Cyber Threat Profile MALTEIRO

Overview
The following post aims to analyze the modus operandi, infrastructure, tools, the malware used, and the TTPs of the group of cybercriminals named Malteiro by SCILabs, which operates and distributes the URSA/Mispadu banking trojan. On the other hand, an investigation of the most recent banking trojan distribution campaigns is presented, showing the potential risk for the information of Mexican and LATAM bank account holders. Although URSA/Mispadu campaigns have been launched since the end of 2019, it has undergone various modifications over time to turn it into a more sophisticated and difficult to detect malware. Based on research by SCILabs, an update campaign for the banking trojan was identified and is currently active. This malware reuses and improves some TTPs used by its first versions, which were previously analyzed in some security blogs.
Region of operation
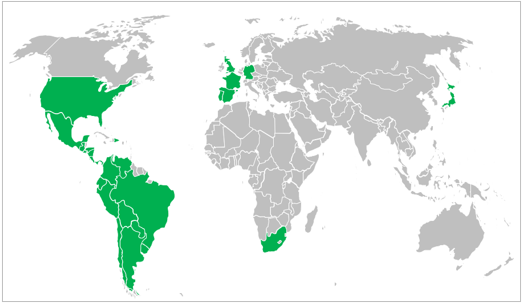
According to the evidence compiled by SCILabs, the campaign is mainly directed at USA, Mexico, LATAM and other countries of the European, African, and Asian continent. Some studies suggest that URSA/Mispadu is one of the banking trojans that most affects the region.
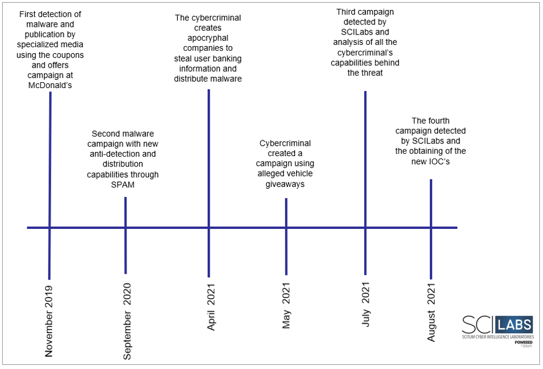
Based on the information collected and analyzed by SCILabs from closed and public sources, the timeline of the identified campaigns is shown below:
Who is affected?
During the investigation SCILabs identified that the phishing campaigns are mainly directed at Mexico. Based on SCILabs telemetry, the top industries that could potentially be targeted by these campaigns are listed below:
- Financial industry
- Food industry
- Communication industry
- Health industry
- Retail industry
- Manufacture industry
- Service industry
- Government industry
How do they work?
Threat context Malteiro is a group of cybercriminals who operate, manage, and sell the URSA/Mispadu banking trojan, as well as the tools for installation and configuration. With the information obtained from the research conducted by SCILabs, it is possible to determine that cybercriminals use the Malware-as-a-Service (MaaS) business model with URSA/Mispadu.
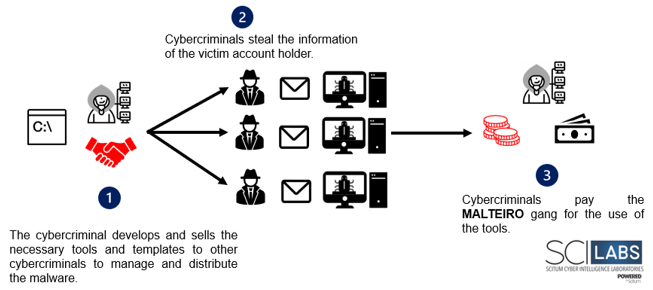
Likewise, they oversee the creation of campaigns and other techniques for the distribution of malware as can be seen in the following image.
