New Banking trojan Silver Oryx Blade Activity observed in August 2024
Overview
This post aims to describe the TTPs and provide indicators of compromise related to a new banking trojan, which SCILabs named Silver Oryx Blade. Its main characteristics are the compromise of infrastructure, such as malware repositories, Minecraft video game servers, and the combination of different programming languages during the infection. SCILabs identified this threat in August 2024 through monitoring and threat hunting in LATAM.
The main objective of Silver Oryx Blade is to steal banking information from Brazilian users by monitoring the banking sites that they access through their web browsers.
This trojan’s distribution method is phishing emails, which use tax matters and supposed salary bonuses as pretexts. Those emails impersonate the Brazilian Ministry of Finance and the finance departments of organizations in that country.
SCILabs has identified the use of libraries such as WatsonTCP in Silver Oryx Blade, as well as the application of AES encryption in some chains (features that have also been utilized by the Coyote trojan). Furthermore, a domain used in the Silver Oryx Blade campaign was identified during the investigation, which is possibly related to a Coyote campaign. However, the differences in the TTPs and artifacts used in the infection chain are significant. Therefore, SCILabs has the hypothesis, with a medium level of confidence, that this new banking trojan is being distributed by the same malware operators.

How could it affect an organization?
Silver Oryx Blade can steal banking information from all types of users, including employees of organizations. Additionally, it has command execution capabilities, and some artifacts used in the infection chain have a low detection rate in antivirus engines on the VirusTotal platform, increasing the likelihood of successful attacks. If an attack succeeds within an organization, cybercriminals could leak or sell the stolen information on clandestine Dark Web forums or the black market, jeopardizing the organization’s information’s confidentiality, integrity, and availability, resulting in financial and reputational losses.
Analysis
Threat Context
In August 2024, SCILabs identified a malicious MSI file compressed in ZIP format through proactive threat monitoring in the region. Upon analysis, different TTPs from previously reported trojans by SCILabs were detected, like plain text payloads, which are undetectable by antivirus engines on the VirusTotal platform, along with other techniques described later.
Through retro hunt techniques, SCILabs identified that this trojan’s distribution method is through phishing emails (targeting Brazilian users) which use pretexts such as alleged salary bonuses, PIX transfers, and fiscal notices, impersonating HR finance departments and the Ministry of Finance of Brazil.
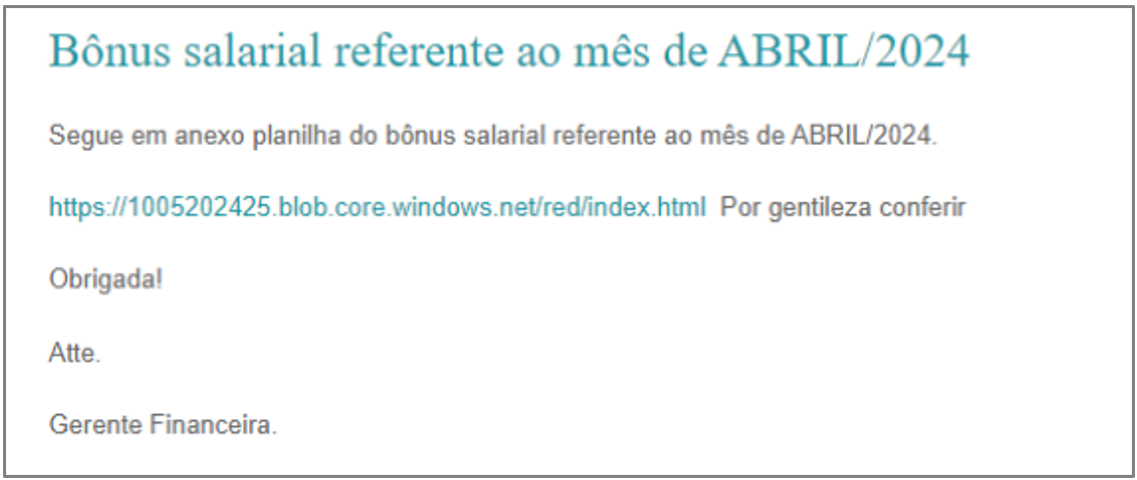

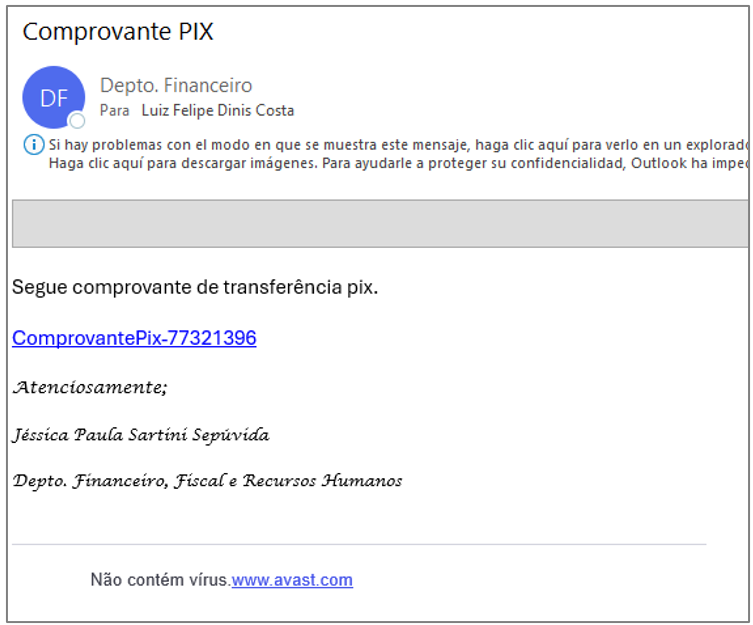
The threat actors behind this campaign use email spoofing to send malicious emails, impersonating the senders. During the analysis of one such email, the domain milkdavaca[.]com was identified and tagged by a user on the VirusTotal platform as part of the Coyote trojan’s infrastructure due to its use of the same SSL certificate and registrant. So far, the domain is still protected by the Withheld for Privacy[3] service. This finding suggests that the operators of Coyote and Silver Oryx Blade might be the same.
