Cyber Threat Profile Red WinterDog

Overview
The following post describes the modus operandi analysis of a threat actor named Red WinterDog by SCILabs as, which operates the BlackDog and BlackBelen malware families.
Red WinterDog targets users of all types in Mexico, including employees of organizations intending to steal victims’ banking and personal information, and business email accounts, using web browser malicious extensions designed primarily for Google Chrome and Edge. The initial access vectors are mainly malvertising campaigns in search engines such as DuckDuck Go and Bing, in addition to possible phishing campaigns, impersonating governmental organizations in Mexico such as the Registro Nacional de Población (RENAPO) and the Servicio de Administración Tributaria (SAT).
Our research shows that Red WinterDog has been operating predominantly in Mexico since June 2022, making constant updates to its TTPs to evade security solutions or hinder analysis by cyber threat researchers. SCILabs detected the last activity of this adversary during May 2023.
Geographical region of operation
As a result of the open-source intelligence process and the analysis of the malicious artifacts used by this threat group, SCILabs determined with a high level of confidence that the primary country of operation is Mexico.
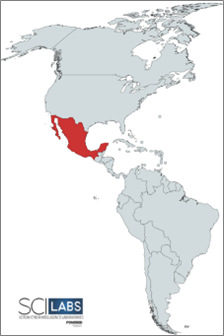
Figure 1. Red WinterDog activity map
Based on our research, we present a timeline of Red WinterDog’s most relevant activities from June 2022 to January 2023.
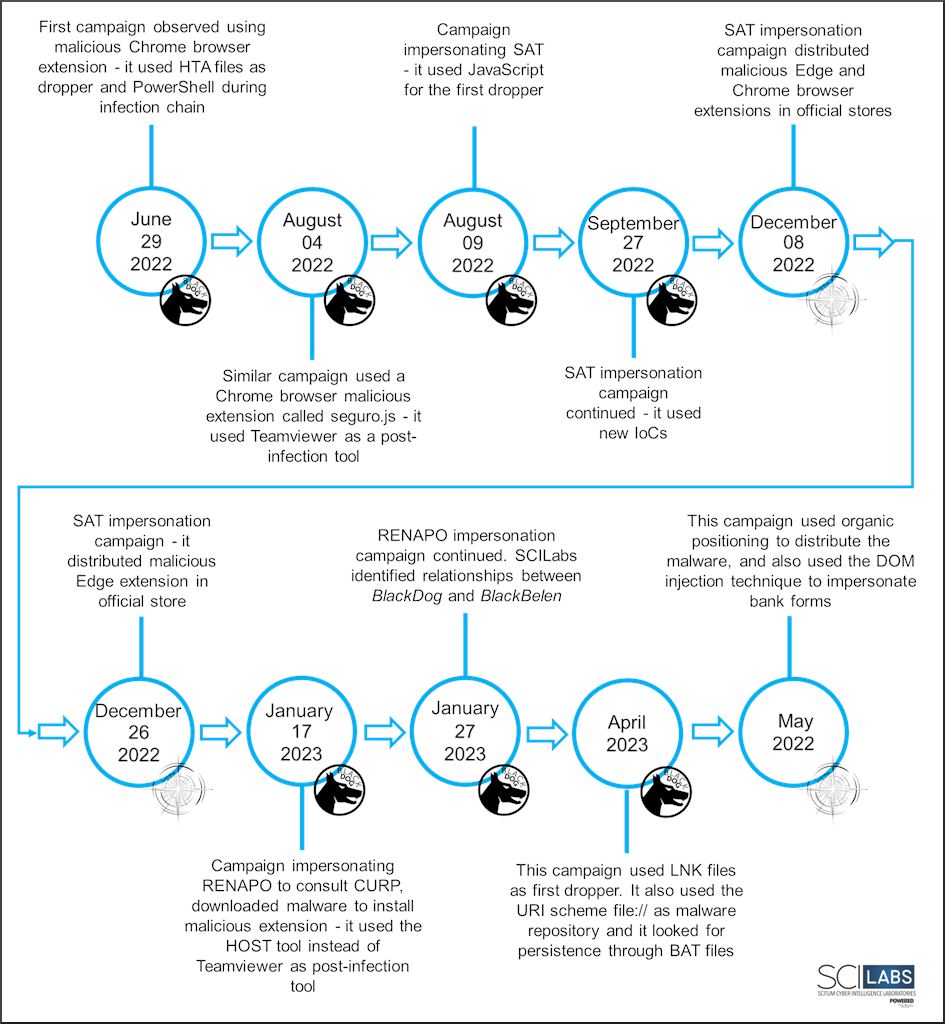
Figure 2. Timelne of Red WinterDog campaigns
About the victims
During constant monitoring of the region, SCILabs identified that Red WinterDog’s main target is end users in Mexico; however, malvertising campaigns can affect the reputation of some government institutions and financial entities due to the adversary’s brand impersonation.
