Threat Profile: Ransomhouse

Objective
The objective of this document is to present available information about the RansomHouse threat actor. To that purpose, the data and the Indicators of Compromise within were gathered by SCILabs through intelligence processes in open sources, monitoring tasks, and dedicated threat hunting in the region during the first and second weeks of November 2023. Furthermore, detailed descriptions of the TTP, and tools used by this cybercriminal group are provided.
General overview
The RansomHouse threat actor has been active since December 2021, and has become relevant for having carried out attacks on large companies such as AMD, ADATA , and IFX Networks: the latter is known for having had the major impact in LATAM.
According to their leak site and their Telegram channel, the members of RansomHouse are dedicated to find security flaws in computer systems; however, instead of reporting them as ethical hackers would do, they take the opportunity to extract the information and then request ransom payment, which according to public investigations can reach amounts close to 4.5 million euros.
The victims of this threat actor have not revealed many details because, according to their posts, most intrusions are personalized attacks. However, according to the information analyzed by SCILabs, some of the vulnerabilities that the group exploits are in Google Chrome (CVE-2023-4863 ), MacOS (CVE-2023-41064 and CVE-2023-41061) and ESXi (CVE-2023-20867 ).
RansomHouse only encrypts the information if the ransom demands are not met. It was possible to identify that they use variants of the Babuk ransomware that mainly seek to encrypt virtual machines on Linux (ESX). Also, it is worth mentioning that the code of that ransomware was leaked in 2021 (also the year RansomHouse emerged) on a Russian forum.
Some of the Babuk ransomware variants observed in attacks by RansomHouse are WhiteRabbit and MarioLocker, both considered Ransomware-As-a-Service (RaaS).
With a high confidence level, according to SCILabs’ hypothesis, the threat actor engages in opportunistic attacks, indicating a lack of preference for a specific sector or location. This approach allows them to achieve broader reach and maximize their chances of success.
Region of operations
As a result of the OSINT processes and the analysis of the artifacts, SCILabs determined, with a high level of confidence, that the RansomHouse´s victims are from Germany, Australia, Belgium, Canada, China, Colombia, United Arab Emirates, Spain, United States, Philippines, India, Indonesia, Italy, Maldives, United Kingdom, San Cristobal y Nieves, Singapore, South Africa, Sweden, Taiwan and Vanuatu, and it has international presence
The following map shows in red the countries that have had most of the security incidents (18) related to RansomHouse, in orange those that have been moderately affected (between 7 and 8 attacks) and finally, in yellow, the locations that have only been victims 1 or 2 times by this threat actor.
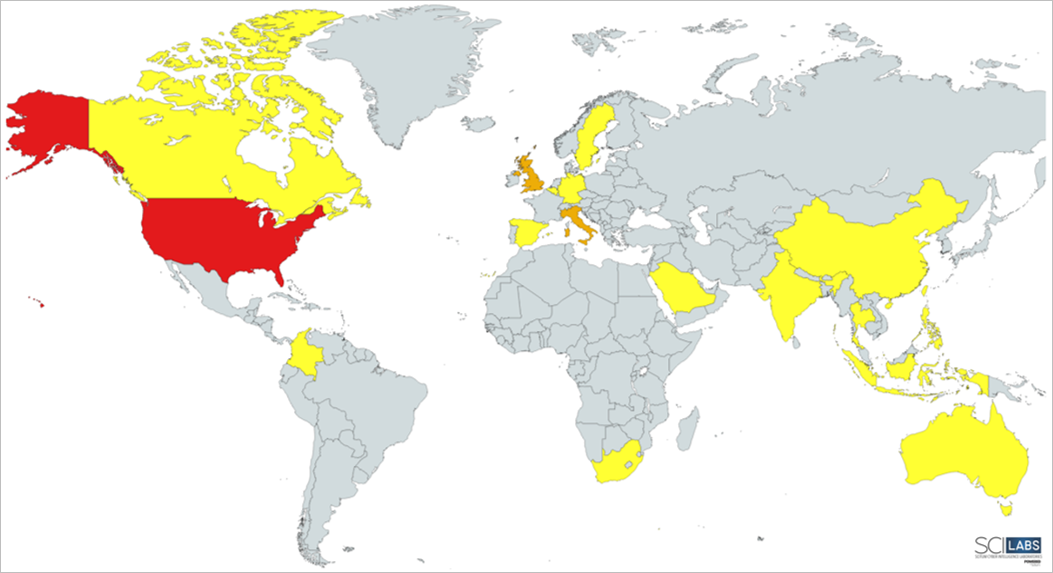
Figure 1. RansomHouse confirmed attacks by region
In Latin America the most affected country by this group was Colombia (with two confirmed attacks), and internationally, the United States is the nation that has suffered the most ransomware attacks orchestrated by RansomHouse, with a total of 18, followed by Italy with 8 attacks and the United Kingdom with 7 attacks.
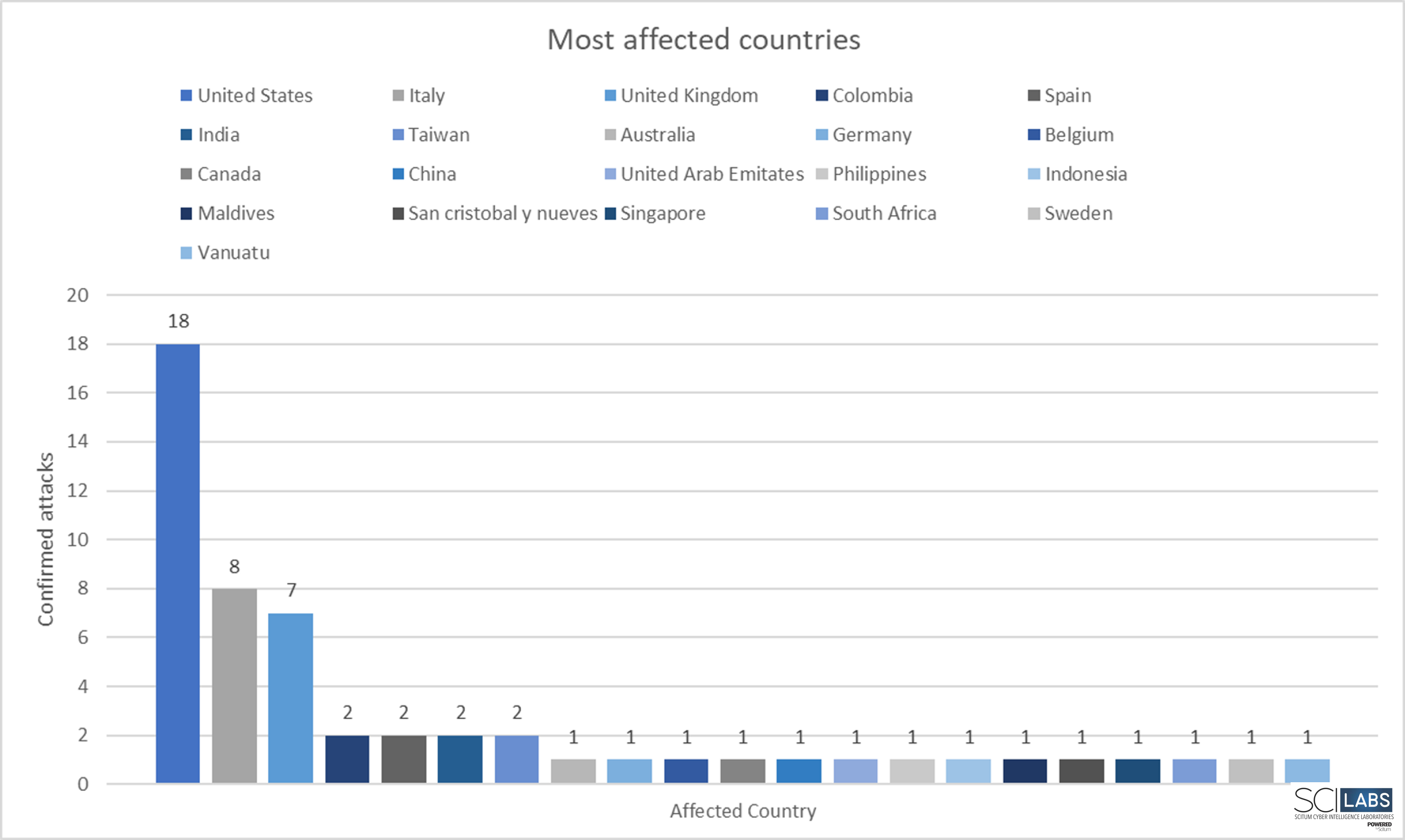
Figure 2. RansomHouse confirmed attacks by country
Below is a timeline with the most relevant activity (large-scale events or events with great media impact) of RansomHouse based on SCILabs telemetry, along with various posts from the attackers’ leak blog, since its appearance in December 2021 to September 2023.