Most emails contain embedded URLs that redirect victims to sites that automatically download ZIP files. These ZIP files contain MSI droppers with names that simulate legitimate documents, such as PDFs (e.g. pdf.mes168.msi), office files (e.g. Ofic.01194.msi), or company names with a presence in Brazil, like VISU (e.g. visu.96178215.msi). The variety of these artifact names indicates that, in addition to the pretexts and impersonated institutions, the operators adapt the lures to the sociocultural context of the target country, in this case, Brazil — a common tactic in Latin American banking trojans.
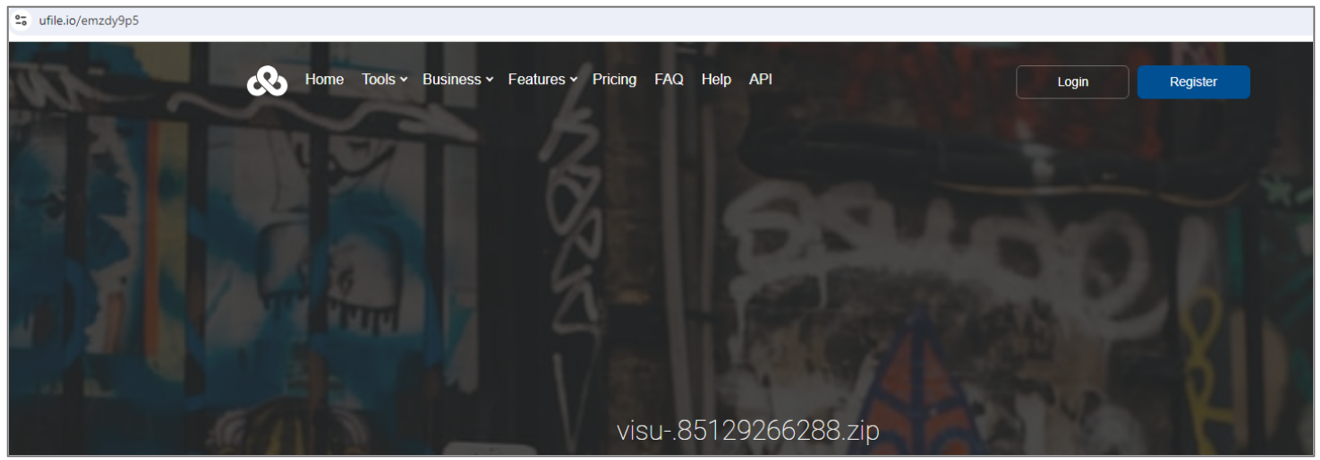
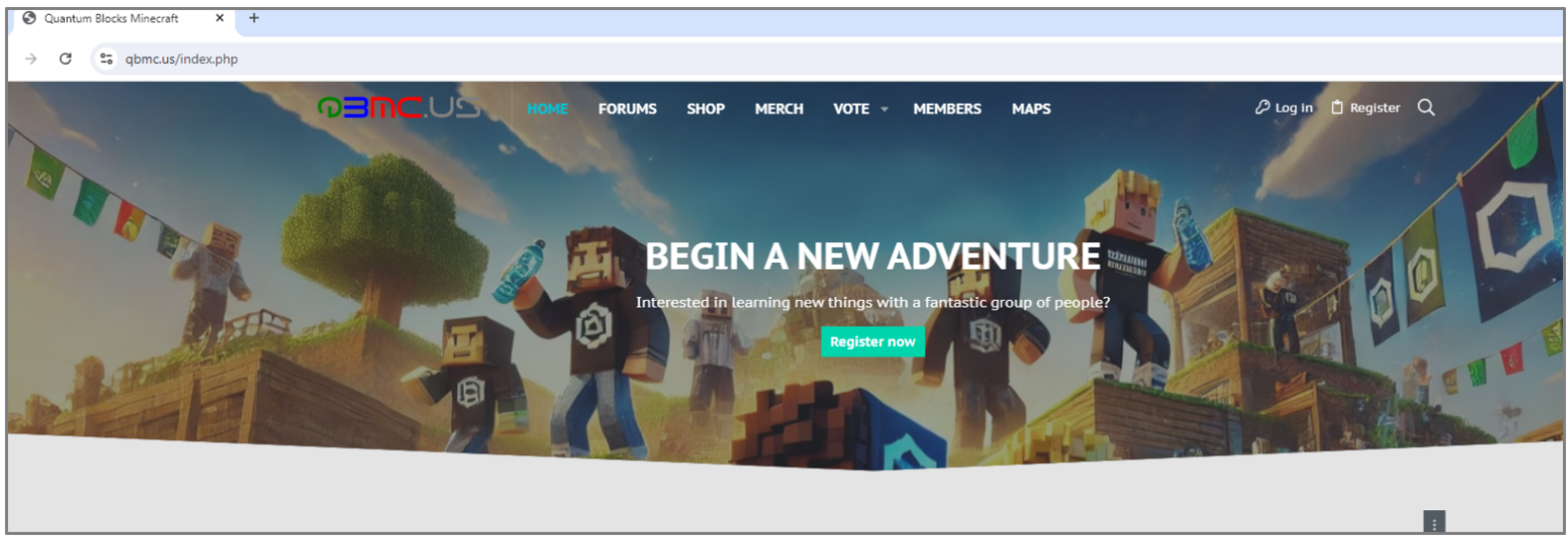
During the investigation, SCILabs discovered that the operators of this malware use link shorteners like bit[.]ly and file storage platforms like ufile[.]io, as well as compromised sites like a Minecraft game server, which was used around May 2024 to distribute the malware.
