Red Akodon, a new threat actor distributing RAT to Colombia
Overview
The purpose of this report is to highlight a new threat actor that SCILabs identified and profiled during April 2024. This actor has been observed impersonating organizations, primarily government entities from Colombia. The information and indicators of compromise were obtained through threat-hunting activities, malware analysis, and intelligence processes in public and private sources.
Due to its behavior and characteristics, SCILabs named it Red Akodon. This threat actor targets users of all types in Colombia, including public and private organizations employees, to steal confidential information such as bank accounts details, e-mail accounts, social media credentials, and access to corporate portals, among others, using remote access trojans (RAT) like RemcosRAT, QasarRat, AsyncRAT, and, XWorm. Red Akodon‘s initial access vector occurs mainly using phishing emails, which are used as a pretext for alleged lawsuits and judicial summonses, apparently coming from Colombian institutions such as the Fiscalía General de la Nación and Juzgado 06 civil del circuito de Bogotá.
According to SCILabs’ research, Red Akodon has operated mainly in Colombia since April 2024, gradually increasing its activity since its first appearance. It has made small but constant changes to its infrastructure (such as its command-and-control servers or its malware download) and has used TTP to evade security solutions and make it difficult for cyber threat researchers to analyze.
Region of operation
After conducting threat hunting and intelligence processes on public and private sources, SCILabs determined with a high confidence level that Red Akodon attacks have primarily affected Colombia.
To date, no campaigns have been identified affecting another region of LATAM or the world; however, SCILabs has the hypothesis, based on experience, that it is highly likely that this threat actor will spread the distribution of its campaigns to other Latin American countries in the future.
The following map shows Red Akodon‘s main operating region (highlighted in red), and its future potential target countries (highlighted in green).
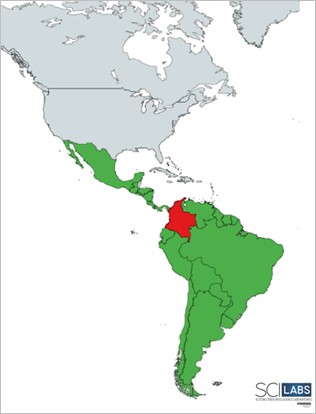
Figure 1. Red Akodon’s operating region
Below is the chronology of the most relevant activity of Red Akodon, according to the campaigns identified by SCILabs during April 2024. It is important to mention that, over time, the infrastructure and artifacts operated by this threat actor have experienced constant changes. Thus, for the following example the most outstanding activity observed so far was considered.
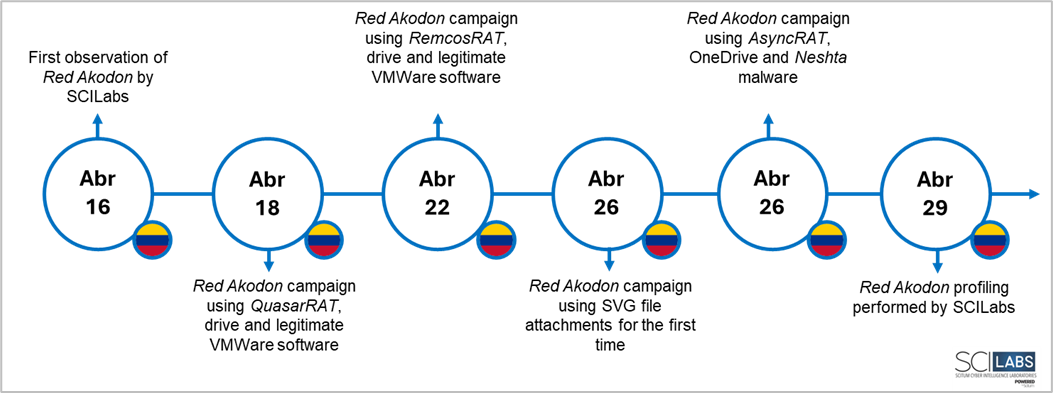
Figure 2. Red Akodon’s most relevant activity
Who is affected?
During the investigation, SCILabs identified that this threat actor’s campaigns primarily target Colombia. Although it did not appear to target any specific sector, it may affect public and private organizations of any industry, for example:
- Public organizations in industries such as:
- Government
- Health
- Education
- Private organizations in industries such as:
- Financial
- Manufacturing
- Food
- Services
- Transportation
How can this affect an organization?
Red Akodon’s main goal is to steal all types of information (including highly sensitive data from multiple users, as well as logging the activity of their keyboard, screen and mouse). The victims can be employees of any kind of public and private organizations.
Considering the information above and taking into account that the intention of this threat actor campaign intends to infect victims with Trojans which are designed for logging and tracking devices remotely, a successful attack could result in the compromise of sensitive information that could be used maliciously by cybercriminals, leaking it or selling it within clandestine forums on the Dark Web or in the black market, to then use it to carry out more sophisticated and dangerous attacks such as ransomware, which can put at risk the integrity, confidentiality, and availability of the organization’s information, not mentioning that it may cause financial and reputational losses.
Analysis
Threat context
During April 2024, through monitoring and threat-hunting processes, SCILabs identified several phishing emails aimed mainly at users in Colombia, which used an alleged lawsuit on behalf of the victim as a pretext. Two email variants were identified: the first contains a hyperlink to a DOCX-type file hosted on Drive; the second includes an attached SVG file which is also an alleged Word file, like in the first e-mail, but it is actually an image with a hyperlink inside.
