Operation Saci, observed during november 2024

Overview
The following report aims to provide indicators of compromise, along with the technical tactics and procedures associated with a malware campaign named by SCILabs as Operation Saci, which was identified during the second week of November 2024 through ongoing threat monitoring and hunting activities in Latin America.
After conducting an investigation, SCILabs observed that the Grandoreiro and URSA/Mispadu malware families are being distributed through Operation Saci. Given the impersonated institution (Citibanamex) and the impacted banks, it is highly likely that the installed banking Trojan is targeting Mexico.
Operation Saci‘s distribution method is phishing emails, which may contain a hyperlink or an attached PDF file, using pretexts related to invoices, pending payment receipts, or payment vouchers. Its main objective is to distribute the Grandoreiro and URSA/Mispadu malware families, which aim to steal banking information from users of different financial institutions through the overlapping of windows. In the case of some URSA/Mispadu installations, they may also steal browser history, Outlook credentials, and SMTP access.
It is important to mention that, during this investigation, SCILabs found different overlaps between various aspects of the Grandoreiro and URSA/Mispadu infection chain. First, the Grandoreiro infection will be addressed broadly (as it represents the final stage in this specific campaign) before highlighting the similarities between both attack flows and describing them in detail.
How could it affect an organization?
The malware families distributed by Operation Saci can steal banking and confidential information (such as browsing history and Outlook credentials) from all types of users, including employees of public and private entities. If an attack is successful within the organization, cybercriminals may leak or sell the stolen information in clandestine Dark Web forums or black markets, compromising the confidentiality, integrity and availability of the data, and leading to potential financial and reputational losses for clients.
Analysis
General context of the threat
During the second week of November 2024, through ongoing threat monitoring and hunting activities in Latin America, SCILabs identified an email containing an attached PDF file —protected by a password included in the same email— named after the victim’s email address. The email uses the pretext an alleged payment receipt to impersonate Citibanamex. It was determined, with a high level of confidence that this specific campaign is targeted at Mexico.
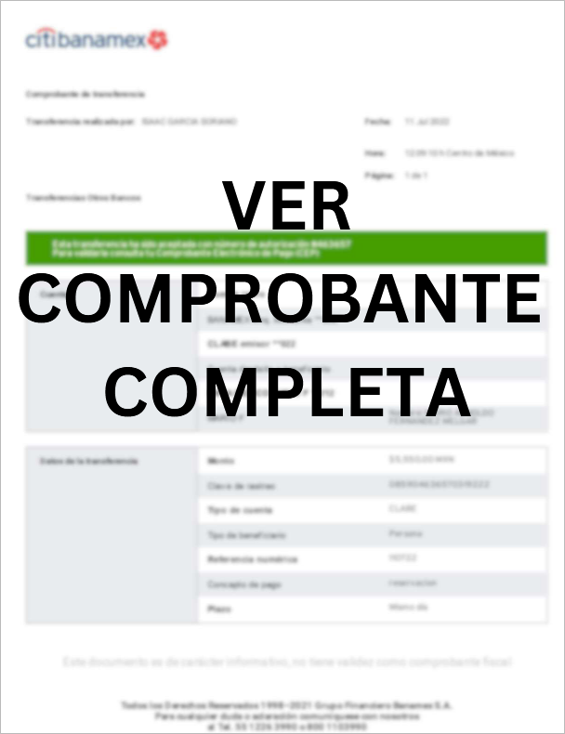
Figure 1. Visual appearance of the attached PDF file
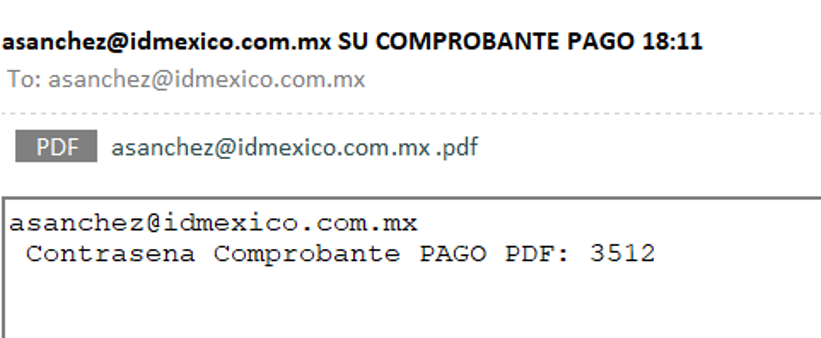
Figure 2. Phishing email visual appearance
Technical summary of Grandoreiro’s installation process
The PDF file contains an embedded hyperlink. When the victims click on it, they are redirected to a site where a file named “❉𝔸𝕣𝕔𝕙𝕚𝕧𝕠𝕤❉_①①⑨④①①,” in ZIP format is automatically downloaded. However, those numbers vary with each download.