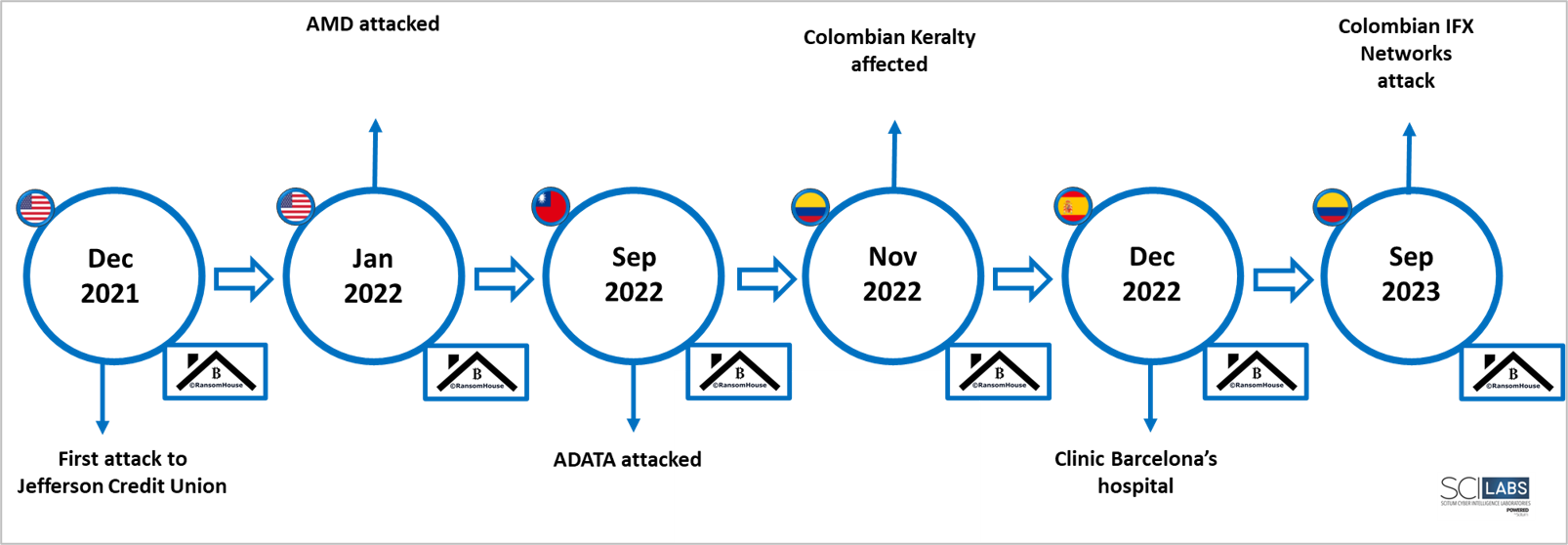
Figure 3. Most relevant attacks by RansomHouse
It is essential to mention that, although the attacks shown above are the most relevant, they are not the only ones perpetrated by RansomHouse. According to SCILabs telemetry, there are currently at least 55 organizations, public and private that have been victims. This threat actor has had its most productive period in 2023 (31 attacks in 2023, 22 attacks in 2022, and 2 attacks in 2021) since its inception in 2021.
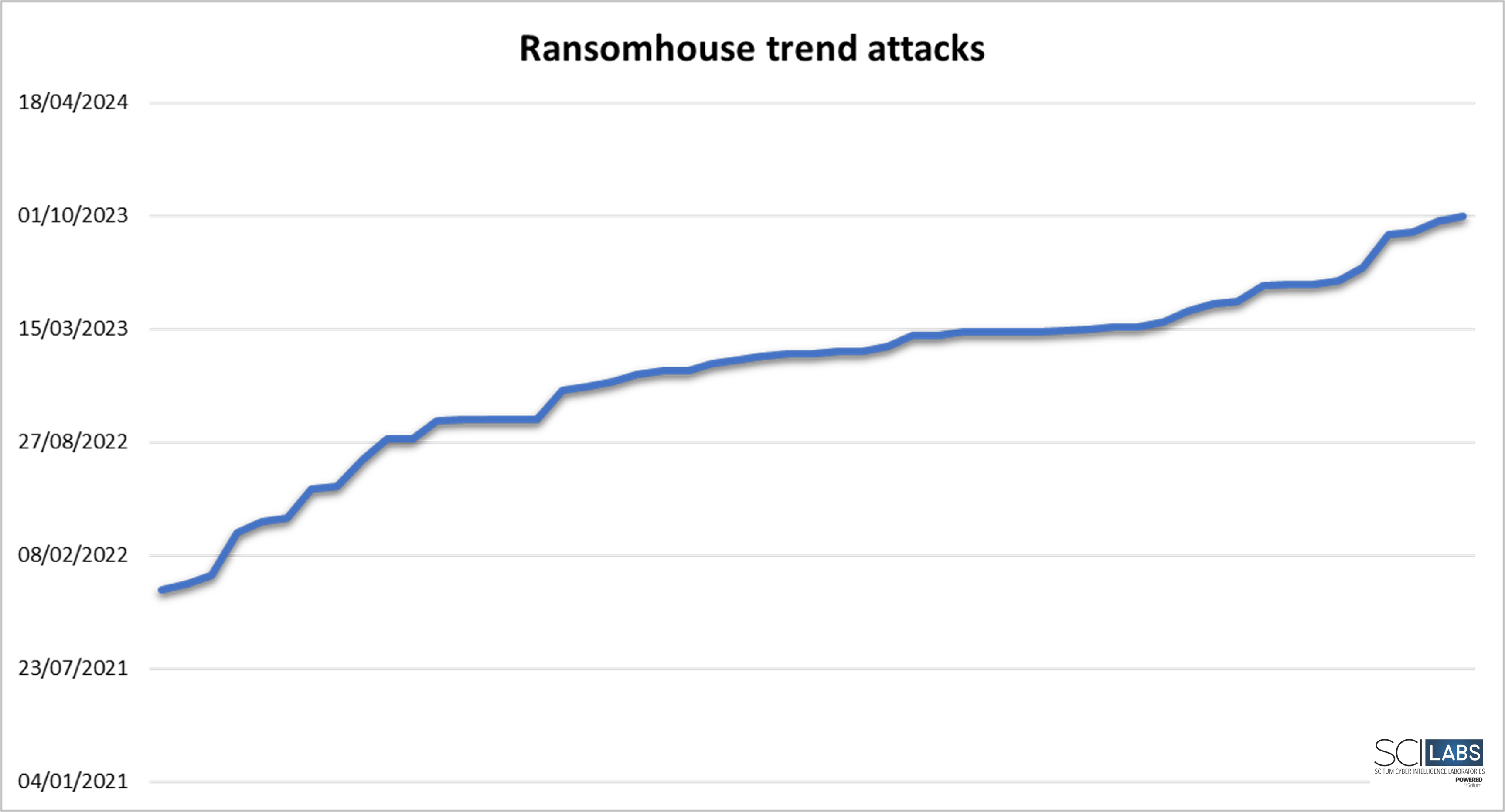
Figure 4. Trend attacks of RansomHouse
Who can it affect?
