Beware of Emotet
The origin of Emotet
Emotet, also known as Geodo and Heodo, is a trojan aimed at all types of users, from ordinary users to corporate employees. Emotet is mainly distributed via MalSpam email campaigns. This malware was discovered in 2014, and its main functionality was to steal bank credentials; that is, it started as a banking trojan; however, over time, it evolved into a powerful Botnet, used as Malware-as-a-Service (MaaS)[1], to be the gateway for other types of malware such as Ryuk[2] ransomware[3], or other Trojans such as Trickbot[4], QakBot[/5] and Dridex[6] or Cobalt Strike[7] beacons.
Based on various investigations, Emotet is attributed to the threat actors known as MUMMY SPIDER[8] (also identified as TA542 or Mealybug), making it one of the most dangerous and most frequently distributed threats “In-the-wild[9]”.
Below is a timeline with an overview of Emotet’s evolution.
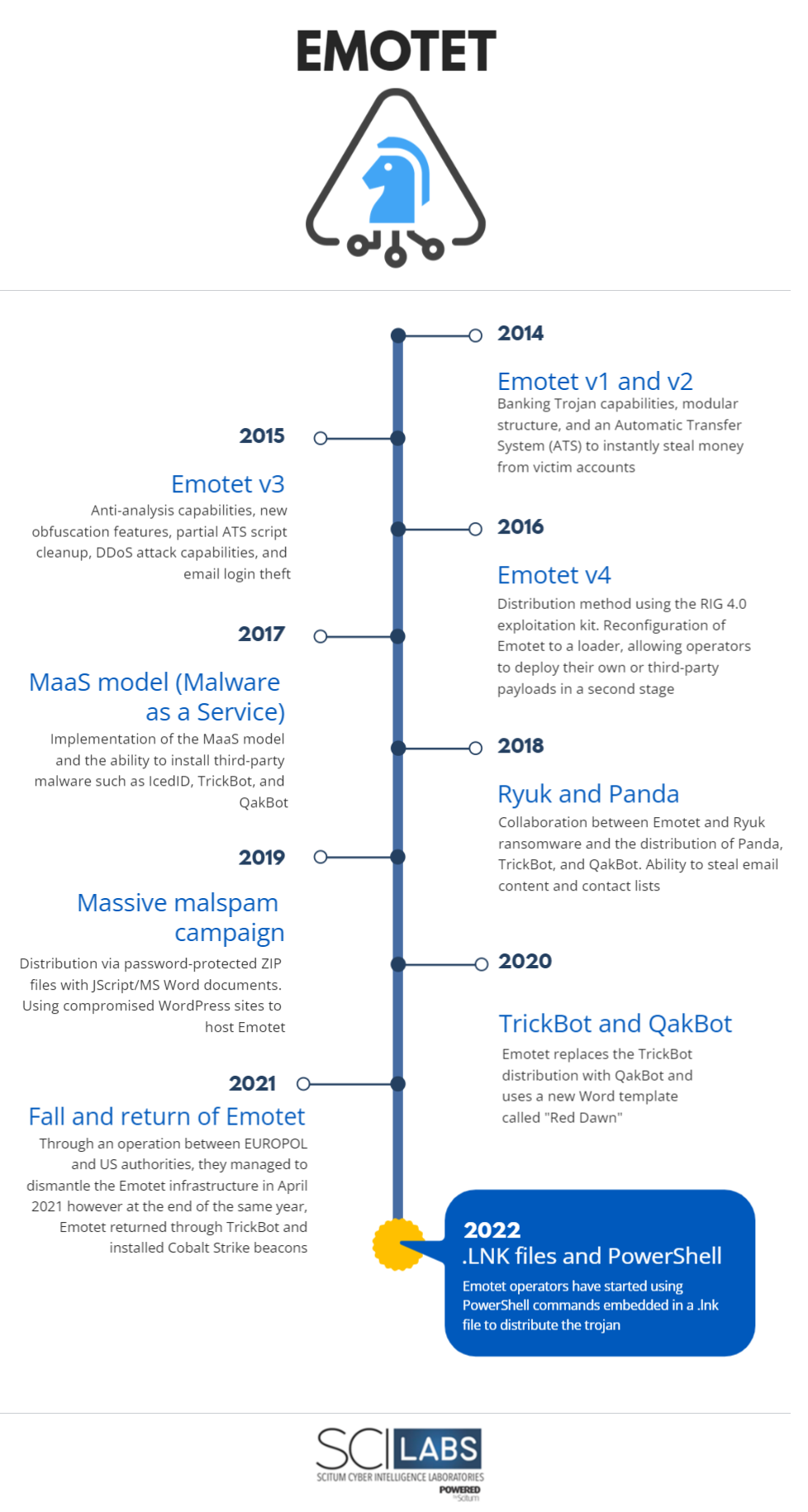
Figure 1 – Emotet timeline
The Sophisticated Emotet Botnet and Epoch Sub Botnets
As we mentioned before, Emotet evolved into a sophisticated Botnet, which comprises sub-groups or sub-botnets, called “Epoch.” Each Epoch has its C2 server infrastructure and distribution methods; this way of segmenting the Botnet can target different objectives with different payloads or act as redundant infrastructure[10].
As of this writing, five Emotet sub-botnets are known, from Epoch 1 to Epoch 5. In recent research[11], Epoch 1, Epoch 2 and Epoch 3 were observed before the Emotet takedown in early 2021; Epoch 4 and Epoch 5 were introduced after its revival in late 2021.
It is essential to mention that the Emotet subgroup can generally be identified by the public encryption keys contained in the C2 configuration of the samples. Although each one of the Epoch’s Emotet artifacts has its configuration data in different formats, they all store it in an encrypted “internal” DLL embedded in the Emotet executable payload.
According to some research carried out[12],[13], the Epoch 1, 2, and 3 sub-botnets can be identified because they use an embedded RSA (Rivest-Shamir-Adleman)[14] public key to encrypt the standard encryption key AES (Advanced Encryption Standard)[15] which is used to encrypt network traffic.