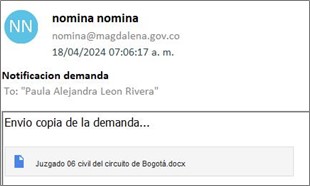
Figure 3. Mail used by Red Akodon with a malicious link
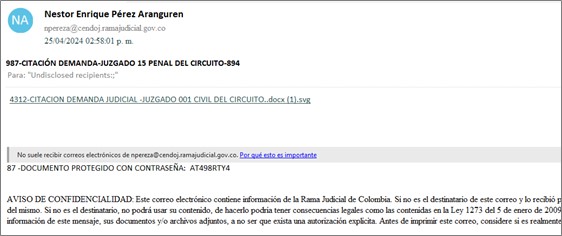
Figure 4. Mail used by Red Akadon with a malicious SVG file
It is important to mention that no email spoofing techniques were identified and that the accounts from which the phishing emails were sent have domains that belong to agencies of the Colombian government (gov.co) and legitimate companies of the same country.
SCILabs conducted an investigation and identified several posts on underground forums, where compromised credentials of domains related to the analyzed malware campaigns were found. According to these publications, the credentials were obtained through the infostealers RisePro and Vidar.

Figure 5. Post in a clandestine forum with credentials for sale of the domain magdalena[.]gov[.]co
Technical overview
First campaign identified
In the first campaign identified by SCILabs, the email contains a link with an alleged .docx file related to a lawsuit. If the user clicks on it, they are redirected to a Google Drive or OneDrive repository where a preview of an Office Word document is displayed in which more details of the alleged lawsuit are shared, and which contains a URL for downloading an additional file protected with a password (shared within the document).
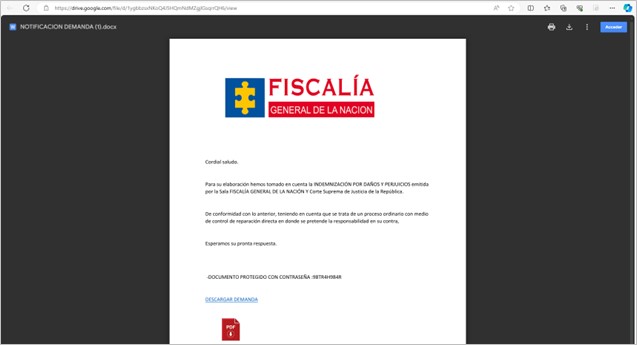
Figure 6. DOCX document formatted as a supposed lawsuit
If the user clicks on the link “DESCARGAR DEMANDA”, the download of a .zip-type compressed file from a GitHub repository begins. During the investigation, multiple active campaigns were identified in different repositories, such as advertising, filed, judicial, demand, receipt, and files.
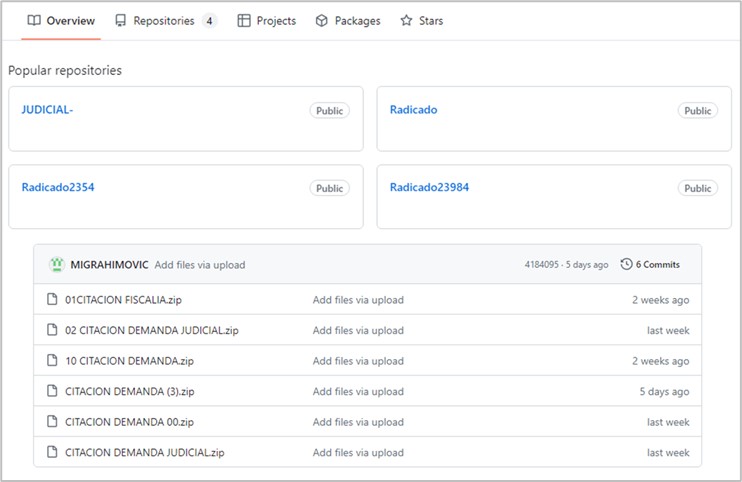
Figure 7. GitHub repositories used by Red Akadon (top) and ZIP archives stored in the repositories (bottom)
Additionally, the compressed file contains a folder with the same name, which is a directory that includes the following files:
- 01 CITACION DEMANDA.exe: VMWare Tools legitimate executable
- glib-2.0.dll: Biblioteca maliciosa encargada de inyectar AsyncRAT en el proceso MSBuild.exe
- gmodule-2.0.dll: GLib legitimate library
- gobject-2.0.dll: Glib legitimate library
- gthread-2.0.dll: Glib legitimate library
- dll: Legitimate library for the use of icons
- dll: Windows legitimate library
- dll: VMWare legitimate library
- html: HTML type file. No malicious behavior was identified during the analysis
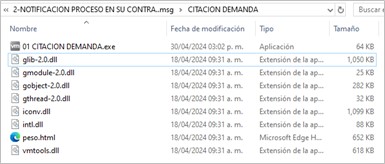
Figure 8. Content of the downloaded compressed file
In one of the campaigns identified by SCILabs, the zip file also contains a folder with a legitimate executable WinZIP; however, it was not observed to be used at any stage of the infection chain.
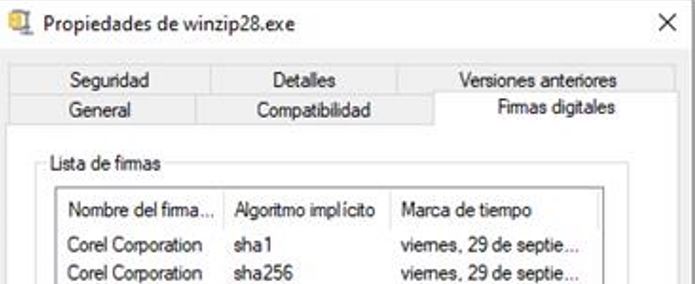
Figure 9. Digital signature of the WinZip28.exe file
If the user executes the file 01 CITACION DEMANDA.exe, the infection chain begins by exploiting a DLL-hijacking vulnerability contained in the VMWare executable to inject the AsyncRAT malware into the legitimate MSBuild.exe process. This technique has been observed in the past and documented in public investigations.
During the execution, a connection to melo2024[.]kozow[.]com was detected, and the text string “AsyncRAT Server” could be observed in the request.

