Overview
The following report describes the identified TTPs and IOCs of a campaign that is distributing the Mekotio banking trojan in LATAM. It was identified and analyzed by SCILabs while conducting a threat hunting during the third week of September and has been monitored in the last days by the team. This trojan aims to steal information from multiple banking institutions using fake forms to impersonate original sites and capture bank credentials, in addition the trojan also seeks to hijack cryptocurrency transactions by replacing wallets copied to the clipboard by the cybercriminals’ wallet.
During the investigation, no further details were obtained about how this campaign is being delivered; however, based on the evidence collected, SCILabs considers the use of phishing by email and websites as the main initial attack vectors with a high level of confidence. On the other hand, this report will show the analysis of each of the elements of the campaign, which, based on the telemetry of SCILabs, its modus operandi supplants the name of Mexican and Chilean tax institutions such as: Secretaría de Administración Tributaria (SAT) and Servicio de Impuestos Internos (SII), to be used as a pretext in phishing emails.
After analyzing the campaign and the artifacts, SCILabs determined with high confidence that the attacker’s general objective is to install the banking Trojan on common users’ machines, to steal user information in LATAM, particularly Chile and Mexico.
Additionally, with the intelligence of SCILabs and the information obtained from public and private sources, it is possible to determine that the campaign has the potential to begin to spread in other countries of LATAM, expanding the banking institutions it is targeting due to its versatility and the rapid evolution of its TTPs.
How could it affect an organization?
The campaign has the potential to financially affect an organization because Mekotio’s main objective is to steal bank information from users. In addition, during the analysis of the trojan, some capabilities were found to drop other types of malicious artifacts on demand, so, it could be combined with other types of malwares such as ransomware. This could make the organization’s information assets subject to unauthorized viewing, hijacking, and data leakage. Considering that the trojan has evolved its TTPs compared to previous campaigns to make it difficult to detect and analyze, it is important to be aware of these types of threats.
Analysis
Threat Context
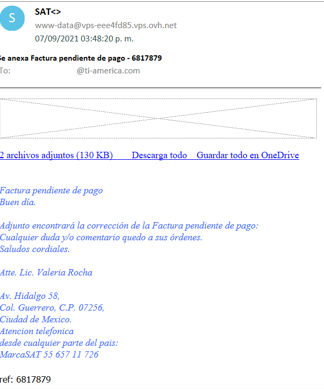
During the threat hunting process, three artifacts were identified that share similar behavior. SCILabs analyzed and investigated each of the items to determine if they were part of the same campaign. Based on the research carried out by SCILabs we consider with a high level of confidence, that Mekotio’s distribution campaign in Mexico is by means of phishing email trying to supplant the Secretaría de Administración Tributaria (SAT) and with a medium level of confidence that the campaign directed to Chile is through an apocryphal site of the Servicio de Inpuestos Internos (SII).
Attack flow
Campaign directed to Mexico
Campaign directed to Chile
Malware analysis
As a result of the analysis of the artifacts carried out, SCILabs determined that the campaigns targeting Mexico and Chile use two different versions of the Mekotio trojan. The main difference between the versions is that the artifact aimed at Chile contains within it the MSI file the three files necessary to run the banking trojan, instead of downloading them as in the version aimed at Mexico, however, they share some capabilities that are listed below:
- AntiSandbox capabilities
- Packaged banking trojan DLL
- Obtaining information from the operating system and architecture
- Detection of active open windows and the deployment of embedded resources according to the institution from which the malware will steal the information
- Clipboard hijacking
- Theft of bank information
The MSI files of the malware were analyzed and in the case of the artifacts directed to Mexico, it was possible to observe the download URL that contains the AutoHotkey executable, its script, and the DLL of the Mekotio trojan. In the case of the artifact directed to Chile, it was found that the malicious devices are within the MSI file.
Also, the necessary conditions for the malicious MSI file to be executed were obtained, of which mainly the following were observed:
- The MSI file cannot be executed on computers that have names such as: JOHN-PC, LISA-PC, SVIARTA, among others
- The MSI file cannot be run in virtualized or SANDBOX environments
- The MSI file can be run only if there is an Internet connection
The MSI file cannot run on Windows 9x versions
It is important to mention that once the MSI file verifies that the conditions to be executed are met, it drops a xy.txt or ko.txt file in the C:\ProgramData directory that serves as a verification flag to continue with the infection.