It is essential to highlight that SCILabs identified some overlaps with the Coyote banking trojan. These include general features like using specific libraries like WatsonTCP and AES-encrypted strings; however, the infection chain (detailed below) and the trojan show substantial differences compared to the Coyote campaigns previously reported by SCILabs, and investigations published in open sources.
Technical Summary
The file downloaded from the phishing email’s embedded URLs is an MSI file with various names, such as “pdf.mes168.msi,” “visu.96178215.msi“, or “Ofic.01194.msi,” among others. These files correspond to the first dropper of Silver Oryx Blade.
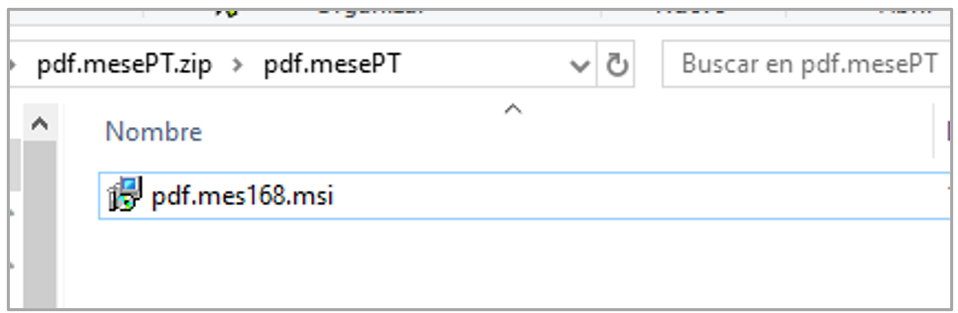
The MSI file contains the following artifacts:
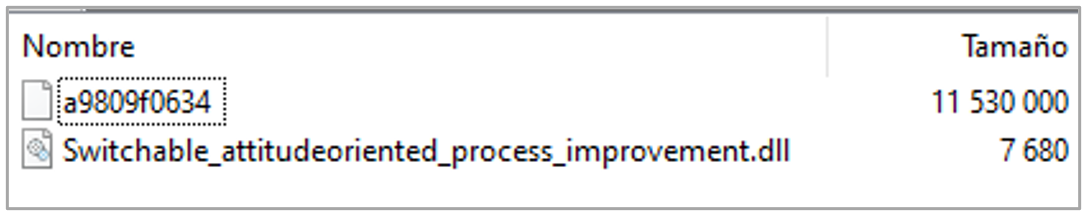
- Switchable_attitudeoriented_process_improvement.dll: This is a 64-bit PE file developed with C# .NET, which acts as a second dropper and aims to deploy the next and final stage of infection. This file performs the following actions:
-
- It reads the file “a98090f0634,” which is also included within the MSI and processes its contents. Then, it decodes all base64-encoded files found inside and writes them to the previously created directory. These files represent the final stage of the infection chain.