On the other hand, the most recent sub-botnets (Epoch 4 and Epoch 5) use Elliptic Curve Cryptography (ECC) to perform asymmetric encryption and make use of an embedded Elliptic Curve Diffie-Hellman (ECDH)[16] public-key identified as ECK1 and used for encryption, and an embedded Elliptic Curve Digital Signing Algorithm (ECDSA)[17] public key identified as ECS1 to perform data verification.
The way the Emotet Botnet is organized can make it difficult to track this threat, as research[18],[19] has shown that bots that are part of Emotet can be moved from one Epoch to another, as well as being able to maintain the Botnet running in case an Epoch is removed or is undergoing maintenance.
Main features of Emotet
As mentioned above, Emotet is distributed via MalSpam campaigns using Word or Excel documents, malicious links, password-protected .zip files, or, more recently, .lnk[20] files for download.
Phishing emails used to distribute Emotet can be simple or contain images of trademarks or logos of well-known companies with related urgency messages such as pending invoices or payments, authorizations, etc.
On the other hand, since the discovery of Emotet, the use of different modules[21] has been identified, among which the following are mainly found
- The Main module: can download other modules from a C2 server
- Spam module: used to propagate Emotet by sending emails
- Credential Stealing Module: used to steal credentials from web browsers and email clients using legitimate or malicious tools such as Nirsoft Mail PassView, WebBrowser PassView, and NetPass.exe
- Spreader module: used to enumerate network resources to try to spread to other computers, in addition to carrying out brute force attacks using an encrypted list embedded in the Emotet code; furthermore to copying to network folders where the trojan was accessed and configuring a service on the remote system to run the malicious file
- Email Harvesting Module: used to exfiltrate email content from infected computers
- Windows address book theft module: used to extract the list of names and addresses of each identified profile to share the information to the spam module later
Even more, Emotet can deliver additional malware to infected computers, such as Cobalt Strike beacons or the IceID[22], TrickBot o QakBot banking trojans, which can deploy other types of threats such as ransomware.
