New campaign Red Appaloosa targeting Mexico and distributing a banking trojan
Overview
The following report provides TTPs and IoCs used in a malware campaign targeting Mexico distributing a banking trojan, which SCILabs named Red Appaloosa based on its different characteristics. These new indicators were obtained from security monitoring and threat hunting in the region during the first week of January 2023.
The propagation method of this threat is mainly done through phishing emails trying to impersonate different institutions and using pretexts such as invoices, and payment receipts, among others.
In this campaign, SCILabs recovered a PDF file attempting to impersonate the Mexican electricity utilities Comision Federal de Electricidad (CFE) using a payment receipt as a pretext. The importance of this update is the fact that this malware campaign continues using the TTPs characteristic of other threats, such as URSA/Mispadu (banking trojan), Grandoreiro (banking trojan), and Banload (dropper).
The main objective of this threat is to steal banking information from multiple financial institutions of customers located in Mexico, the USA, and Portugal, including Banco Azteca, CaixaBank, Banco de Portugal, Banco Efisa, Banco Inmobiliario Mexicano, Banco Bancrea, Banco Finterra, Banco De Confianza, Banco Autofin, Banco Actinver, Scotiabank, Activobank, Orange Bank, American Express Bank, and Intercam Banco, however, based on the monitoring of the region, there is a possibility that shortly, they may attempt to steal information from financial institutions with a presence in other countries, both in LATAM and other countries in the world.
Considering that the campaign is apparently in an experimental phase and is under development, the objective of this document is to present all the information available so far to allow organizations to identify and recognize in a preventive way the behavior of this banking trojan, as well as its TTPs and IoCs, to avoid becoming a victim of this threat.
It is important to mention that SCILabs will continue to track this threat, and this report will use information already known in a general way only to provide context on the new findings.
How could it affect an organization?
The main objective of Red Appaloosa is to steal banking information from multiple financial institutions of all types of users, including employees of organizations, so if an attack is successful inside an organization, it could compromise the confidentiality, availability, and integrity of the company’s information because the extracted data can be leaked or sold on the black market or the Dark Web, which could cause economic and confidence losses for the victim companies.
Analysis
Threat context
SCILabs observed Red Appaloosa during the monitoring and threat hunting in the region during the first week of January 2023; in addition, SCILabs have monitored this threat since November 2022.
Although in this campaign, SCILabs was not able to recover the email that triggered the infection, in other campaigns it was observed that the distribution begins through phishing emails containing URLs and/or PDF or HTML files attached, with various pretexts, related to the payment of invoices, the validity of rights, digital tax receipts, and payment receipts, among others. After observing the impersonated organization (CFE), the SCILabs team was able to determine with a high level of confidence that this campaign is targeting Mexico.
The objective of the PDF recovered by SCILabs is to redirect the victim to a website to download a compressed file in ZIP format containing a greater than 300MB EXE. Upon execution, a CAPTCHA validation is displayed on the screen, and once resolved, the following stages of the malware, described later in this report, begin.
Finally, it tries to communicate with the C2 server and waits for the user to log in to certain bank’s portal to steal their banking information.
Technical Summary
The PDF file recovered by SCILabs with the name “CFE_PENDIENTES_Factura1593365.pdf” pretends to impersonate the CFE by duplicating one of its receipts in a blurred form and with the caption “Ver Factura Completa“. The image has a hyperlink inside, which, unlike the one reported by SCILabs in December, does not use URL shorteners or QR generators. Clicking on any part of the alleged receipt initiates downloading a compressed file in ZIP format.

Figure 1 – PDF file with an alleged CFE receipt
The compressed file contains an executable file, and a second compressed file contains a Firefox installer, in which no malicious behavior has been observed, and its functionality in the infection chain has not been determined.
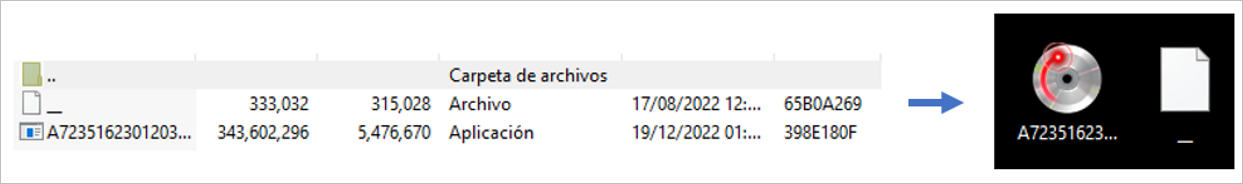
Figure 2 – Compressed file content
When executing the file named “A72351623012034.exe” a CAPTCHA validator is displayed, which seeks to evade sandbox security solutions by forcing human interaction to continue with the malware execution. It is important to note that this window cannot be closed if the CAPTCHA is not resolved or is resolved incorrectly.
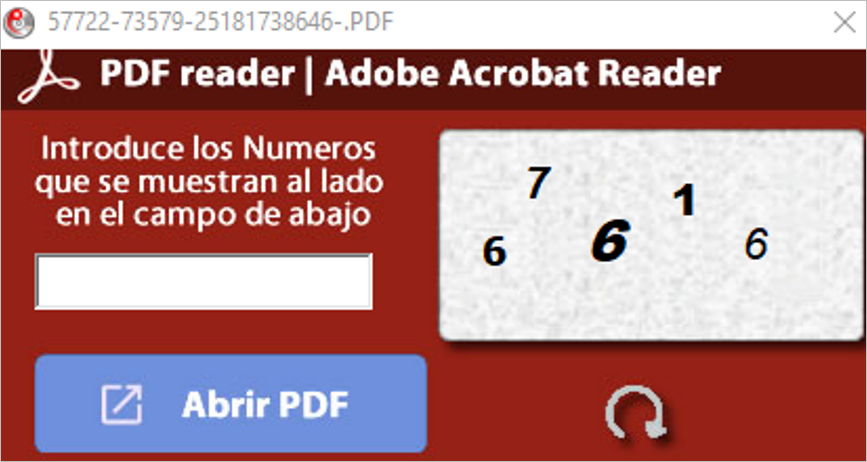
Figure 3 – CAPTCHA validator used by the malware
After the validation of the CAPTCHA, it starts downloading a MPEG format file named jama22bg; although it looks like a video, this artifact is a compressed file, which contains two directories, an installer and three DLLs (one of them malicious and over 500MB).
To decode this supposed video, the malware uses the VideoLan software. The final archive is password protected, and SCILabs has not yet been able to determine the password.
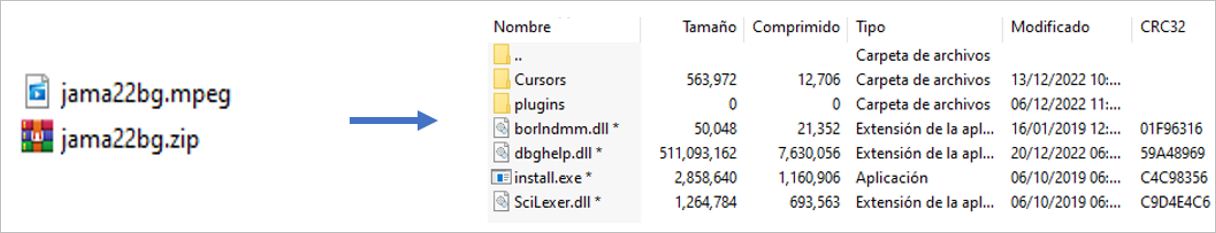
Figure 4 – Content of the supposed video
The malware automatically unzips this artifact and moves the contents to the C:\Users\<user>\<random characters> directory, then runs the “install.exe” file and attempts to impersonate the NotePad++ text editor.