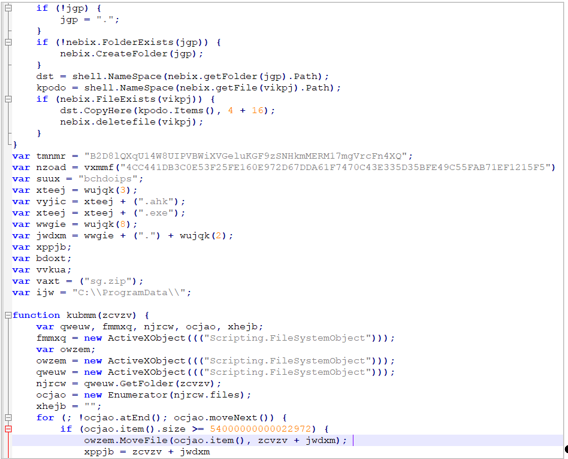
One of the characteristics to highlight within the custom actions of the MSI file of the campaign directed to Mexico is that it contains obfuscated JavaScript code that fulfills the following functions:
- Verify that the compiled folder that was downloaded by the MSI file exists in the C:\ProgramData\%RandomName% directory and that it contains the malicious artifacts of the Mekotio trojan
- Extract and rename the artifacts
- Delete the downloaded compressed folder
- Create the btdae file to validate if there is a previous infection on the computer in case the MSI file is executed more than once
- Create the registry key in HKCU\Software\Microsoft\Windows\CurrentVersion\Run\%RandomName% to generate persistence
- Run the AutoHotKey file to load the Mekotio trojan DLL into memory
All operations are performed through ActiveXObject instances.
At the end of the infection process, the victim’s computer is rebooted to run the .ahk script later through the AutoHotKey executable and load the Mekotio trojan DLL into memory. In the case of the campaign directed at Chile, the victim machine is not rebooted, and the trojan is executed immediately after infection.
Once the trojan is loaded into memory, the flag [%month-year%].txt file is generated in the path C:\ProgramData. The trojan waits for the user to open an internet browser to generate a sub-process that will oversee displaying apocryphal windows trying to impersonate banking institutions. Once the user enters a banking page, a nod32.block file is generated, communication with the C2 site begins and artifacts related to apocryphal Windows are dropped in the path C:\ProgramData\%BankingInstitution%.
An important feature found during the analysis carried out by SCILabs is that the trojan can replace the contents of the clipboard. With a medium level of confidence, we consider that when a cryptocurrency wallet is copied, it is replaced by that of a cybercriminal.
Cybercriminal Wallet: 18MvuBqbvrb6E4KseC91YRFjYNBKfcVp5f
It is essential to mention that based on the analysis carried out by SCILabs, with a medium level of confidence, we consider that the Mekotio trojan c2 sites can detect connections through VPN and geolocation to prevent the trojan from being executed in unwanted locations, in addition, the ability to download artifacts on demand was identified. During this analysis a batch file that eliminates the DLL of the Mekotio trojan was downloaded.
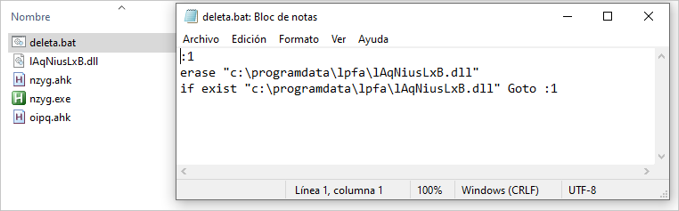
Most significant changes in Mekotio campaigns
After the previous campaigns, SCILabs continued to monitor the behavior of the Trojan in the region, and we identified that Mekotio can abuse legitimate software such as VirtualBox Guest Additions Tray Application and Disc Soft Bus Service Pro, from DAEMON Tools, to load itself into memory. In addition, the malware is accompanied by some legitimate DLLs, such as sptdintf.dll, ipworksedi20.dll, ssleay32.dll, or libeay32.dll, as observed in other similar analyzes.
SCILabs identified that the cybercriminals behind Mekotio are capable of constantly evolving their TTPs.
During the monitoring in the region, SCILabs managed to identify the use of compressed “.bat” files to distribute the Trojan.
In addition, a PowerShell script to verify the geolocation of the victim, which must correspond to Brazil, Chile, Mexico, Spain, and Peru, validates if it is running in a virtualized environment and download the artifacts necessary to carry out the infection.
Below, we present the attack flow of the last identified campaign.
Based on the evidence found, SCILabs hypothesizes that the cybercriminals behind the threat are Brazilians due to the typical Brazilian jargon used in the source code of their artifacts.