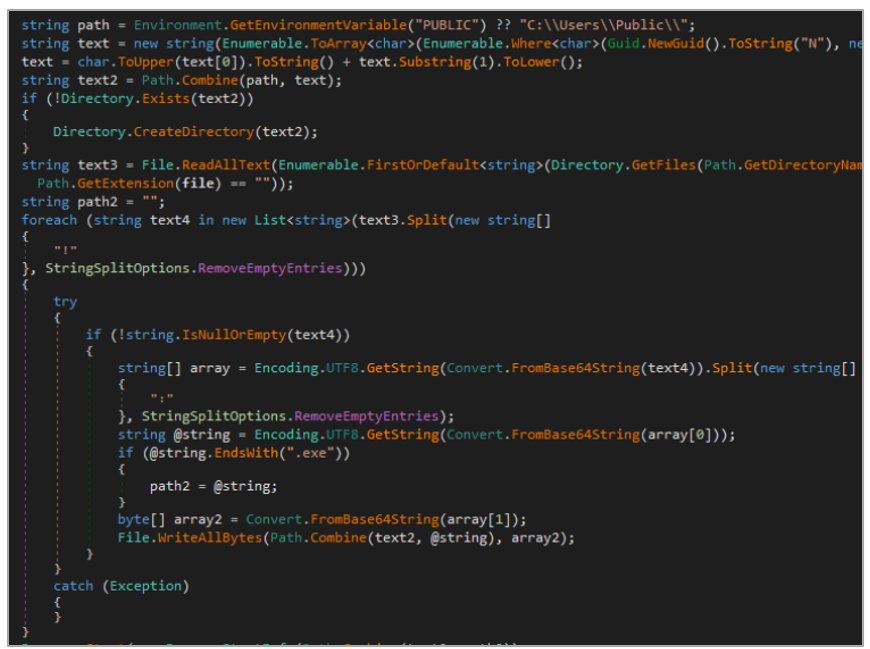
- a98090f0634: This is the base64-encoded payload processed by the dropper above. It contains the files that correspond to the final stage of infection, described below.
Once the victim executes the MSI file, the actions to install the final stage of the infection chain in the %PUBLIC%/[pseudo-random alphabetic string of “n” characters] directory begin. The following files are installed:
- EACefSubProcessª.exe: A legitimate executable from the videogame company Electronic Arts used to load the trojan into memory via DLL Side-Loading.
- libcef.dll: A loader developed in C++ used to load the Silver Oryx Blade trojan into memory.
- chrome_elf.dll: A legitimate Chromium library likely used by the trojan due to its use of the Chromium Embedded Framework (CEF), possibly allowing traffic redirection from the browser to the attacker’s C2 and capturing login information from websites visited by the victim.
- MqSFsKgLSw1GKqGcD5bP.txt: The AES-encryptedSilver Oryx Blade payload, loaded into memory by the libcef.dll loader.
- msvcp140.dll and msvcp140d.dll: Legitimate Microsoft C Runtime Library files used for string handling, mathematical operations, and file input/output in C++ applications, as in the case of this trojan.
- vcruntime140.dll and vcruntime140_1.dll are also legitimate Microsoft libraries responsible for executing C++ code and handling exceptions and resources, such as global variable initialization and runtime exception management.
An important point to highlight is the inclusion of legitimate libraries msvcp140d.dll and vcruntime140_1.dll, which correspond to the debug versions of the Microsoft C Runtime Library. This could indicate that the malware operators are still testing the trojan.
Once Silver Oryx Blade is installed, the second dropper executes EACefSubProcessª.exe, which uses the DLL Side-Loading technique to execute the libcef.dll loader, which then injects the AES-encrypted payload stored in the MqSFsKgLSw1GKqGcD5bP.txt file into memory.
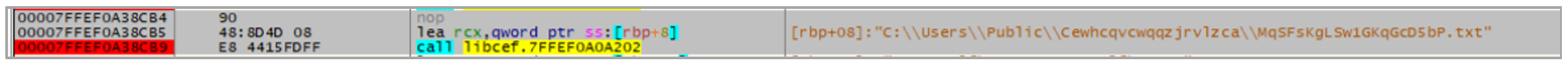
After its execution, the trojan achieves persistence by creating a shortcut in the startup directory: %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\EACefSubProcessª.lnk.
Finally, Silver Oryx Blade attempts to communicate with one of its configured command-and-control (C2) servers by connecting via a socket using the WatsonTCP library. Subsequently, the trojan begins monitoring banking windows of interest in Brazil to steal information.
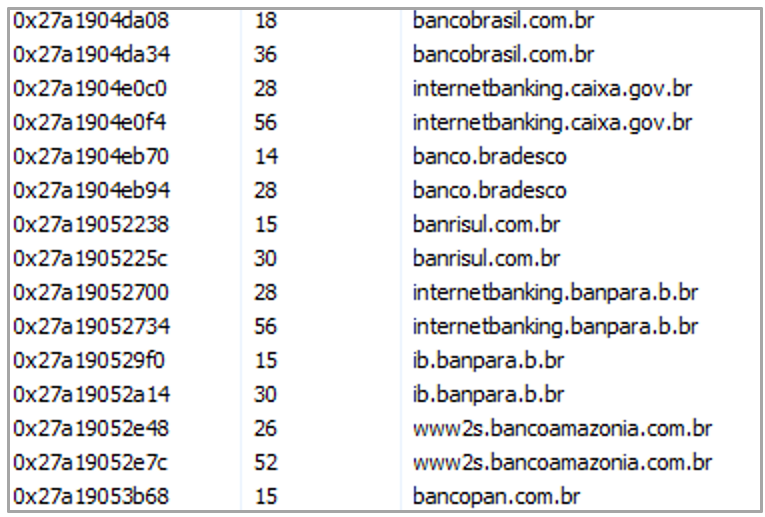
Among the banking institutions of interest to Silver Oryx Blade identified during the analysis are approximately 50 entities, including institutions like Mercado Pago and Binance.
