Red Mongoose Daemon: a new banking trojan identified in May 2024 by SCILabs
Red Mongoose Daemon: a new banking trojan
Overview
The purpose of this document is to describe TTPs and provide indicators of compromise related to a new banking trojan that SCILabs identified during May through a threat monitoring and hunting in LATAM and named Red Mongoose Daemon.
The main objective of Red Mongoose Daemon is to steal victims’ banking information by spoofing PIX transactions through overlapping windows. This trojan is aimed at Brazilian end users and employees of organizations with banking information.
SCILabs was unable to identify the distribution method of this threat, however, based on its experience and the name of the files used in the identified campaign, such as “Apelacao_Processo-NNYN.msi”, “Processo-judicial.B9WU”, and “Pedido_Faturado. -WJVUC”, to mention a few, it is likely that the distribution method is through malicious emails using invoices and legal issues as pretexts, just like it is common in the activity of banking trojans in LATAM such as Grandoreiro and URSA/Mispadu.
How could Red Mongoose Daemon impact organizations?
Red Mongoose Daemon can steal banking information from all types of users, including organization employees. Additionally, it has command execution capabilities, as well as advanced anti-analysis and persistence methods that will be described later, which increase the possibility of successful attacks. If an attack is successful within an organization, cybercriminals can leak or sell the stolen information in clandestine Dark Web forums or on the black market, putting at risk the confidentiality, integrity, and availability of the information, leading to financial and reputation losses.
Analysis
Threat Context
During May, through a threat monitoring in the region, SCILabs identified a malicious file compressed in ZIP format. Upon conducting the analysis, TTPs different from those of other trojans discovered and reported by SCILabs were identified, such as the use of the legitimate tool Daemon Tools, and the creation and pseudo-random modification of directories for their persistence; that is how it was given the name of Red Mongoose Daemon.
SCILabs was unable to identify the distribution method for this campaign. However, being common in banking trojan campaigns in LATAM, phishing emails are likely to be used under the guise of supposed invoices, legal matters, and tax notes. These emails mostly contain embedded URLs that redirect the victim to sites for automatic downloading of ZIP-type files, which contain MSI files named after the pretext used, for example, “Apelacao_Processo-NNYN.msi.”
Because the names of the artifacts found were written in Portuguese and it is the Brazilian payment system PIX which the trojan attempts to impersonate, with a high confidence level, SCILabs determined that this campaign is aimed at Brazilian users.
During the investigation, SCILabs identified some overlaps with the Javali/Ousaban banking trojan, which are have general characteristics such as the appearance of some C2 Endpoints (shown below in Figure 1) and capabilities such as the manipulation of windows of the operating system (this technique is used by the majority of LATAM banking trojans); however, the infection chain, which will be detailed later, and the DLL of the trojan, in comparison with Javali/Ousaban campaigns.
Based on the above, SCILabs has the hypothesis that the threat actors behind Red Mongoose Daemon are also the operators of Javali/Ousaban and will continue monitoring them.
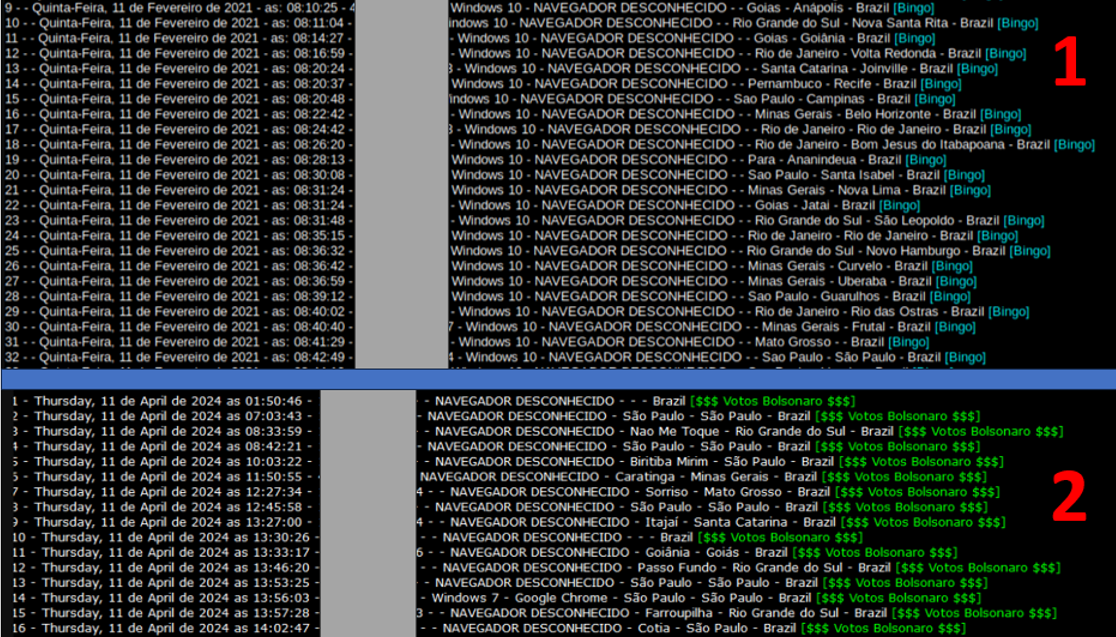
Figure 1. (1 – Top) Template used by Javali/Ousaban operators to query infected machines, (2 – Bottom) Template used by Red Mongoose Daemon operators with the same objective
Technical summary
The identified MSI file is named “Apelacao_Processo-NNYN.msi” and corresponds to the first Red Mongoose Daemon dropper. The infection chain begins if the victim executes it.