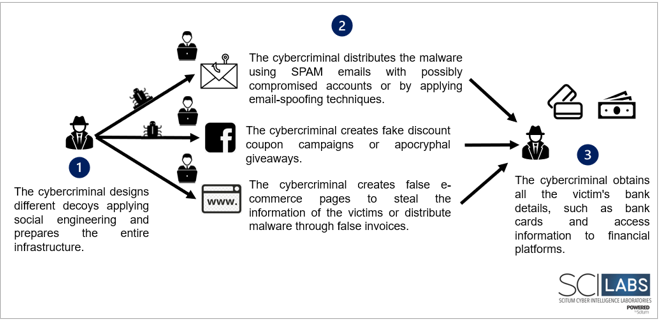
URSA/Mispadu is a family of trojan-type banking malware mainly targeting Spain and Mexico which was discovered in November 2019. The malware was written in Delphi and has different capabilities such as: screen capture, simulate mouse and keyboard actions, as well as log keystrokes. Malware can be updated through a Visual Basic Script (VBS) file that is automatically downloaded and executed. During the infection process, the malware collects the following data from the victim’s computer:
- Operating system version
- Computer name
- Computer language
- Installed antivirus
URSA/Mispadu’s entry vector is spam and malvertising, like other active campaigns in the region. Fake discount coupons are used in campaigns, as well as malicious emails refer to overdue invoices, attackers create a seemingly urgent situation that then persuades recipients to download a .zip file of malicious URLs. Social engineering as a method of spreading malware Apocryphal companies used to create malware In the investigation process, SCILabs observed that the cybercriminal uses apocryphal e-commerce companies that are used to distribute URSA/Mispadu malware through fake invoices and steal customer banking information. Next, one of the sites called “baratomx” that is a fake e-commerce page created to distribute malware is shown:

Fake coupons, giveaways and prizes based on the impersonation of banks in Mexico Additionally, the cybercriminal has shared on social networks such as Facebook, fake McDonald’s discount coupons or giveaways for vehicles that lead to malware pages where the brand impersonation of banks is used.
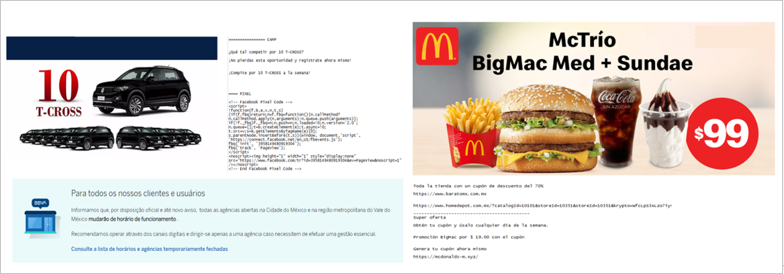
Among the malvertising campaigns identified by SCILabs, there is also one related to an alleged giveaway of 50 iPhones which was also distributed through social networks. Below is an analysis of each of the malware campaigns managed by cybercriminals:
First campaign distributed through malvertising and spam
In this campaign URSA/Mispadu operators placed sponsored ads on Facebook offering fake discount coupons for McDonald’s. In case of clicking on one of the advertisements, the potential victim is directed to one of the apocryphal web pages which, upon clicking the button suggested by the advertisement, will download a ZIP file containing an MSI installer. Occasionally, this ZIP file will also include legitimate software such as Mozilla Firefox or PuTTY, but they are mere decoys and are not used at all. The cybercriminal compiled two different versions of the banking Trojan depending on the country it is attacking. In addition to that, they decided to use different installers and later stages for each country attacked.