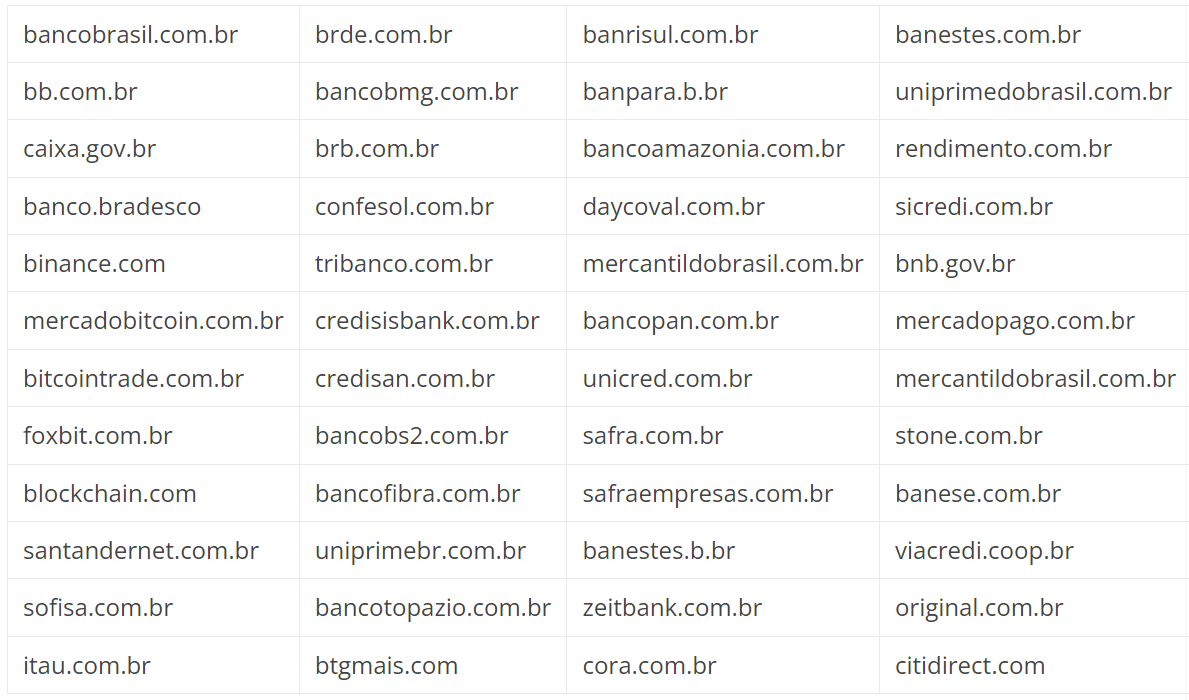
It is essential to mention that during the analysis, the Newtonsoft Json.NET Framework was identified as manipulating data transmitted to the C2. This is possible because the trojan operators used Fody Costura to embed .NET resources.
The infection Chain of Silver Oryx Blade:
- Execution of the MSI file
- msiexec.exe
- EACefSubProcessª.exe
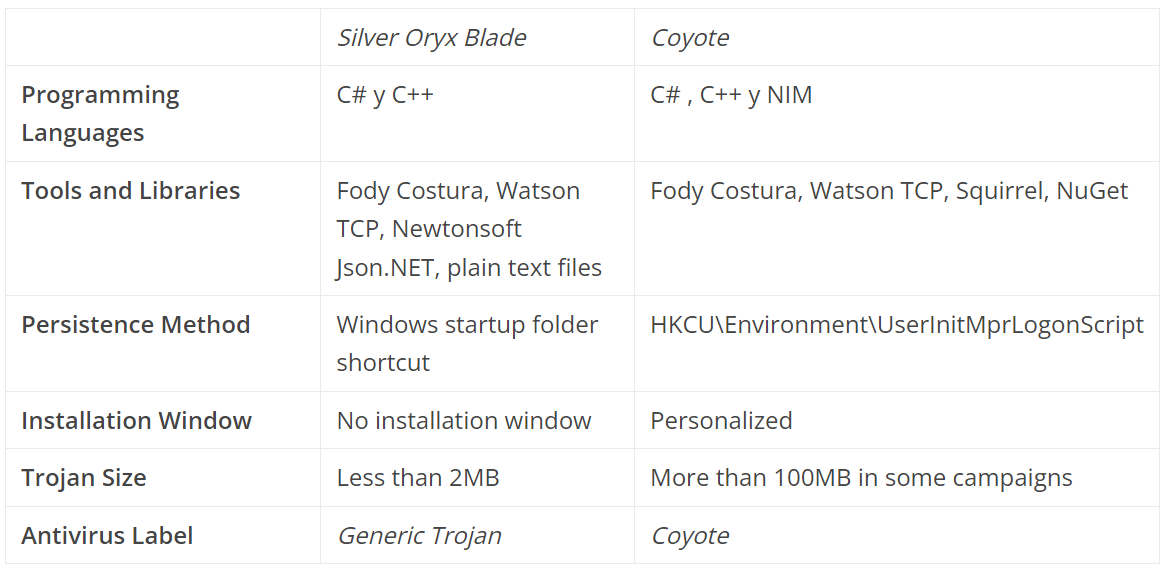
Key Differences Between Silver Oryx Blade and Coyote
Below are the main distinguishing features of Silver Oryx Blade, compared to previously observed Coyote trojan campaigns in the region. This analysis aims to provide greater clarity in identifying this new threat for future research. Since SCILabs has observed some overlaps between the two trojans, it is important to highlight these similarities, as they allow us to hypothesize, with a medium level of confidence, that the operators of Silver Oryx Blade could be the same as those of Coyote.