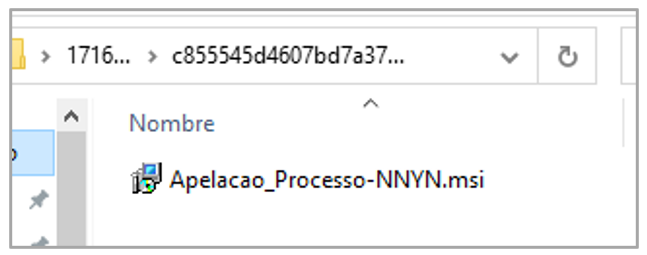
Figure 2. First Dropper
The MSI file contains the following artifacts:
- exe: The real name of this artifact is DTShellHlp.exe, which corresponds to a legitimate component of the DAEMON Tools software. This Windows’ executable is used to create virtual drives and mount disk images, providing different functionalities, such as a context menu, to facilitate their creation. It is mainly used in videogame environments.
- dll: This artifact is the malicious Red Mongoose Daemon DLL, loaded into memory through the DLL Side-Loading technique after executing the previous legitimate artifact.
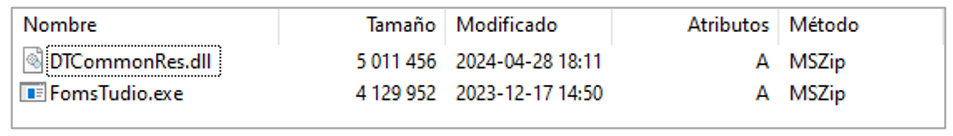 Figure 3. Compressed content of the first dropper
Figure 3. Compressed content of the first dropper
Once the victim executes the MSI file, the trojan is installed in the %APPDATA%/[directory with the pseudo-random name]. According to the analysis, the name of the installation directory may correspond to some legitimate applications such as “Dev-Cpp,” “Wireshark,” “Softplicity,” and “Notepad++,” and sometimes, simply random letters such as “CDTPL.”
In that same sense, the name of the DAEMON Tools executable is also assigned in a pseudo-random manner, placing names such as “recent_common,” “cache,” “recent,” “Temp,” or bck<execution date>, to mention a few. In the following figures (4, 5, and 6), there are different directories as examples where the executables (red icon) and the DLLs of the trojan are installed, which are sometimes renamed with the “.jwt”. If there is a legitimate installation of the applications mentioned above, the trojan does not modify its directories or files; it places the loader and the malicious Red Mongoose Daemon DLL.
In the following images, in addition to the trojan, there are other types of files with “.ini,” “.xml,” or “.cfg” extensions, which correspond to legitimate installations of the applications mentioned above and which have no relation to the chain of infection.