The following files are located inside the final directory:
- Cursors: A directory that contains six files with CUR extension, which have not yet been observed being used by the malware so that they could be distractions for the security researchers.
- Plugins: Empty directory that is only used if NotePad++ is not installed on the victim’s machine. Otherwise, it remains empty during the infection chain.
- Borlndmmdll: Legitimate DLL that has not been observed to have any malicious behavior.
- BraveCrashHandler gduuplZ33.exe: Malicious executable, which tries to impersonate NotePad++, since it is digitally signed by NotePad++, making it difficult to categorize it as malicious.
- Dbghelp.dll: Malicious DLL that is over 400MB in size which allows it to evade certain security solutions that only allow the analysis of artifacts smaller than 100MB.
- SciLexer.dll: Legitimate DLL that has not been observed to have any malicious behavior.
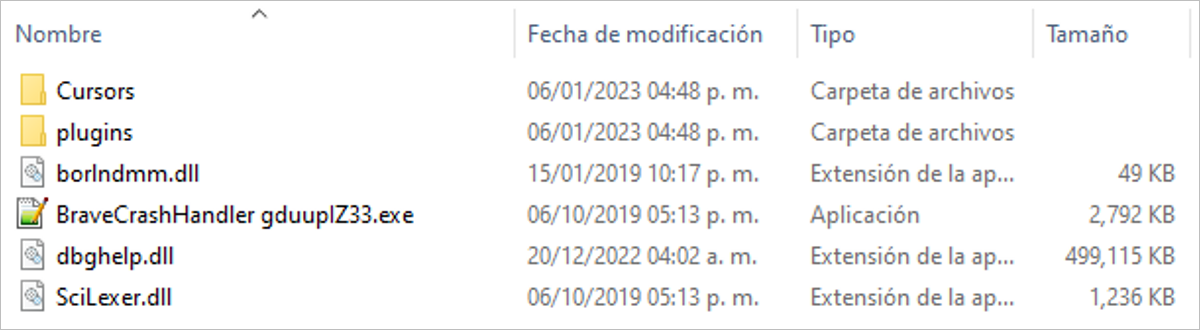
Figure 5 – Contents of the directory where the malware is installed
An important point to highlight, which could be used as an indicator of attack, is that if NotePad++ is previously installed on the victim’s machine, it becomes unusable after the execution of the malware; however, if NotePad++ is not installed, the malware executes without modifying any previously installed component on the victim’s machine. The attacker is probably using NotePad++ to implement DLL hijacking techniques; this technique allows to achieve persistence and execution of arbitrary code. The malicious code is executed every time the user tries to open the compromised software.
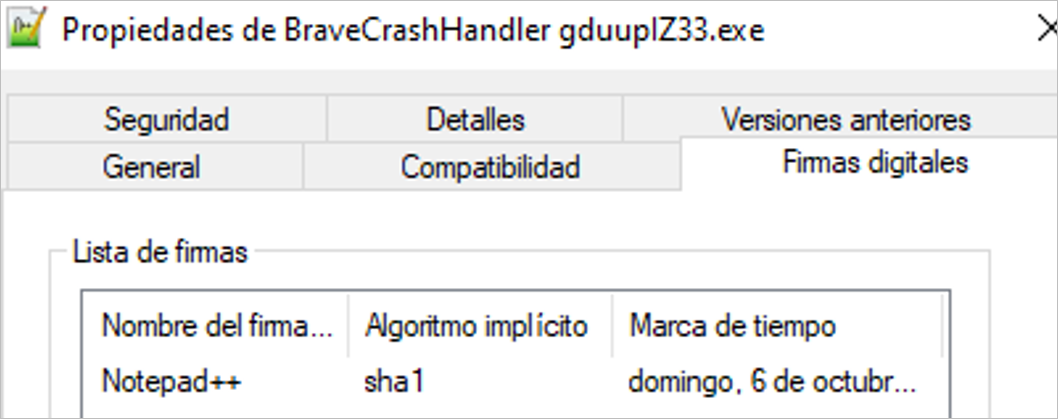
Figure 6 – Digital signature of the malicious artifact
This threat creates persistence by creating an execution key in the Windows registry Software\Microsoft\Windows\CurrentVersion\Run.
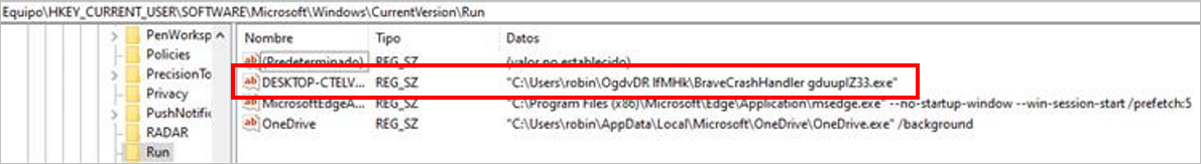
Figure 7 – Persistence generated
Finally, it attempts to communicate with the C2 server and begins to wait for the user to log in to their bank’s portal to steal banking information from one of the following listed banks:
- Banco Azteca
- CaixaBank
- Banco de Portugal
- Banco Efisa
- Banco Inmobiliario Mexicano
- Banco Bancrea
- Banco Finterra
- Banco De Confianza
- Banco Autofin
- Banco Actinver
- Scotiabank
- Activobank
- Orange Bank
- American Express Bank
- Intercam Banco
The process listens for strings that have the following format https://www.google.com/search, and that include any of the banks listed.