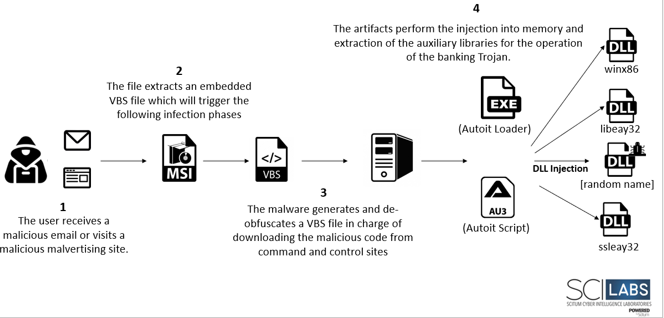
Second campaign distributed through phishing campaigns
This campaign was characterized by the URSA/Mispadu operators sending phishing emails of apocryphal overdue invoices, Mexico being the most affected country; in countries such as Portugal and nearby countries, phishing campaigns were sent impersonating various entities such as Vodafone or the Portuguese judicial police. In this campaign the cybercriminals persuade the recipients of the emails to download a .zip file of malicious URLs, the .zip file, as in the previous campaign, contains an MSI installer that contains a Visual Basic Script. This is followed by the download of two more droppers and three obfuscation layers that, when removed, produce the final .vbs file that runs an AutoIT Loader that loads a Delphi binary containing the Trojan’s code and processes into memory. The malware uses names and logos of legitimate banks to create windows and overlay the victim’s browser to steal their bank details. The binary also uses 2 legitimate tools, NirSoft’s WebBrowserPassView and Mail PassView, which are used to steal the credentials stored in the victim’s browsers and email clients. Some of the functionalities found in this version of the Trojan are that if it detects a virtual environment such as: Hyper-V, VirtualBox or VMWare, the script ends the execution, it also verifies that the victim’s computer has a code corresponding to the languages: Spanish – Spain, Brazilian Portuguese, Spanish – Mexico, Portuguese – Portugal or Spanish, if the system uses a language ID different from those listed, the attack process stops, also the attack ends if the computer name is “JOHN-PC“. Technical Flow
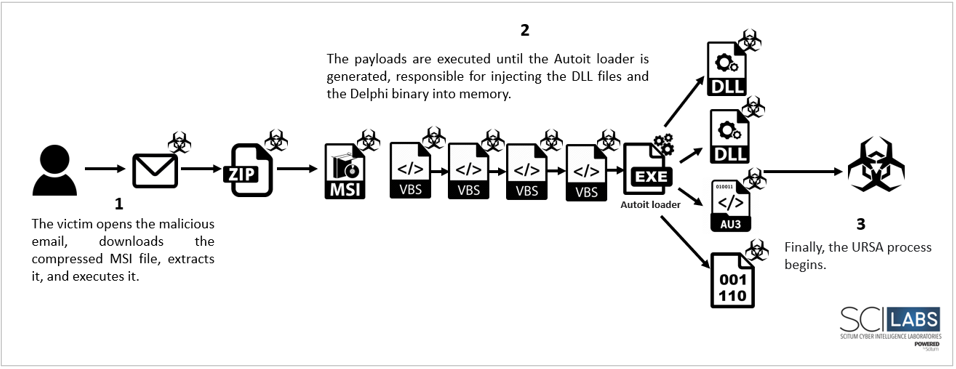
Third campaign analyzed by SCILabs
Based on the analysis of the entire campaign, SCILabs identified that with respect to previous URSA/Mispadu campaigns, the TTPs used by cybercriminals have evolved, the actions that cybercriminals take to infect computers are the following: The cybercriminal group behind the campaign has a large infrastructure for the distribution, storage and management of computers infected with the URSA/Mispadu banking trojan. After the phishing email is sent and downloaded and executed by the victim, another .vbs file is downloaded that makes a GET request to an .xml file that contains another .vbs code. This code works as a dropper to obtain the files: Autoit script and an executable loader. The aim is to inject a malicious DLL corresponding to URSA/Mispadu into memory and download the necessary plug-ins to carry out its malicious activity. Technical Flow The victim receives the phishing email related to an invoice which contains a compressed file attached. If the victim extracts and runs it, the infection flow continues as shown in the following diagram.