It is essential to mention that Emotet had a banking module, which was in charge of intercepting web browser traffic to banking institutions to steal the data sent by the victim, and a module to carry out DDoS attacks; however, based on public investigations[23], these modules are no longer active in the latest versions of Emotet.
Attack Flow
As we have mentioned throughout the article, Emotet has different versions and sub-botnets. This threat is constantly evolving; the attack flow may vary; however, below is an overview diagram of a common Emotet attack.
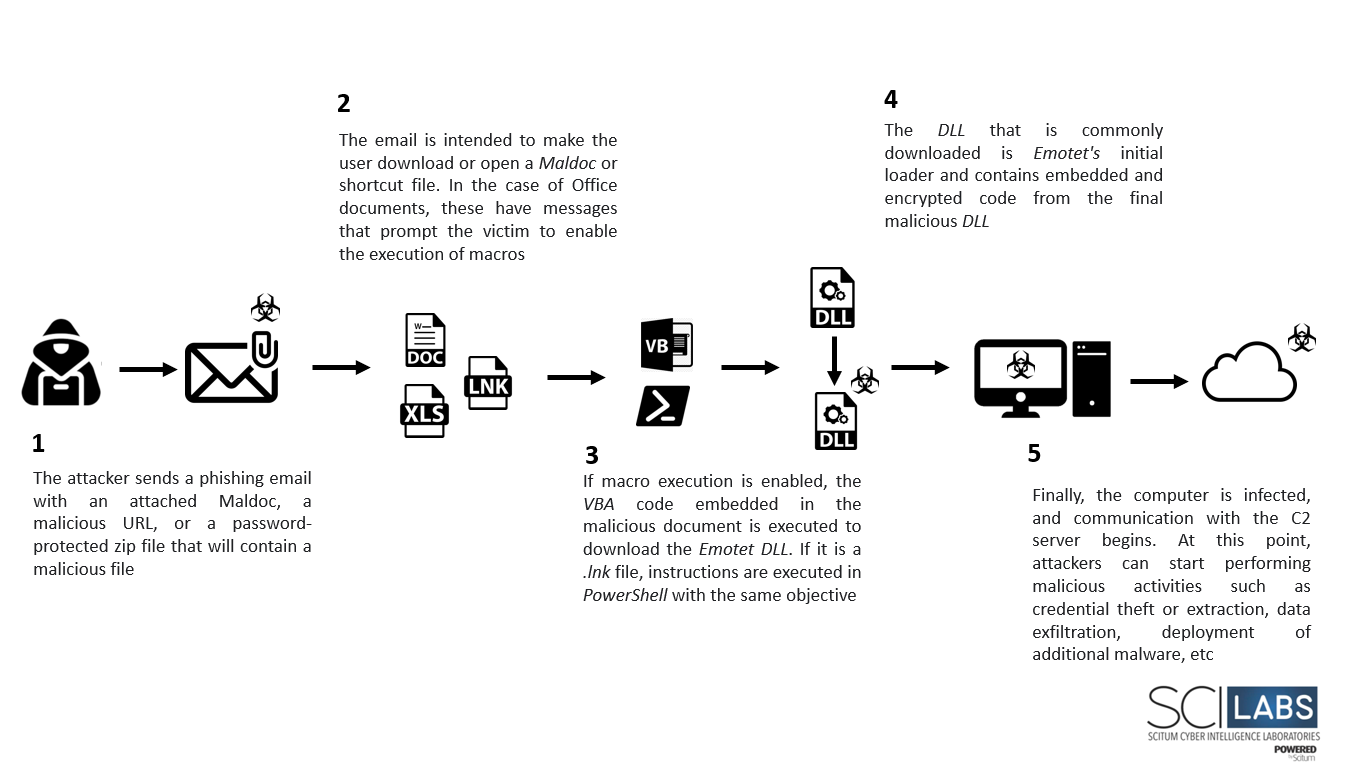
Figure 2 – Attack Flow
Key points that could help identify a potential Emotet phishing email
Emotet can be distributed using multiple pretexts in phishing emails; however, a few points to consider can help identify a potential Emotet campaign email.