TTPs observed aligned to MITRE’s ATT&CK framework
Below is the MITRE matrix based on the banking trojan campaign:
| Initial Access | Execution | Persistence | Defense Evasion | Credential Access | Discovery | Collection | C&C | Exfiltration |
| T1566.002 Spear phishing Link | T1059.003 Windows Command Shell | T1547 Boot or Logon Autostart Execution | T1140 Deofuscate/Decode Files or Information | T1179 Input Capture | T1083 – File and Directory Discovery | T1056 Input Capture | T1571 Non-Standard Port | T1041 Exfiltration Over C2 Channel |
| T1059.007 JavaScript | T1036 – Masquerading | T1010 – Application window discovery | T1115 Clipboard Data | |||||
| T1204.001 Malicious Link | T1027.005 Indicator Removal from Tools | T1082 System Information Discovery | T1005 Data from local system | |||||
| T1204.002 Malicious File | T1027.002 Software Packing | T1614 System Location Discovery | ||||||
| T1497 Virtualization/Sandbox Evasion | T1016.001 Internet Connection Discovery | |||||||
| T1112 Modify Registry | T1497.001 System Checks | |||||||
| T1012 Query Registry | ||||||||
Assessment
According to SCILabs telemetry, as in other campaigns, it has been observed that many trojans targeting LATAM use common techniques and share some characteristics. They use droppers generally obfuscated in other programming languages; they contain backdoor functionality; they use legitimate tools like AutoHotKey; they use living off the land techniques; rapidly evolve their techniques and dynamically generate malicious artifacts to make their detection and analysis difficult.
A clear example is the case of the Mekotio Trojan, previous campaigns had been observed where Autoit was used to load the malicious DLL in memory, however, in the last campaigns we can observe that the Trojan began to use AutoHotKey as a loading tool, in addition to add sandbox detection techniques in all phases of infection, packaging and encryption of the artifact strings corresponding to Mekotio and detection of VPN connections and Geolocation in order to make their detection and analysis more difficult.
During the analysis of these campaigns carried out by SCILabs, a technique that is commonly used by cybercriminals to eliminate their malicious artifacts in case of being detected was detected, downloading tools for this purpose; this capacity could easily be used to combine its functionality with other types of malware, such as ransomware, which could jeopardize the security of organizations’ information assets, that is why it is important to monitor these types of campaigns.
It is important to mention that based on SCILabs telemetry, banking Trojans that target the region commonly target users of the most representative banks, trying to trick users with apocryphal windows to steal their confidential information. It is common for the initial attack vector of this type of campaign to be phishing emails or sites that impersonate representative organizations of each country. In Mexico, as we saw in the analysis of this campaign, it is common for an attempt to impersonate the SAT, for what is extremely important to constantly carry out awareness campaigns at all levels of the organization so that users know the social engineering techniques that cybercriminals use to deceive.
IoC
E262FEBEBFC91330540D721CF2773E53254B29BC669E74785F994C0268A930A3
9AF066B849412783F1A6A7FED9AB354CB281858AD22A2570B7F0B63AAAFF18E3
