BPL Side-Loading: technique exploited by threat actors in LATAM
Overview
The purpose of this post is to provide information on a technique disclosed in May of 2024 and recorded on multiple open feeds due to its continued use by some known and unknown threat groups (such as Red Akodon, which was profiled by SCILabs in April of 2024).
Since mid-2024, SCILabs has consistently identified artifacts used in malware campaigns targeting LATAM that are executed during the infection process through the BPL Side-Loading technique in conjunction with IDATLoader malware. Most of these artifacts are distributed via phishing emails.
The information provided here focuses on disclosing some of the malware campaigns primarily affecting Colombia, and potentially other LATAM countries, leveraging email pretexts such as alleged legal demands and citations, as well as a campaign impersonating a Crowdstrike update after the July 19, 2024 incident, when the provider released a configuration content update for its Windows sensor (part of the Falcon Sensor platform) that resulted in critical operating system failures (Blue Screen of Death [BSOD]) in some Windows hosts.
It is important to notice that this information aims to explain how BPL Side-Loading is exploited in conjunction with IDATLoader malware, with the objective of understanding recent malware campaigns under the premise that these techniques will likely continue to be employed constantly by threat actors in the future.
How can this affect your organization?
BPL Side-Loading has been previously recorded publicly; however, it hasn’t received enough coverage nor sufficient in-depth analysis. This technique would allow an attacker to deploy any kind of malware, evading security controls such as EDR and AV. Consequently, organizations lacking prior knowledge of this technique and its functionality are unable to implement effective security countermeasures, which may lead to integrity, confidentiality and availability risks, leading to financial losses and reputational damage.
Technical analysis
First campaign
This campaign was found through open feed posts where the distribution method was determined to be phishing emails using a pretext of a supposed legal citation impersonating the “Fiscalía General de la Nación” of Colombia.

This email has a ZIP file attached by the name of “08 CITACION DEMANDA.zip”, which works as the first dropper.
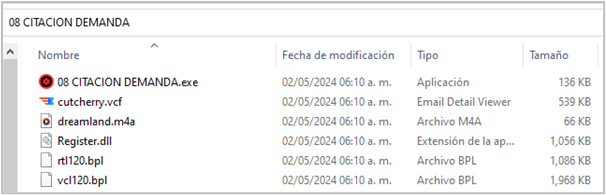
We’ll provide a brief description of the artifacts identified inside the ZIP file, as their full analysis is not the main objective of this post. The focus is to understand their role in exploiting the BPL Side-Loading technique. Moreover, we will examine the functionality of the highlighted artifacts further down the post.
- 08 CITACION DEMANDA.exe: Legitimate IObit Driver Booster executable developed in Delphi
- dreamland.m4a: Encoded Shellcode (IDATLoader)
- cutcherry.vcf: AsyncRAT encrypted payload, encrypted by IDATLoader
- vcl120.bpl: Malicious BPL. Loads the first payload into Driver Booster executable
- Register.dll: Legitimate DLL required for Driver Booster execution
- rtl120.bpl: Legitimate BPL required for Driver Booster execution
Second campaign
SCILabs identified this campaign, which, similar to the first one, targets users in Colombia. It was distributed through phishing emails using the pretext of a legal citation impersonating the “Juzgado Tercero Laboral del Circuito” of Colombia.

This email had an attached SVG file displaying a message that encouraged the victim to download a file related to a supposed citation through a PDF file icon. Within the same email, the attacker provides a password for opening the PDF file as a mechanism to evade automated analysis by AV solutions and sandboxes.

Once the victim clicks on the link, a compressed file is automatically downloaded from Dropbox. Similar to the previous campaign, a ZIP file by the name “01-CITACION DEMANDA EN SU CONTRA -JUZGADO PENAL 01 CIRCUITO ESPECIALIZADO EXTINXION-01.zip” is downloaded.