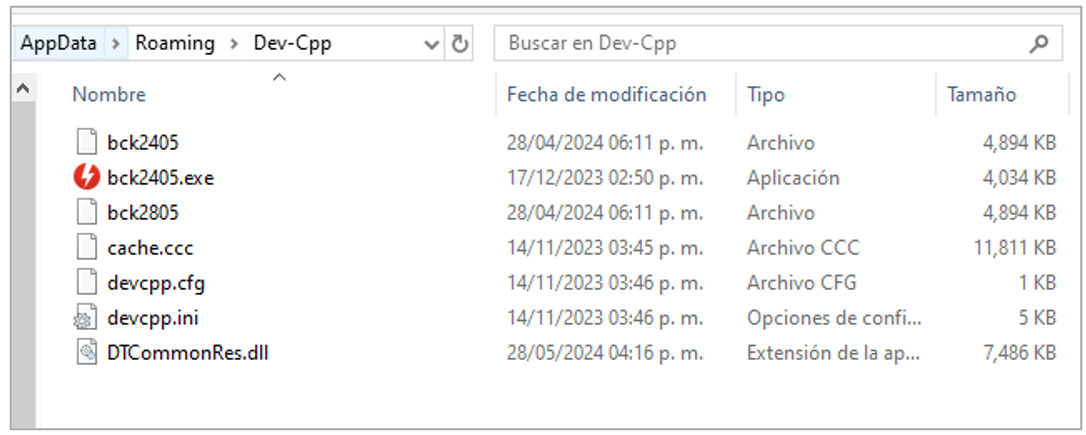
Figure 4. Example of execution in Dev-Cpp directory
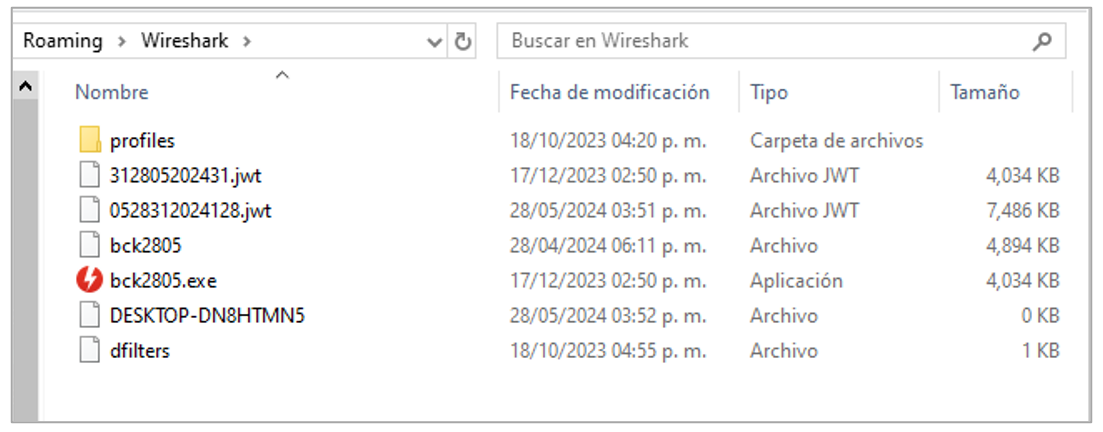
Figure 5. Example of running in Wireshark directory
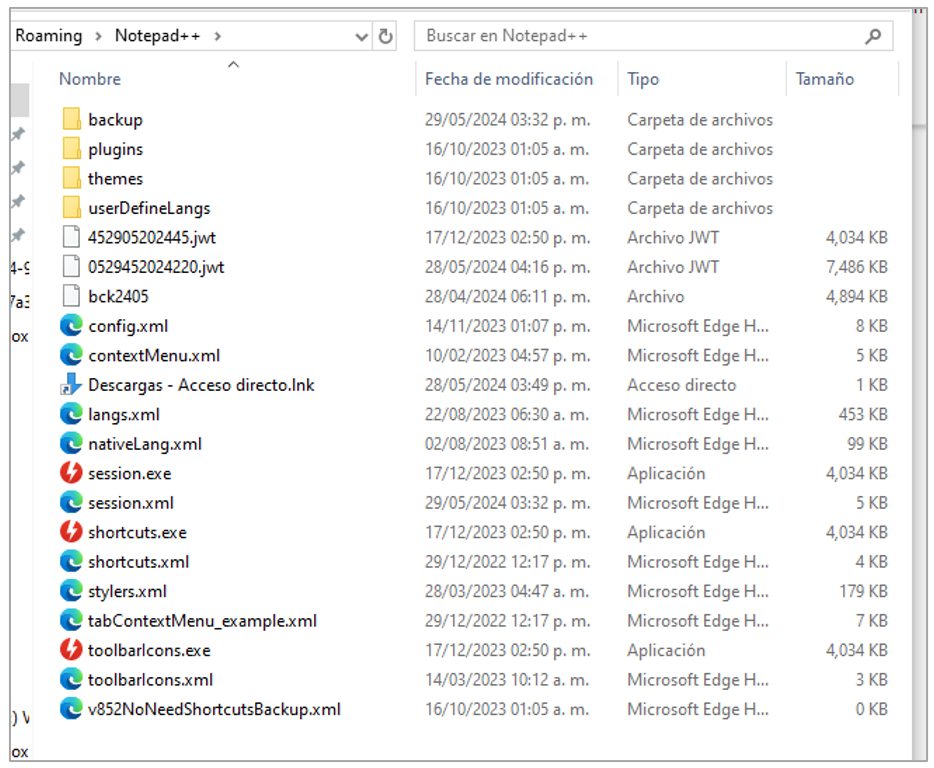
Figure 6. Example of execution in Notepad++ directory
Red Mongoose Daemon generates persistence using scheduled tasks that run every 5 minutes and a shortcut in the Windows home directory. It is important to mention that, with each computer restart, the trojan is reinstalled in a different directory.