Figure 3. Visual appearance of the automatic download site
The ZIP contains a file in HTA format (with the same name as the compressed file) which includes the instructions to download and execute a JavaScript script.

Figure 4. Content of the compressed file

Figure 5. Code fragment contained in the HTA file
Furthermore, as an additional defense evasion mechanism, the malware displays an alleged password validator, typical of other malware families like URSA/Mispadu.
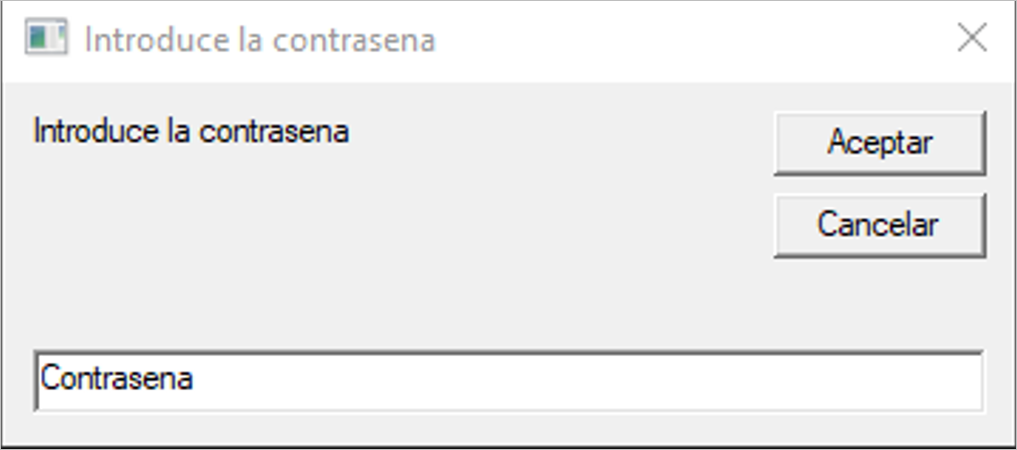
Figure 6. Password validator used by Grandoreiro in this campaign
After the validation, the second stage of the infection begins. The script named 6725c86d7fa55.js is responsible for downloading an additional dropper in VBS format installed within the %PUBLIC% directory.

Figure 7. Code fragment contained in the JavaScript file
This dropper performs the following tasks:
- Code Formatting: formats a text string corresponding to PowerShell code.
- Download: this function downloads a second file in VBS format that works as a Grandoreiro dropper and saves it within the %PUBLIC% directory.
- Execution: executes the following Grandoreiro dropper, which is also in VBS format.

Figure 8. Code fragment contained in the first VBS file
This second dropper performs the following tasks:
- Download: opens the site hxxp[:]//62[.]113[.]116[.]63/mx01/cancun01[.]zip and downloads a compressed file in ZIP format named “cancun01”.
- Execution: searches for executable files (with EXE extension) within the compressed file; if it finds any, it automatically runs it.
Information registration: obtains the name of the infected computer and through a GET request with the form hxxp[:]//62[.]113[.]116[.]63/conta[.]mx/index[.]php?nomepc=[equipo_name] shares it with its command server and control.