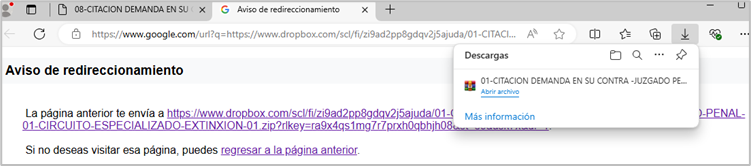
Within the ZIP file we found the following artifacts:
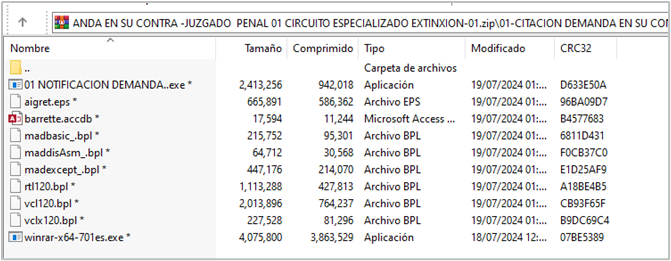
- 01 NOTIFICACION DEMANDA.exe: Legitimate iTOP DualSafe Password Manager executable developed in Delphi
- barrette.accdb: Encoded Shellcode (IDATLoader)
- aigret.eps: AsyncRAT encrypted payload (encrypted by IDATLoader)
- vcl120.bpl: Malicious BPL. Loads the first payload into DualSafe Password Manager executable
- madbasic_.bpl: Legitimate BPL required for DualSafe Password Manager execution.
- maddisAsm_.bpl: Legitimate BPL required for DualSafe Password Manager execution.
- madexcept_.bpl: Legitimate BPL required for DualSafe Password Manager execution.
- vclx120.bpl: Legitimate BPL required for DualSafe Password Manager execution.
- rtl120.bpl: Legitimate BPL required for DualSafe Password Manager execution.
- winrar-x64-701es.exe: Winrar legitimate executable; not used during the attack
Third campaign
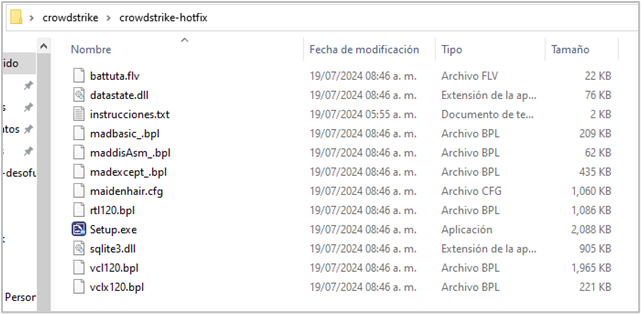
In the third campaign, SCILabs identified the use of a Dropbox storage link hosting a ZIP file by the name “crowdstrike-hotfix.zip”, being this file sample the same as the one reported in Crowdstrike’s Blog . According to their post, the distribution method remains unknown and is likely part of a malware campaign targeting LATAM, leveraging a CrowdStrike update pretext as a result from the Crowdstrike failure on July 19th, 2024. This sample contains a file by the name “instrucciones.txt”, where the attacker provides alleged steps for executing a file patch. In reality, these instructions lead the victim to execute a malicious file that initiates the infection.
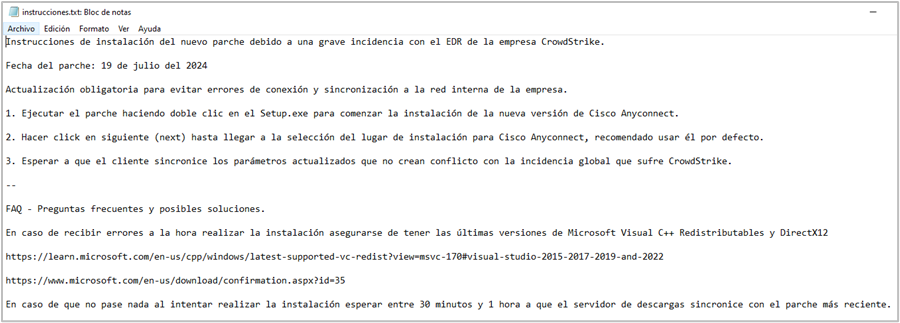
The zip file contains the following artifacts:
- Setup.exe: Legitimate iTOP Data Recovery Backup executable developed in Delphi
- battuta.flv: Encoded Shellcode (IDATLoader)
- maidenhair.cfg: Remcos encrypted payload (encrypted by IDATLoader)
- vcl120.bpl: Malicious BPL. Loads the first payload into Data Recovery Backup executable
- madbasic_.bpl: Legitimate BPL required for Data Recovery Backup execution
- maddisAsm_.bpl: Legitimate BPL required for Data Recovery Backup execution
- madexcept_.bpl: Legitimate BPL required for Data Recovery Backup execution
- vclx120.bpl: Legitimate BPL required for Data Recovery Backup execution
- rtl120.bpl: Legitimate BPL required for Data Recovery Backup execution
- sqlite3.dll: Legitimate DLL required for Data Recovery Backup execution
- datastate.dll: Legitimate DLL required for Data Recovery Backup execution
Analysis of BPL Side-Loading technique in conjunction with IDATLoader
BPL Side-Loading is a technique mentioned among the Hijack Execution Flow: DLL techniques registered in the MITRE ATT&K framework; however, it does not have an official categorization at the time of writing this post.