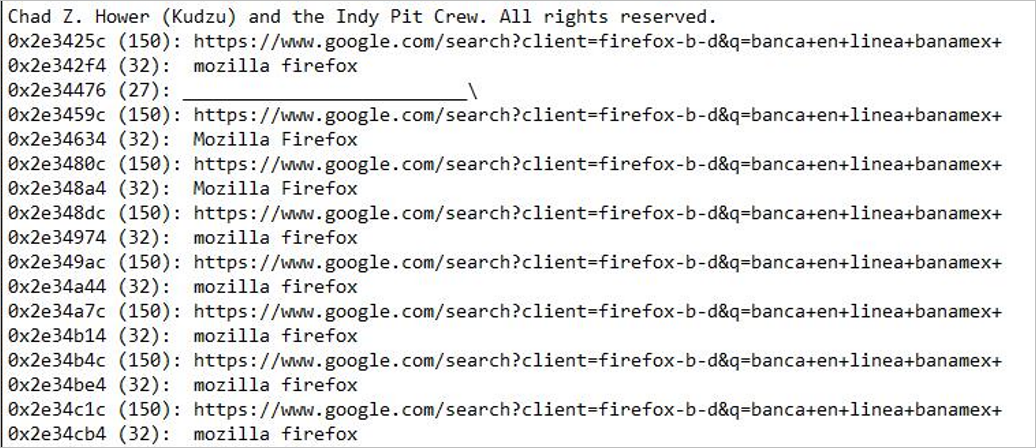
Figure 8 – Records of the process waiting for one of the listed banks
Attack Flow
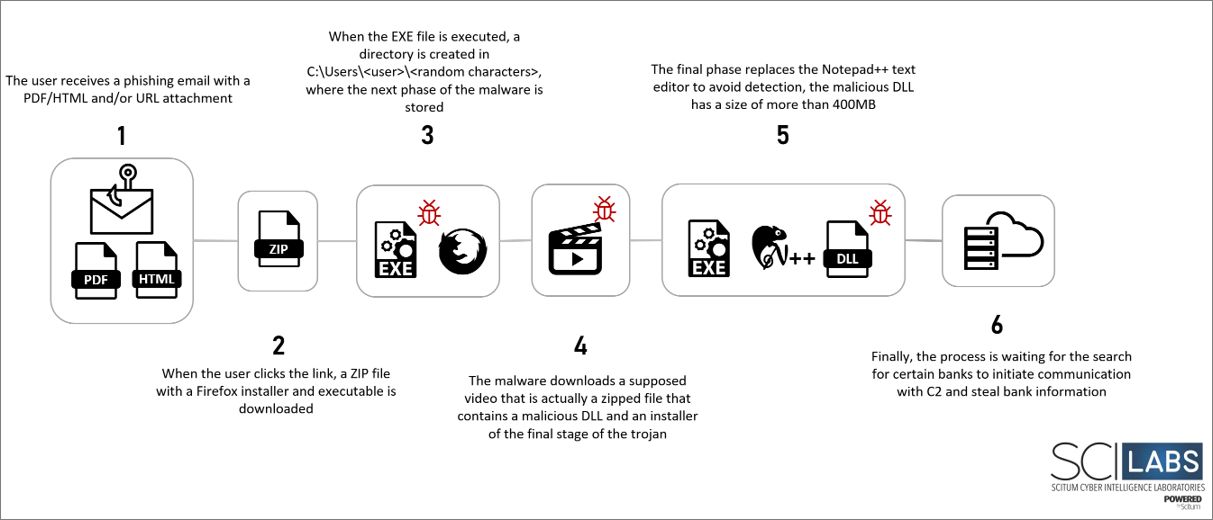
Figure 9 – Attack flow
TTPs observed aligned to MITRE’s ATT&CK framework
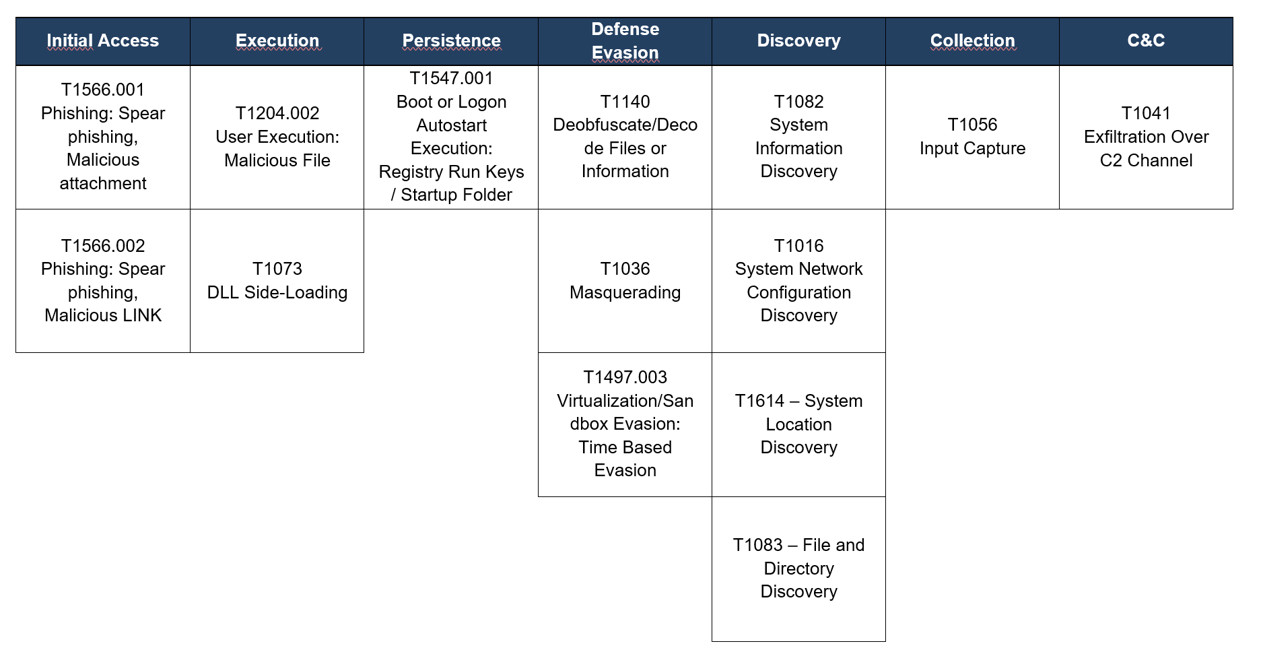
Table 1 – TTPs observed aligned to MITRE’s ATT&CK framework
Assessment
The danger of this threat is that this banking trojan is taking the “best and most effective” TTPs from other threats affecting LATAM and using them in its infection chain to have a higher success rate in its attacks because the campaign is designed to delay researchers’ analysis, evade security solutions (which can only analyze artifacts smaller than 100MB), evade security solutions that automatically run samples to determine whether or not they are malicious, and evade security solutions that only track the creation of malicious processes but do not track legitimate processes that could load a malicious DLL into memory.
SCILabs has observed a rapid evolution in its TTPs, changing its infrastructure quickly and adding steps to its infection chain, and we observed that the group behind this threat has been using fewer files in the final stage of the malware.
By analyzing the origin of the banks obtained during the different campaigns found, SCILabs has the hypothesis that this threat will continue to be present during 2023, and it could spread to other countries in Latin America and the world.
Finally, SCILabs will continue to track this threat to keep organizations and users updated on changes in their TTPs, new IoCs, or relevant information that could be vital to avoid becoming a victim of this campaign.
SCILabs recommends that organizations conduct constant awareness campaigns about the social engineering techniques used by cybercriminals to distribute this type of banking trojans, as well as the entry vectors identified by SCILabs through continuous monitoring of the region. The following suggestions are recommended:
- Avoid opening emails from unknown senders, avoid or restrict the downloading of files and/or programs from unknown or non-legitimate links.
- Avoid and/or restrict the download and installation of non-legitimate software or software from unofficial sites.
- Block the indicators of compromise present in this document.
- Perform threat hunting looking for directories named with random letters or characters in C:\Users\.
- Scan for suspicious registry keys created in Software\Microsoft\Windows\CurrentVersion\Run.
- Constantly monitor the systems and perform threat hunting activities to identify large executable files or DLLs (greater than 100 MB) in directories with names similar to C:\USERS\[USER]\[RANDOM CHARACTERS], C:\ProgramData, C:\Users\Public or %APPDATA% to detect possible infections of this banking Trojan.
- Monitor if the Notepad++.exe process is running in the background without the end user using the application.
- It is advisable to offer security awareness training to your employees.