Threat group’s operating model
Red WinterDog distributes its malware using malvertising campaigns on search engines such as DuckDuck Go and Bing, as well as possible phishing campaigns impersonating government institutions in Mexico. Based on a trends analysis conducted through open sources, we observed that the words CURP and SAT are two of the most searched words by users in Mexico, along with other words such as CFE or “Pasaporte”. It is likely that adversaries also perform this type of analysis to determine which organizations they are going to impersonate in their malicious advertising campaigns and thus reach the largest number of potential victims.
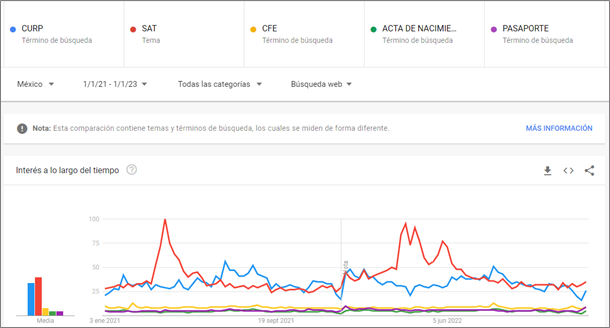
Figure 3. Comparative of different search parameters in Mexico (Google Trends)
Malware families operated by Red WinterDog
BlackDog and BlackBelen are the two trojans operated by the threat actor and they have particular characteristics, which are described in general terms below:
BlackDog:
- It is installed via malicious JavaScript and HTML files.
- It can be distributed through emails with pretexts related to supposed transfers, SAT add-ons, CURP, Google Drive or through malicious campaigns in search engines such as Bing and DuckDuck Go.
- If the victim executes a malicious file coming from the Internet or downloaded from the email, a malicious extension is installed in the Chrome browser, often called “seguridad” by cybercriminals.
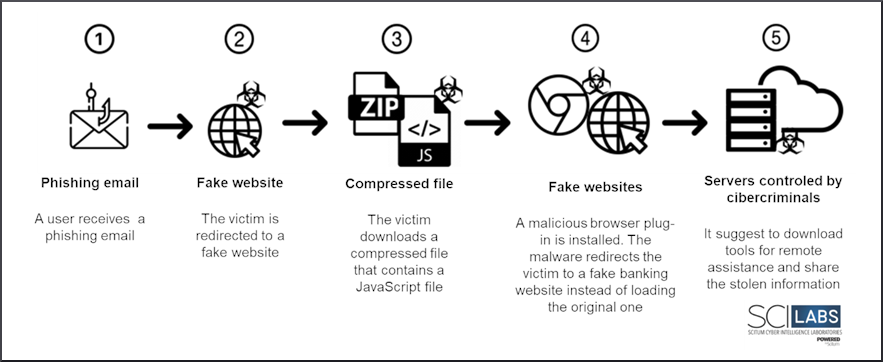
Figure 4. Attack flow of BlackDog
BlackBelen
- It is installed directly from the official Google Chrome or Edge store, making it particularly dangerous.
- It can be distributed through emails with pretexts related to supposed transfers, SAT add-ons, CURP, Google Drive or through malicious campaigns in search engines such as Bing and DuckDuck Go.
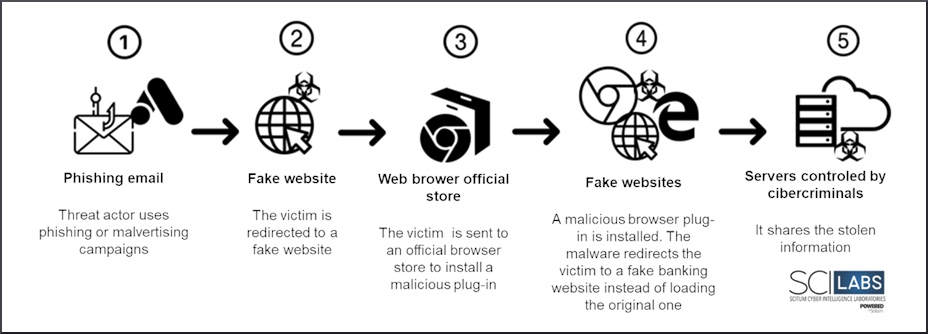
Figure 5. Attack flow of BlackBelen

Figure 6. SAT impersonating malvertising campaign
Finally, if a user accesses a banking site, they will be redirected to a fake site or JavaScript and HTML code will be injected into the official page to impersonate banking forms and steal their information without the victim being aware of it.