Figure 9. Code fragment contained in the second VBS file
SCILabs identified that the compressed name cancun01.zip contains four files, which were observed in a campaign documented by SCILabs in July of this year and are described below:
- CSRPS.exe: this is a legitimate file that belongs to an application called Beyond Compare11.
- CSRPS.dll and unrar.dll: these are two legitimate libraries necessary to execute “CSRPS.exe.”
- 7zxa.dll: corresponds to the malicious library, which uses the Grandoreiro‘s technique of increasing its size to make it challenging for security tools to analyze static and dynamic data. In this case, it weighs almost 2GB.
It is worth mentioning that these artifacts are unzipped to a randomly named folder in the root of C:\ composed of <one number><one capital letter><three lowercase letters><three numbers>
The DLL 7zxa.dll is loaded into memory by the CSRPS.exe executable using the DLL Hijacking technique. In this case, the technique exploits the CVE-2024-7886 vulnerability by replacing the original library with a malicious one crafted by the attacker.
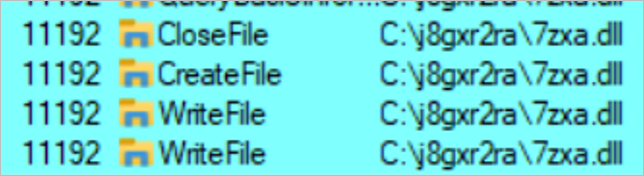
Figure 10. Evidence of the existence of the DLL Hijacking vulnerability
During the dynamic analysis of the artifacts, the SCILabs team identified that the malware records the computer’s infection in a log that contains the victim’s IP address and the names of the files that were downloaded.

Figure 11. Fragment of victim registration log
Furthermore, within the text strings of the process deployed by the malware, some of the target banks (all of them from Mexico) could be observed.
| Bank |
| Citibanamex |
| Afirme |
| Banco Azteca |
Table 1. Banks targeted by Grandoreiro in this campaign
Finally, the Trojan generates persistence within the Windows registry keys at HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
Summary of the attack flow observed in the Grandoreiro campaign
- The user receives a phishing email using pretexts related to pending payment receipts, invoices, or vouchers.
- The email contains a password-protected PDF file with a hyperlink embedded in it.
- If the user clicks on the hyperlink, they are redirected to an automatic download site from where they obtain a compressed file in ZIP format.
- If the user decompresses the file, they obtain a file in HTA format, corresponding to the first malware dropper.
- If the user executes the HTA, the malicious banking Trojan activity described below begins:
- Deploys a password validator.
- If the user solves it correctly, it leads to the next malware stage.
- Executes a script in JS format that is responsible for launching a dropper in VBS format.
- A second VBS dropper is installed in the %PUBLIC% directory. It is responsible for downloading a compressed file in ZIP format containing a legitimate executable and a malicious DLL that is loaded into memory and corresponds to the Grandoreiro payload.
- Information from the victim’s computer is shared with its command-and-control server.
- The Trojan generates persistence within the Windows registry keys in HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
Summary of the attack flow observed in the Grandoreiro campaign

Figure 12. Grandoreiro‘s observed attack flow
Overlaps observed between Grandoreiro and URSA/Mispadu
SCILabs identified the following overlaps during the analysis of the Grandoreiro campaign described earlier in this report, which together give rise to Operation Saci.
After performing the corresponding analysis, SCILabs identified numerous coincidences between the Grandoreiro infection chains and those of URSA/Mispadu (observed in previous reports), which are described below.
- Download template: Both Grandoreiro and URSA/Mispadu use a template with a white background, black text, and a gray box (25%) that indicates when the download of the first dropper is started and completed.