Figure 10. Content of the request observed during the analysis
Furthermore, the memory of the created process identified the text string “CRACKED BY hxxps[:]//t[.]me/xworm_v2”. The URL belongs to a Telegram group where multiple RATs are distributed, including AsyncRAT, RemcosRAT, and various versions of XWorm.
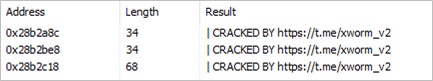
Figure 11. Strings observed in the memory of the MSBuild.exe process
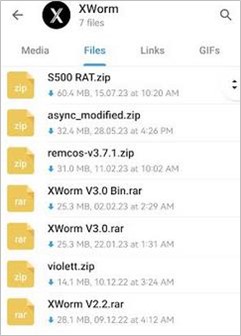
Figure 12. RATs distributed by the Telegram group
SCILabs also observed the execution of the taskkill.exe /im cmstp.exe /f command to disable UAC (User Account Control), which grants administrator privileges without user authorization.
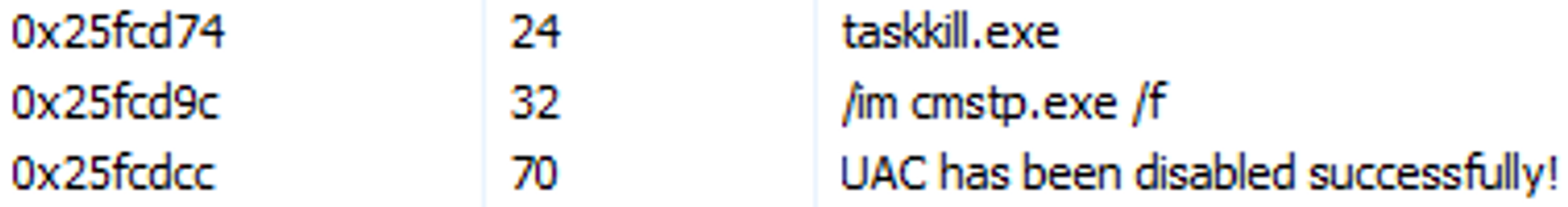
Figure 13. Command executed for UAC deactivation
The malware operated by Red Akodon executes a PowerShell script stored in C:\Users\Public to configure Windows Defender exclusions, avoiding certain processes and directories on the system and stopping the process cmstp.exe.
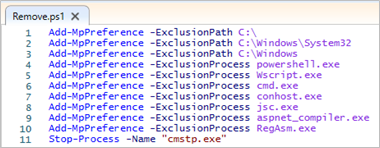
Figure 14. Script used to change Windows Defender settings
Red Akodon performs persistence generation by creating shortcuts in the Windows Start menu directory and a scheduled task that runs the legitimate VMWare file.
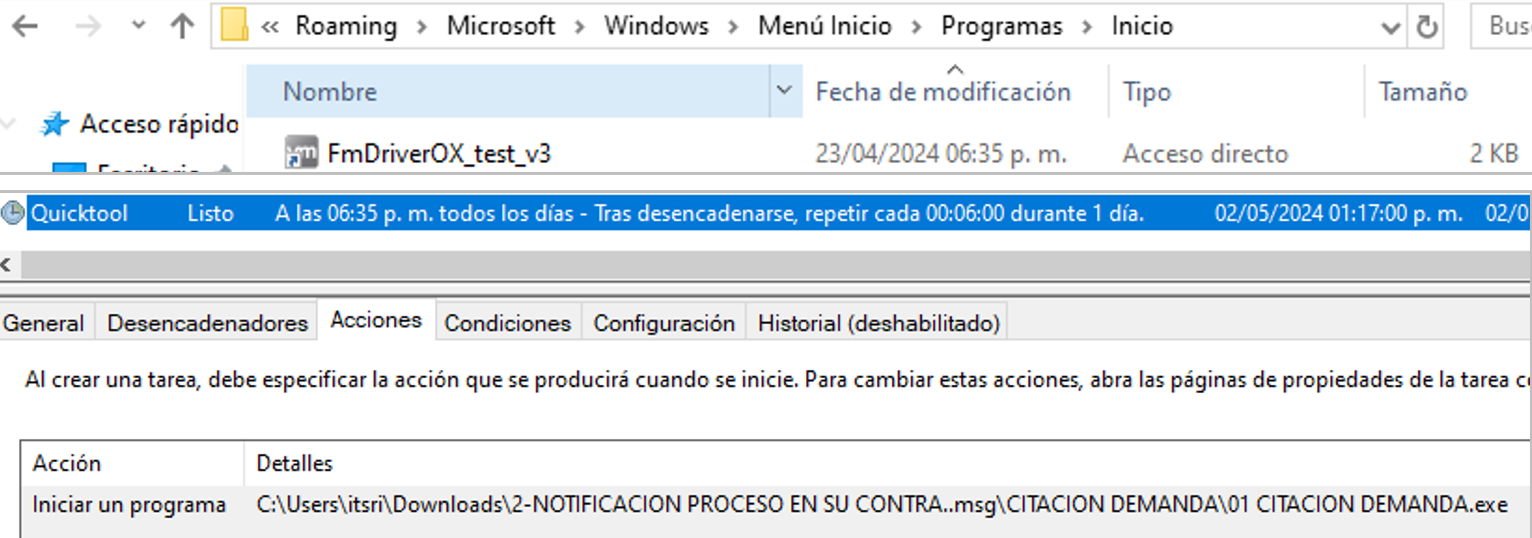
Figure 15. Persistence created in the Windows start menu (top) and task scheduled for dropper execution (bottom)
Once the AsyncRAT malware is injected into the MSBuild.exe process, it collects information from the infected computer and downloads additional Trojans. During the analysis of this campaign, the installation of the RemcosRAT and Quasar Trojans was observed.
SCILabs has the hypothesis that Red Akodon installs different Trojans to have multiple mechanisms for information theft.

