Overview
The following post describes the identified TTPs and IOCs of a campaign analyzed by SCILabs, that is distributing Lokibot in LATAM. It was identified by SCILabs while conducting a threat hunting during the third week of September. The pretext of the campaign is related to urgent financial issues such as: invoices, payment vouchers, payment notices, price quotes, payment details, and more. In this post, the respective IOCs will be provided to protect organizations.
The investigation did not obtain further details on how this campaign is delivered; however, SCILabs considers the use of email phishing as the top threat vector with a medium confidence level. After analyzing the campaign and the artifact, SCILabs determined with high confidence that the attacker’s general objective is to steal confidential information from the victims, as the trojan features are profiled to steal cryptocurrency wallets, usernames, passwords, and other credentials. It is important to mention that the cybercriminal infrastructure seems to be intermittently active on demand or when they launch a campaign.
Finally, it is important to mention that the campaign has begun to accelerate its pace. Since, during the first half of the year, only 2 attacks were observed with the same characteristics, one in Mexico and the other in Peru. However, during the last 2 months a notable increase in attacks with the same characteristics has been observed in the region. Although it is not known who the campaign is targeting, SCILabs determined with medium confidence that the campaign is aimed at ordinary users but has the potential to start targeting various institutions to obtain confidential information from them. Additionally, with the intelligence of SCILabs and information obtained from public and private sources, it is possible to determine that the campaign impersonates financial sector institutions to give credibility to the phishing pretext.
SCILabs will continue to analyze similar attacks as no key elements have been observed, such as the initial access method, lateral movements, or any other essential feature, which allows profiling cybercriminals and raising the level of confidence about the similarities between other campaigns and the attack analyzed throughout this post.
How could it affect an organization?
The campaign can affect the confidentiality of the company’s information because Lokibot’s main purpose is to steal sensitive information, so there is no guarantee that information assets will be protected from unauthorized viewing, data leakage, or intrusion into organization systems.
Analysis
Threat Context
The artifact was detected through a threat hunt. Its specifications can be found below:
- TGU0000207262.pdf.exe: is a trojan that steals sensitive information such as usernames, passwords, cryptocurrency wallets, and other credentials.
Attack Flow
Analysis of Lokibot
Technical summary
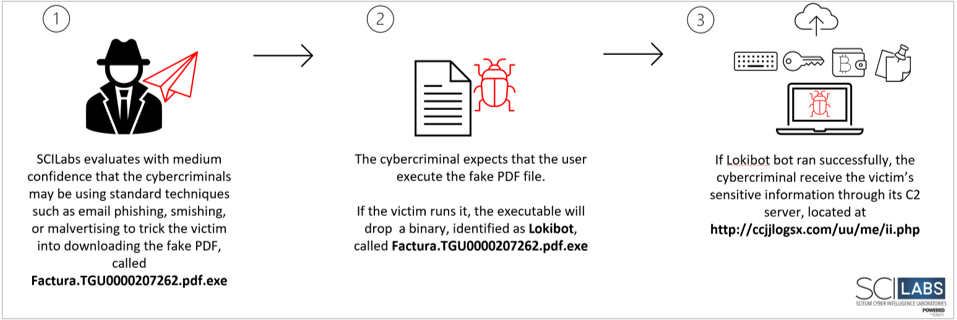
- The initial access method is uncertain, but with intelligence generated by other campaigns, SCILabs has hypothesized that cybercriminals may be using standard techniques such as email phishing, smishing, or malvertising as a decoy to infect the victim.
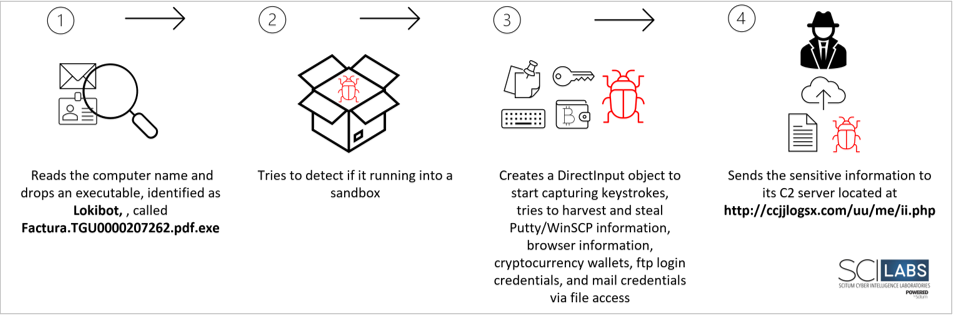
- When the user executes the file, the malware drops a binary, identified as
- The Lokibot trojan detects if it is running on a sandbox using:
- WINE_GET_UNIX_FILE_NAME
- DLL
- Creates a DirectInput object to start capturing keystrokes
- It harvests and steals Putty/WinSCP information opening:
- HKEY_CURRENT_USER\Software\9bis.com\KiTTY\Sessions
- HKEY_CURRENT_USER\Software\Martin Prikryl
- It collects and robs browser information reading:
- C:\Users\user\AppData\Local\Google\Chrome\UserData\Default\LoginData
- C:\Users\user\AppData\Roaming\Mozilla\Firefox\Profiles
- It gathers and steals ftp login credentials through:
- HKEY_CURRENT_USER\Software\Far2\Plugins\FTP\Hosts
- HKEY_CURRENT_USER\Software\NCHSoftware\ClassicFTP\FTPAccounts
- HKEY_CURRENT_USER\Software\FlashPeak\BlazeFtp\Settings
- HKEY_CURRENT_USER\Software\Far\Plugins\FTP\Hosts
- Steals mail credentials via file access from:
- HKEY_CURRENT_USER\Software\IncrediMail\Identities
- HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook
- Finally, it sends the collected sensitive information to its C2 server located at hxxp[:]//ccjjlogsx[.]com/uu/me/ii[.]php
TTPs observed aligned to MITRE’s ATT&CK framework
Below are the MITRE matrixes based on the element analyzed.