During constant monitoring of the region, SCILabs identified that RansomHouse attacks are directed at organizations of all types in different industries such as: health, retail, education, services, construction, transportation, and technology. Telemetry indicates that the most affected sector by this ransomware is health, followed by services and technology.
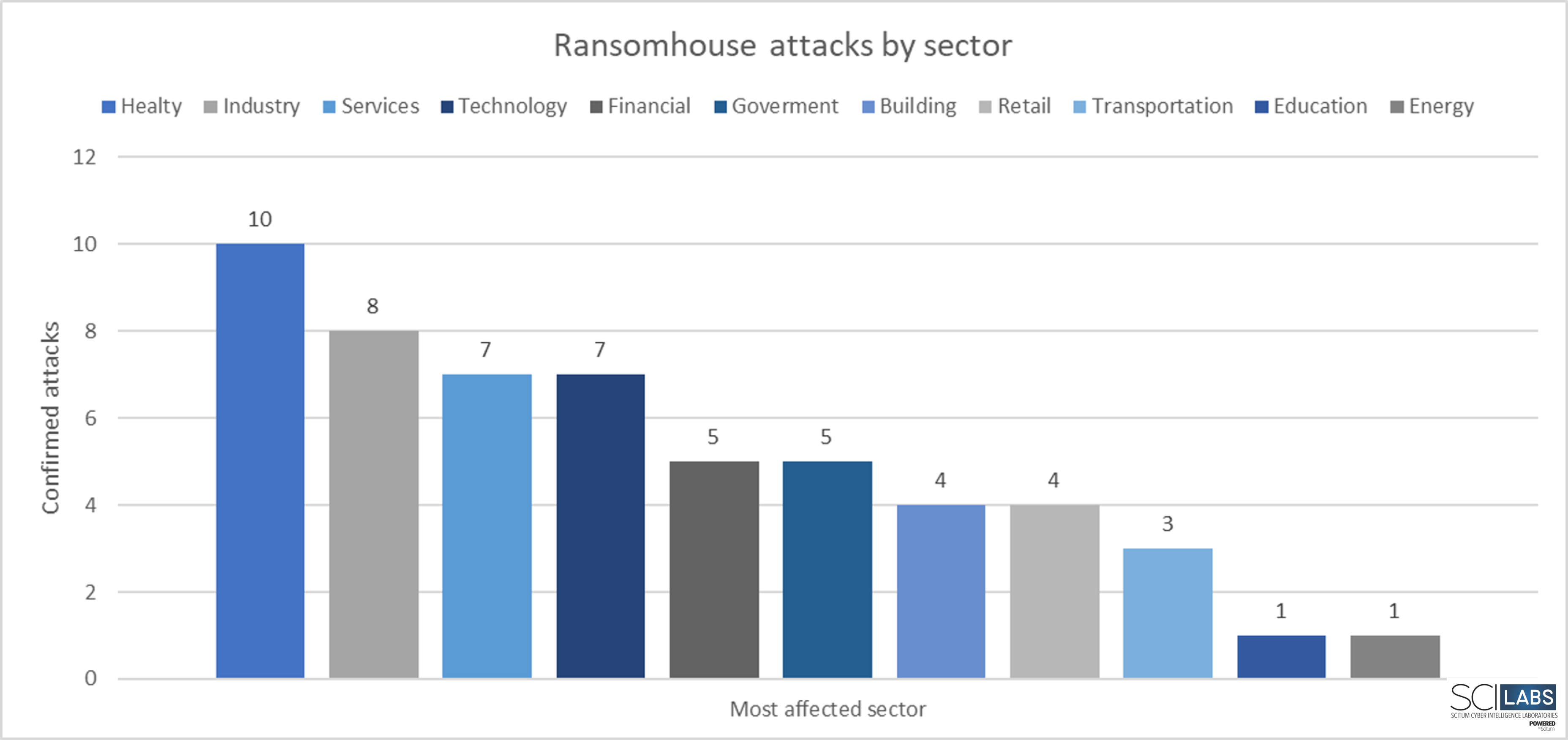
Figure 5. RansomHouse attacks by affected sector
How can it affect an organization?
If a RansomHouse attack is successful, the threat actor could steal, leak, and encrypt information of all types from victim organizations, disrupting operations that cause financial loss, compromise of sensitive data, as well as loss of reputation and trust in the organization. Therefore, organizations must be aware of this threat actor’s TTP (Tactics, Techniques, and Procedures) to minimize the probability of being infected and know how to act if RansomHouse compromises them.
Analysis
Threat context
Despite not being a new threat actor (active since 2021), as of this document’s creation date, no research has yet been made public that describes the full range of behavioral and tools that RansomHouse uses during its infection chain. However, SCILabs analyzed all the information available about this threat actor campaigns, artifacts, and TTP, resulting in the following summary:
- Initial access: In some of their attacks, RansomHouse has used phishing e-mails as the main entry method. However, it is common for them to gain access to corporate environments by exploiting vulnerabilities such as CVE-2023-4863, CVE-2023-41064 and CVE-2023-41061, which, when exploited, can allow an attacker to execute remote code. They also use non-interactive sessions to bypass multi-factor authentication (MFA) and exploit CVE-2023-20867 vulnerabilities to gain access to VMware virtual machines.
- Access to credentials: The operators of this ransomware use the following applications to steal credentials.
-
- ProcDump: This application, created by SysInternals, performs memory dumps from lsass.exe process (applicable only on Windows).
- Mimikatz: This is used to perform Pass the Hash attacks and to extract clear text credentials obtained via memory dump made by ProcDump or its dump module.
- Persistence: To generate persistence, attackers carry out a DCSync attack, a well-known credential dump technique that allows attackers to obtain sensitive information from the Active Directory database. This technique also helps attackers simulate the replication process from a remote domain controller (DC) and requests credentials from another DC credential collection, in addition to exploiting vulnerabilities CVE-2022-42475, CVE-2023-20269, which can allow the attacker to access via VPN.
- Discovery: RansomHouse exploits the CVE-2023-3519 vulnerability to deploy a WebShell in victims’ non-productive environments and perform discovery in the active directory.
- Lateral movement: By collecting domain controller credentials, they abuse remote services such as Secure Shell (SSH) and RDP to perform lateral movements.
- Impact: Attackers steal sensitive data from victims to encrypt it later if the attackers’ demands are unmet. They post the stolen data on their leak site and threaten to sell it to other groups.
Artifacts analysis
During the third week of October 2023, through constant monitoring and threat hunting in LATAM, SCILabs identified three ransomware samples based on the Babuk ransomware encryption source code, which according to our analysis and public investigations, are related to RansomHouse.
Babuk Cryptor (Linux variant)
- File type: SCILabs identified that the recovered file is a Babuk ransomware encryption source code, corresponding to an ELF-type executable for Linux compatible with 64-bit systems.
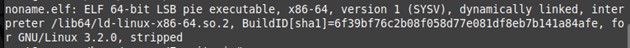
Figure 6. Babuk ransomware encryption source code properties
- Libraries used: During the static analysis of the sample, SCILabs identified some functions and libraries that are part of the C and C++ standard libraries. These libraries provide capabilities related to file management, processes, and others described in Annex II of this document.