- Although Silver Oryx Blade uses WatsonTCP for communication with the C2 and AES encryption for strings, Coyote embeds these strings directly in its artifacts. Additionally, the new trojan stores its payloads in text files, sometimes using base64 encoding.
- Both, Coyote and Silver Oryx Blade, use artifacts developed in .NET and C++. However, Coyote also uses NIM and a wider array of tools, such as Squirrel and NuGet, with artifacts exceeding 100MB in some campaigns.
- Some DLL names used by both trojans coincide in specific campaigns, such as libcef.dll and chrome_elf.dll. However, Coyote uses a legitimate libcef.dll to load a maliciousdll via DLL Side-Loading. In contrast, Silver Oryx Blade uses a malicious libcef.dll as a loader and a legitimate chrome_elf.dll.
- Antivirus solutions on VirusTotal detect Silver Oryx Blade and its entire infection chain, mostly as generic trojans. This contrasts with Coyote campaigns, which are specifically labeled by name by most antivirus engines.
- As mentioned in the “Threat Context” section, a VirusTotal user identified that a domain used in one of Silver Oryx Blade’s campaigns is related to Coyote’s infrastructure because it uses the same SSL certificate and registrant.
- Furthermore, it was observed that during the new trojan campaigns that have been active since at least April 2024, Coyote campaigns were also being carried out, which continue to be detected recently.
In conclusion, although both trojans present significant differences in their artifacts and TTPs, key similarities exist, such as encryption, shared libraries, and the possible coincidence of the registrant and SSL certificate in the C2 infrastructure. These similarities allow us to hypothesize that the same threat actors operate in both trojans.
A summary of the general differences between Silver Oryx Blade and Coyote can be seen in the table below.
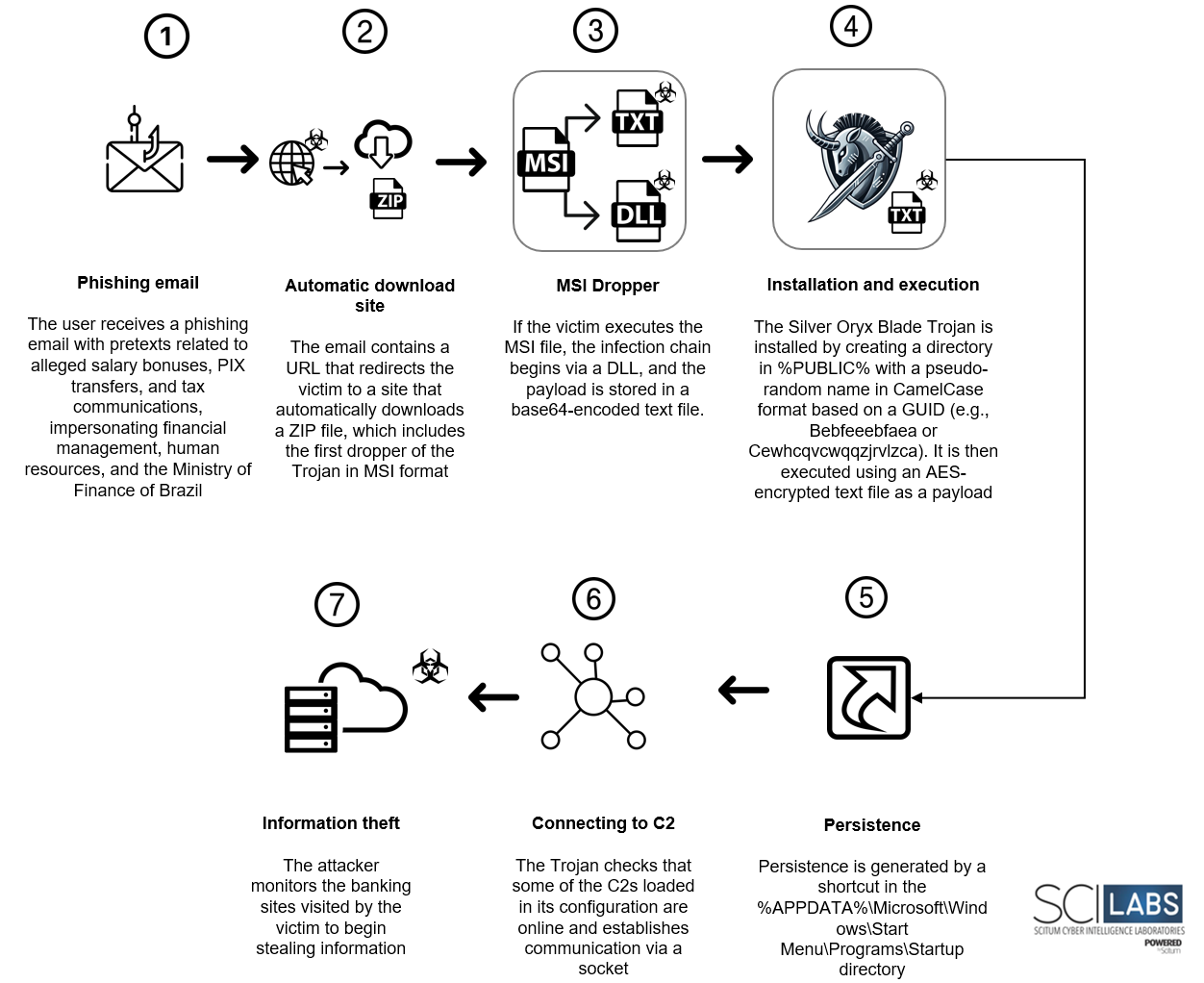
Attack Flow Summary