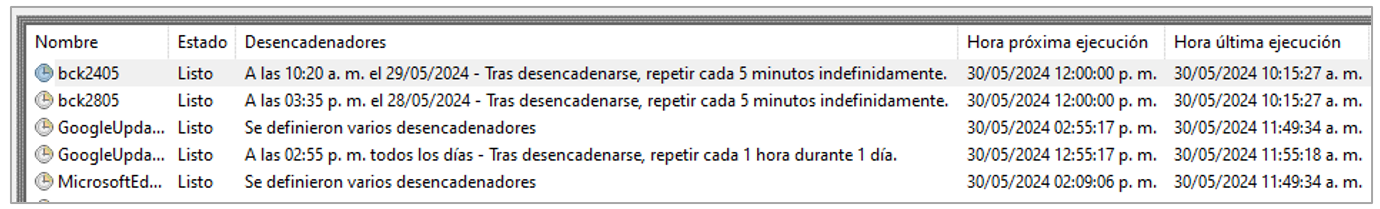
Figure 7. Persistence through scheduled tasks
As soon as the process starts, the malicious DLL and the legitimate executable change their name and extension to a name like <12 random numbers>.jwt.
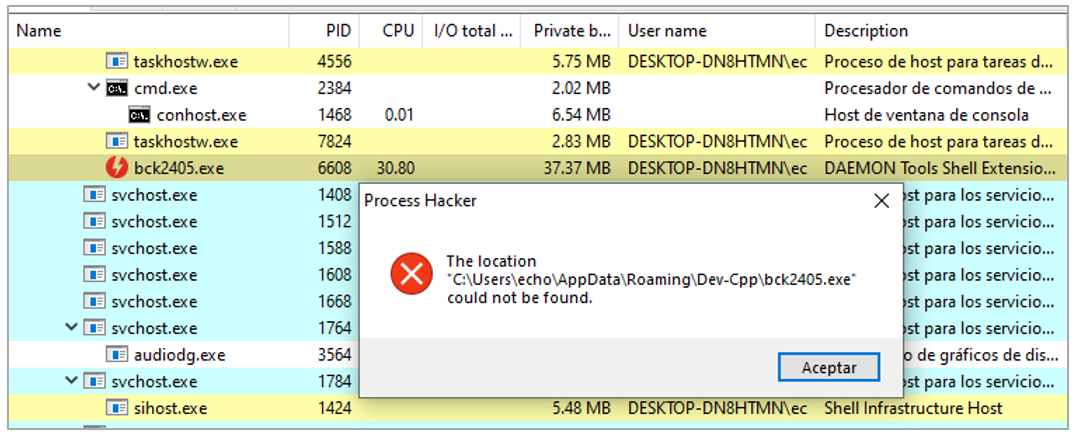
Figure 8. trojan execution
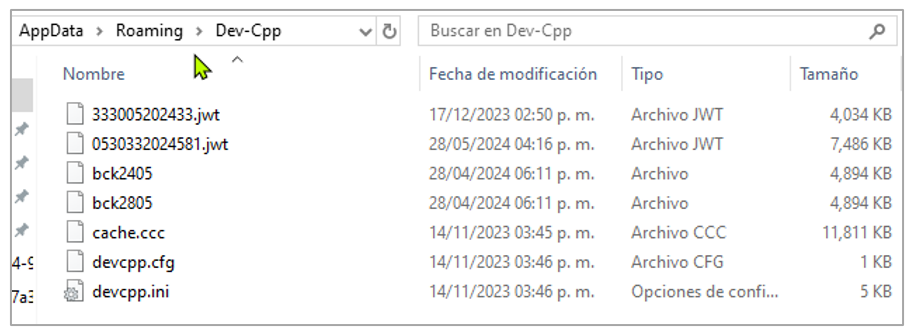
Figure 9. Files renamed by the trojan
Subsequently, it sets the registry key HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP\PROXYBYPASS with a value of 1 to try to evade security mechanisms and communicate freely with external servers, which is a common tactic to maintain persistence and control over the infected system.