Email subjects
- “Payment Remittance Advice”
- “Overdue invoice“
- “Please see attached”
- “Click here to view a file”
- “I have attached this file for your review”
- “Your Invoice”
- “Payment Details”
- “Buona Pasqua, happy easter”
- “Información de pago de [Empresa X]”
- “Notificación de pago”
- “Transacción de su factura”
- “Pago vencido”
- “Facturas pagadas”
- “Factura de venta”
- “Actualización de estado”
- “Documento necesario”
- “Nuevo pedido”
- “Recibo de su factura”
- “Adjunto … “
- “Perfecto!”
- “Se adjunta documentación para la firma”
- “Según la conversación mantenida te adjunto la información”
It is important to mention that, although some subjects have been identified in Emotet campaigns, they are not the only ones, and even the emails may not have a subject. Another point to consider is how, based on our telemetry, Emotet has been observed to be distributed.
- Microsoft Word or Excel documents with embedded macros
- PDF with malicious Microsoft Word or Excel document download links
- PDF with ZIP file download links with Microsoft Word or Excel files
- Password-protected ZIP archives containing Microsoft Word or Excel files
- Malicious Microsoft Word or Excel document download URLs
- ZIP file download URL with Microsoft Word or Excel files
During the last campaigns analyzed by SCILabs, we observed that the most frequent was the reception of Microsoft Word or Excel documents, which, by enabling the execution of Macros, the threat is executed and starts the chain of infection. Here are some email and document templates observed in SCILabs research.
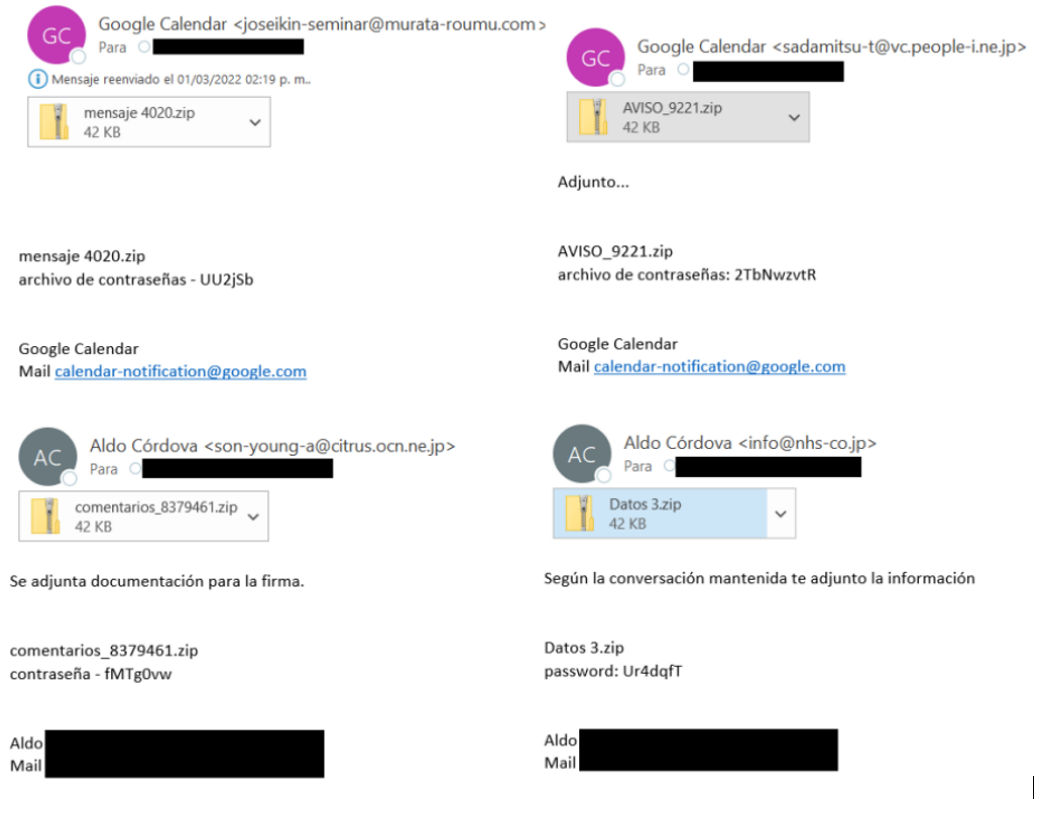
Figure 3 – Emotet email templates (I)
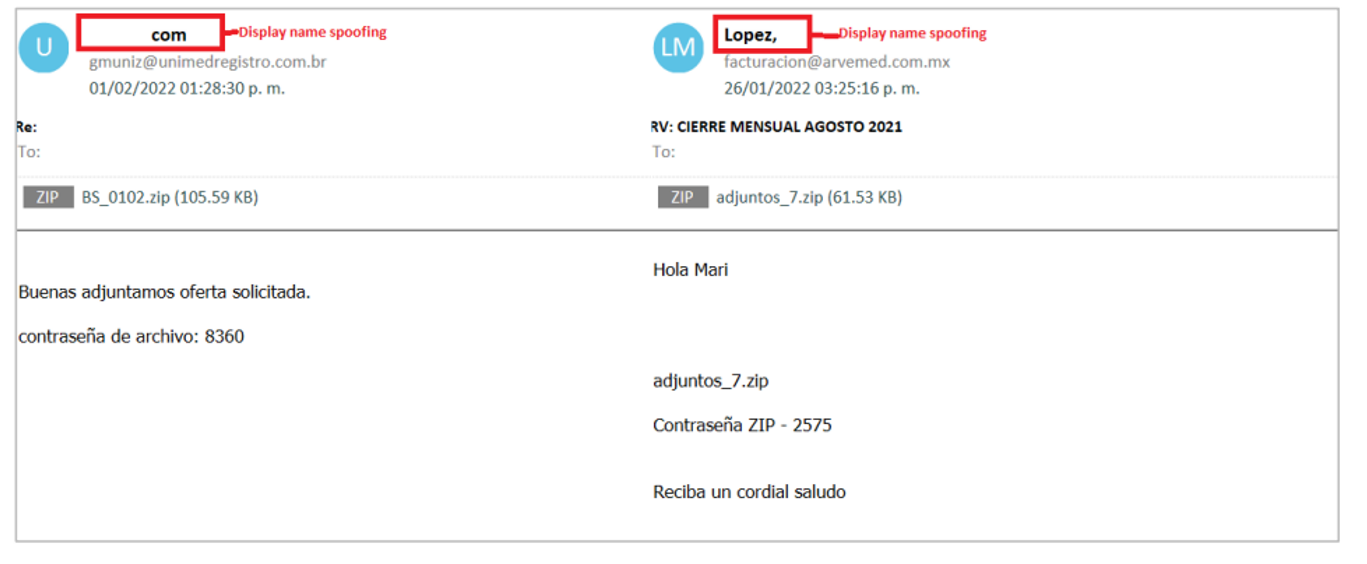
Figure 4 – Emotet email templates (II)
Figure 5 – Emotet Word template
Figure 6 – Emotet Exceltemplate (I)
Figure 7 – Emotet Excel template (II)
SCILabs believes that due to Microsoft’s decision to disable Microsoft Office macros by default, attackers have chosen to use other techniques to distribute Emotet. As we mentioned before, we have begun to observe the distribution of this threat through documents of the .lnk type to execute PowerShell or CMD commands directly and downloads Emotet.