A BPL (Borland Package Library) file is a package file used by Borland software development tools, such as Delphi and C++ Builder. These files are similar to dynamic link libraries (DLLs) but are specifically designed for applications developed in the aforementioned environments. Like DLLs, BPL files can be loaded dynamically at runtime, allowing applications to extend their functionality without requiring recompilation.
Considering the above, the BPL Side-Loading technique is based on the dependency of applications on external BPL libraries, which can be exchanged or manipulated to load other artifacts into memory, much like DLL Side-Loading.
The initial artifact is a legitimate executable that must be launched by the user to continue the attack flow. It is developed in Delphi and requires BPL libraries to function, as is the case with the Data Recovery Backup, DualSafe Password Manager, and Driver Booster applications, which are vulnerable to this technique.
When executed, the libraries required for the application to function are imported by name; therefore, a legitimate BPL library can be easily replaced by one that has been modified by the attacker. In the analyzed campaigns, the malicious file “vcl120.bpl” was found in the same directory as the executable, being a malicious BPL tailored by the attacker.
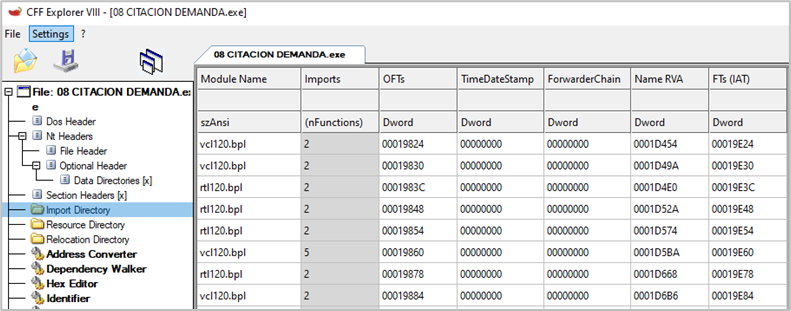
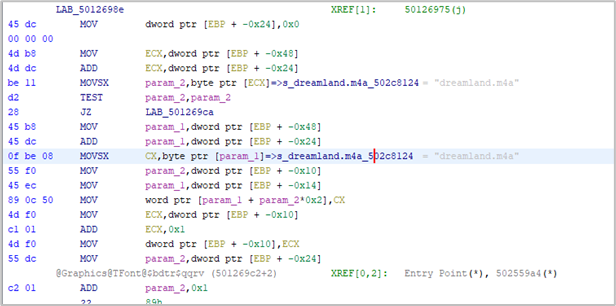
The executable then imports functions from the malicious BPL library; in this case, the file “vcl120.bpl”. This library has been previously modified by the threat actor to import artifacts that do not correspond to its regular operation. This is where malware called HijackLoader or IDATLoader is executed, which begins to read the contents of a file containing the main shellcode and corresponding to the main IDATLoader module. In these campaigns, the names of these files are “barrette.accdb”, “dreamland.m4a”, and “battuta.flv”. In the example shown in the following image, the name is “dreamland.m4a”.
It is important to mention that in the three campaigns analyzed, the BPL Side-Loading technique has been used in conjunction with the IDATLoader malware.