Red Mongoose Daemon performs a query with its C2 through the URL hxxps[:]//rdcontra.com/clientes/index.php, where it saves the victim’s data such as IP, date of infection, device name, user, and country of origin. It is essential to mention that, if anybody tries to access it from the Internet (port 80 or 8080), a redirection is made to the URL hxxps[:]//i.pinimg.com/236x/5b/f8/1a/5bf81a501ab9d26db806e7fec4edfa75.jpg that corresponds to an image not used during the infection chain and can only be viewed from a web interface.
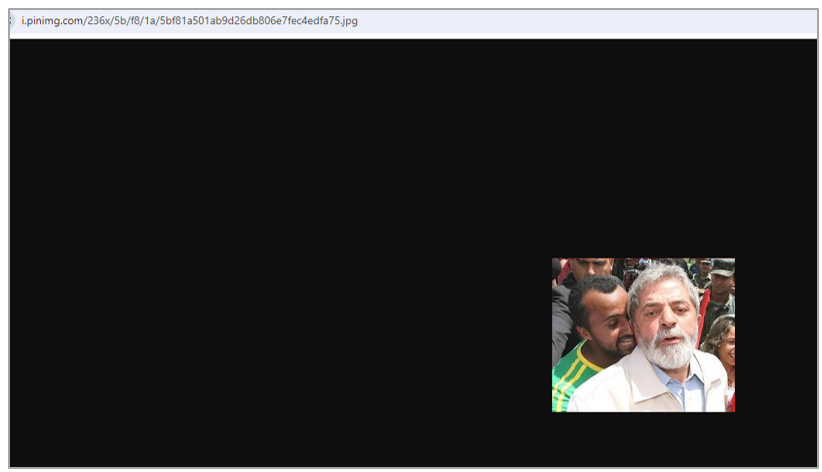
Figure 10. Redirection URL
The process chain created by this threat is:
- MSI file execution
- exe
- exe
- exe (/delete /f /tn “FomsTudioª”)
- exe (/create /SC MINUTE /MO 5 /TN “[random name]” /tr “%APPDATA%\<random directory>\[random name].exe k7”) migrating to recent_common.exe process
An important point to note is that the trojan needs the “k7” parameter to run successfully.
If the user enters a site that allows the PIX payment method of the Central Bank of Brazil, the trojan performs the window overlay technique to steal the victims’ information.

Figure 11. Window used by the trojan that tries to impersonate a PIX transaction
Finally, SCILabs identified that Red Mongoose Daemon has capabilities for manipulating and creating windows, executing commands, controlling the computer remotely, manipulating web browsers, hijacking clipboards, and impersonating Bitcoin wallets by replacing copied wallets with the ones used by cybercriminals, such as the following: 1Jp4A7NEwhk2uNPnZbewN9QfCdoXFRL9Xp. So far, no transactions have been identified using that wallet.
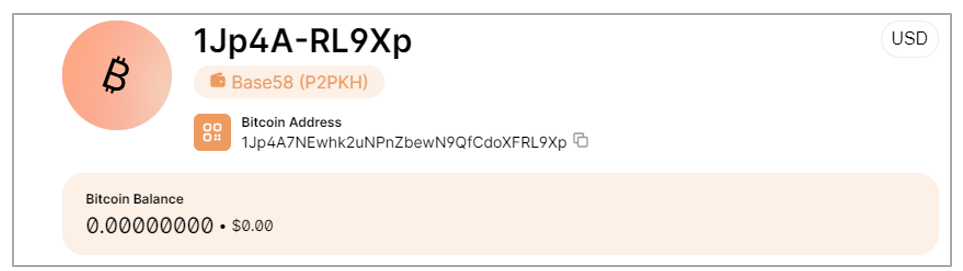
Figure 12. Attackers’ Bitcoin wallet balance
During the analysis, some common characteristics were identified in trojans that affect LATAM, such as Mekotio, Javali/Ousaban, and Grandoreiro. Some of them are the ability to manipulate the browser and the generation of Windows operating system’s windows.