| Defense Evasion | Credential Access | Discovery | Collection | C&C |
| T1140
Deobfuscate/Decode Files or Information |
T1003
OS Credential Dumping |
T1552.002
Credentials in Registry |
T1560
Archive Collected Data |
T1573
Encrypted Channel |
| T1027
Obfuscated Files or Information |
T1056
Input Capture |
T1083
File and Directory Discovery |
T1005
Data from Local System |
T1095
Non-Application Layer Protocol |
| T1027.002
Software Packing |
T1552.002
Credentials in Registry |
T1082
System Information Discovery |
T1114
Email Collection |
T1071
Application Layer Protocol |
| T1497
Virtualization/Sandbox Evasion |
T1518.001
Security Software Discovery |
T1056
Input Capture |
||
| T1055
Process Injection |
T1057
Process Discovery |
|||
| T1497
Virtualization/Sandbox Evasion |
||||
| T1033
System Owner/User Discovery |
Table 1 – MITRE’s ATT&CK framework of Lokibot
Assessment
The danger of this campaign lies in its sudden accelerated pace observed in recent months, compared to the first half of the year, which could mean that the attacks observed during the first months of the year were only tests to evolve and refine their pretexts of phishing.
Based on the research carried out, it is possible to determine that the cybercriminals plan to continue evolving and refining the campaign by taking advantage of the misinformation of people against phishing scenarios, as well as the sense of urgency that attackers generate in the victims when receiving an email related to financial issues.
SCILabs will continue to monitor the campaign, its behavior, and malware, as well as any group of cybercriminals that begins to take credit for the attacks.
IoC’s
A77D42E5CF03FCE86D5FCC844840AB9F8DB3F562791348AE5BCA2AABA0D3F54D
55DD34E26E94366E5CB30AA3FD40CD9AD85F7D4D36DE6885084257290087FFA4
EB121B73BB46F824AFC5E73C7CCDC93340D87DEA79E61DF986D90BD3B8A947B1
08DCC10E83BCEDEDF65A87E8F0A3E631F5BBAFDD13AB2B2213EFE9C664CB96A5
D3B21861D2DBBAE76B30B6C1253BE0775C7EA63D183DED44F041A609CBD929C4
90770A21604880EF1E140798AD7F679383853F070358A5B29C15C4A26A9AA9EB
F4982822F4DD3DB87F26C5C9BB9AB4C7BAAC9BF970CABABA3493E1A5DD8CE5F7
0F747FAA13A45806A17DE55E3353849F7FF6C9687AC78CBA22DFD6049192C42A
C60D377A5324054912D63303E2553B4B39E6778447A3A23EEFD24EB09FFA4A8F
HXXP[:]//ALPHASTAND[.]TRADE/ALIEN/FRE[.]PHP
HXXP[:]//ALPHASTAND[.]TOP/ALIEN/FRE[.]PHP
HXXP[:]//KBFVZOBOSS[.]BID/ALIEN/FRE[.]PHP
HXXP[:]//ALPHASTAND[.]WIN/ALIEN/FRE[.]PHP
HXXP[:]//CCJJLOGSX[.]COM/UU/ME/II[.]PHP
HXXP[:]//CJJLOGSX[.]COM/UU/ME/TC[.]PHP
HXXP://63[.]141[.]228[.]141/32[.]PHP
HXXP://51[.]195[.]53[.]221/P[.]PHP
172[.]67[.]143[.]169
104[.]21[.]39[.]75
63[.]141[.]228[.]141
51[.]195[.]53[.]221