IOC
Obtained during analysis
Hash SHA-256
29347E1F1D7ABEB6BB4E3D23851020B410E4614BD27A3D074AF64E47F5651188
BA3EAB3C379D4F04B00F3D0C2D5CE281A9F5C2FF4CA5FF1C323D5552B001D373
C335ADB8E995FE7FF19B80B9E5FF30C07B0C8605C3839D7E90F259626FA77941
Domains
MERCADAODORJ[.]COM
MEX[.]FACTURAPAGO[.]SHOP
URLs
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS.PHP
HXXPS[:]//APPLICATIONFILESTORAGEMX[.]BLOB[.]CORE[.]WINDOWS[.]NET/APPSTORAGEMX/PAGO_REF_C432844614[.]ZIP
HXXPS[:]//A[.]NEL[.]CLOUDFLARE[.]COM/REPORT/V3?S=NDV6TYGEEKBXA7N44WMYKYY85%2BQLLXHBVE15AFXSXUDBTWTYXVCUGMVGQ3WAO5USYHKXOUC7XB7AAPVB6PAKEJO4RGL8D9BFB42WTYDNRTRSYINWWWFQTNHA5U0PTCA957N8
HXXPS[:]//A[.]NEL[.]CLOUDFLARE[.]COM/REPORT/V3?S=YQNRMOPJZVSLQFYB%2BY8UENO6LTRHSDDFEKNDIIO%2FMEWSZTLIAPQTYREBG0%2F6UZO2LX4AZ%2B1NTJCVQMULUALUWOTS4CSPSABT7NMSSLIU8MELYRCMH7KTDO6TEZQHLONPNYOS
HXXP://MEX[.]FACTURAPAGO[.]SHOP/JAMA22BG[.]MPEG
HXXP[:]//MERCADAODORJ[.]COM[:]80
Subdomains
APPLICATIONFILESTORAGEMX[.]BLOB[.]CORE[.]WINDOWS[.]NET
Obtained during analysis
Hash SHA-256
29347E1F1D7ABEB6BB4E3D23851020B410E4614BD27A3D074AF64E47F5651188
BA3EAB3C379D4F04B00F3D0C2D5CE281A9F5C2FF4CA5FF1C323D5552B001D373
C335ADB8E995FE7FF19B80B9E5FF30C07B0C8605C3839D7E90F259626FA77941
Domains
MERCADAODORJ[.]COM
MEX[.]FACTURAPAGO[.]SHOP
URLs
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS.PHP
HXXPS[:]//APPLICATIONFILESTORAGEMX[.]BLOB[.]CORE[.]WINDOWS[.]NET/APPSTORAGEMX/PAGO_REF_C432844614[.]ZIP
HXXPS[:]//A[.]NEL[.]CLOUDFLARE[.]COM/REPORT/V3?S=NDV6TYGEEKBXA7N44WMYKYY85%2BQLLXHBVE15AFXSXUDBTWTYXVCUGMVGQ3WAO5USYHKXOUC7XB7AAPVB6PAKEJO4RGL8D9BFB42WTYDNRTRSYINWWWFQTNHA5U0PTCA957N8
HXXPS[:]//A[.]NEL[.]CLOUDFLARE[.]COM/REPORT/V3?S=YQNRMOPJZVSLQFYB%2BY8UENO6LTRHSDDFEKNDIIO%2FMEWSZTLIAPQTYREBG0%2F6UZO2LX4AZ%2B1NTJCVQMULUALUWOTS4CSPSABT7NMSSLIU8MELYRCMH7KTDO6TEZQHLONPNYOS
HXXP://MEX[.]FACTURAPAGO[.]SHOP/JAMA22BG[.]MPEG
HXXP[:]//MERCADAODORJ[.]COM[:]80
Subdomains
APPLICATIONFILESTORAGEMX[.]BLOB[.]CORE[.]WINDOWS[.]NET
Obtained from retrohunt processes
Hash SHA-256
A159306C35D36BE5838164AB994E8539BD16105FCE9971469E9422BB95D8BA4B
257509134B49AD4ED4F18B93E97F8A5CF8E27E1FF3E32595B4CBBFA7DABD23EA
9D814CF55B7C317A918E208722EC7A7AA64F10092518D9FF9A6B8F2EC882F369
CD1797A3299C3433C1FB67EE7288C2D9B07CD6F7E3EA8A1217121479588B269D
EC818EA64BC515664AAA73B639277EA4BBF66417E4935C06AC23BDB02E640119
29347E1F1D7ABEB6BB4E3D23851020B410E4614BD27A3D074AF64E47F5651188
9E738F90C14BE77587D1A4035BD6F0B213726A138944EB67C86CF71B9149AF7A
E8E5D10D6FF77CAFE37ABC806C2F53BD1895B6DBFDD517CD0E00BC0FD2940924
89C9F07AAAD1773F2E2432634C04F118CD1E57A1639A2234B9A03B53FC813D81
43315AB9B55A08A7787FE03FA0B129D9BBDF2E5BC4CC0661861BAC03F1310C5F
9D1F91DB7C27EBE637093788438A33714A4594E6789A312C9FFE269122218E79
2C2697F11FA554742B62EE9FE3C8AAB3C9AC31823161BD4BCC8A410161D6B734
79F5849A1C7B1A6118FB1ACA86A6446853159081DB03C88E0F117D5B463BB01D
7DDE1E742B1D1A9A9884FAB019B0C6D5A8AAD597FB914E7103BDDA227639B20A
80C5FFDC066C55DA1F29B5FF7A5555C358C4AACAF5BF13CC8AAF37B49A0AC307
9FDC2A8611A8FC66D6F1D96EEEA2D6E84859C7CD9C4C58F4A3FC03F7466A41FA
E530766D1C59FAF5BB3EC0BCC755AE97B4E9D4972C850D0CF93490372C58A38B
A3F76DC191B9FA368B20F83A46A1C5C8BCE6227C2B0DEC929F69EB0D0BEB24D6
0549C1FF0EB7B7F66128EA02FB7F7ECA82D74EA77F08A93932CAF4AB66426019
09A63F3066A8FCA724939B186C48246A473027E8846A3184203C4AC521D9BF56
0A8819C35AA185E2695AEDF01FC7C8B1A997FB6ED556D481D5F4988D781FA2B1
118E4FC96581312F627539E90CB4FBBCAC40AB36EBC6BDFDE883B685FBF74039
1326882E04B4059CF316313CFE76667631973BFE1A5A74A22C0D0285EAE78420
150D21475EB176E938DC4B33E3196514D76E4C5A2E34625B2D38E8984DD3F533
1BC0B1A3E8C1547969E1CF59D20C9CEE8AECE9DFE1B19247E513FA4B889A08E1
21E3B21C5A63D906C22CE233B52F2CE61259C7258065CA662B709C614580A8ED
2308008290B2E5A59734E4C41649F624E73097556E2BC64181B85BBD7DC74978
25C6A148B54DF7E072AA45C282025C9F7DC024097D5A864CEB260D73BBCCF041
2742927E776412D2A002D8392237D8E09584F728CEE32F32872A9B375C4D1633
32661DD7F837B7381C64DEC348212293B49571CC6B243E77FFFDFE43C4A72969
3CF372C2248BB025E108022DAAD59A3055BB4D2AB645BB0CECB03334F46BB097
4E3A1A71BC4FEDD85EDE0CA9AD87B6B36E9E3EB373CA4436DB395CA7C8399BB1
4E6893FBE18D5BCAA0DAD2F76F4F05BD2A2AFFE3CAB08794A36FF898BCB6424D
55364BCD6999E99AD45D41A0988E1354E60ADD4CC0CDB4ADC83D236C6A9C7348
56A97F834B4A74E1876696D06B0520DC1F35AA43BB8A8930967BDBA9DFE7F96E
627E9959C29E98B9AF31434981A6E98CEC24733953B4839ED76B0181A652294B
6E8A407A07348EC0CA7855D2AEEA017647A11E88202995767BFF34448297ED74
70BB9B5DB04307C00132943AE425C99E32618E72EAC4CB85D7C716C61612AD41
715A5092C5D8607E898F5B1DA79DB1706DEB20A27E61F0D4EF2BE77134DA5B8E
7651CCD7190113EBD2D236AC8B41C372AE09CB803617D174A4733D1D085D1610
76B8469DB9B2F958954FCD2863EF1E8633F50BCBC0B0C00165282AD4F8AE826F