IDATLoader is modular in nature, so its loading into memory begins with the main shellcode but consists of different stages. During the analysis, the following were identified:
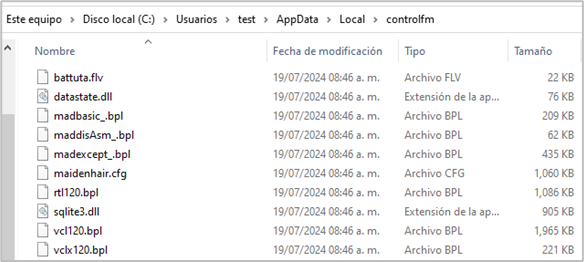
- Copying artifacts: Copies the files needed to execute the BPL Side-Loading technique in conjunction with the IDATLoader malware, regardless of whether they are malicious or legitimate, to a directory other than where the execution takes place. The directory depends on the operator’s choice; however, the following paths were identified in these campaigns:
- C:\Users\[User]\AppData\Local
- C:\Users\[User]\AppData\Roaming
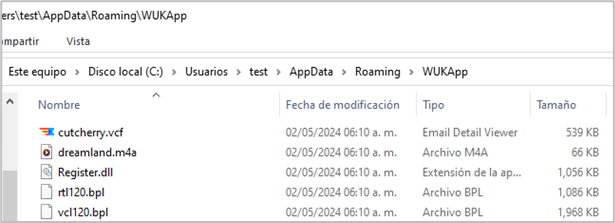
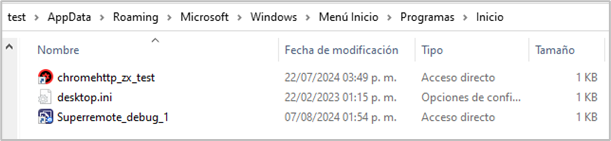
- Persistence: Generates persistence by creating shortcuts in the C:\Users\[User]\AppData\Roaming \Microsoft\Windows\Start Menu\Programs\Startup folder.
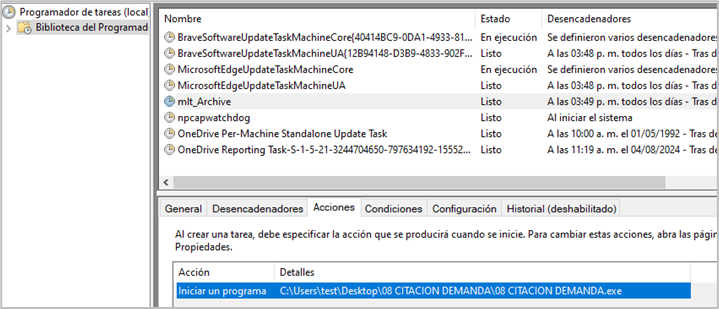
Persistence through scheduled tasks was also observed:
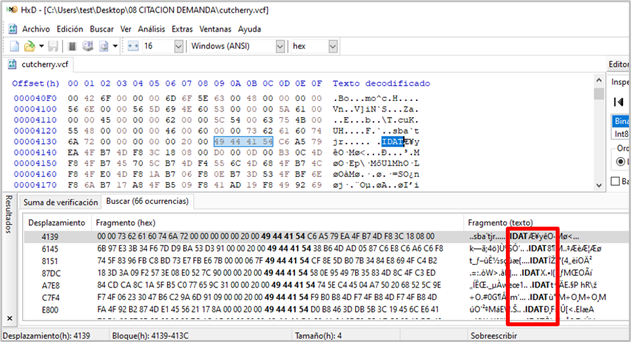
- Payload decryption: The file containing the IDATLoader payload is easy to identify because its encryption technique includes the word “IDAT” to segment the content; in the campaigns analyzed, these are the artifacts named “cutcherry.vcf”, “aigret.eps”, and “maidenhair.cfg”. Each segment is decrypted individually using the XOR operator with a key located immediately after the first “IDAT” flag. The decrypted segments are then joined and decompressed using the LZNT1 algorithm.
- Payload loading: Using advanced techniques known as Process Doppelgänging and Heaven’s Gate, it loads the already decrypted content into a process started with elevated privileges. In the case of the campaigns analyzed, the AsyncRAT and the Remcos Trojan are loaded into the MSBuild.exe or explorer.exe processes.


- Trace removal: Once the payload is loaded and executed, it deletes the main shellcode from memory and terminates unnecessary processes, leaving only those processes active that are necessary for the payload (Trojan) to function.
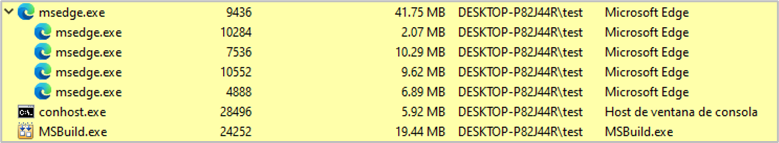
At the end of this process, the payload executes actions corresponding to its operation similar to other campaigns. These actions include creating new persistence as in the case of AsyncRAT and establishing communications with the command-and-control (C2). Additionally, IDATLoader retains the persistence generated during execution.