Figure 16. RemcosRAT and Quasar execution
In the specific case of RemcosRAT, it is installed in the path C:\ProgramData\Remcos\, and creates a registry key to add it to the Windows Start menu.
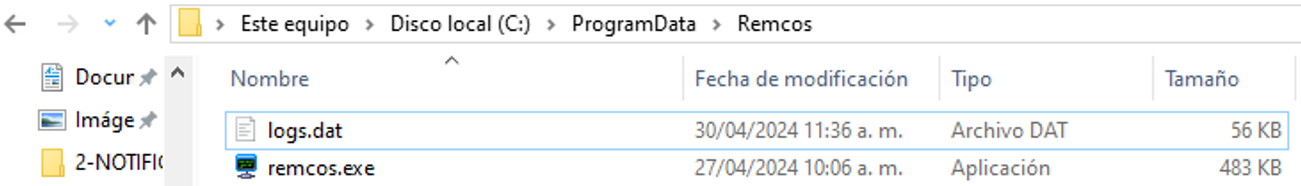
Figure 17. RemcosRAT installation path
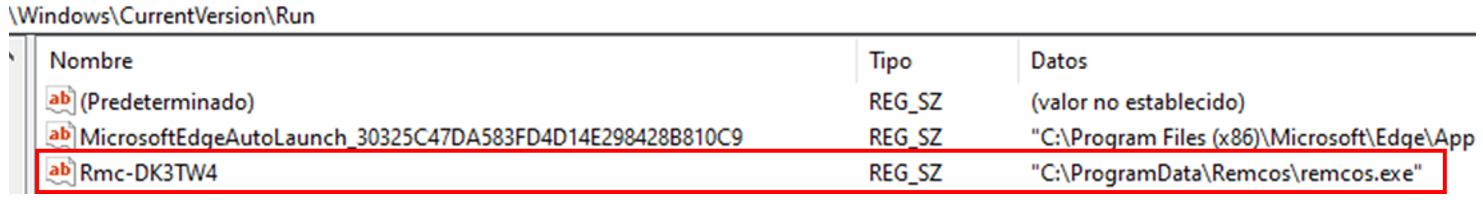
Figure 18. Registry key created for persistence
The following table shows the parameters found when analyzing the RemcosRAT samples installed in this campaign.
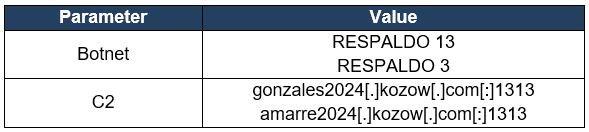
Table 1. RemcosRAT parameters
On the other hand, Quasar is stored in %TEMP%; however, no persistence methods were identified for this malware. SCILabs hypothesizes that the execution is triggered from the MSBuild.exe process since there are text strings in the process memory with the path of this executable.
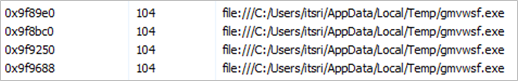
Figure 19. Strings found in the process MSBuild.exe
The following table shows the parameters when analyzing the Quasar samples installed in this campaign.
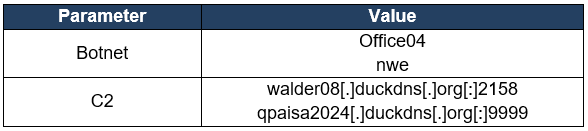
Table 2. Quasar parameters
In addition to installing the Trojans, there is a download of multiple artifacts which seem to be legitimate files but contain the Neshta malware. This malware aims to modify sections of an executable file and load malicious code. The executable is stored in C:\Windows with the name svchost.com and creates a registry key that tells the system to run the Neshta artifact every time an EXE-type file is opened. When a program is executed, the original file is sent to the path %TEMP%\3582-490.
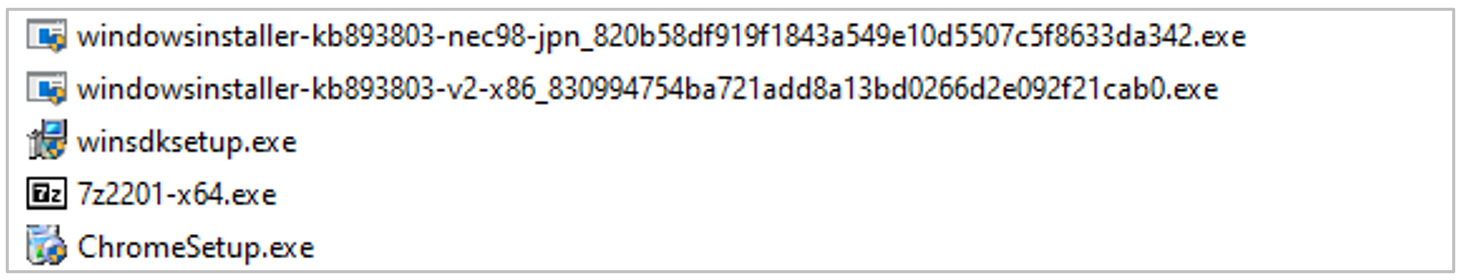
Figure 20. Neshta artifacts downloaded during infection

Figure 21. Registration key created by Neshta
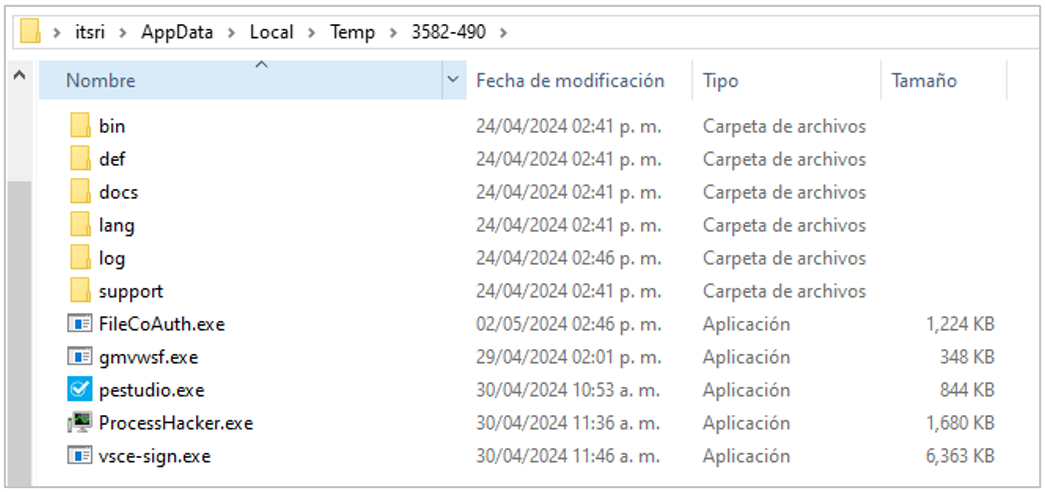
Figure 22. Directory where the original executables are stored after their sections were modified
The IObit Unlocker software installation was also observed in path C:\ProgramData\IObitUnlocker. This program offers file management functionalities, such as deleting, renaming, moving, and copying any file, regardless of whether another program uses it. Yet, it is important to mention that some security solutions on VirusTotal classify this software as a PUA (Potentially Unwanted Application).