While no windows associated with other banks were detected, the presence of these characteristics suggests that the trojan might also target other Brazilian banks.
In addition, during the dynamic analysis, it was identified that the trojan monitors the access to domains such as Outlook, Hotmail, and OneDrive, among others, so it is possible that it also aims to steal credentials.
Red Mongoose Daemon’s notable characteristics
Below, some distinctive characteristics of Red Mongoose Daemon are mentioned and compared with Javali/Ousaban trojan campaigns previously observed in the region, aiming to provide clarity in the identification of this new threat for future investigations, given that SCILabs identified some overlaps like as the appearance of some C2 Endpoints with Javali/Ousaban, mentioned in the “Threat Context” section of this document.
- Unlike the Javali/Ousaban campaigns observed in public sources in 2021 and others by SCILabs since 2023, the architecture of the Red Mongoose Daemon DLL is 64 bits.
- During the analyses carried out by SCILabs, it has been identified that threat actors use Borland/Embarcadero Delphi <= 10 along with Turbo Linker 2.5 in the process of building the Javali trojan DLL; on the contrary, in the Red Mongoose Daemon campaign, the use of Delphi 11, Turbo Linker 8 and MSLinker 8 was identified, the latter possibly to ensure compatibility with the use of library dependencies compiled with Visual Studio.
- A notable difference between the Javali/Ousaban campaigns and the Red Mongoose Daemon campaign is the absence of packers in the latter. In Javali/Ousaban campaigns, it is common to observe the use of packers such as VMProtect, Themida, and ENIGMA, but the threat actors in the Red Mongoose Daemon campaign did not use any packer.
- The trojan is detected by VirusTotal antivirus solutions, mainly as a generic trojan, in contrast to Javali/Ousaban campaigns, which are labeled as Ousaban by most antiviruses.
As can be seen in the following list, which shows some of the trojan’s capabilities through the analysis of the classes implemented in its source code, this trojan has the capabilities of most Latin American banking trojans, such as window spoofing and browser manipulation, except for the PIX transaction spoofing not previously observed by SCILabs.
- TClipBoard: Clipboard manipulation
- TMouse: Mouse manipulation
- TDragObject: Image Manipulation in Window Instances
- TJSONObject, TJSONArray: Manipulating data in JSON format
- TCustomCanvas, TCanvas, TScrollBar, TCustomPanningWindow: Creating and manipulating windows
- THTTPClient: C2 communication
- TGraphic, TPicture: Graphics and images manipulation
- PixTrocar: PIX window manipulation
The following table summarizes the general differences between Javalí/Ousaban and Red Mongoose Daemon.
|
|
Javalí/Ousaban | Red Mongoose Daemon |
| DLL architecture | X32 | X64 |
| Programming Language | Borland/Embarcadero Delphi <= 10 | Delphi 11 |
| Linker | Turbo Linker 2.5 | Turbo Linker 8 y MSLinker 8 |
| Packer | VMProtect, Themida y ENIGMA | – |
| Label assigned by most antivirus solutions on VirusTotal | Ousaban | Generic trojan |
Table 1. Differences between Javalí/Ousaban and Red Mongoose Daemon
Observed attack flow summary
- It is highly likely that the victim will receive a phishing email with pretexts related to supposed invoices, legal matters, and digital tax notes.
- The email probably contains a URL that takes the user to an automatic download site for a ZIP file.
- Inside the compressed file, there is an MSI-type file.
- If the victim executes the MSI file, the infection chain begins.
- 2 files contained in the MSI are deployed in the %APPDATA%/[random pseudo name] directory. The executable legitimate Daemon Tool has a pseudo-random name, s the loader and the trojan DLL.
- The [Random Pseudo Name].exe process is started, and the Red Mongoose Daemon DLL is loaded using the DLL Side-Loading technique.
- Persistence is generated through a scheduled task that runs every 5 minutes and through a shortcut in the Windows home directory. On each reboot, the installation directory and the name of the loader change.