Figure 13. Matches of the templates used by Grandoreiro and URSA/Mispadu
- File generation function: Grandoreiro and URSA/Mispadu use the HTML Smuggling technique to generate and download the compressed file containing the first dropper. Within the source code of the automatic download site, numerous variables with pseudorandom letters that vary between uppercase and lowercase letters and numbers are observed. There is also a base64 string that corresponds to the ZIP with the HTA script inside, followed by the final name of the artifact and the different conditions to point the user to when the download is started and completed.
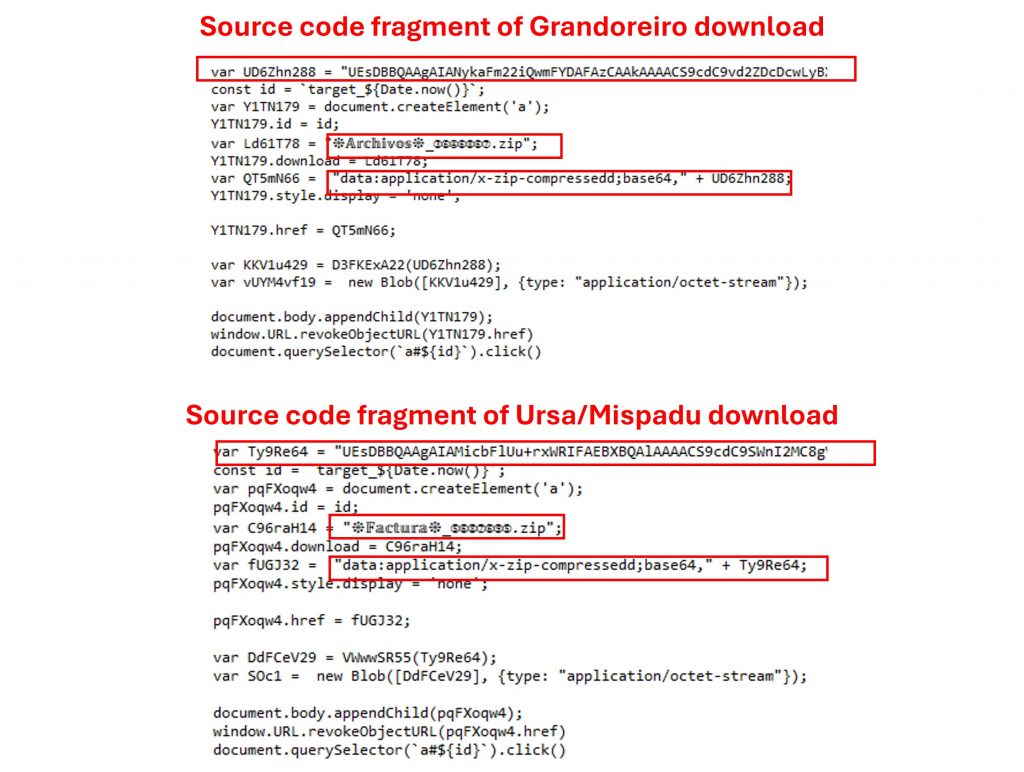
Figure 14. Matches between the source code of the Grandoreiro automatic download site and URSA/Mispadu
- Archive typography: Both Grandoreiro and URSA/Mispadu use distinctive typography to name their artifacts. They use double-stroke letters from the Unicode block known as Mathematical Alphanumeric Symbols; they also use the special Unicode character known as the decorative asterisk “❉”, and employ pseudo-random numbering from the Unicode block for CJK Unified Ideographs.

Figure 15. Typography similarities of Grandoreiro and URSA/Mispadu
- First dropper written in HTA format: Grandoreiro and URSA/Mispadu use scripts written in HTA as the initial dropper to download and execute a second dropper written in JavaScript.

Figure 16. Matches in the table content of the first dropper from Grandoreiro and URSA/Mispadu

Figure 17. Matches in the code of the first dropper of Grandoreiro and URSA/Mispadu
- Password validator: Both Grandoreiro and URSA/Mispadu use a password validator (commonly a password) to continue their infection chains.

Figure 18. Matches in the password validator of Grandoreiro and URSA/Mispadu
- Second dropper written in JS: both Grandoreiro and URSA/Mispadu use a JavaScript script to download additional artifacts written in VBS, install them in the %PUBLIC% directory, and execute them. It is important to note that while the files downloaded by this dropper are written in the same language, in this case the code is different. However, their purpose remains the same: to continue the infection chain.

Figure 19. Matches in the code of the second dropper of Grandoreiro and URSA/Mispadu

Figure 20. Matches in the installation of the third dropper of Grandoreiro and URSA/Mispadu
- Suspended account template: Both Grandoreiro and URSA/Mispadu use a template on their command-and-control, and malware download servers that warn of a supposed suspended account. SCILabs has already identified this as one more defense evasion mechanism used by malware operators to divert analysts’ attention and avoid further analysis.

Figure 21. Matches in the suspended account template on Grandoreiro and URSA/Mispadu download and C2 servers
- Use of subdirectories with particular names: Both Grandoreiro and URSA/Mispadu use subdirectories composed of one or two letters, for example, /v, /fw, among others, on their command and control and malware storage servers, where it was possible to identify malicious artifacts related to the analyzed campaigns.