7843658143C80D4148B09F9C71EA8001277E11EC78866FEB298E0D2D1E42B92A
8923498A7AE41471F2EC87293E5474D474DE0225E629A1407176716786A74B40
990A3BFC25F935CA485BD442BFC27EA06174B409E75729903F4E9CA3B320728B
9A3A9B0D93A50C0F1E7589CA82FD8BED40356AEE95266B74A72D74ECB801CF66
9BF948EE126D5D68DF3FBF82C416F58C07C5F0296C800CF902EEC53F650FB0FE
9EFC7FD313E2F4D189C266E3D375B4C5C8150290EC2D531E1F7E3BD1E876D045
A9C314FBE09F14D4C00A98A422D92E35B4346F30FCD8AE7AB4A1B0AFE66E9E96
B5ECC47A73B4F751EDF0738C33CCEC20AC91BFC63C099A949EABE002A34EAD93
B9F29D95AFC647E992AF74D807820D88AD525D14E8AE741F1121BB808F0E624A
C92BCE899EF68EE4162456C87959CDAA2FD07F28AB3D37BD6D4F5755A8872229
D3DE331A99CADA7AD030ACDEB321D96600CCF36913A99BE45184D102B9DF2902
D49F18291611DD7B304F3F1AB19634BED3110EE61905B80F20969BABE77398F8
D4A8B93B16F94EF346AFCB3CB3CF14BF53B20D6CD6F94047CF45E877684A4ABD
D7642B55C29D2C019C70B2B7C0DD4D30BD3E50D1673B3DDA3D3B8241E2560347
D79C72E1599B4D3838D3D1D2C862B2071024787B3BCA43B94C4BD22AF059C499
D7CA7FA79D98DD37054E576ACFB170CE6EE6A211D53BAB5E8B51D70CD506C073
DAD8DD850C88725A3BD5B9E14E1416E641D23799F1A9679806F24230C52E2F45
DC43288AFA0C32D7E8A023EAEDDBA67F952735054E181F5311092FB903501186
E4FA8D9ADCA0BB32E128127EFB30F2575B4E30C065493812FE174E43A50B1BDD
ED7EF14058D99E738CC078F44DD0C9A545C3FFEF9E4C1B496F60169FCA57DCF0
EFC14055117633A34851CC7C891515D4F5970E72A01D9DE750D6034CBD6D2A7B
F20D9D16FFDEEEFD5BBC546CDB1976C83159E117A89CD9BCC413BE58E0024215
FDEDC55731F936A808EBE1D81A42C732681E47C8C34EB6B97E6849E27814D6E6
FEDE719B831EB7160431F255E759EA1DFD6259D7E993735B97506A87D07728B0
06BBF545F815C8B0330075DF90B55266E133559E1DAEC60E7B63443D98957F5B
100B321C3EB6B895E69F23471D51BEC4F99F18C0F61ABB29DDCED7A866C09726
15BE38594321321ED8A97E193733E9C1C217CD48E637B430BDB5CC4CEFFCB9CA
3CAC6E74DBD797F25585D206D93551467CAD2934AF18C345764316D78D2EE537
7BE825573DD86B4E93D0954B33B5D89BD23B521D7E41A1426685CA4A983AA504
9DDF84BA82CD4C62F0AB8D9F44E80F8F7484E94BE065B684D0BEEE236ADB4A6B
B13326C87C6ADB0B1D1CC43D592637963C07A1DF01F91B1908E8C612CE7F6984
CE2ACB7829AA15F325A0293C580846AF0BE8A68D5522A12B5ED92437007D53EE
DF36F4718861FBDF8A5860CD2C121CCC04AFE9D8937611A9432C1A86795C483F
E4B206C38909250FAED4A09C6EFEC81553F232519AE2A2F2D2AA16920D3900B1
E69D91A78C2E334F0972DC515FBB90E3F44CD5B06FFC9A87CEDB443C157E2FB4
F26D161443C991D8F77835B8DD1E9C3C3750E39FCCCDB19BCFFF32FF432D5833
F402C14EE49A08BE08F5826BB5BC43D4D20C78C30F6720CFA52C029152E3601C
FACB3B3FDFC6CC411C410A7A78D9318D264A25FA62733BC2DC35DF899303B905
FD81964795C8DCCD02DE0A5FBB07FEED54214E04B1E6EDDB1ACBC8330A9FA042
1683A0019D1C49BC1A60049B8BD6A4DB6C108745639AB8033300AD796DA8C2CC
E2301C42C6D054A86CB247765124AEB443DDA738A893C56A2CAD461A63EC3A30
3F225E7AAABB1EB8AF1AC41489BFDC0F637AB75CFCB0F285C6D7783B235E6BEE
44471D9D0A04EA71D1002AE5659010BCB79679BEDA423D24EE185D14BCBC70CF
AB8DB2CD01A7EFBF28EE07B0F98259E2DE3637A3364727F8466B4A91BF7C2C30
328BDC9EDDE08130CBBD04200A3C4E581AD400D68728BD8698CFC7868865C074
87254DDF2FAA8ABECEE4C4B8985771A6A858632532868AC5032C0E8FFFDEA51A
2C971916D134DE95D6614DAD17F3A1F81FEAF8311011D213732EE5992854950F
622EE447BF1F5C6087EFE261D17B8378BDE8967BF0E677CA1164602C67396B3B
Subdomains
CERTIFICATED[.]EMPRESASCFDI-PERSONAS[.]SHOP
CFDI[.]SMART2NOPAGOS[.]SHOP
EMPRESARIALMX[.]SHOP
EXECULTIVO[.]MONEYGOLDX[.]SHOP
FACTGEFORCEX[.]SHOP
FACTURACION[.]SGSCOMMANAGER[.]SHOP
FACTURAS[.]MARKETING4GRP[.]SHOP
GERENCIA[.]MULTISISTEMPAGOSMX[.]SHOP
L[.]EAD[.]ME
MANAGER[.]INVESTHARBOURSESSION[.]SHOP
MEX[.]FACTURACOMPROBANTE[.]SHOP
MEX[.]FACTURACOMPR[.]SHOP
MEX[.]MASSATEST[.]SHOP
MEX[.]TENESNET[.]SHOP
MULTI[.]MULTISESSIONLTDA[.]SHOP
MX-CORREEOSUPORT[.]SHOP
MX[.]EMPRESA020[.]SHOP
MX[.]EMPRESARIAL1MX[.]SHOP
MX[.]EMPRESARIALLLMX[.]SHOP
MX[.]EMPRESARIALLMXX[.]SHOP
MX[.]EMPRESARIALL[.]SHOP
MX[.]EMPRESARIALMX03[.]SHOP
MX[.]EMPRESARIALMX04[.]SHOP
MX[.]EMPRESARIARMX030[.]SHOP
MX[.]EMPRESARIIALMX[.]SHOP
MX-ITUNES[.]SHOP
MX[.]MEXEMPRESSARIAL[.]SHOP
MX[.]MXEMPRESAA[.]SHOP
MX[.]NEGOCIOAPPS[.]SHOP
MX[.]NEGOCIOMX2[.]SHOP
MX[.]NEGOCIOMX3[.]SHOP
MX[.]NEGOCIOMX4[.]SHOP
MX[.]NEGOCIOMX[.]SHOP
MXX[.]DIRETORGERALXX[.]SHOP
NEGOCIOMX3[.]SHOP
PAGO[.]SGSCOMMANAGER[.]SHOP
PAGOS[.]MULTISESSIONLTDA[.]SHOP
PORTAL[.]ADIMCOPAGOS[.]SHOP
PORTAL[.]ROSENPARKPRIVATEPAGOS[.]SHOP
PROMOCIONES[.]ROSENPARKPRIVATEPAGOS[.]SHOP
Q-R[.]TO
RECIBO[.]MBUSSINESSCFDI[.]SHOP
RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET
SAC1[.]FAFORCE[.]SHOP
SAC2[.]FACTGERFORCE[.]SHOP
SAC3[.]FACTGIFORCE[.]SHOP
SAC4[.]FACTGEFORCEX[.]SHOP
SSL[.]ADIMCOPAGOS[.]SHOP
SSL[.]MARKETING4GRP[.]SHOP
SSL[.]MULTISESSIONLTDA[.]SHOP
SSL[.]WESTNEX[.]SHOP
STORAGERECIBOSPAGOS0712[.]BLOB[.]CORE[.]WINDOWS[.]NET
WWW1[.]COMPROBANTEMX[.]SHOP
WWW1[.]EMPRESA020[.]SHOP
WWW1[.]EMPRESARIALLMXX[.]SHOP
WWW1[.]EMPRESARIALL[.]SHOP