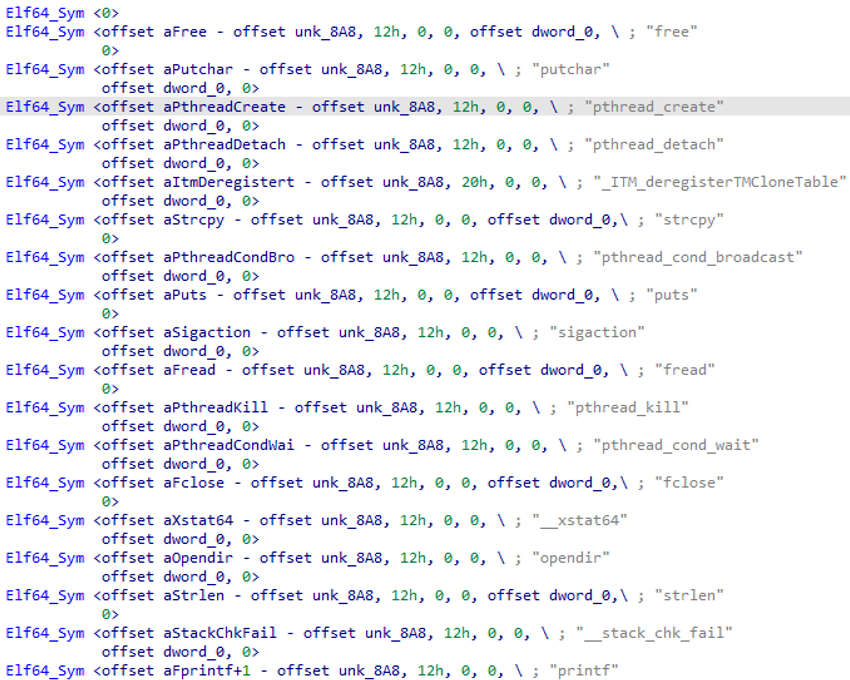
Figure 7. Babuk cryptor libraries (Observed by static analysis)
- Parameterized execution: Through the malware analysis, it was possible to identify that for the correct execution of the file it is necessary to give the directory in which the files will be encrypted as a parameter.

Figure 8. Babuk parametrized execution
- Searched files: Through the malware analysis, it was identified that the artifact focuses on encrypting files that have the following extensions, among which can be found database files and virtual machine files, besides many others.
| Filetype | Filetype | Filetype |
| .XVGV | .dump | .vab |
| .backup | .dmp | .zip |
| .nvram | .vmx | .rar |
| .vmdk | .vbk | .sql |
| .vmdx | .vbm | .log |
| .vmxf | .vrb | .vib |
| .vmsd | .vlb | .gz |
| .vmss | .vob | .wt |
| .vmem | .vsm | .vmsn |
| .vswp | .vsb |
Table 1. Babuk extensions to encrypt
- Encryption extension: In the case of Babuk, the extension used to encrypt the victim’s files is “.XVGV”.
Figure 9. Original files
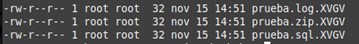
Figure 10. Files after Babuk execution
- Specifications at the end of the execution: It was identified that statistics related to the encrypted files are displayed at the end of the execution of the Babuk cryptor.
-
- Name of the encrypted files
- Files that were already encrypted before execution
- Number of files that have been encrypted
- Number of files that have been skipped
- Total of files contained in the directory.
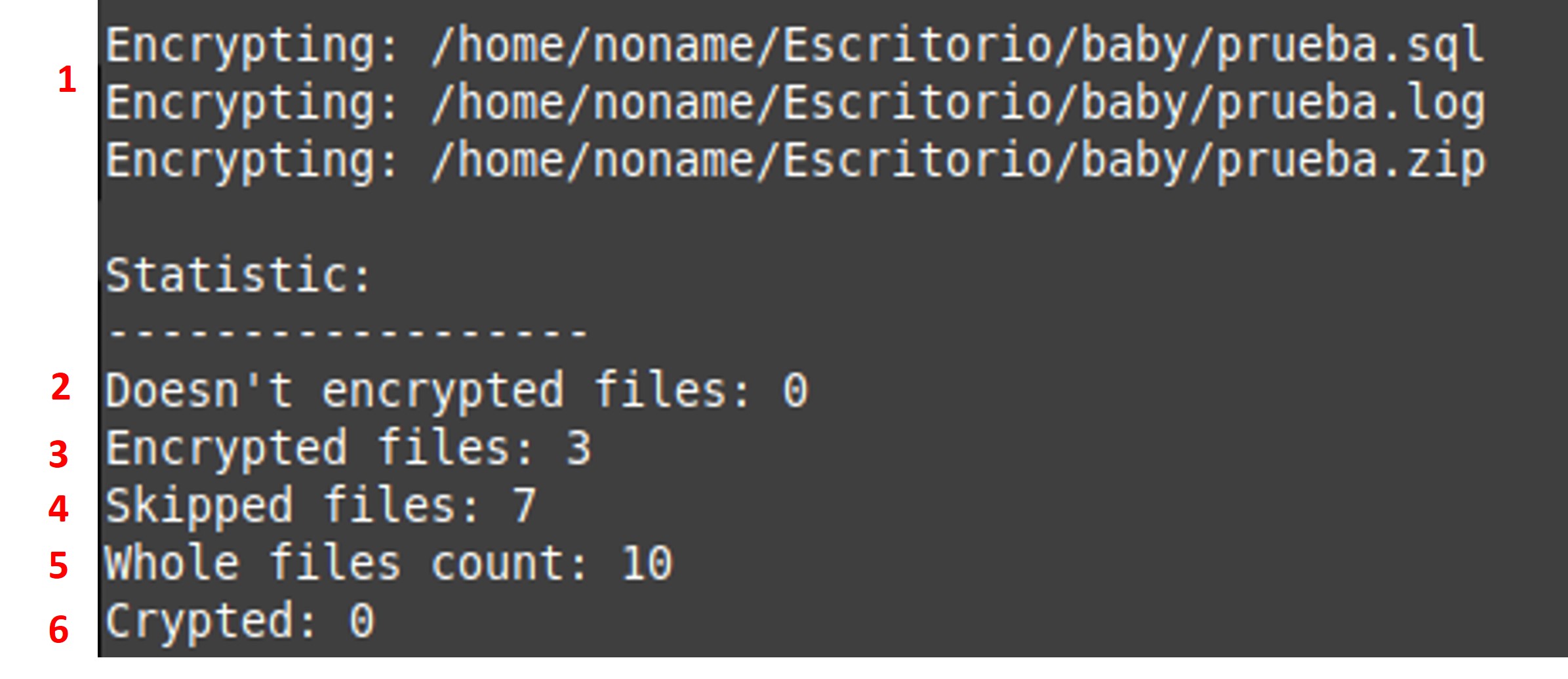
Figure 11. Result shown by Babuk cryptor
- Ransom notes: When the execution of the artifact finishes, in addition to displaying the statistics of the encrypted files, the ransom note is created. In this case, the file’s name is HowToRestore.txt, and it is in all the subdirectories in the previously specified folder (at execution).
The ransom note tells the user that their security has been breached and that more than 500GB of information has been stolen (only in some infection cases); they also indicate a maximum period of 3 days to contact the attackers and suggest not trying to recover the files, as they could be permanently damaged.
At the end of the ransom note, the attackers also share their contact e-mail addresses, and an ID to identify the victim.
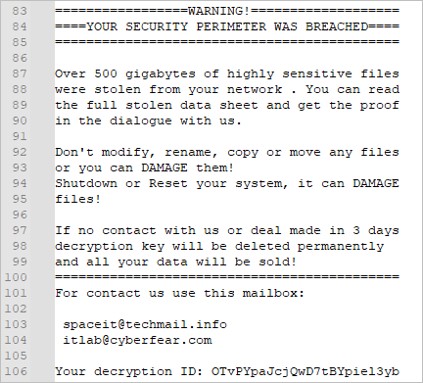
Figure 12. Babuk’s rescue note
WhiteRabbit cryptor (Linux variant)
SCILabs determined that WhiteRabbit is a Babuk variant after having identified multiple overlaps summarized below:
- Type of file
- Used C/C++ libraries
- Execution with the same parameters
- Summary of encrypted files
- Extensions that seek to encrypt
In addition, some differences between both cryptors were identified. The most relevant are the following:
- Encryption extension: It was possible to identify that, in the case of WhiteRabbit, the extension used to encrypt the victim’s files is “.mario”.