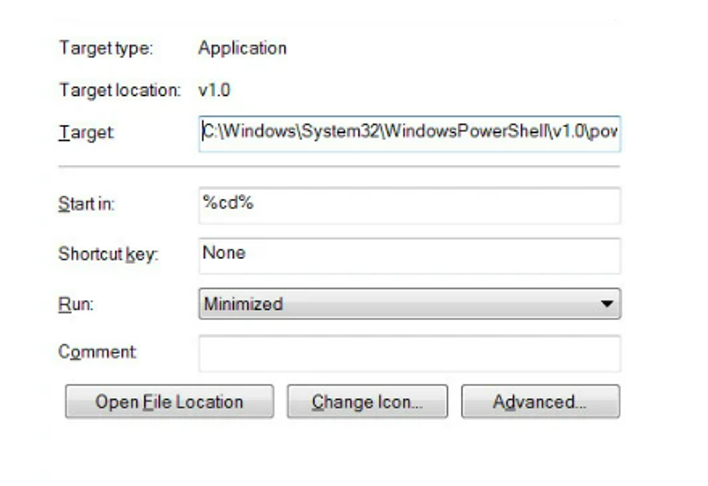
Figure 8 – Properties of a .lnk file with direct execution of PowerShell
Why is Emotet so dangerous?
Emotet is a threat that is constantly improving its capabilities, with a highly versatile infrastructure distributed all over the world, which makes it challenging to eradicate; in addition, as we mentioned before, Emotet operates as Malware as a Service (MaaS), which means that it is used to be the entry point for more dangerous threats like ransomware.
Emotet could be used by other more dangerous threats like the Conti or Ryuk ransomware families as an entry point.
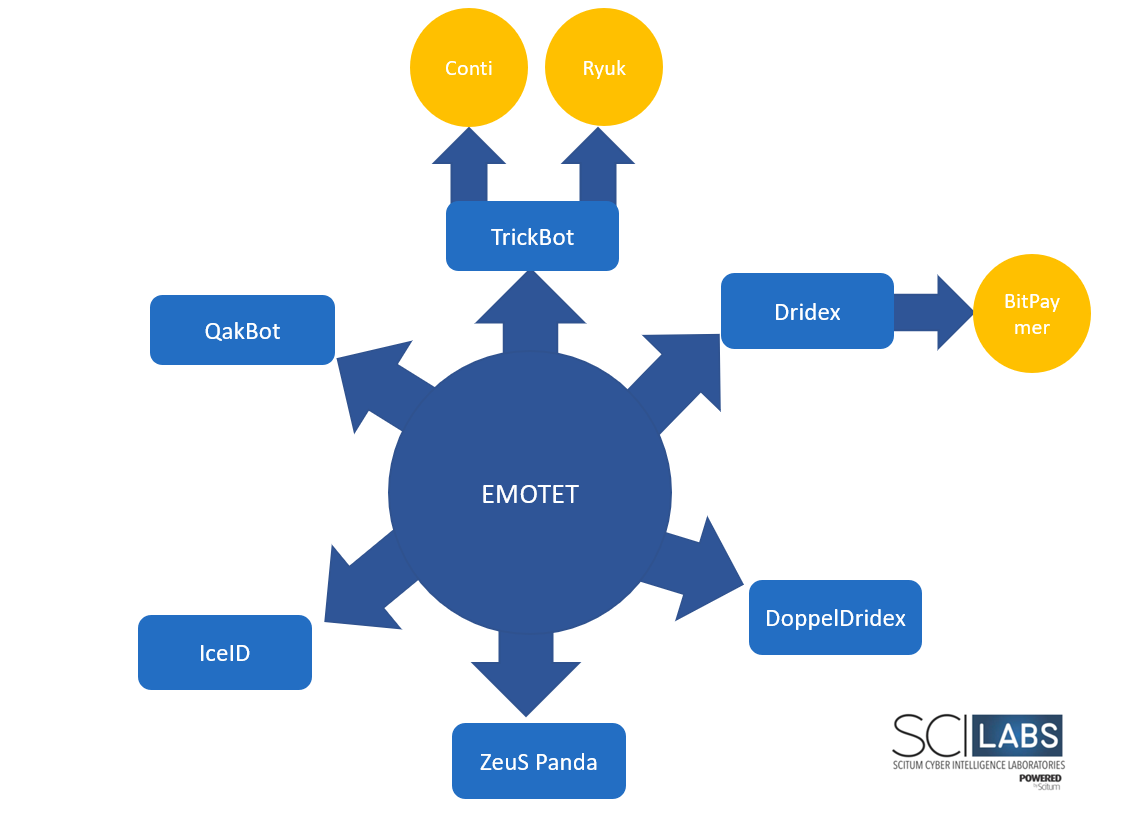
Figure 9 – Emotet as a base in the infection chain
Conclusion
Emotet is a dangerous threat due to its modularity and extensive distributed infrastructure. The campaigns used to distribute this threat and its improvements in the distribution chain are designed to evade the most significant number of security solutions, as we can see by using techniques such as the execution of PowerShell commands through direct access files “.lnk”.