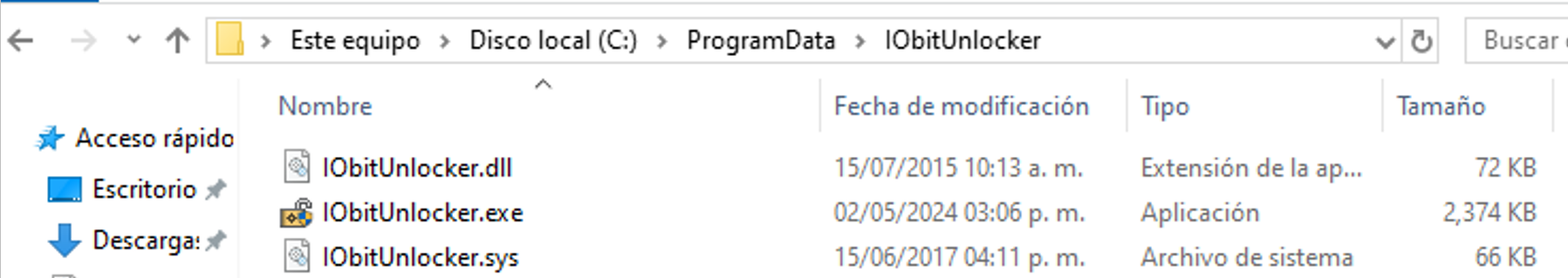
Figure 23. IObit Unlocker installation path
Second campaign identified
In the second campaign identified by SCILabs, the email contains an SVG file that seems to be an alleged document of a lawsuit from the Fiscalía General de la Nación of Colombia. Like in the first campaign, the image contains a URL: if the user clicks on it, they are redirected to a GitHub repository from where the download of a compressed file begins.
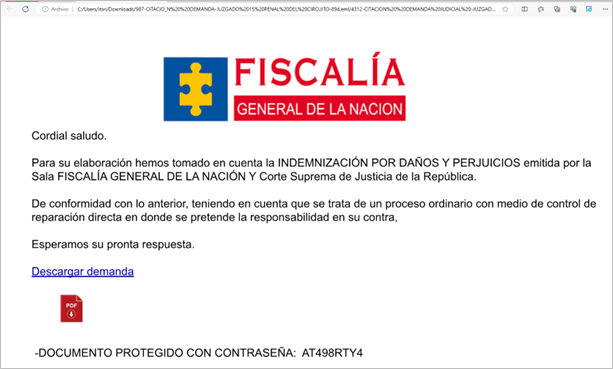
Figure 24. SVG file with the alleged lawsuit
Additionally, the compressed file contains a folder with the same name, which is a directory that includes the following files:
- 04 CITACION DEMANDA.exe: Neshta executable file
- dll: Malicious library responsible for injecting AsyncRAT into the MSBuild.exe process
- dll: ASUS legitimate library
- dll: ASUS legitimate library
- eps: Unknown file, no malicious behavior detected during analysis
- ai : Unknown file, no malicious behavior detected during analysis
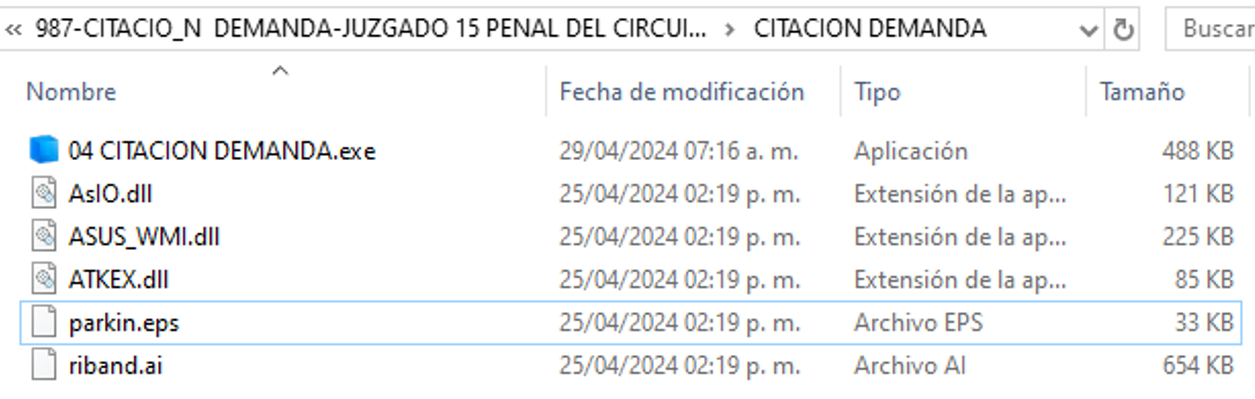
Figure 25. Contents of the compressed file
If the user executes the file 04 CITACION DEMANDA.exe, the infection chain described above begins. It is important to mention that during the analysis, no additional downloads of the Neshta malware were identified as in the first campaign analyzed. Hence, SCILabs hypothesizes that this activity is not carried out in this campaign because the dropper is a variant of Neshta and already fulfills that function.