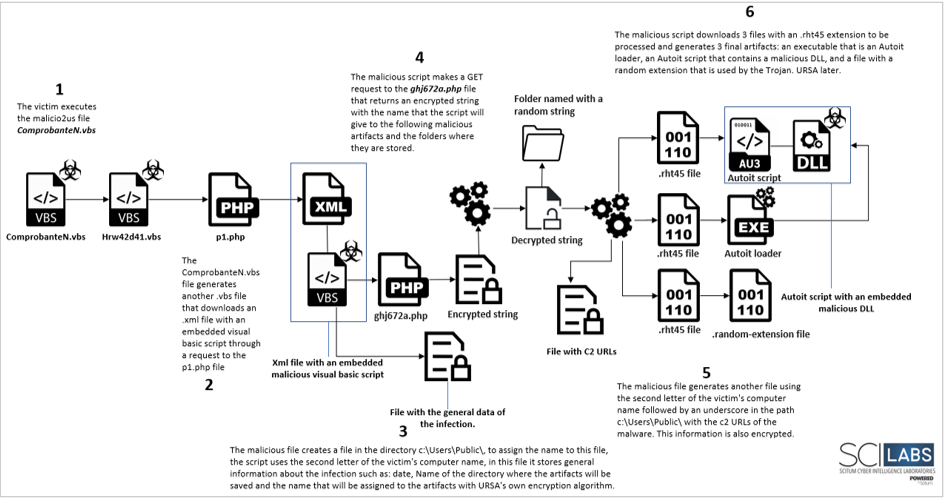
As in the previous campaign, to create, download and process the infection artifacts, the dropper, as in the version of the second campaign, verifies that the language code of the victim machine is Spanish – Spain, Spanish – Mexico, Portuguese Brazil, Portuguese – Portugal or Spanish, and in addition, that it does not have the name “JOHN-PC” and verify that it is not running in a virtual machine, as shown in the following diagram.
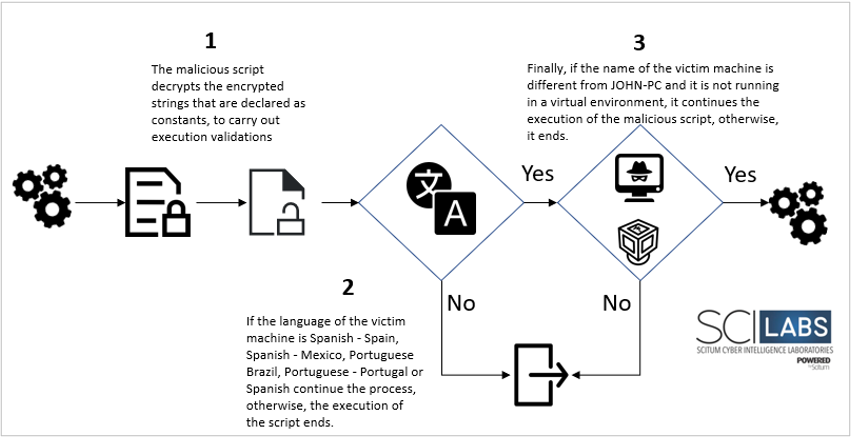
Once the final artifacts are generated: Autoit loader, autoit script with embedded malicious DLL and the random extension file, the ShellExecute method is called by the malicious script and loads the Autoit script with the loader to continue the infection. After the malicious DLL is loaded into memory, two compressed folders are downloaded, containing: ssleay32.dll and libeay32.dll that are associated with the OpenSSL Toolkit used by the trojan. In the last stage, this malware can create apocryphal banking windows superimposed on the browser when victims enter banking portals to steal their credentials, in addition the Trojan uses two legitimate tools, WebBrowserPassView and Mail PassView, that are used to extract the stored credentials in browsers and e-mail, finally the data is sent to the C2 server. When the trojan detects that a victim enters a banking portal, it establishes a connection with the C2 server, with which the cybercriminal gains control of the compromised computer, allowing him to use different commands on demand.