- The victim receives a phishing email impersonating HR finance department, and the Brazilian Ministry of Finance, using salary bonuses, PIX transfers, and fiscal notices as lures.
- The email contains a URL that redirects the victim to a site that automatically downloads a ZIP file containing the trojan’s first MSI dropper.
- When executing the MSI file, the infection chain begins.
- The MSI, which includes an embedded .NET DLL and a base64-encoded payload, extracts the necessary artifacts to install the trojan.
- The trojan creates a directory in %PUBLIC% with a pseudo-random CamelCase name based on a GUID (e.g., “Bebfeeebfaea” or “Cewhcqvcwqqzjrvlzca”). In this directory, a vulnerable executable is deployed for DLL Side-Loading, which loads the trojan into memory, along with a C++ loader, AES-encrypted payload, and legitimate Microsoft DLLs used during execution.
- To maintain persistence, the trojan creates a shortcut in %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup.
- If available, the trojan communicates with one of its configured command and control (C2) servers.
- Once the victim accesses banking sites of interest to the malware, the trojan begins stealing information, such as usernames and passwords, which are sent to the attacker’s C2 server.
Attack Flow Diagram
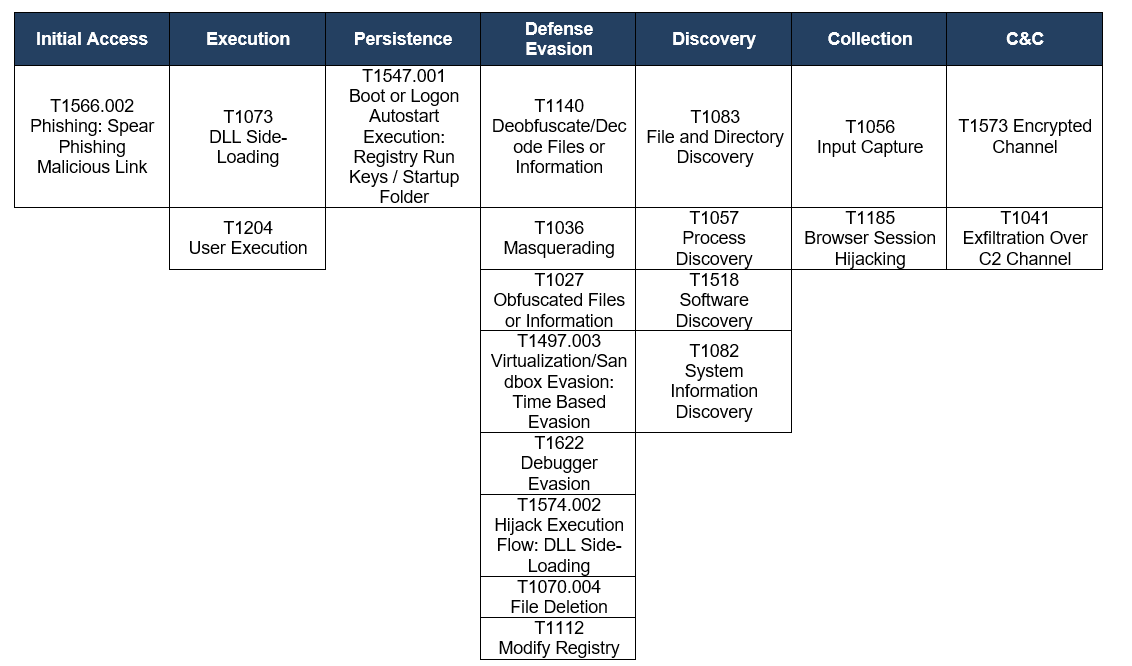
Observed TTPs aligned to the MITRE ATT&CK framework
Conclusion
SCILabs considers Silver Oryx Blade to be a significant threat in the region due to its techniques for distributing its payloads in text files, which can evade detection systems. Furthermore, it could expand its activity to other Latin American countries in the future, such as Mexico. On the other hand, other trojans like Grandoreiro, Mekotio, and Red Mongoose Daemon may adopt some of the TTPs mentioned in this report. SCILabs considers that the operators of this trojan and Coyote will continue to modify their artifacts and attack flow to ensure a higher success rate in their attacks.