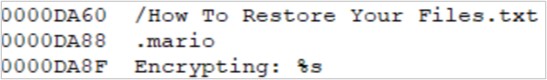
Figure 13. WhiteRabbit encrypt extension
- Ransom note: When the execution of the artifact ends, in addition to displaying the statistics of the encrypted files the ransom note is created; in this case, the file name is How To Restore your files.txt and it is located in all subdirectories contained in the previously specified folder (at execution).
The ransom note has six sections within the same file, separated by a sequence of middle dashes (—). Each of them is described below:
- It allows some prohibited actions, including shutting down, restarting the infected computer, editing, moving encrypted files, and even using a third-party software to recover information.
- It provides a brief explanation of what just happened and the steps for the victim to follow.
- It shares the negotiation process, establishing a maximum period of 4 days to begin.
- It indicates the URL where the evidence of the leak can be found.
- It shows the contact instructions and means of establishing communication with attackers.
- It describes the possible consequences of ignoring or failing to comply with the attackers’ requests.

Figure 14. WhiteRabbit Rescue note
MarioLocker cryptor (Linux variant)
SCILabs determined that MarioLocker is a variant of Babuk after having identified multiple matches which are summarized below:
- Type of file
- Used C/C++ libraries
- Execution with the same parameters
- Summary of encrypted files
In addition, some differences between both cryptors were identified. The most relevant are:
- Searched files: Through malware analysis, it was identified that the artifact focuses on encrypting files that have the following extensions, which are virtualization files.
| Filetype | Filetype |
| .vmdk | .ova |
| .ovf | .vmem |
| .vib | .vswp |
| .vbk | .vmsd |
| .vbm | .vmsn |
Table 2. MarioLocker files to encrypt
- Encryption extension: It was possible to identify that, in the case of MarioLocker, it uses the following five extensions to perform the encryption; in this case, the artifact is only encrypted with the .emario extension. It is worth mentioning that the attacker uses the Linux urandom service to encrypt the information.
| Filetype |
| .mario |
| .emario |
| .lmario |
| .mmario |
| .nmario |
| .wmario |
Table 3. MarioLocker Extension files
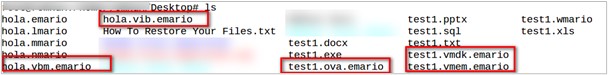
Figure 15. MarioLocker files after execution
- Ransom note: When the execution of the artifact ends, in addition to displaying the statistics of the encrypted files, the ransom note is created; in this case, the file name is HowToRestore.txt, and it is located in all the subdirectories contained in the previously specified folder (at execution).
-
- It shows some prohibited actions, including shutting down, restarting, editing, moving encrypted files, from the infected PC or using third-party software to recover information.
- It provides a brief explanation of what just happened and the steps for the victim to follow.
- It shares the negotiation process, establishing a maximum period of 4 days to begin it.
- It indicates the URL where evidence of the leak can be found.
- It shows the contact instructions and means of establishing communication with the attackers.
- It describes the possible consequences of ignoring or failing to comply with attackers’ requests.
In the case of the sample analyzed, it was possible to observe that the attackers used the mentioned note for one of their victims.
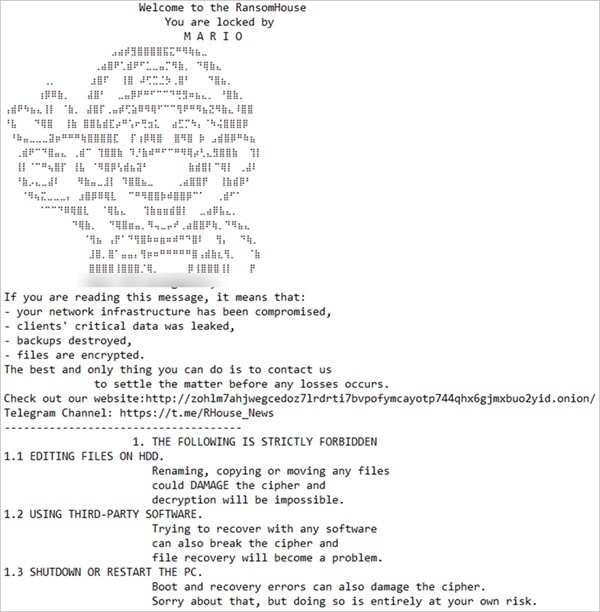
Figure 16. MarioLocker rescue note
SCILabs also obtained one of the MarioLocker cryptors aimed at ESX systems, which has the following differences.
- Parameterized execution: Through a malware analysis it was possible to identify that for the correct execution of the file, it is necessary to give an IP address with a port associated with ESX services. It is not detailed what the reason for this type of execution is, but the attacker may enter the victim’s address so that he can continue with his infection process.
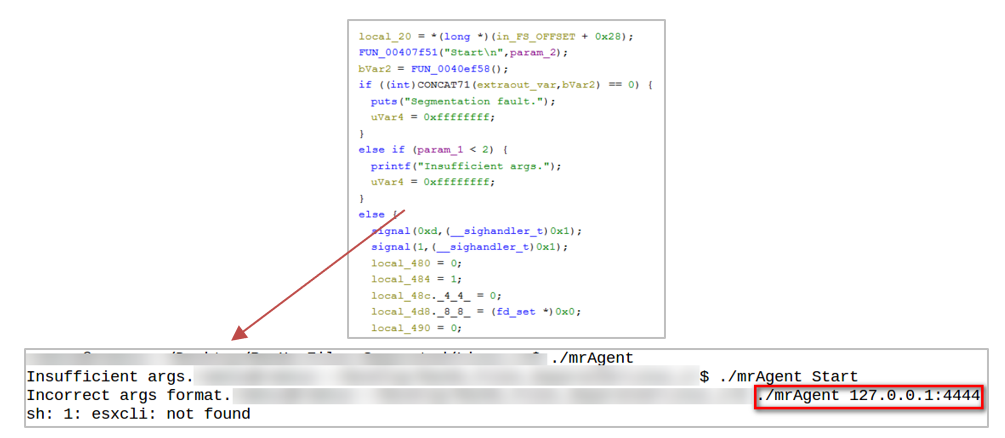
Figure 17. Parametrized MarioLocker execution in ESX
- Skip directories: Through the malware analysis, as seen in the previous image, it is specified that the following operating system folders are not checked. The attacker does this to increase the speed of searching for encrypted files.
| Filetype | Filetype |
| /sys | /proc |
| /run | /var/log |
Table 4. MarioLocker directories
- Deletion of traces: In this case, the device erases its traces on the ESX server by deleting the “.log” type files found in the “/vaf/log” path with the purpose of reducing the possibility of locating the attacker’s activities during the event.
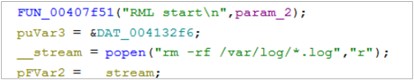
Figure 18. MarioLocker deleting clues
- Reconnaissance: Once the artifact is executed successfully, it performs a reconnaissance of the equipment to identify users, the number of virtual machines, and network interfaces, which could provide relevant information for the attacker to expand its operations.