- The trojan waits for the victim to consult a site that allows PIX transactions to steal information through window overlays and possibly steal information from other banks and credentials from sites such as Outlook, Hotmail, and OneDrive.
- The trojan connects with the C2 to share the stolen information.
Attack flow diagram
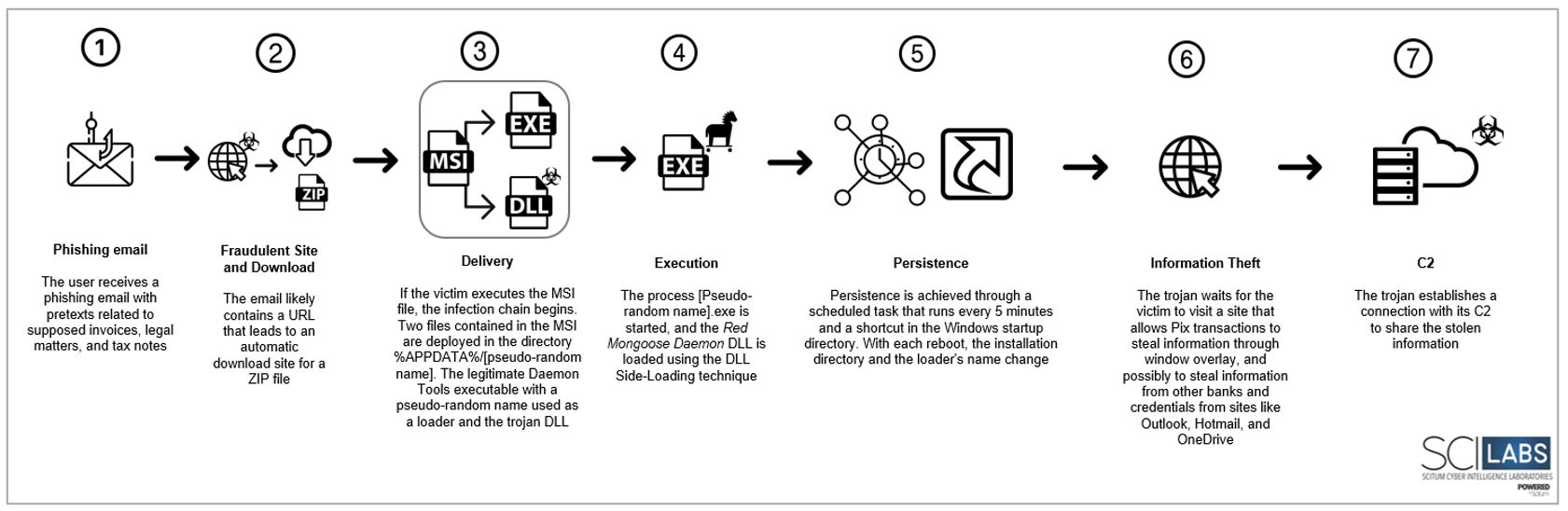
Figure 13. Attack Flow diagram
Observed TTPs aligned to the MITRE® ATT&CK framework
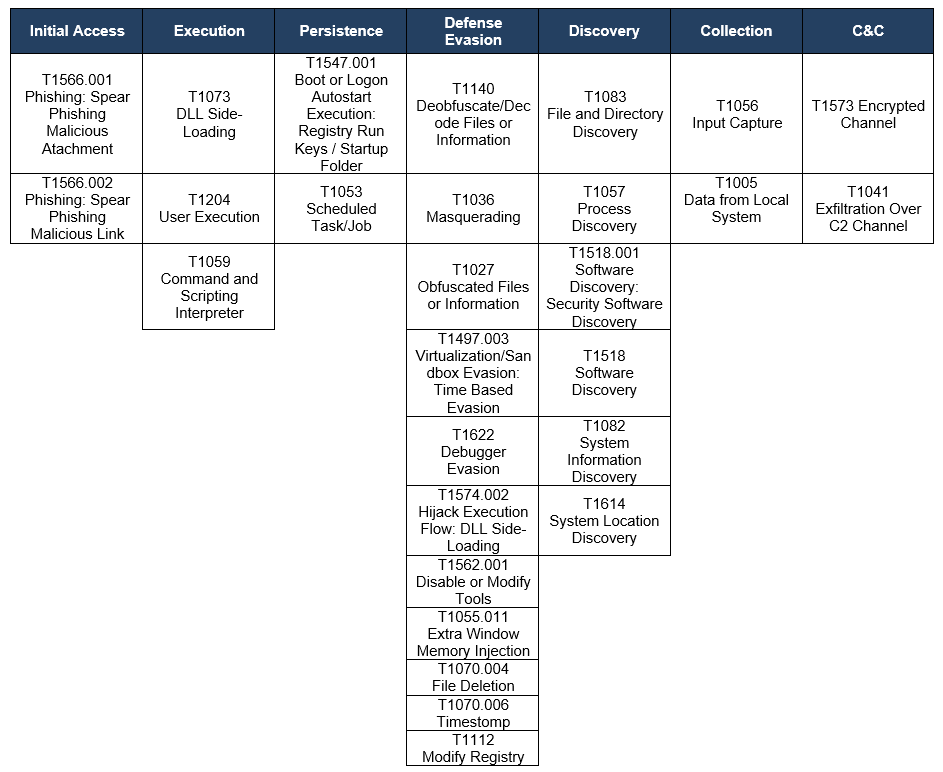
Table 1. Observed TTPs aligned to the MITER® ATT&CK framework
Conclusion
SCILabs considers Red Mongoose Daemon a significant threat in the region due to its advanced persistence and defense evasion techniques mentioned in this report. This trojan is likely to expand its activity to other Latin American countries, such as Mexico, and other trojans, such as Grandoreiro, Mekotio, and Javali, will adopt some TTPs mentioned in this report. Additionally, this trojan’s operators are expected to modify their artifacts and attack flow to ensure a higher success rate in their attacks.
SCILabs considers it essential that institutions and companies are aware of updates to TTPs and compromise indicators to minimize the risk of infection and the impact that the theft of banking information can have on organizations. We suggest considering the following recommendations:
Red Mongoose Daemon Specific Recommendations
- Add the IoCs shared in this document to your security solutions.
- Regarding emails, it is recommended to:
- Avoid opening emails from unknown senders
- Avoid opening suspicious links
- Avoid opening or downloading suspicious files