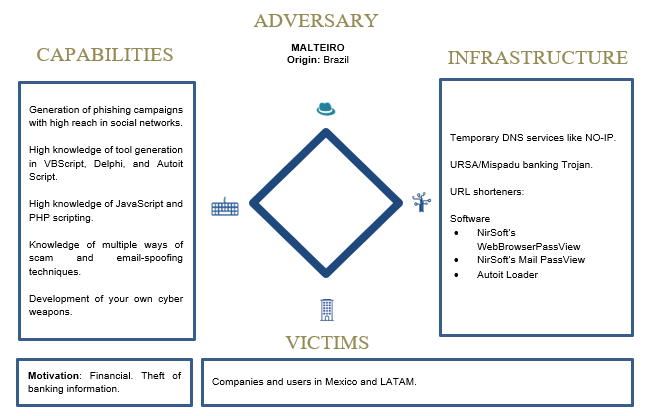
Diamond model of Malteiro
Threat profiling based on the MITRE Matrix (PRE-ATT&CK)
Based on the research carried out by SCILabs, the following PRE matrix was obtained
| Reconnaissance | T1592.002-Software | T1592.004-Client Configurations | T1589.001-Credentials | T1589.002-Email Address | T1598.003-SpearPhishingAttachment | |||||
| Resource Development | T1583.001-Domains | T1583.003-Virtual Private Server | T1583.004-Server | T1586.001-SocialMediaAccounts | T1586.002-Email Accounts | T1587.001-Malware | T1585.001-Social Media Accounts | T1608.001-Upload Malware | T1608.002-Upload Tool | T1608.005-Link Target |
Threat profiling based on the MITRE Matrix (ATT&CK)
From the analysis of the artifacts and TTPs, the following ATT&CK matrix is obtained:
| Initial Access | Execution | Persistence | Defense Evasion | Credential Access | Discovery | Collection | C&C | Exfiltration |
| T1566.002-Phishing: Spearphishing Link | T1059.005-Command and Scripting Interpreter: Visual Basic | T1176-Browser Extensions | T1140-Deobfuscate/Decode Files or Information | T1552.001-Unsecured Credentials: Credentials in Files | T1083-File and Directory Discovery | T1056-Input Capture | T1573-Encrypted Channel | T1041-Exfiltration Over C2 Channel |
| T1106-Native API | T1547.001-Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1036-Masquerading | T1081-Credentials in Files | T1057-Process Discovery | T1115-Clipboard Data | T1132.002-Non-Standard Encoding | ||
| T1204.002–Malicious File | T1027-Obfuscated Files or Information | T1552.002-Unsecured Credentials: Credentials in Registry | T1518.001-Software Discovery: Security Software Discovery | T1113-Screen Capture | T1001-Data obfuscation | |||
| T1055.001-Dynamic-link Library Injection | T1555.003-Credentials from Web Browsers | T1010-Application window discovery | T1560-Archive Collected Data | |||||
| T1497-Virtualization/Sandbox Evasion | T1082-System Information Discovery | T1005-Data from local system | ||||||
| T1614-System Location Discovery | T1074-Data Staged | |||||||
| T1497.001-System Checks |
Recommendations
- Constantly carry out awareness campaigns about the different techniques of social engineering and phishing at all levels of the organization.
- Avoid downloading and executing suspicious email attachments, especially if they have extensions: “.exe”, “.vbs”, “.jar” and “.msi”.
- Create strong password policies and apply the principle of least privilege for users within the organization.
- Keep all computer equipment in the organization updated to the latest version of the operating system and security updates applied.
- Consider the indicators of commitment shared below.
Associated IOCs
URSA banking trojan D2099233A72C282E64E85ABCDDB284CDFFC18B24E088947254F9B55670F52F83 87340165EA0FB1E06364AA479ACB2FF104CEDDEAACE0E548F687B2960A28ED36 09886CE8106CD07A3694F221DD19899AA29A72826F2FEE8A8BAA1B044704737A 91A687ED27F469797317D82B8EB2BCEB4DFC84973B4BFB00F15E951DFDAEA9AE 0916767D0EAA4E3E94DAF740B621C62258832F3F811FE4FA1C9536227FCBEA17 C9E22D965771D8A8005D79B771AF602B95C14B0E23187ED4F718FFC0E87B26E2 4BDA083A30A82698F57F672C5A333ADC84F37FE53D8FED6D8AA7AA31ECAC02FC 02F541522898F87AA36552EAC38A70DC8A23B59E2BF6D4F65EE55485B05EDAAB