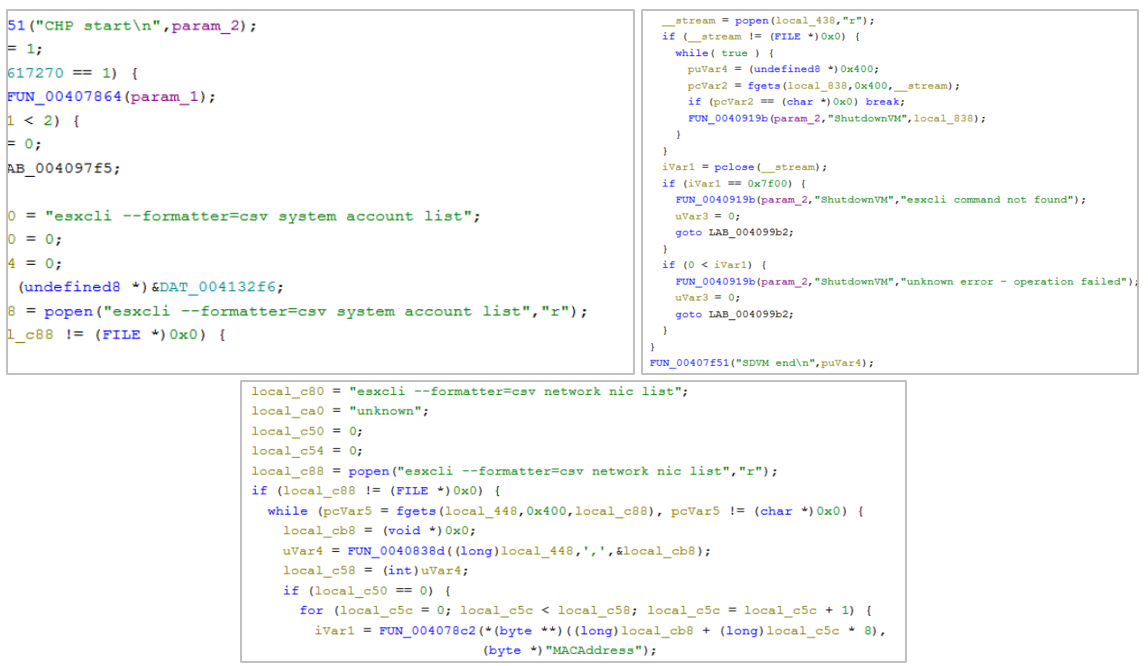
Figure 19. MarioLocker recognition activities
- Security evasion: The artifact can turn off the device’s firewall if enabled and restart the agent for the connection with the VCenter, which is responsible for sending the established configuration.
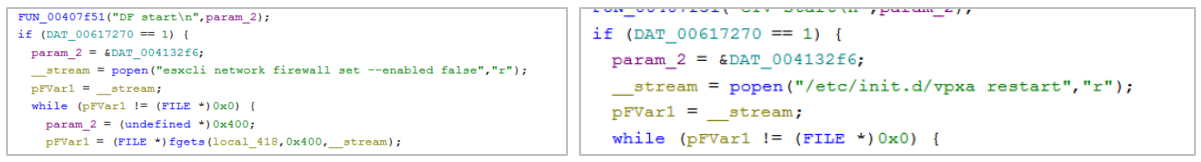
Figure 20. MarioLocker defense evasion
Also, what appears to be an attempt to change the users’ password on the ESX was detected with a password known to the attacker, which could help to automate malicious tasks or establish persistence.
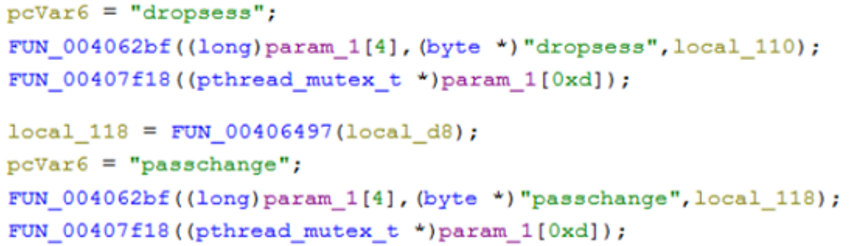
Figure 21. MarioLocker password change in ESX
Leaks site
Through OSINT processes, it was possible to recover some addresses corresponding to the RansomHouse leak site in which the following elements were observed.
- List: At the beginning of the site, a historical list of the organizations that have been victims of RansomHouse since its first attack in 2021 is shown, as well as a “news” section in which they reveal the latest companies that have been attacked.
Each element in the list has the victims’ names, the affected organization’s website, the action they carried out on it, the date they carried out the attack, and the status in which the information was found.
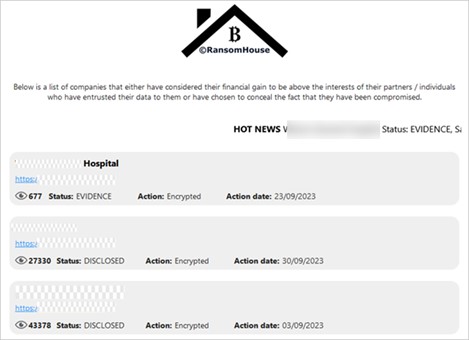
Figure 22. RansomHouse website
- Evidence: Each victim has a page dedicated to them. On this site, it possible to identify several boxes with the following information:
-
- Name and a brief description of the organization affected by RansomHouse.
- Details of the organization, in which it is feasible to find the website, profits, or number of employees.
- Evidence of packages, with the possibility of being downloaded for whoever wants to consult them, whether the data package has a password or not.
- Indicates the status of the stolen or encrypted files; in this case, there can be two aspects:
- Evidence – when the attackers are in a negotiation period with the victim, and to persuade them to make the ransom payment they publish a small portion of the stolen information.
- Disclosed – when the negotiation has ended and the attackers publish the stolen information, probably because the victim did not pay the ransom.
- Date when the victim’s files were encrypted and the amount of information the attackers extracted from the organization.
- Sharing the publication on social networks like X (beforeTwitter) or Facebook is possible.
- Telegram channel of the attackers to establish communication with them.
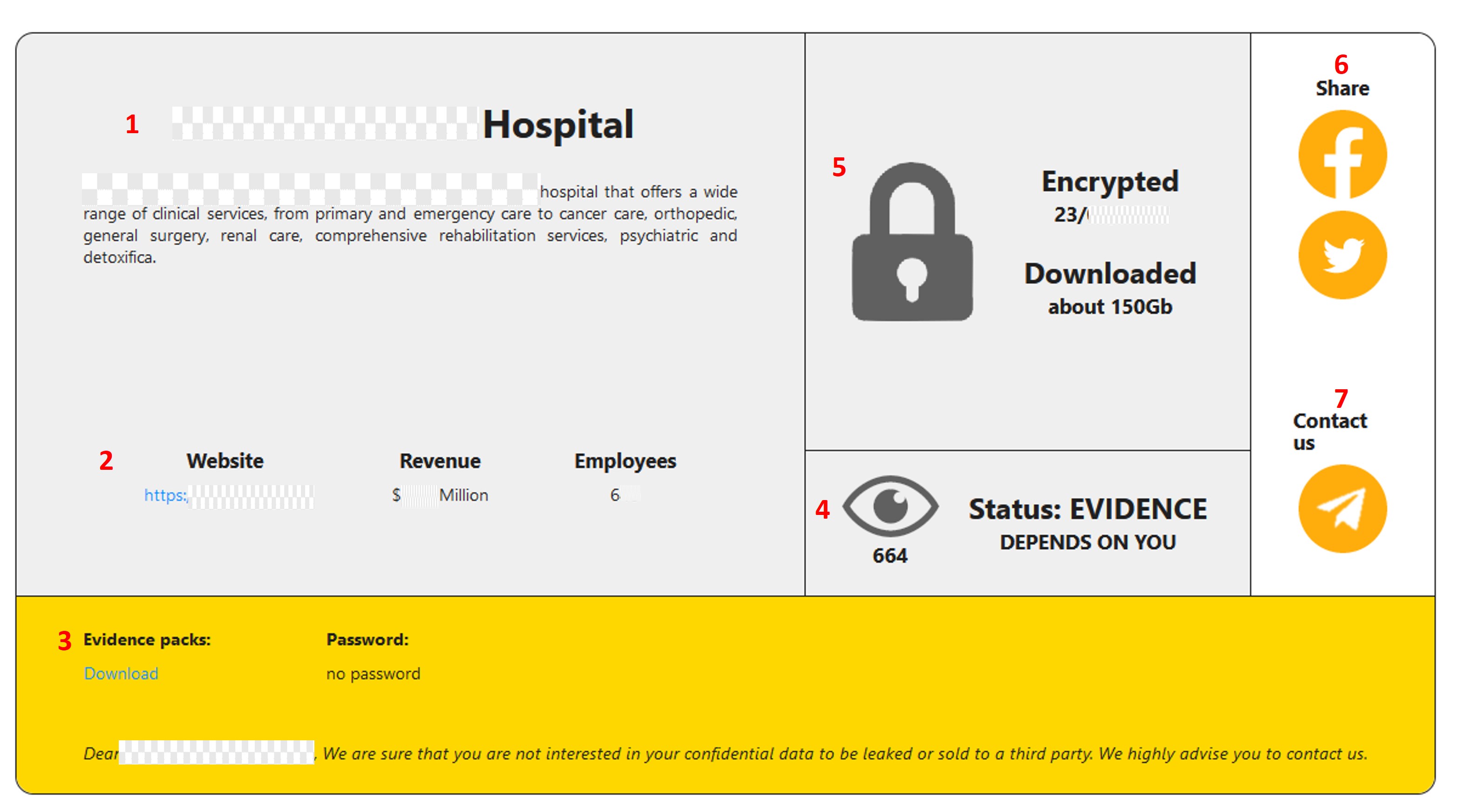
Figure 23. RansomHouse Website with affected companies and its evidence
Attack Flow
The following attack flow was developed from open-source malware analysis and intelligence processes.