Institutions and companies must remain aware of TTPs updates and indicators of compromise to minimize the risk of infection, and the impact banking information theft could have on organizations. The following specific recommendations are suggested to prevent being affected by Silver Oryx Blade:
Specific Recommendations Against Silver Oryx Blade
- Add the shared IoCs to this document for security solutions.
- Regarding emails:
- Avoid opening emails from unknown senders
- Avoid clicking on suspicious links
- Avoid opening or downloading suspicious files
- Conduct threat-hunting activities on EndPoints, looking for suspicious processes and unauthorized startup folder shortcuts.
- Check for suspicious directories in %PUBLIC% with a pseudo-random CamelCase name and perform in-depth investigations to rule out or confirm a Silver Oryx Blade.
- Check for suspicious shortcuts in %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\ and perform an in-depth investigation to confirm or rule out an infection.
- Perform threat-hunting activities on your EndPoints, looking for text files larger than 1 MB with AES or base64 encrypted strings within the paths used by Silver Oryx Blade in %PUBLIC%. Then, further investigation will be conducted to rule out or confirm a banking trojan infection.
Indicators of compromise
Below are the indicators of compromise obtained from the analysis performed by SCILabs, with a HIGH level confidence.
Hashes SHA256
FF756F33ED59E6623D6C6D6F08147F9537D57E3B9794975A462DC18A75165EB2
DBAEB3BBF3F194B4ED43BBA67177F4DFA79D5957504CCC638CCD3B9244261BF9
57178E5581D7BEB1936722E8B5642120ECC1A129B00AE123AC5B89C13A8F604B
36577DFC9D3266124993D9C4D104B533657D84D29E8FC8D7D4F9D9896747CC0E
4E9D19A0AC036B4542119A642BD18EF5D6ED6272043D598A630B8501B235B2F2
77C552981A57576C12EB0E0BF186424925C70F13AFB5D93D20D28D4DF5FE1A89
83C73A2E1D118C2B7B8C634D705E99E583F54D13F22123A03B235C4A8A9C2DD2
5CB49673F81DD79F3FC2688B2A7B5F8EDB6D02F21F1461A3ADB5CE4CE4CB08D0
A3DA2089155C3275AD02A0DFF65E4A717E8376FA1DDBFEA4537C4C0DCA7FAA15
D358B01958B4E6091A0B6D290D1724AAF5D1B19B1A98D173A2FAAFD6C707771D
DFFEE58979C13FCB39D6666854C4FDBCA3959DDD68A2560832B76E4C15DCE6D6
URLs
Full URL blocking is recommended to avoid future false positives or interruptions in the operation.
hxxps://portaldriverdownloads[.]com/alnnov2/3039a97419926c5ad50405bc16de7315
hxxps://redetop.com.br/pipermail/cn.supply_redetop.com.br/2024-May/029485.html
hxxp://bit.ly/3dU5poL
hxxps://ufile[.]io/emzdy9p5
bydeletrico[.]com
perpetualosten[.]com
belensysten[.]com
skydewiller[.]com
blendcyte[.]com
submarineclock[.]com
syetemcuevo[.]com
paginagogo[.]com
foursiason[.]com
Observables
The following indicators do not indicate malicious behavior by themselves. However, they are used during the infection chain. In case of detection, alerts, and threat-hunting processes are recommended to confirm or rule out infection by Silver Oryx Blade.
Valores Hash SHA-256
A6EB323A5E732691B2E7E6907E16E23214AC6EFDBA77BCC23037B81AB8BC3055
A030DC2DFD2ECA28A9375C92989ADF4DAF161F988DB5E16B9E10678EB0DFF4C7
E6B7D94725DC1603E121614AE88C1E3672776712A7C419A8F7F0295334266A09
F843CD00D9AFF9A902DD7C98D6137639A10BD84904D81A085C28A3B29F8223C1
E4E85EEA1106D361923995E53A0B961A28D4FB58555F40945003F35E5BF2C273