Based on our telemetry, SCILabs believes that Emotet will continue to be very active, especially in LATAM, in many cases due to the lack of awareness campaigns in organizations in the region and the lack of implementation of security solutions that are not only based on signatures for the timely detection of this type of threat but also behavior patterns based on machine learning functions.
Another point to consider is the trust generated between email accounts to distribute the trojan because Emotet can steal victims’ email accounts (Business Email Compromise, BEC) and use them to forward malware from the compromised account to the victim’s contacts.
Although Emotet is a well-known and historically analyzed threat, organizations must be aware of this type of threat and have the necessary measures in places, such as policies on the correct use of email, regular awareness campaigns, security solutions such as EDR in all the organization’s EndPoints and constant threat hunting activities to identify malware attacks on time and minimize the risk of more dangerous attacks through Emotet.
Recommendations
- Change the passwords of email accounts you suspect have been used to send phishing emails.
- If possible, block emails with password-protected .zip file attachments in your anti-spam solution and only enable the exceptions as required.
- If you believe Emotet has victimized you, use the EmoCheck[24] application to check activity on Windows systems as a supplemental aid.
- Check if your email or domain is in the Emotet spam database using the HaveIBeenEmotet[25]
- Enable multi-factor authentication for your personal and corporate email accounts and operational applications that allow it.
- Avoid using the same password for different websites or email providers; use strong passwords and update them regularly.
- Do so in a password management application when storing passwords, obtaining them from an official source.
- Carefully review the sender of the emails you receive to validate that it is not a spoofing of the name or email address of the sender; when in doubt, carry out a second validation, preferably by calling the sender by phone.
- When you need to access an application, page, or service, always do so from the organization’s official page or by entering the corresponding web address yourself.
- If the email contains a link attached, verify that the web address is legitimate to the related service. Generally, official pages begin with “HTTPS://,” which indicates that the transmission of information is secure. By clicking on the security locks that are usually located on the left side of the Internet browser’s address bar, you can check the validity of the digital certificate and obtain information about the identity of the site you are accessing.
- Do not download or open files from untrusted or official sources. Those files may contain malware or other harmful software that could allow an attacker to access your computer and any information you store or enter on it.
- Keep the software on your devices up to date. Install security updates for your operating system and all the applications you use, especially for your antivirus products or EDR solutions, your web browser, and your email client.
- Do not reply when you receive suspicious emails from unknown senders asking for personal or financial information, do not reply.
- Stay current on the most common techniques attackers use to distribute malware.
- Constantly run awareness campaigns at all levels of the organization about the social engineering techniques used by cybercriminals to distribute malware.
- Establish a process within your organization that allows all operational staff to know how and with whom to directly and immediately report any suspicious email or derived malicious activity.