Figure 24. RansomHouse attack flow
Framework MITRE ATT&CK® TTPs
The following TTP matrix based on the MITRE Framework was obtained from open-source malware analysis and intelligence processes.
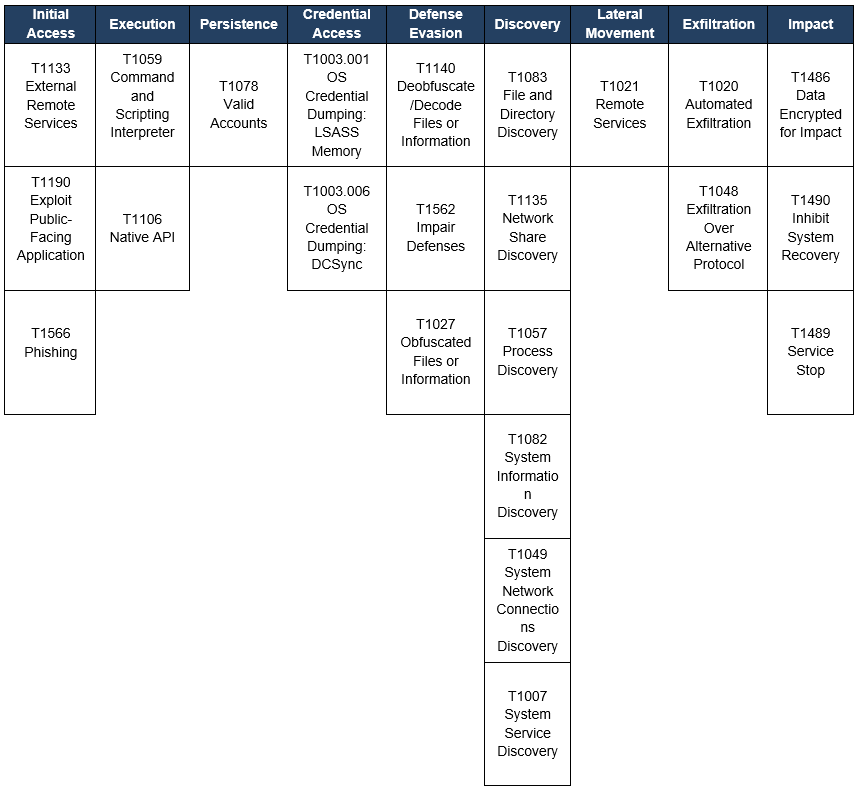
Table 5. Framework MITRE ATT&CK® TTPs
Diamond model
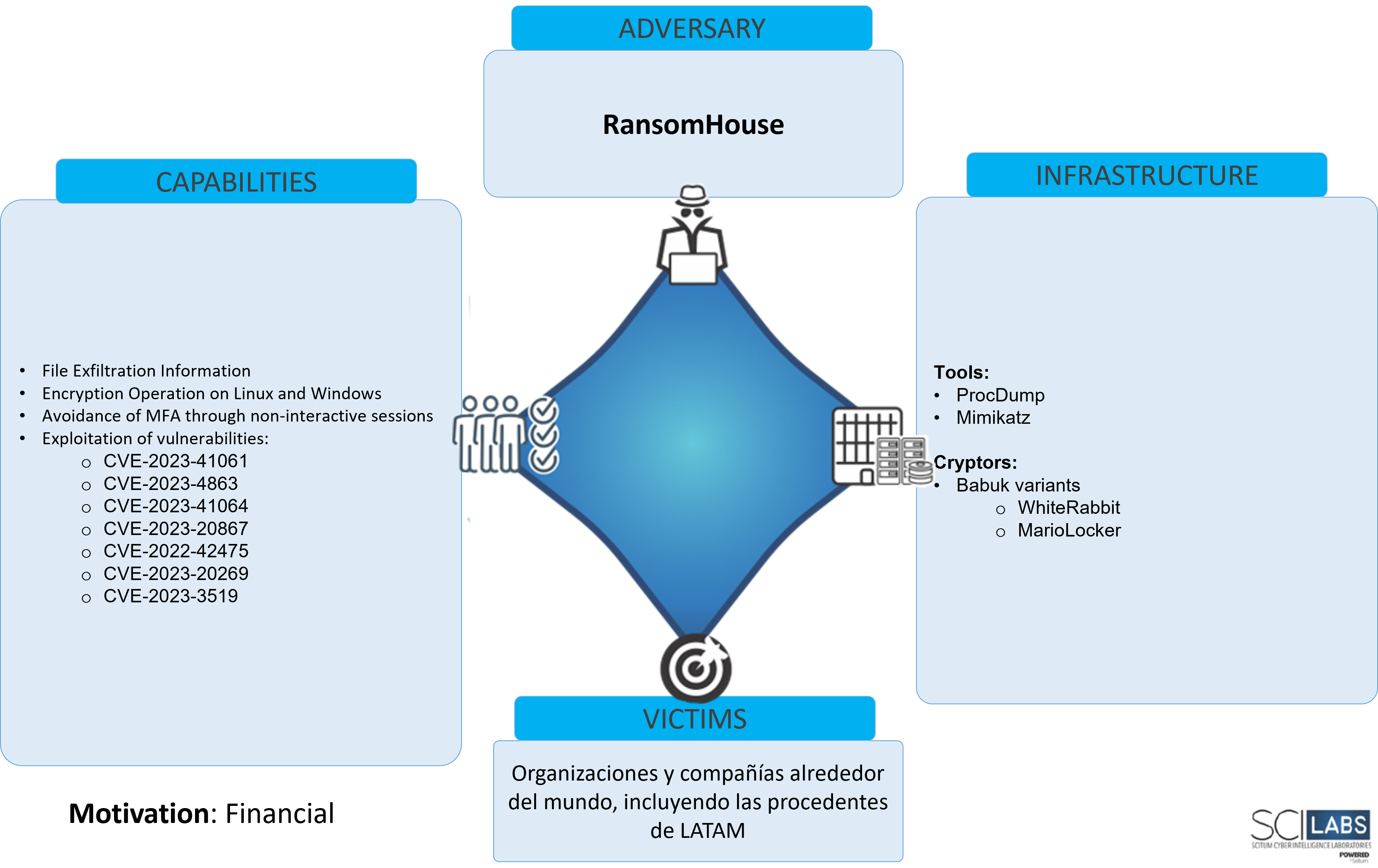
Figure 25. RansomHouse Diamond model
Conclusions
According to SCILabs telemetry, ransomware is one of the biggest threats affecting organizations in different industries in LATAM, especially those that operate as managed service providers (MSP). The most common initial vectors are the exploitation of critical vulnerabilities in devices accessible from the internet, brute force attacks on RDP and VPN services, the purchase of access credentials on Dark Web forums or through access brokers, and the use of phishing e-mails directed at organizations.