Figure 22. Similarities in the Grandoreiro and URSA/Mispadu subdirectories
After reviewing the evidence available at the moment, SCILabs has the hypothesis (with a medium level of confidence) that the campaigns mentioned in the overlap analysis are related to each other or belong to the same threat actor; however, without a greater amount of evidence, this relationship will be classified as an operation, named by SCILabs as Operation Saci.
Summary of the attack flow observed in Operation Saci
Below is the flow diagram of the malware attack used by Operation Saci.
- The user receives a phishing email using pretexts related to pending payment receipts, invoices, or vouchers.
- The email contains a password-protected PDF file with a hyperlink embedded in it.
- If the user clicks on the hyperlink, they are redirected to a site that automatically downloads a compressed file in ZIP format.
- If the user decompresses the file, they obtain a file in HTA format, which serves as the first malware dropper.
- If the user executes the HTA, the malicious banking Trojan activity described below begins:
- It deploys a password validator.
- If the user solves it successfully, it leads to the next malware stage.
- Executes a script in JS format that is responsible for launching a dropper in VBS format.
- The Trojan generates persistence within the Windows registry keys in HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- A second dropper written in VBS is installed in the %PUBLIC% directory to download the following malware stages.
- In the case of Grandoreiro, it downloads a ZIP-compressed file containing a legitimate executable and a malicious DLL, which is loaded into memory using the DLL-Hijacking technique and serves as the Grandoreiro payload.
- In the case of URSA/Mispadu, it uses an AutoIt Script to steal SMTP credentials as well as Google Chrome and Microsoft Edge history. If the environment is optimal for URSA/Mispadu, the malware is loaded into memory using a legitimate AutoIt executable along with a malicious AutoIt script.
- The information from the victim’s computer is shared with its command-and-control server.
Flowchart of Operation Saci

Figure 23. General flow diagram of an Operation Saci attack identified in this campaign
Observed TTPs aligned to the MITRE ATT&CK® framework
The following MITRE ATT&CK® Matrix was observed by SCILabs during the analysis of Operation Saci.