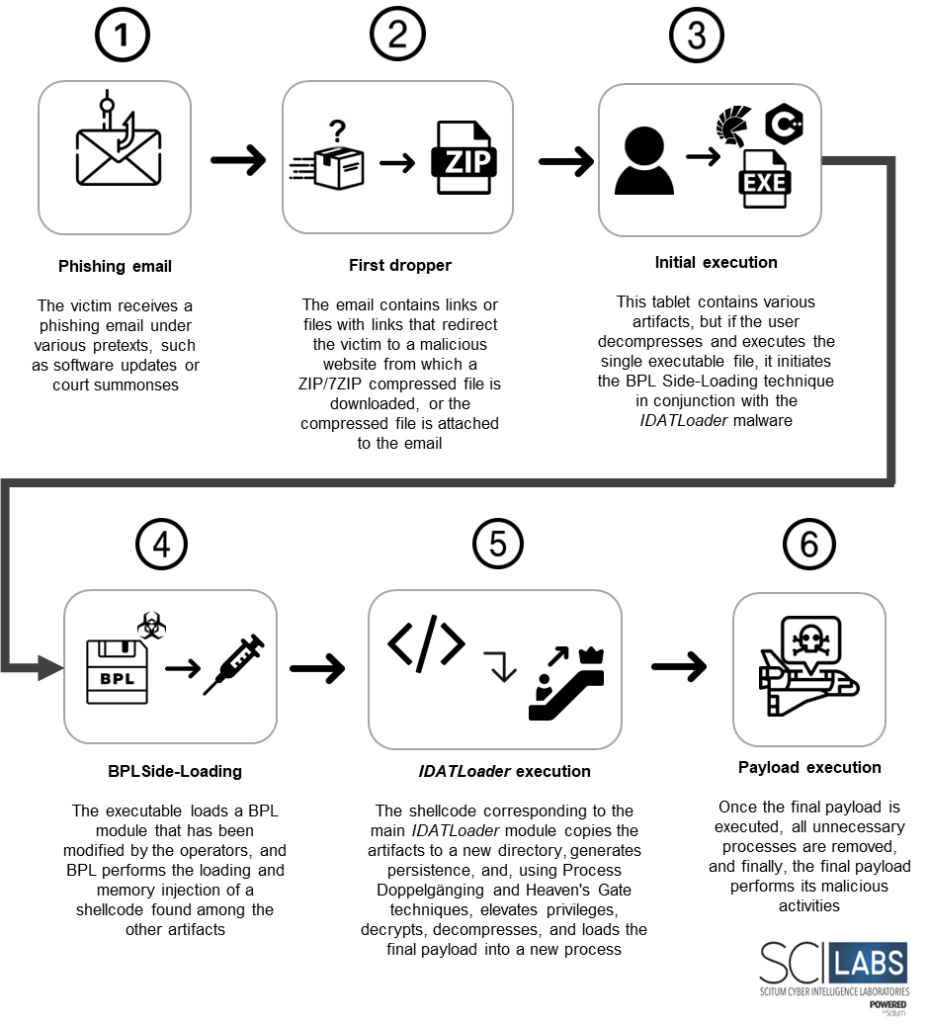
Attack chain summary
- The user receives a phishing email using different pretexts, such as alleged lawsuits, court summonses, or even software patches.
- The email may contain attachments with links that automatically download a compressed file, or it may directly contain a compressed ZIP or 7ZIP file as an attachment. It is important to note that this distribution method is not exclusive, and malware using this technique could also be distributed through malvertising.
- The attached compressed file contains various artifacts, but if the user decompresses and executes the single executable file, it initiates the BPL Side-Loading technique in conjunction with the IDATLoader malware, the steps of which are summarized below:
- The legitimate executable file loads a BPL module that has been modified by the operators.
- The BPL module loads and injects into memory a shellcode found in another artifact.
- The shellcode, which corresponds to the main module of IDATLoader, copies the artifacts to a new directory, generates persistence, and, using Process Doppelgänging and Heaven’s Gate techniques, decrypts, decompresses, and loads the final payload into a new process.