WWW1[.]EMPRESARIALMXX[.]SHOP
WWW1[.]FACTURAMX[.]SHOP
WWW1[.]MEXEMPRESARIIAL[.]SHOP
WWW1[.]MEXFACTURA[.]SHOP
WWW1[.]MXEMPREESA[.]SHOP
WWW1[.]MXEMPRESAR[.]SHOP
WWW1[.]MXEMPRESSARIIAL[.]SHOP
WWW1[.]MXFACTURA[.]SHOP
WWW1[.]NEGOCIOMX2[.]SHOP
WWW1[.]NEGOCIOMX3[.]SHOP
WWW2[.]BOGFAC[.]SHOP
WWW2[.]BOGJAM[.]SHOP
WWW2[.]EMPRESARIALMX15[.]SHOP
WWW2[.]JAMNET[.]SHOP
WWWS1[.]MBUSSINESSCFDI[.]SHOP
WWWS[.]EYEWATCHDESIGN[.]SHOP
WWWS[.]SMART2NOPAGOS[.]SHOP
URLs
HXXP[:]//24[.]152[.]38[.]151/COMPROBANTE_PAGO/
HXXP[:]//24[.]152[.]38[.]151/COMPROBANTE_SPEI/
HXXP[:]//24[.]152[.]38[.]151/FACTURA/
HXXP[:]//24[.]152[.]38[.]151/FACTURA_COMPROBANTE/
HXXP[:]//24[.]152[.]38[.]151/FACTURA_PAGO/
HXXP[:]//24[.]152[.]38[.]151/PAGO_COMPROBANTE/
HXXP[:]//24[.]152[.]38[.]151/PAGO_RECIBO/
HXXP[:]//24[.]152[.]38[.]151/RECIBO_PAGO/
HXXP[:]//CERTIFICATED[.]EMPRESASCFDI-PERSONAS[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP?APPLICATIONS
HXXP[:]//CFDI[.]SMART2NOPAGOS[.]SHOP/DOCS_RECIBOS/CFDIPAGOS[.]PHP
HXXP[:]//EMPRESARIALMX[.]SHOP/COMPROBANTE_SPEI/
HXXP[:]//EXECULTIVO[.]MONEYGOLDX[.]SHOP/FACTURA/DASSSASHYTSRFWEWDW4DVSSF351W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//FACTGEFORCEX[.]SHOP/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//FACTURACION[.]SGSCOMMANAGER[.]SHOP/APP_DOCS_CD20185205/DOCS_FICHERO05502022[.]PHP
HXXP[:]//FACTURAS[.]MARKETING4GRP[.]SHOP/DOCS_RECIBOS/CFDIPAGOS[.]PHP?PORTALCFDI15201477
HXXP[:]//FACTURAS[.]MARKETING4GRP[.]SHOP/DOCS_RECIBOS/CFDIPAGOS[.]PHP?PORTALFACTURA1588933
HXXP[:]//GERENCIA[.]MULTISISTEMPAGOSMX[.]SHOP/GERENCIABR02/YBNZKVJ[.]PHP
HXXP[:]//L[.]EAD[.]ME/BANAMEXAPPS15278
HXXP[:]//L[.]EAD[.]ME/BDCRRR
HXXP[:]//L[.]EAD[.]ME/BDOAFK
HXXP[:]//L[.]EAD[.]ME/BDPAOF
HXXP[:]//L[.]EAD[.]ME/BDQ5P9
HXXP[:]//L[.]EAD[.]ME/BDQ6IF
HXXP[:]//L[.]EAD[.]ME/BDQ6MM
HXXP[:]//L[.]EAD[.]ME/BDQ7YY
HXXP[:]//L[.]EAD[.]ME/BDQ7Z0
HXXP[:]//L[.]EAD[.]ME/BDQOB8
HXXP[:]//L[.]EAD[.]ME/BDQOC1
HXXP[:]//L[.]EAD[.]ME/BDQXFG
HXXP[:]//L[.]EAD[.]ME/BDROOO
HXXP[:]//L[.]EAD[.]ME/BDRYNG
HXXP[:]//L[.]EAD[.]ME/BDRYNN
HXXP[:]//L[.]EAD[.]ME/BDRZOR
HXXP[:]//L[.]EAD[.]ME/BDWZ6B
HXXP[:]//L[.]EAD[.]ME/BDZHVF
HXXP[:]//L[.]EAD[.]ME/CFDIFACTURAAPPS
HXXP[:]//L[.]EAD[.]ME/MXSATGOX158233
HXXP[:]//MANAGER[.]INVESTHARBOURSESSION[.]SHOP/DOCS_RECIBOS_EMISSION/APPSMANAGER[.]PHP?APPSCFDIPAGOSMX-2022-001
HXXP[:]//MANAGER[.]INVESTHARBOURSESSION[.]SHOP/DOCS_RECIBOS_EMISSION/APPSMANAGER[.]PHP?APPSDOCSMX
HXXP[:]//MEX[.]FACTURACOMPROBANTE[.]SHOP/JMBACK[.]BMP
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/7777777777/
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/COMPROBANTE_FACTURA/
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/FACTURA/
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/FACTURA_COMPROBANTE/
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/PAGO_FACTURA/
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/GCDUKKLCIKNRSBJWONSTQPNDFERVKYFSMBNFYFQWFYBFKHTYJBDTRFW[.]PHP
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/GCDUKKLCIKNRSBJWONSTQPNDFERVKYFSMBNFYFQWFYBFKHTYJBDTRFW[.]PHP
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/GCDUKKLCIKNRSBJWONSTQPNDFERWKYFSMBNFYFQWFYBFFKHTYJBDTRFW[.]PHP
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/IMAGEM/BANAMEXSEGURO[.]JPG
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/IMAGEM/CITIBANAMEX[.]JPG
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/IMAGEM/COMPUTADOR[.]JPG
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/IMAGEM/CONTATO[.]JPG
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/IMAGEM/ENDERE
HXXP[:]//MEX[.]FACTURACOMPR[.]SHOP/RECIBO_FACTURA/IMAGEM/ENDERE%C3%A7O[.]JPG
HXXP[:]//MEX[.]MASSATEST[.]SHOP/JM3VIEW[.]AVI
HXXP[:]//MEX[.]TENESNET[.]SHOP/JAMANEW2[.]PNG
HXXP[:]//MULTI[.]MULTISESSIONLTDA[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP?PAGOS-DOCUMENT
HXXP[:]//MX-CORREEOSUPORT[.]SHOP/
HXXP[:]//MX[.]EMPRESA020[.]SHOP/
HXXP[:]//MX[.]EMPRESA020[.]SHOP/GJNEW[.]DRIV
HXXP[:]//MX[.]EMPRESA020[.]SHOP/KGRIN2023[.]CERT
HXXP[:]//MX[.]EMPRESA020[.]SHOP/KGRIN23JM[.]CERT
HXXP[:]//MX[.]EMPRESARIAL1MX[.]SHOP/
HXXP[:]//MX[.]EMPRESARIALLLMX[.]SHOP/
HXXP[:]//MX[.]EMPRESARIALLLMX[.]SHOP/JM2VER[.]DVR
HXXP[:]//MX[.]EMPRESARIALLLMX[.]SHOP/JM2WIN[.]DRV
HXXP[:]//MX[.]EMPRESARIALLLMX[.]SHOP/JMAA2V[.]CORE
HXXP[:]//MX[.]EMPRESARIALLMXX[.]SHOP/GJNEW[.]DRIV
HXXP[:]//MX[.]EMPRESARIALLMXX[.]SHOP/GJNEW[.]DRIV
HXXP[:]//MX[.]EMPRESARIALLMXX[.]SHOP/KGRIN2023[.]CERT
HXXP[:]//MX[.]EMPRESARIALLMXX[.]SHOP/KGRIN23JM[.]CERT
HXXP[:]//MX[.]EMPRESARIALL[.]SHOP/
HXXP[:]//MX[.]EMPRESARIALL[.]SHOP/JAMA3V[.]CORE
HXXP[:]//MX[.]EMPRESARIALL[.]SHOP/JM3WWV[.]CORE
HXXP[:]//MX[.]EMPRESARIALL[.]SHOP/JM3WWVW[.]CORE
HXXP[:]//MX[.]EMPRESARIALMX03[.]SHOP/JM2VER[.]DVR