- Conducting comprehensive threat-hunting activities on EndPoint processes is a major security measure. Look for any suspicious and persistent processes in scheduled tasks and operating system home directories, particularly those with names such as bck<execution date>.exe or names of applications not authorized by the organization.
- Verify if the Daemon Tools and FormsTudio tools are installed, if they are legitimate or were consciously carried out by the user. Conduct an in-depth investigation to rule out or confirm an infection of the Red Mongoose Daemon banking trojan.
- Perform threat hunting activities on your EndPoints seeking to find directories or files with suspicious names such as “DTCommonRes.dll.exe” within the paths commonly used by Red Mongoose Daemon, as well as all directories in %APPDATA%.
Hashes SHA256
C855545D4607BD7A370F0B6AE575171050A7E9D003A4DA157EF90C15A2A92EEB
E1E2E0E4FF5C0FAE93B7D7526C5C0398E482EDDE0F5A0AF71430FFF5C852E1A6
27940A0201C50163493B8920588D932978A5AE8B192F7BF710FF030CCF048DB7
4E7A3F1CA0545919831F6CFAC4C7194716EB8B67FB15DBBB63C577E66F856E07
38D19F6C43007B1B314BE3C3E093E042F6F29638AF42F6045828C15901459DAB
78F865BC8012AC787408ECCE89CC8C6DBC294EBF929C62283C39504D9B1EEE2C
532CA82269C60CC6FC9197413C9BCC1CCA840F40B966524F1C2681660196C7F9
282FC28644DB919FEE960F1D09C94076EB5CC57C266E25D47DC1C13E38EAC27A
URLs
It is recommended to completely block URLs to avoid future false positives or interruptions in the operation.
hxxps[:]//i.pinimg.com/236x/5b/f8/1a/5bf81a501ab9d26db806e7fec4edfa75.jpg
hxxps[:]//rdcontra.com/clientes/index.php
hxxps[:]//rdcontra.com/awstats/awstats.pl
hxxp[:]//34.68.151.162/arquivo.msi
hxxp[:]//galvaoministerio.com
hxxp[:]//brigadafraternidade.com
hxxps[:]//notas.blogdns.net/6E%2028%205B%205E_5E128%205B%205E_5E%2028%205B%205E_5E128%205B%205E_5E%2028%205B%205E_5E128%205B%205E_/
hxxps[:]//newsfoos.from-mo.com/