Attack flow summary
- The user receives a phishing email from a compromised account belonging to the gov. codomain, using alleged lawsuits and court summons as pretexts.
- The email contains an attached SVG file, a OneDrive or a Google Drive hyperlink.
- If the user opens the SVG file, they are shown an alleged lawsuit or judicial summons that appears to come from the Fiscalía General de la Nación or from a Colombian court.
- If the user clicks on the hyperlinks, they are redirected to a Google Drive or OneDrive repository (as the case may be) containing the supposed lawsuit or judicial summons allegedly coming from the Fiscalía General de la Nación, or any Colombian court.
- If the user clicks on “Descargar una copia de la demanda” (Download a copy of the lawsuit) they are redirected to a GitHub repository to obtain a compressed file in ZIP or 7ZIP format.
- If the user unzips and executes the contents of the previous file, the malicious activity begins.
- Red Akodon injects a variant of AsyncRAT into the legitimate Windows MSBuild process, by exploiting DLL-Hijacking vulnerabilities in legitimate artifacts mainly related to VMWare, or the Neshta malware that pretends to be a legitimate software.
- Red Akodon generates persistence using shortcuts in the Windows start menu.
- Red Akodon downloads and installs one or more remote access Trojans.
- The RAT begins tracking and logging the keyboard, and screen activity, obtaining all kinds of information from the victim.
- The stolen information is shared with the attacker’s command and control server.
- Finally, the attacker can install remote administration tools and perform other tasks, such as downloading additional artifacts and restarting the computer.
Attack flow diagram
The following attack flow was observed by SCILabs from malware analysis.

Figure 26. Diagram of the attack flow identified by SCILabs
TTP observed aligned to MITRE ATT&CK® Framework
The following TTP matrix based on the MITRE Framework was obtained from malware analysis and intelligence processes in open sources.
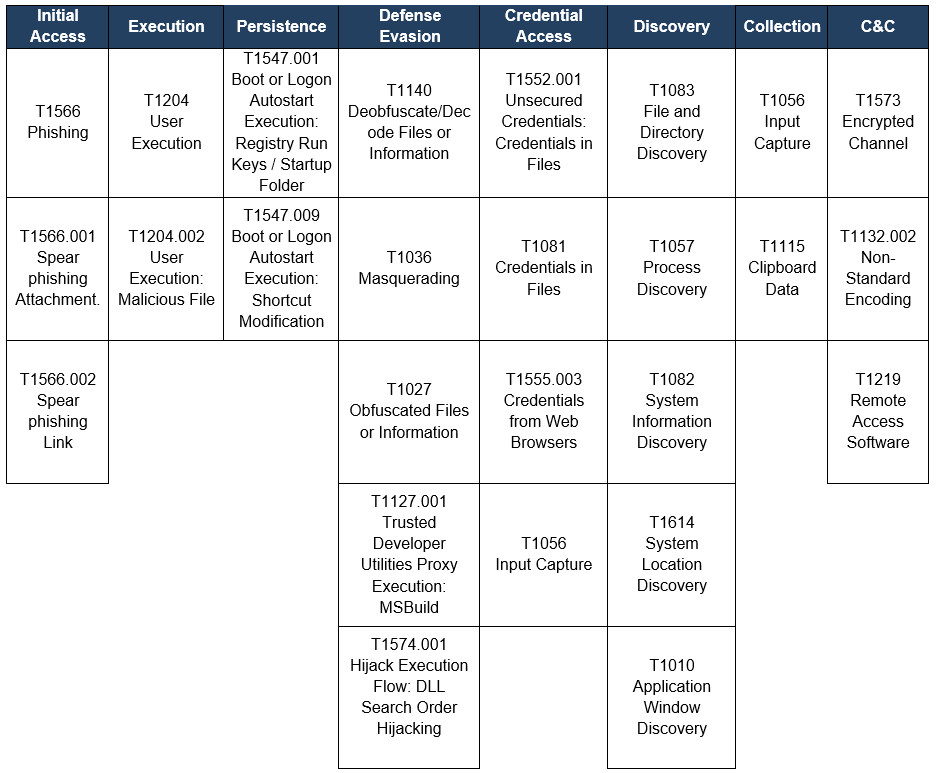
Table 3. TTP observed aligned to the MITRE ATT&CK® framework
Diamond model
The following diamond model was obtained from the malware analysis and intelligence processes in open sources.
