the permissions strictly necessary to perform their functions.
- Disable default credentials and enforce multi-factor authentication (MFA) for critical access.
- Enable technologies such as Windows Defender Credential Guard to protect credentials stored in system memory against hash-stealing attacks, such as Pass-the-Hash.
- Actively monitor the use of privileged accounts and detect the use of attack tools such as Mimikatz using security solutions such as Sysmon and SIEMs.
- Implement endpoint detection and response (EDR/XDR) solutions that identify anomalous behavior and block attacks before they spread. Additionally, a well-configured SIEM helps correlate suspicious events and generate real-time alerts.
- Monitor for unusual access via RDP and suspicious credential usage, which may indicate lateral movement attempts by attackers.
Depending on the magnitude of the incident, the incident response team will determine the most appropriate actions and establish a critical path that can lead to the recovery of the affected systems, based on their understanding of the threat and available intelligence.
What to do after a ransomware attack?
Once organizations emerge from the crisis caused by a ransomware attack, it is essential to consider the following recommendations:
- Conduct a lesson-learned session to determine what they could have done differently and implement actions to prevent reinfection.
- Carry out an advanced threat hunting exercise to identify whether the same or a similar threat exists in any part of the network that must be addressed as soon as possible.
- Maintain exhaustive monitoring for at least three months to ensure that the organization no longer has any traces of the attacker; this involves understanding the alerts generated by the various security solutions implemented during incident response and thoroughly investigating each one.
- Develop detection models that resemble the attacker’s modus operandi to ensure timely detection of any new events associated with the same threat.
- Implement a campaign for partners and users, summarizing the organization’s recent events and the importance of following established security guidelines.
- Conduct a comprehensive assessment to determine the organization’s current state from a process, people, and technology perspective. This will help determine the organization’s internal and external cybersecurity posture and develop a cybersecurity strategy.
- Design the organization’s cybersecurity strategy with a holistic approach, considering at least the following points:
- Consider the new opportunities cybersecurity services must support to protect critical data, considering business objectives, needs, and regulatory compliance.
- Consider focusing on the organization’s risks based on its sector and threat model.
- Recognize the importance of the human factor and user behavior in how individuals respond to internal and external expectations, and use this to determine how and to whom ongoing awareness campaigns should be targeted.
- Execute continuous Cyberintelligence monitoring and threat model mapping to visualize the cybersecurity posture and how it is perceived internally and externally.
- Ensure that the security strategy includes identification capabilities through a visible architecture, continuous monitoring, and prevention, through a holistic approach that considers continuous threat hunting, protection through appropriate technology at the necessary points, prepared people, solid processes, response orchestrated by expert personnel, recovery, verification through processes, and an emphasis on resilience.