SCILabs considers that the danger of RansomHouse lies primarily in the fact that it is a group that distributes cross-platform ransomware, which means that it has variants for both Linux and Windows; on the other hand, it orchestrates supply chain attacks, such as the one directed at IFX in September 2023.
The ideal victims of these attacks are those organizations that do not have robust security mechanisms to protect their infrastructure, such as multi-factor authentication (MFA), organizations without a well-managed EDR system, servers exposed on the internet with vulnerabilities, or lousy password management practices. As expected, organizations that do not have a well-defined disaster recovery plan (DRP) and business continuity plan (BCP) could have a more significant impact from ransomware attacks.
SCILabs will continue to monitor this threat to keep organizations and users updated on any changes to their TTP, new IoC, or relevant information that could be vital to avoid falling victim to RansomHouse.
Finally, SCILabs considers essential to comply with the following recommendations to detect malicious activity related to this campaign in time and avoid becoming a victim.
RansomHouse recommendations:
- Add the IoC shared in this document to your security solutions to reduce the possibility of infection by this variant.
- Add the YARA rule in this document to your security solutions to reduce the possibility of infection by this variant.
- Recommendations for ESX administration:
- Keep ESX-type computers in an isolated network sector that is administration-only and can only be accessed by specific users.
- Users with access to ESX must have constant training on threats, such as infostealers and phishing to reduce the ability of attackers to reach these computers.
- Make frequent password changes to the ESX and store them in password managers to avoid having them in plain text.
- Prevent the ESX administration from being on the same network as the virtual machines.
- Perform threat-hunting activities looking for executions of the rm -rf /var/log/*.log command the attacker uses to perform fingerprint deletion.
- Perform threat-hunting activities by looking for executions of files with an EXE, OUT, or ELF extension followed by a directory or IP address, as these are the execution parameters used by RansomHouse.
- Verify if Cisco ASA and Fortinet technologies are present in your organization, update to the latest versions and make sure there is a 3-month periodical password change policy for the VPN, as well as a two-factor authentication (2FA).
- If your organization uses Chrome in MacOS or iOS, always keep them updated to the latest version because vulnerabilities have been seen in those that are exploited by RansomHouse operators.
- Follow the recommendations provided by SCILabs on their blog before, during, and after a ransomware attack.
IOCs
The following indicators were obtained with a high confidence level through a malware analysis.
Hash SHA256
2C1475F1B49A8B93A6C6217BE078392925535E084048BF04241E57A711F0F58E
549A8BC04C0EA9C622BAC90B0607E3F4FD48CB5610601031E054CC6340F8EBA5
D36AFCFE1AE2C3E6669878E6F9310A04FB6C8AF525D17C4FFA8B510459D7DD4D
8189C708706EB7302D7598AEEE8CD6BDB048BF1A6DBE29C59E50F0A39FD53973
D2B55BA46104FB1657478FA307623F39BEEEB488583CEAA8F8C60432777A1E9E
URLS
XW7AU5PNWTL6LOZBSUDKMYD32N6GNQDNGITJDPPYBUDAN3X3PJGPMPID[.]ONION
VA5VKFDIHI5FORRZSNMINS436Z3CBVF3SQQKL4LF6L6KN3T5KC5EFRAD[.]ONION
ZOHLM7AHJWEGCEDOZ7LRDRTI7BVPOFYMCAYOTP744QHX6GJMXBUO2YID[.]ONION
HXXP[:]//ZZF6L4WAVAYC2MVBZWETTBLCO2QODVE5SECTJQYWC6FUWKVCVJLUAMYD[.]ONION/?URL=82B40DD6-E600-43BF-B4DF-0BB2CF76B426
HXXPS[:]//T.ME/RHOUSE_NEWS
Email accounts
SPACEIT@TECHMAIL[.]INFO
ITLAB@CYBERFEAR[.]COM
The following indicators were obtained through RetroHunt activities and open-source intelligence and were validated by SCILabs with a high confidence level.
Hash SHA256
E142F4E8EB3FB4323FB377138F53DB66E3E6EC9E82930F4B23DD91A5F7BD45D0
8140004FF3CF4923C928708505754497E48D26D822A95D63BD2ED54E14F19766
BC4066C3B8D2BB4AF593CED9905D1C9C78FFF5B10AB8DBED7F45DA913FB2D748
Annex I
YARA rule to detect RansomHouse cryptor
| rule Detects_RansomHouse: RansomHouse
{ meta: description = “Detects_RansomHouse” author = “SCILabs” date = “21/11/2023” sample1 = “E56C97CB4F9DF25845CDA36E3CD7D597” sample2 = “C0FAA37055ED3E9783E6F86CFE499E68” sample3 = “0DCBB7C7AF77EFD4A2B39F2303806FCD” sample4 = “D2853C1D92C73DC047CDB1F201900A99”
strings: $s1 = “emario.out” ascii $s2 = “e_esxi.out” ascii $s3 = “.mario” ascii $s4 = “.emario” ascii $s5 = “.lmario” ascii $s6 = “.mmario” ascii $s7 = “.nmario” ascii $s8 = “.wmario” ascii $s9 = “HowToRestore.txt” ascii $s10 = “FASF)@#$#k” ascii $s11 = “/path/to/be/encrypted” ascii $s12 = “Welcome to the RansomHouse” ascii
condition: 2 of them }
|
Annex II
Babuk functions
| Function / Library | Utility |
| closedir | Close a directory previously opened with opendir. |
| difftime | Calculates the difference between two-time values. |
| entry | Check if encryption has been started, otherwise start it |
| environ | Get environment variables |
| exit | Terminates program execution. |
| fclose | Closes a file stream. |
| fflush | Clears the buffer of a file stream. |
| finalize | Can be part of a function or variable name |
| fopen | Open a file. |
| fprintf | Prints formatted data to a file stream. |
| fread | Reads a block of data from a file stream. |
| free | Free previously dynamically allocated memory with malloc, calloc, or realloc. |
| fseek | Sets the position of a file pointer. |
| fwrite | Writes a block of data to a file stream. |
| malloc | Reserve memory dynamically. |
| memcpy | Copies a block of memory from source to destination. |
| memset | Sets the first n bytes of a memory area to a given value. |
| opendir | Opens a directory for reading. |
| prctl | Controls the behavior of a process. |
| printf | Prints formatted data to standard output. |
| pthread_cond_broadcast | Wakes up all threads that are waiting on a condition variable. |
| pthread_cond_init | Initializes a condition variable. |
| pthread_cond_signal | Wakes up a thread that is waiting on a condition variable. |
| pthread_cond_wait | Causes a thread to wait on a condition variable until signaled by another thread. |
| pthread_create | Create a new thread of execution. |
| pthread_detach | Indicates that a thread should be automatically released after completion. |
| pthread_kill | Send a signal to a thread. |
| pthread_mutex_init | Initializes a mutex. |
| pthread_mutex_lock | Locks a mutex. |
| pthread_mutex_unlock | Unlock a mutex. |
| putchar | Prints a single character to standard output. |
| puts | Prints a string of characters followed by a line break to standard output. |
| readdir | Read the following directory entry. |
| rename | Change the name of a file. |
| sigaction | Establishes the handling of a signal. |
| sigemptyset | Search for free space in memory to later start the mutex |
| sleep | Causes the program to pause for a specified number of seconds. |
| snprintf | Prints a formatted character string to a buffer. |
| sprintf | Prints a formatted character string to a buffer. |
| stat | Returns information about a file or directory |
| stderr | Used to print error messages to standard error output. |
| stdout | Show standard output and save file simultaneously |
| strcat | Concatenates two-character strings. |
| strcmp | Compares two-character strings. |
| strcpy | Copies one string of characters into another. |
| strlen | Returns the length of a character string. |
| strstr | Finds the first occurrence of a substring in another string. |
| sysconf | Returns system configuration information. |
| time | Gets the current time. |
Table 6. Babuk and variants’ libraries and functions