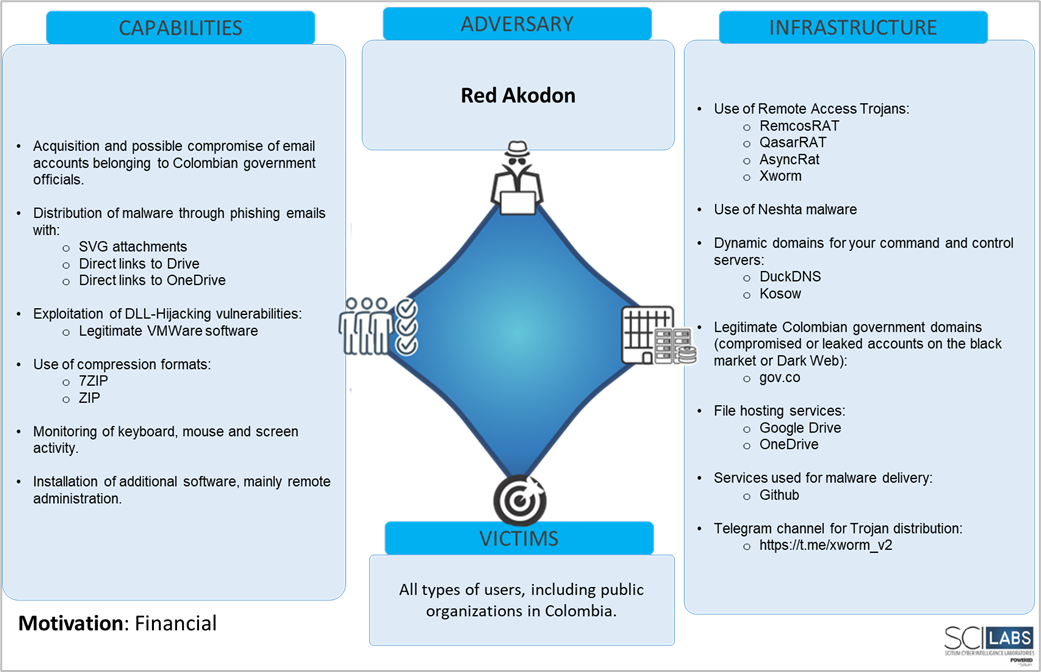
Figure 27. Diamond model identified by SCILabs
Attribution
To make the corresponding attribution and determine with a high level of confidence that this is a new threat actor, SCILabs conducted an in-depth investigation looking for overlaps with other known threats, particularly with APT-C-36 and TA558, which are highly active threat groups in Colombia.
Below is a table with the characteristics of the different threats identified by SCILabs and aligned to the diamond model, whose overlaps with APT-C-36 are highlighted in red and with TA558 in green.
| Adversary/Diamond Model | TA558 | APT-C-36 | Red Akodon | |
| Infrastructure
|
Dynamic domains for their command-and-control servers, primarily DuckDNS | Yes | Yes | Yes |
| Dynamic domains for their command-and-control servers, primarily Kozow | No | Yes | Yes | |
| Legitimate Colombian government domains (accounts compromised or leaked in the black market or Dark Web), mainly gov.co | No | No | Yes | |
| File hosting services, mainly Drive | No | No | Yes | |
| File hosting services, mainly OneDrive | No | No | Yes | |
| Services used for malware delivery, mainly GitHub | No | No | Yes | |
| Telegram channel for obtaining/distributing malware | No | No | Yes | |
| Patterns in the domains of their command-and-control servers, mainly, gonzalez2024, melo2024, qpaisa2024, quepasa2024 | No | No | Yes | |
| Capabilities | Distribution through phishing e-mails | Yes | Yes | Yes |
| Use of Remote Access Trojans, among which we find RemcosRAT, QasarRAT, AsyncRAT y XWorm | Yes | Yes | Yes | |
| 7ZIP and ZIP compression format | Yes | Yes | Yes | |
| Keyboard, mouse, and screen activity monitoring | Yes | Yes | Yes | |
| Installation of additional software, mainly remote administration software | No | No | Yes | |
| Exploitation of DLL-Hijacking, mainly in legitimate VMWare products | No | No | Yes | |
| Use of Neshta malware | No | No | Yes | |
| Use of scripting for first droppers (JS, VBS) | Yes | Yes | No | |
| Victim | So far, only campaigns targeting Colombia have been identified | No | No | Yes |
Table 4. Overlaps between APT-C-36, TA558 and Red Akodon
As a result of the investigation, it can be observed that out of 17 characteristics attached to the diamond model, overlaps were found only in 6, of which 3 (ZIP and 7ZIP files, phishing emails, and dynamic domains) are usually used by different threats in the region, including banking Trojans, for instance. SCILabs can determine with a high level of confidence that this is a new threat actor.
Conclusions
SCILabs considers that the danger of Red Akodon lies in multiple factors, among which the following stand out:
- Constant modification of its infrastructure, making it difficult for researchers to track the malware activity operated by this threat group.
- Constant creation of malware repositories, which makes the task of obtaining samples, blocking indicators of compromise, etc. complicated.
- The use of Trojans with public source code, which allows them to easily make modifications to their artifacts.
- The use of multiple remote access Trojans could increase the effectiveness of one of their attacks by generating multiple infections at the same time.
- The use of the DLL-Hijacking technique exploits vulnerable applications, making detection difficult for malware analysts and security solutions.
- The use of Neshta malware to infect EXE files.
- The use of legitimate hosting services.
- Implementation of geofences, which ensure that their victim belongs to a specific region.
Having said the above and based on the capabilities set forth in this report, Red Akodon should be considered a potential threat to all companies and organizations, mainly in Colombia, although it is important to mention that as a consequence of the exponential increase in its activity and its rapid creation of a variety of campaigns it is highly likely to affect other countries in the LATAM region in the future.
SCILabs will continue to monitor the activity of this threat actor and provide IOCs accordingly to strengthen the security of our clients. Additionally, we make the following recommendations to avoid being victims or, where appropriate, to reduce the impact of a Red Akodon infection:
- Block the IoCs mentioned in this document.
- Conduct awareness campaigns on the techniques used by this threat actor.
- Have strict policies regarding the use and installation of software on corporate computers, mainly utilities related to VMWare, exploited by Red Akodon.
- For phishing emails, it is recommended:
- Avoid opening emails from unknown senders.
- Avoid opening suspicious links.
- Avoid opening or downloading suspicious files.
- Keep the operating systems and software of all devices on your network up to date.
- Carry out correct implementation of policies for the creation and use of passwords.
- Avoid storing passwords in browsers.
- vestigate leaks of information, credentials and data related to your organization through intelligence services.
- Have a correct implementation of In-Depth Security in all the organization’s systems.