HXXP[:]//MX[.]EMPRESARIALMX03[.]SHOP/JM2WIN[.]DRV
HXXP[:]//MX[.]EMPRESARIALMX03[.]SHOP/JMAA2V[.]CORE
HXXP[:]//MX[.]EMPRESARIALMX04[.]SHOP/CURURU[.]PUTA
HXXP[:]//MX[.]EMPRESARIARMX030[.]SHOP/
HXXP[:]//MX[.]EMPRESARIARMX030[.]SHOP/JM2VER[.]DVR
HXXP[:]//MX[.]EMPRESARIARMX030[.]SHOP/JM2WIN[.]DRV
HXXP[:]//MX[.]EMPRESARIARMX030[.]SHOP/JMAA2V[.]CORE
HXXP[:]//MX[.]EMPRESARIARMX030[.]SHOP/JMAA2V[.]CORE
HXXP[:]//MX[.]EMPRESARIIALMX[.]SHOP/
HXXP[:]//MX-ITUNES[.]SHOP/EXPIRE/INDEX2[.]HTML
HXXP[:]//MX[.]MEXEMPRESSARIAL[.]SHOP/MJ3PHP[.]MQL
HXXP[:]//MX[.]MEXEMPRESSARIAL[.]SHOP/MJ3PHP[.]MQL
HXXP[:]//MX[.]MXEMPRESAA[.]SHOP/
HXXP[:]//MX[.]MXEMPRESAA[.]SHOP/MJ2CORE[.]WIN
HXXP[:]//MX[.]MXEMPRESAA[.]SHOP/MJ2CORE[.]WIN
HXXP[:]//MX[.]NEGOCIOAPPS[.]SHOP/
HXXP[:]//MX[.]NEGOCIOMX2[.]SHOP/
HXXP[:]//MX[.]NEGOCIOMX2[.]SHOP/FACTURAPAGO/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//MX[.]NEGOCIOMX3[.]SHOP/JM3WWVW[.]CORE
HXXP[:]//MX[.]NEGOCIOMX4[.]SHOP/
HXXP[:]//MX[.]NEGOCIOMX[.]SHOP/MJ1WIN[.]CORE
HXXP[:]//MXX[.]DIRETORGERALXX[.]SHOP/
HXXP[:]//MXX[.]DIRETORGERALXX[.]SHOP/FACTURA/
HXXP[:]//MXX[.]DIRETORGERALXX[.]SHOP/FACTURA/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//NEGOCIOMX3[.]SHOP/FACTURA_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//PAGO[.]SGSCOMMANAGER[.]SHOP/APP_DOCS_CD20185205/DOCS_FICHERO05502022[.]PHP
HXXP[:]//PAGOS[.]MULTISESSIONLTDA[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP?DOCUMENTS-PAGOS
HXXP[:]//PORTAL[.]ADIMCOPAGOS[.]SHOP/NF-5034297/NF5034297[.]PHP?BR152346
HXXP[:]//PORTAL[.]ROSENPARKPRIVATEPAGOS[.]SHOP/RECIBO_EMISSIONS/RECIBO_EMISION[.]PHP?DOCSRECIBOSMX1732
HXXP[:]//PORTAL[.]ROSENPARKPRIVATEPAGOS[.]SHOP/RECIBO_EMISSIONS/RECIBO_EMISION[.]PHP?PAGOSDOCSMX
HXXP[:]//PROMOCIONES[.]ROSENPARKPRIVATEPAGOS[.]SHOP/RECIBO_EMISSIONS/RECIBO_EMISION[.]PHP?PAGOSDOCSMX01
HXXP[:]//Q-R[.]TO/BDYGW2/
HXXP[:]//RECIBO[.]MBUSSINESSCFDI[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP?DOCUMENTS-APPSMX
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/CMH9MHRGHJV99ATV3EPBTXMO_0K0NK3LZ9XXTQPVI84B4JQTJ1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/DOCS_J06MC512DJMXGO15SMX22_1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/DZLAPWQAVKP2NHM_5JMHDTLSBSUVF7BKJNMGVMZM6[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/FILEPII_428DEAC269C4D907881538D5D974B18890B7D825[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/J06MC512DJMXGO15SMX22_1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/J16MP250STXSDG02SM5[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/J22MC510DJMXGO15SMX1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/PAGOS_RECIBO_J12MC520DJMXGO18SMX2[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/PDF_ARCHIVO_09112022[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/PDF_ARCHIVO_MJMOSMOC8VSMSDK5JNMX1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO0111_20552MXJMLSPC2VSMSDK5JNMX1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO0811_20252MXGOJMWC2VSMSDK8JNMX1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO0811_20252MXGOJMWC2VSMSDK8JNMX2[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO1710_250SPJMLWIC9VJKR6JNMX1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO1710_250SPJMLWIC9VJKR6JNMX1[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO2110_2555MXJMLSPC2VSWK8JNMX2[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/RECIBO_PAGO2110_2555MXJMLSPC2VSWK8JNMX2[.]ZIP
HXXP[:]//RECIBOPAGOSMX2022[.]BLOB[.]CORE[.]WINDOWS[.]NET/CONTAINERMX01/YFCXASVFXZ2OSRHCO_7SHNP2NJUGKRBU3Y3[.]ZIP
HXXP[:]//SAC1[.]FAFORCE[.]SHOP/
HXXP[:]//SAC2[.]FACTGERFORCE[.]SHOP/
HXXP[:]//SAC3[.]FACTGIFORCE[.]SHOP/
HXXP[:]//SAC4[.]FACTGEFORCEX[.]SHOP/
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?15234789MVCB45020155A787F5A_SERIE_IWAVZ_Y_FOLIO_1524863877[.]HTML
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?15996321475MNCVBGDHJUGH
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?15996321475MNCVBGDHJUGH
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP??4502010-4B6E-8F5E-8E1D0DD985_SERIE_IWAVZ_Y_FOLIO_158502022[.]HTML
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?BNVMXNJKUYT
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?MBNGNJUI5293652MNVHJF
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?MHGNJUYTMJNBVF11K1256399
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?MHGNJUYTMJNBVFGHK1256399
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?MNBGFHSJ1963251
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?MXVCBNJMKIOLA
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?MXVCNMJBHN1523694CVBNJMKLLM
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP\?MXVCNMJBHN1523694CVBNJMKLLM