IoCs
HXXP://FARSCHID.DE/VERKAUFSBERATER_SERVICE/OZRW36A2Y1CH2CLUZY/ HXXP://77HOMOLOG.COM.BR/DEV-JEALVES/GP55WBYNXNP6/ HXXP://GEOWF.GE/TEMPLATES/PJREA3IU3WG/ HXXP://H63402X4.BEGET.TECH/BIN/WL0ENIE3BHELXV6V/ HXXP://ECOARCH.COM.TW/CGI-BIN/E/
HXXPS://GALAXY-CATERING.COM.VN/GALXY/FG1VVHLYJ/
FARSCHID[.]DE
77HOMOLOG[.]COM[.]BR
GEOWF[.]GE
H63402X4[.]BEGET[.]TECH ECOARCH[.]COM[.]TW
GALAXY-CATERING[.]COM[.]VN
44CBB81D7EA274183675EBFEEC5498C244B99EB1
784C4D39CA9893630836A43310249EA2DF4E137A
502BE9F4649606E60E9C39D432891E83E077798C
3A4B4FE9F7A8C271A43230531A6FBD6ACDAD6CBF
3D2A06E24CD754FC6BB8F3CEF7360464F5DA259C
D037D66B881112A47EB88A7A3E843EFBAF9D2456
C39C0AB3E3818E745BE13B0D9448F1E58CA8299B
15980A3056105F71A6D8B8EEBDF2F7BA0E0CDD55
B677DF2DCE4A674FA63188A63E11F7831222A326
References
[1] https://success.trendmicro.com/dcx/s/solution/1118391-malware-awareness-emotet-resurgence
[2] https://www.cybereason.com/blog/research/one-two-punch-emotet-trickbot-and-ryuk-steal-then-ransom-data
[3] https://www.bleepingcomputer.com/news/security/emotet-botnet-comeback-orchestrated-by-conti-ransomware-gang/
[4] https://www.cybereason.com/blog/research/triple-threat-emotet-deploys-trickbot-to-steal-data-spread-ryuk-ransomware
[5] https://www.bleepingcomputer.com/news/security/emotet-botnet-is-now-heavily-spreading-qakbot-malware/
[6] https://nakedsecurity.sophos.com/2017/08/10/watch-out-for-emotet-the-trojan-thats-nearly-a-worm/
[7] https://duo.com/decipher/emotet-shifts-gears-drops-cobalt-strikedirectly
[8] https://malpedia.caad.fkie.fraunhofer.de/actor/mummy_spider
[9] https://www.trendmicro.com/vinfo/us/security/definition/in-the-wild
[10] https://www.bleepingcomputer.com/news/security/emotet-trojan-evolves-since-being-reawakend-here-is-what-we-know/
[11] https://blogs.vmware.com/security/2022/03/emotet-c2-configuration-extraction-and-analysis.html
[12] https://intel471.com/blog/emotet-returns-december-2021
[13] https://blogs.vmware.com/security/2022/03/emotet-c2-configuration-extraction-and-analysis.html
[14] https://jryancanty.medium.com/understanding-cryptography-with-rsa-74721350331f
[15] https://medium.com/swlh/an-introduction-to-the-advanced-encryption-standard-aes-d7b72cc8de97
[16] https://medium.com/swlh/understanding-ec-diffie-hellman-9c07be338d4a
[17] https://medium.com/coinmonks/ecdsa-the-art-of-cryptographic-signatures-d0bb254c8b96
[18] https://www.bleepingcomputer.com/news/security/emotet-trojan-evolves-since-being-reawakend-here-is-what-we-know/
[19] https://blogs.vmware.com/security/2022/03/emotet-c2-configuration-extraction-and-analysis.html
[20] https://www.bleepingcomputer.com/news/security/emotet-malware-now-installs-via-powershell-in-windows-shortcut-files/
[21] https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-ta542-banker-malware-distribution-service
[22] https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/evolution-emotet-trojan-distributor
[23] https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-ta542-banker-malware-distribution-service
[24] https://github.com/JPCERTCC/EmoCheck
[25] https://www.haveibeenemotet.com/