- If they are not essential for the organization’s operation, block free DNS services such as duckdns[.]org and kozow[.]com.
- Perform threat hunting tasks looking for suspicious shortcuts, primarily in the Windows Start Menu directory.
- Pay attention to alterations on your devices, for example, a double cursor, pop-up screens, among others.
Indicators of compromise
Below, with a HIGH level of confidence, are the indicators of compromise (IoCs) obtained from the analysis carried out by SCILabs.
SHA256
30C835EA23ED533816533C0FABF62811007140CF84F9610E9F9B42F9A30539FE
C0747C10BE35B8C1072A360C7759228B17F35D2EC890154020C716D572B00FBD
174FA8BB281AD832A5CBC6132E5D16E71C951CEB8F505C305F5D6816E6F75BBE
78576AAAEA61227E3EA0AA5311D72878630E83B04CBDBCE436D7CC119749A428
06D966537F2236E4ECC8F4BA62070398980CF42D74971B47D0018DD8089C3A15
675A60B1C6C7F593C96EA6787D961B6ABD32FE644D1A23A2FF32BEC785EA1DA1
CC419B8CC78BBF52A96E33142C99E129A96D2E83C5E9D23AF7F041BEE803D324
8DC7FA88285ED5466962A8A6F04941DC23D3F5D11398BD33ECB80973189F1A98
665B8F7B2013BC20C6A31F3448C0EC321D17B214629ACCE7405039009DC1C519
27EBF2AF9882393EC6C1EBD17A32C607B08337D419AD93692B9CB44BA54C47CC
7D5B81FA1ADD7DF447EB4A9BE6618C60317C0F11A5AE6A0479451A8FABDB88CA
328BB9FED9B3A2071E504361C6719361192D273D4CF202A3C8D6551C385A70A7
5B72922A652FCD91508E1F6ED54C2936731D5B31A7A0DA1F4289AA822E9AB282
406F0C9C379AC28F1135D8C2AEA49D5105782631CBF5259800E19B93813412C4
C858874090BE999F9EC6C851EF5511829E44DF29E37EDEF7012FB7DD6A6A5884
5C15C27C7C6D942ABBBADACE26B8C3C06F63DCEB474287D39CD561548B274685
70D7598B80ACBB5EDD8913718C5D94EF98AF00FCE9726048FE72235EB1AAA47E
3795B2AAA4D61C30528C897DD02D610E3C1734C6BBC093A932381E7FA58D0CA6
AD7A0816DFC4F551CFB5122388FAB2418D2822DEDA4A55E59DBC95E037EF8305
Malware download URL
It is recommended to block the entire URL to avoid future false positives or operation failures. hxxps[:]//drive[.]google[.]com/file/d/1ygbbzsxnkoq4j5hqmndmzgjlgsqrrqh6/view?usp=drive_web
hxxps[://]drive[.]google[.]com/file/d/1a8ju99cr4eaybnlgcztcxfswtltdjn-p/view
hxxps[://]onedrive[.]live[.]com/?redeem=aHR0cHM6Ly8xZHJ2Lm1zL2IvYy8xMTliNTFhOWU4ZWU2OGE1L0VWNHlzdWhYcGR0S3FTdThnUDRzakprQlk1ZWZlaTlqamNoT05NaGxwcG9xUVE&cid=119B51A9E8EE68A5&id=119B51A9E8EE68A5%21se8b2325ea5574adba92bbc80fe2c8c99&parId=root&o=OneUp
hxxps[:]//github[.]com/santiagonasar/publicidad2/raw/main/citacion%20demanda[.]zip
hxxps[:]//github[.]com/colombo08125/publicidada2024/raw/main/citacion%20demanda%2004[.]zip
hxxps[://]github[.]com/jairpicc/demanda/raw/main/demanda%20virtual[.]7z
hxxps[://]github[.]com/mastermr02456/radicado23984/raw/main/citacion%20demanda[.]zip
hxxps[://]raw[.]githubusercontent[.]com/santiagonasar/PUBLICIDAD2/main/CITACION%20DEMANDA[.]zip
hxxps[://]raw[.]githubusercontent[.]com/mastermr02456/Radicado23984/main/CITACION%20DEMANDA[.]zip
hxxps[://]raw[.]githubusercontent[.]com/mastermr02456/JUDICIAL-/main/Notificacion%20Judicial%20854651[.]Tar
hxxps[://]raw[.]githubusercontent[.]com/mastermr02456/Radicado2354/main/CITACION%20JUDICIAL[.]zip
hxxps[://]raw[.]githubusercontent[.]com/mastermr02456/Radicado/main/Radicado_juridico_2141744[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/CITACION%20DEMANDA%2004[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/02%20CITACION%20JUDICIAL%20DEMANDA[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/CITACION%20DEMANDA%2001[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/CITACION%20DEMANDA%20JUDICIAL%20JUZGADO%20007%20CIVIL%20DEL%20CIRCUITO[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/CITACION%20DEMANDA%20JUDICIAL[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/CITACION%20DEMANDA[.]zip
hxxps[://]raw[.]githubusercontent[.]com/colombo08125/publicidada2024/main/CITACION%20JUDICIAL%20DEMANDA[.]zip
hxxps[://]raw[.]githubusercontent[.]com/MIGRAHIMOVIC/MIGRAHIMOVIC/main/-%20PROCESO%20DEMANDA[.]REV
hxxps[://]raw[.]githubusercontent[.]com/MIGRAHIMOVIC/MIGRAHIMOVIC/main/10%20CITACION%20DEMANDA[.]zip
hxxps[://]raw[.]githubusercontent[.]com/MIGRAHIMOVIC/MIGRAHIMOVIC/main/CITACION%20DEMANDA[.]zip
C2
gonzales2024[.]kozow[.]com[:]1313
amarre2024[.]kozow[.]com[:]1313
melo2024[.]kozow[.]com
quepasa2024[.]kozow[.]com