- Once the final payload is executed, all unnecessary processes are terminated.
- Finally, the final payload executes its intended malicious activities.
Attack chain process
The following attach chain was recorded by SCILabs after analyzing the previous campaigns disclosed in this post.
TTPs aligned with MITRE ATT&CK® framework
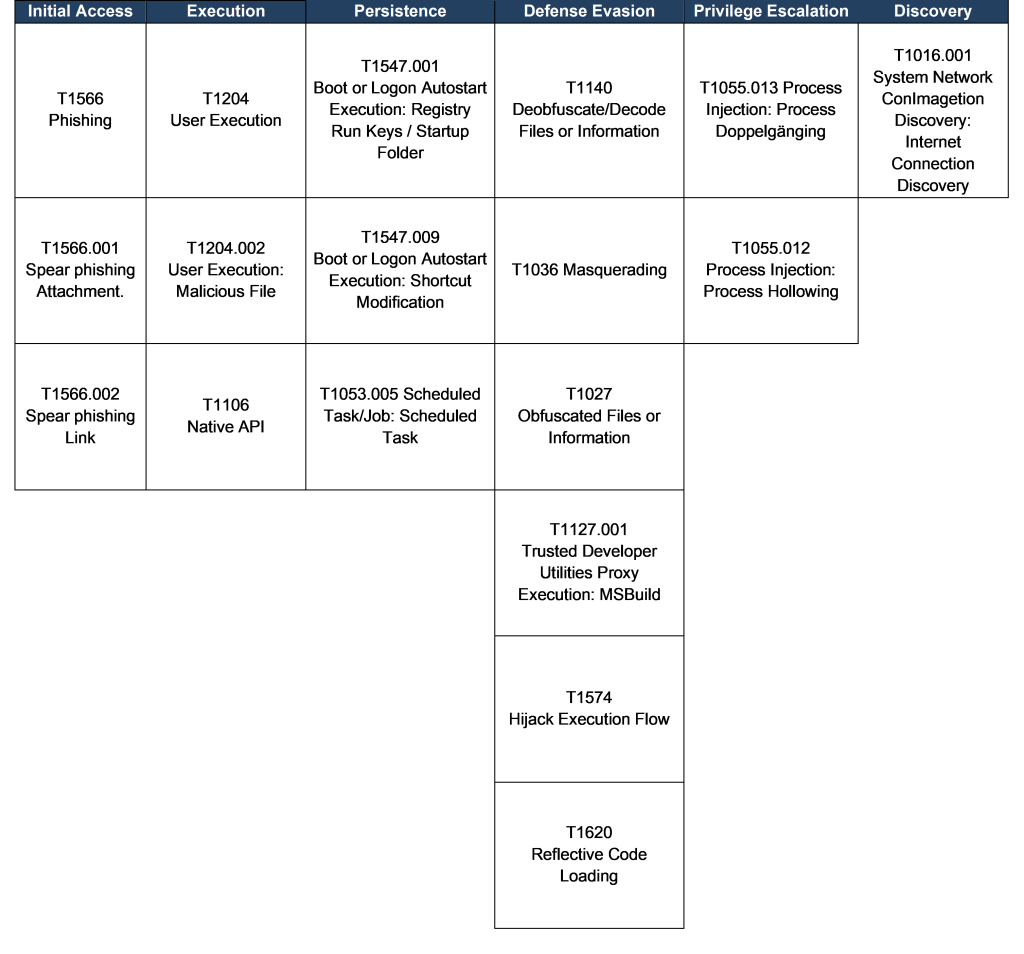
The following TTP matrix, based on the MITRE Framework, was crafted from the analysis of the use of the BPL Side-Loading technique in conjunction with the IDATLoader malware.
Conclusion
The BPL Side-Loading technique is an example of how threat actors are constantly evolving and developing new techniques to evade security tools with the aim of distributing malware, taking advantage of organizations and users that are insufficiently informed or prepared to address emerging threats.
As mentioned in this post, this technique has been used since its discovery by various threat actors in LATAM. SCILabs believes that the number of threat actors using BPL Side-Loading and IDATLoader in their malware campaigns targeting the region will increase in the coming months due to a general lack of awareness of how it works among organizations and some manufacturers.
SCILabs provides the following recommendations to avoid falling victim to this technique or, if prevention is not possible, to mitigate its impact.