Table 2. Observed TTPs aligned to the MITRE ATT&CK® framework
Assessment
In recent months, SCILabs observed multiple overlaps between the infection chains of different families of banking Trojans like Operation Gecko Assault, which randomly distributes URSA/Mispadu and Mekotio, as well as the more recent Operation Saci. Knowing the threat landscape that affects Latin America can help organizations improve their security posture, accurately knowing the TTPs and modus operandi of malware operators.
The main danger of Operation Saci lies in the families of the banking Trojans it uses. URSA/Mispadu and Grandoreiro are two of the most persistent threats in LATAM. They usually attack multiple countries simultaneously and continually modify their TTPs.
Based on the analysis of Operation Saci’s infrastructure conducted by SCILabs, it is likely to remain active throughout the rest of 2024 and expand its geographical reach: evidence of successful infections has already been observed in Argentina and Brazil.
The potential victims of banking Trojans such as Grandoreiro and URSA/Mispadu are all types of users who do not know the social engineering techniques, or the pretexts used by the operators of this malware in their massive phishing email campaigns.
For these reasons, SCILabs considers important for institutions and companies to keep updated about the pretexts and indicators of compromise of these campaigns to minimize the risk of infection and the impact that the theft of banking information can have on organizations.
General recommendations:
- Block the IoCs provided in this report.
- Conduct awareness campaigns about social engineering techniques used by cybercriminals to distribute malware, such as phishing emails using pretexts related to invoices.
- Avoid having RDP services exposed to the Internet and implement Multiple Factor Authentication solutions to minimize the risk of cybercriminals using your infrastructure as a malware repository.
- Raise user awareness to discourage storing access credentials in web browsers and inform them about the associated risks.
- Identify suspicious Windows registry entries in the path HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
Recommendations related to Grandoreiro:
- Perform threat hunting activities on your EndPoints looking for directories with suspicious names within the paths associated with this banking Trojan, for example:
- C:\<9 random characters>
- C:\Users\<USER>\AppData\Local\Temp
- C:\Users\<USER>\AppData\Roaming
- Perform threat-hunting activities on EndPoint processes to identify executions of apparently legitimate processes such as javaw.exe, java.exe, cmd.exe, conhost.exe, more.exe, and chcp.exe that are not part of the operation.
- Perform threat-hunting activities on EndPoint processes to identify suspicious FlashFXP and Beyond Compare process executions with names other than the original, for example, RIPPOi.exe and ULTRAPCKJ.exe.
- Monitor suspicious traffic to geolocation web services such as IP-API[.]COM to identify possible malware compromises. Grandoreiro uses these types of domains during the infection chain.
Recommendations related to URSA/Mispadu:
- Consider blocking AutoIt on all EndPoints within the organization, as it is utilized by URSA/Mispadu and other banking Trojans.
- Identify AutoIt v3 Script executions.
- Perform threat hunting by searching for suspicious files within %APPDATA%, mainly with EXE, AU3 or PNG extensions.
- Perform threat hunting by looking for the creation of suspicious shortcuts within %APPDATA%\Microsoft\Windows\StartMenu\Programs\Startup, mainly with the name AudioDriver.
- Identify SQLite-type files in the %LOCALAPPDATA%\Temp directory, which may contain sensitive information from the victim’s web browser.
- Identify the SQLite3.dll file in the %LOCALAPPDATA%\Temp directory used in some campaigns by URSA/Mispadu.
Indicators of compromise
Below are the Indicators of Compromise identified in the analysis conducted by SCILabs, provided with a HIGH level of confidence.
Hashes SHA256
E418F21E8D2DD33DFE16A1BE01C39C356B6DEAC9308BC4F415E3062537D6A814
14060B79FC2D0DA2B77832C6C4C884A6C16582BC990F3658DC22661911BFC3A3
9A96C9BF51C751B5982219088B78BE606A9DDFCBDCAEB7889360D3CAAA833016
4CF99CB330E585065C1807018846FF0DF1E578B8C6CEEE121C7C3B0F1221C762
C1351BC6F191E5F4E04480A0A873144EFBDB81721D1EC5DB37C9C9D8BDC353D1
99D033C3A625A711D296B70DD178F52A9D28FA670871E2F392AFEF19E9E7D056
3CEB3738C05D6F12443A46C38F6A046658C9F876F2CCEA063234018915EB6FD0
27438884CC83C90A1C5690BC350FE5BB95F8DB35B3E436096B89CD67A8ECA182
23D290AF8A6C39D4E6749D42EDE056EE318480FAC89BB53EE3B31435C6F82A46
88F2533C9F16277F0895EF41CC3AAA7EEDEE88D1503A064DEC2E5473C76561AD
E2C76D4D639337EA98EE80E3F2E83111D25BB8ACBB017F0F54019B823459FDEE
BC49697F846F6EBD79D7156084056B3330729D783268D7E0732A7E4134CABEA9
2784544927037CC35441D5DEF3B024993CD17DEFC7D8A737881D8A3EC129896C
87045CD2D94D3C4280B870652ABA5B8C864CAF20CE340598DA33CE919D39251A
19D2416D99A77FEFF348EC102A87649DB2302FF16A42343F33FA34024837D7B1
0BA03E61E311B64C2886CD33FC438BA7CF8B5AC185FE9226EF668C262CF73EC7
C11C1C02DBA7C5BEB80ECEDB6A9518308D532850551316D32F786C2AD8315D24
0D44DC8EE5CDF32D498C43F36BD08623B354F8F3ACA2A4B6ADC085963DC0A364
Malware download sites
It is recommended to block the entire URL in order to avoid future false positives or operation failures.
hxxps://stomxfct[.]com/con/yPOXE2/RXb7941[.]js
hxxps://adjunto[.]pdfxml[.]store//6725608180da8/6725608180eb7[.]vbs
hxxp://62[.]113[.]116[.]63/mx01/cancun01[.]zip
hxxps://comprobantcdif.blogspot.com
hxxps[:]//carecenterhq[.]com/isuIVXBREGa/JJ2/BpxAu9/
hxxps[:]//carecenterhq[.]com/isuIVXBREGa/
C2 Servers
It is recommended to block the entire URL in order to avoid future false positives or operation failures.
hxxps://stomxfct[.]com/con/v
hxxps://stomxfct[.]com/
hxxp://62[.]113[.]116[.]63/mx01/
hxxp://62[.]113[.]116[.]63/v
hxxp://62[.]113[.]116[.]63/conta[.]mx/index[.]php