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?PORTALFACTURAMX1526399
HXXP[:]//SSL[.]ADIMCOPAGOS[.]SHOP/DOCS_FICHEROS/DOCSFICHEROS[.]PHP?PORTALFACTURAMX1526399?45020155A787F5A-5337-4B6E-8F5E-803E1D0DD985_SERIE_IWAVZ_Y_FOLIO_158502022[.]HTML
HXXP[:]//SSL[.]MARKETING4GRP[.]SHOP/DOCS_RECIBOS/CFDIPAGOS[.]PHP
HXXP[:]//SSL[.]MULTISESSIONLTDA[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP
HXXP[:]//SSL[.]MULTISESSIONLTDA[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP?PAGOS-DOCUMENTS
HXXP[:]//SSL[.]WESTNEX[.]SHOP/DOCS_RECIBOS_EMISSION/APPSPAGOS[.]PHP
HXXP[:]//STORAGERECIBOSPAGOS0712[.]BLOB[.]CORE[.]WINDOWS[.]NET/FICHEROSMX/FACTURA_COMPROBANTE_28537577289461_79436744847[.]ZIP
HXXP[:]//STORAGERECIBOSPAGOS0712[.]BLOB[.]CORE[.]WINDOWS[.]NET/FICHEROSMX/PDF_ARCHIVO_DJTOMMOX8VSJMDS5JNMX4[.]ZIP
HXXP[:]//WWW1[.]COMPROBANTEMX[.]SHOP/PAGO_FACTURA/MZHVBFCLSDKHCHSFGI5DF54VSFDG518FSSZDF548DF357F86[.]PHP
HXXP[:]//WWW1[.]EMPRESA020[.]SHOP/COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]EMPRESARIALLMXX[.]SHOP/PAGO_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]EMPRESARIALLMXX[.]SHOP/PAGO_RECIBO/
HXXP[:]//WWW1[.]EMPRESARIALLMXX[.]SHOP/PAGO_RECIBO/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]EMPRESARIALL[.]SHOP/COMPROBANTE_PAGO/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]EMPRESARIALMXX[.]SHOP/PAGO_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]FACTURAMX[.]SHOP/PAGO_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]MEXEMPRESARIIAL[.]SHOP/FACTURA/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]MEXFACTURA[.]SHOP/SPEI_PAGO/INDEX[.]PHP
HXXP[:]//WWW1[.]MXEMPREESA[.]SHOP/PAGO_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]MXEMPRESAR[.]SHOP/PAGO_COMPROBANTE/
HXXP[:]//WWW1[.]MXEMPRESAR[.]SHOP/PAGO_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]MXEMPRESAR[.]SHOP/PAGO_COMPROBANTE/INDEX[.]PHP
HXXP[:]//WWW1[.]MXEMPRESSARIIAL[.]SHOP/PAGO_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]MXFACTURA[.]SHOP/COMPROBANTE_SPEI/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]NEGOCIOMX2[.]SHOP/FACTURA_PAGO
HXXP[:]//WWW1[.]NEGOCIOMX2[.]SHOP/FACTURA_PAGO/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]NEGOCIOMX2[.]SHOP/FACTURA_PAGO/DASSSASHYTSRFWEWDW4W4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREY[.]PHP
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/7777777777/
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/COMPROBANTE_FACTURA/
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/FACTURA/
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/FACTURA_COMPROBANTE/
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/FACTURA_COMPROBANTE/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/FACTURA/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/FACTURA/DASSSASHYTSRFWEWDW4W432DCADSSSWE32DSFWYWYW67WJJEHNSBVCDFREYD[.]PHP
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/PAGO_FACTURA/
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/PAGO_RECIBO/
HXXP[:]//WWW1[.]NEGOCIOMX3[.]SHOP/RECIBO_FACTURA/
HXXP[:]//WWW2[.]BOGFAC[.]SHOP/NEWMAGIC[.]CERT
HXXP[:]//WWW2[.]BOGJAM[.]SHOP/CONTROLSTRICKV3[.]VBP
HXXP[:]//WWW2[.]EMPRESARIALMX15[.]SHOP/JAMANEW2[.]PNG
HXXP[:]//WWW2[.]JAMNET[.]SHOP/GAMERS2[.]MIC
HXXP[:]//WWW2[.]JAMNET[.]SHOP/JAMANEW3[.]BMP
HXXP[:]//WWW2[.]JAMNET[.]SHOP/JMBACK[.]BMP
HXXP[:]//WWWS1[.]MBUSSINESSCFDI[.]SHOP/DOCS_RECIBOS/APPSPAGOS[.]PHP?DOCUMENTS
HXXP[:]//WWWS[.]EYEWATCHDESIGN[.]SHOP/DOCS_RECIBOS/CFDIPAGOS[.]PHP
HXXP[:]//WWWS[.]SMART2NOPAGOS[.]SHOP/DOCS_RECIBOS/CFDIPAGOS[.]PHP
Observable IOC
Below are the IoCs obtained by SCILabs, which have a High level of confidence. The following files can be used legitimately as (o since) during the dynamic analysis no evidence of malicious behavior was found, however, they may be indicators of infection. In case of detection, it is recommended to alert and perform threat hunting to confirm or discard any possible infection.
Hash SHA-256
ADCE448F59D3A0B844ABF70BD775543135F3D391DD9658B0868566C50BADBE9F
28225C5622637CDAED8342E14560E8DE7B53DD6BA145D973643FC4B5BDD67B75
D7840EEA40A5A88AF824F24473E95D0227E69C4439D6EA791D50CB94BF0CFB2A
B3CC3F8B65B37A807843E07C3848EBA3B86F6E2D0B67C6D7CB14E9660A881618
13F860134473D00689EF3B73008505F444824A6AD58F0C3FD84741D084766B8E
E698B70E15126295B7C573AAA72C000CF050487A491514E8797E5608AD6817F8
60B9BE4867B547D57AFA8B1856FAB95A55F7C246FFD8578CEC811287F14912EC
C0A68DD5BF81DA430F18E658AA83A4D7FA544F71B927438DA1C9424EEF6A156A
3B98BC63B042047ECE450C86C89B2D54005690DBFC95B33C3BA028FECFE0EA8E
18108C75EEC4CDE840614716C828C16912549BF18E0EDC610F15B0236B0512EA
FB59C5F1B02CCB8DFD0CAD9F1DDE148D43F998D24C170FB25D3C8645E8333B8C
C822D20ED712D55B207DBAF9027BD368AF10B70EE8C44A0D813969982AFA69A1