D22B4ABE87C3037194FF131747CC732CC8CB754D1828A68CE82D157C36B34F67
D4692FB2225C871958994669CFAC40DD26BCBC31674CA7261174B2F790356F27
EAC9861E590E1246E3A81D227B5C425B8382C5B259184FBC28C4D0E7BEE98186
945ADADA6CF6698B949359D9B395A5F905989D0D1EB84F537DE492ECC1263148
CEA3FA8EC56E8BC2DFA4B3DFFEF3E847118734CDF250AC87E423DAE450BA6AE7
DBBBA9C48D471E3361882CB41ED716B588B6A112D22C40611EEC9FD52AE65F72
A72F2415046908DB8F26DAFB91F98F3DE6D6CFC302A877BD52DA6C845CFA1BA2
BC6ADE51046ED777632A5F30FF895E8CDE04910EA6DCA6061B2FE2C7ADFD072B
945ADADA6CF6698B949359D9B395A5F905989D0D1EB84F537DE492ECC1263148
594236A8F3090FD8FF0D078CE17B3E512CD87FFA37A94F4162BEC9E72BDB0E9E
5FE74163D2668B86F559079F981A4ECB5D7E899135A005CB37E013BAC88E6E4F
99246C214E12BACD6B6DE328F635AF678CB17078F06B39356A1BC9E3CB98058F
93729227D752399266E1118098FD2C417F25D48CA3C45313A8697DA511A22CA8
945ADADA6CF6698B949359D9B395A5F905989D0D1EB84F537DE492ECC1263148
E5C3F24CAC6ACC208D1B913776B8A5815188CF38CC9D7E81AB2C9612498F6F85
40A1B20169FB746D5E0218132C9D5D51C2C8FC7BAA385CAA8C7C317F19DAF0F0
D320315812AC19BEEE13063800A0CF8264C1A64242F14608F8687CD6F7A4A5ED
945ADADA6CF6698B949359D9B395A5F905989D0D1EB84F537DE492ECC1263148
B83413C5C363F8725B5C9EFCCAAA9CDA87724C4998B3A937F84ECE489F1E0F22
A921451F6635E5D1CB6C35C07A81FD7DD726B4F1996FE3139A9C1634F8AC991F
D36AF74F89DDB6599F1977FDEBF8DBAD64A128BAB6362D2A90E70C89DE25C86F
DCBA29F7634A9AD9EFC2468753AF42FAC6D5E0326E0A7F1627E7C9F2AD7D73AF
56C8C4E9144EF009102DE62159FEF1BF397A725F6C584BE790F107DEF68515B6
50A86C02B5A2A2B1B962284B4DE23C1479AA8717750986B30B750D339245830D
945ADADA6CF6698B949359D9B395A5F905989D0D1EB84F537DE492ECC1263148
D5C0A23B75BF5ED6E0161DB5A57974864A5EB5738E80804BDD30EEAF6817302E
6544F678296B9590A7F6F51FB52BB346EBF75C92D600C2159AB61CB825C772D1
A86F736AD7C91999FD33E0A008E0E7CF1E0D5900795499F50578A38D4C1A16FA
A322FE07DBB51BE33EE92E7295A9EC7FB1A6996CEF000F2723E5CEEEB81F4A5B
945ADADA6CF6698B949359D9B395A5F905989D0D1EB84F537DE492ECC1263148
111AD210C0460F6281EF3D5362D7F3110099B0CBEF2E863B4D8F4270A8617FDD
C19725BFA6EC88FE87564DE040634072F89AAF28E7E10B2B7E055229CCD5E8AB
F9DF0093B5903CBCB735A3E279F9BE2837618D507375323EC5A2E06F48B844E5
325A52F9DCCF111325DFAB8D3BDFACB2E87D86DC8A1356E68A5EAE4684F03C37
1B1F0E65B97E3E244BAA40C683E0F8D5F6E63718864CCCE4C1C26F0B7C832AD5
ACFA710206FE3C68BAF2FC782A7E0F75B13F14A4990837CE8B2F8F83F2D63815
DB8002A405F028C2E3538F8AF4ADB51C2E996F687914287BDA02FB2AE85FE80C
EAFDC2A09BC696D06218541314110E87EA2DB3440125252C9EEBDAA03A14DA50
D0FE2C01297574D7482FBC33FA748863FE5D0C1EE32755128833488E146DDF08
BD0B0417BE5C047F9160F8C97E7E10D1313F350235EF235DC6BDEC9D5C4BE877
905F6E60A3B7C050EAD74F0F0C7D13CFDCF4415B8E7F6780BDE879985507CEDC
E99EBB043992341202F0645D0FCEEF847BCB231973AD42F2D9C6178AD354EC8C
FD011CAB980B5F4D18EFEC142AE5C64107E13569866B6688350247C724C12F15
2A30FE76A78BF9D1C3B3A731E92E2AEB0197E705BB658A1039B3135AE321E8FA
EXODUSWL[.]COM/WACUWACU/NOMEPARACOMPILAR[.]PHP
HOST[.]COLOCROSSING[.]COM[:]4470
GETAMAKEGIFTCARD.COM[:]4498
REDRAINBOW[.]DO[:]4439
40[.]124[.]76[.]15
185[.]66[.]41[.]156
20[.]106 [.]166 [.]75
PAUNAMAQUINA[.]SERVEBEER[.]COM
67[.]21[.]32[.]62
20[.]68[.]248[.]170
HXXP[:]//20[.]68[.]248[.]170/?A=Z0DEXUBSWD7FE45T3JHBMMJXCW3DON98P9LY3SRT
DEMICK@DEMICK.ADV.BR
LZ5[.]DUCKDNS[.]ORG/?3TMB_
HXXP://WWW[.]CARPINTARIASX[.]COM/?NIEBB2RGRFMP
HXXP[:]//POMPANO1[.]DUCKDNS[.]ORG/THERE[.]CARE
RENATONOMENGAO[.]COM/SESSION_WORKS_V2
LIBRASHOPPNG[.]NE