- Block the IoCs mentioned at the end of this publication
- Perform awareness campaigns on the techniques used by different threat actors in the region, such as Red Akodon, to distribute their campaigns
- Have strict security policies regarding the use and installation of software on corporate computers, especially utilities related to applications developed in Delphi that are not necessary for operations, such as Data Recovery Backup, DualSafe Password Manager, and Driver Booster
- In the case of phishing emails:
- Avoid opening emails from unknown senders
- Avoid opening suspicious links
- Avoid opening or downloading suspicious files
- Keep operating systems and software of all devices on your network up to date.
- Ensure that In-Depth Security is correctly implemented on all systems in the organization.
- Perform threat hunting tasks to search for suspicious artifacts, mainly in the following paths:
- C:\Users\[User]\AppData\Local
- C:\Users\[User]\AppData\Roaming
- Perform threat hunting tasks in search of shortcuts within the path C:\Users\[User]\AppData\ Roaming\Microsoft\Windows\Start Menu\Programs\Startup
- Perform threat hunting activities to identify persistence mechanisms and anomalous behavior, including suspicious scheduled tasks and processes not initiated by the user—particularly cmd.exe, conhost.exe, MSBuild.exe, and explorer.exe.
- Perform threat hunting tasks to search for possible infections from other types of malwares such as infostealers, banking Trojans, RATs, or ransomware, among others.
- Pay attention to changes in your devices, such as a double cursor, pop-up screens, among others.
Indicators of Compromise
SHA256 Hashes
4A3BBDB727E0E8FC2B41D5EBB8F7887DEFD468AF19AC76E94B7F452E668555CD
C44506FE6E1EDE5A104008755ABF5B6ACE51F1A84AD656A2DCCC7F2C39C0ECA2
ED88B5C4A8BE75F5DA0400817A9514BDCB38E602AA3FE463D39CEC523DCD3268
6768F27CADD154E4F98704F815901825550609B11D2A3F871AA3DB97D351DC52
D19F51871484CC4A737196BDB048193AD73F7F6BD061EC813766516EBA26E406
1DD7AE853911217095D2254337BEDECEE7267EEA1AC9D0840EAF13506F40C9AB
B6F321A48812DC922B26953020C9A60949EC429A921033CFAF1E9F7D088EE628
F923B85549CF4D2F87C11F4CDEB5ABB408974AEA8235AA68ACC849736EBDDE28
0F6B87DB9F0AE16D439B92514B3A63AE294AB5232901BBD8D87F14BE47F7A67C
BE074196291CCF74B3C4C8BD292F92DA99EC37A25DC8AF651BD0BA3F0D020349
B3ABDC2B792CB4B0160BDCC291DCB13B31078D852BD20AE01AE0908A0B46B72F
BB83ECBDD3C3DD6EC0A63B4C0CB480EDB748165ED3A4A8720CB6605AC7173A6C
931308CFE733376E19D6CD2401E27F8B2945CEC0B9C696AEBE7029EA76D45BF6
Malware delivery URLs
We recommend blocking the full URL in order to avoid false positives or operative disturbances.
hxxps[:]//www[.]google[.]com/url?q=hxxps[:]//www[.]dropbox[.]com/scl/fi/zi9ad2pp8gdqv2j5ajuda/01-CITACION-DEMANDA-EN-SU-CONTRA-JUZGADO-PENAL-01-CIRCUITO-ESPECIALIZADO-EXTINXION-01[.]zip?rlkey%3Dra9x4qs1mg7r7prxh0qbhjh08%26st%3Ds5ausk7x%26dl%3D1&sa=D&source=editors&ust=1721672080375620&usg=AOvVaw1Cb3A9CMaa_JCWCYpBDIuT
hxxps[:]//www[.]dropbox[.]com/scl/fi/zi9ad2pp8gdqv2j5ajuda/01-CITACION-DEMANDA-EN-SU-CONTRA-JUZGADO-PENAL-01-CIRCUITO-ESPECIALIZADO-EXTINXION-01[.]zip?rlkey%3Dra9x4qs1mg7r7prxh0qbhjh08%26st%3Ds5ausk7x%26dl%3D1&sa=D&source=editors&ust=1721672080375620&usg=AOvVaw1Cb3A9CMaa_JCWCYpBDIuT