Diamon model
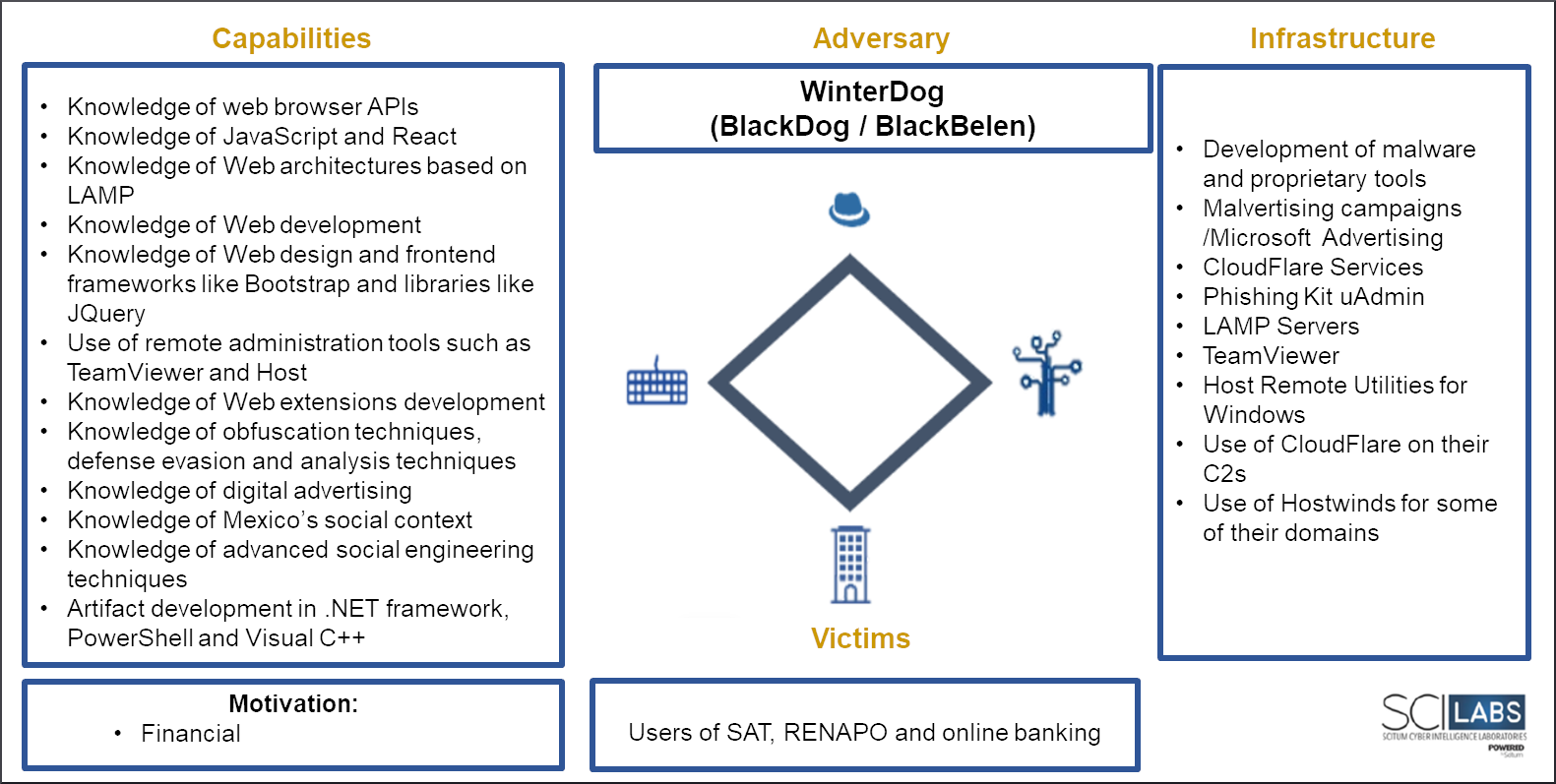
Figure 7. Red WinterDog´s Diamond model
MITRE ATT&CK ® based profiling
The following matrix of TTPs based on the MITRE PRE-ATT&CK Framework was obtained from the analysis of different BlackDog and BlackBelen campaigns.
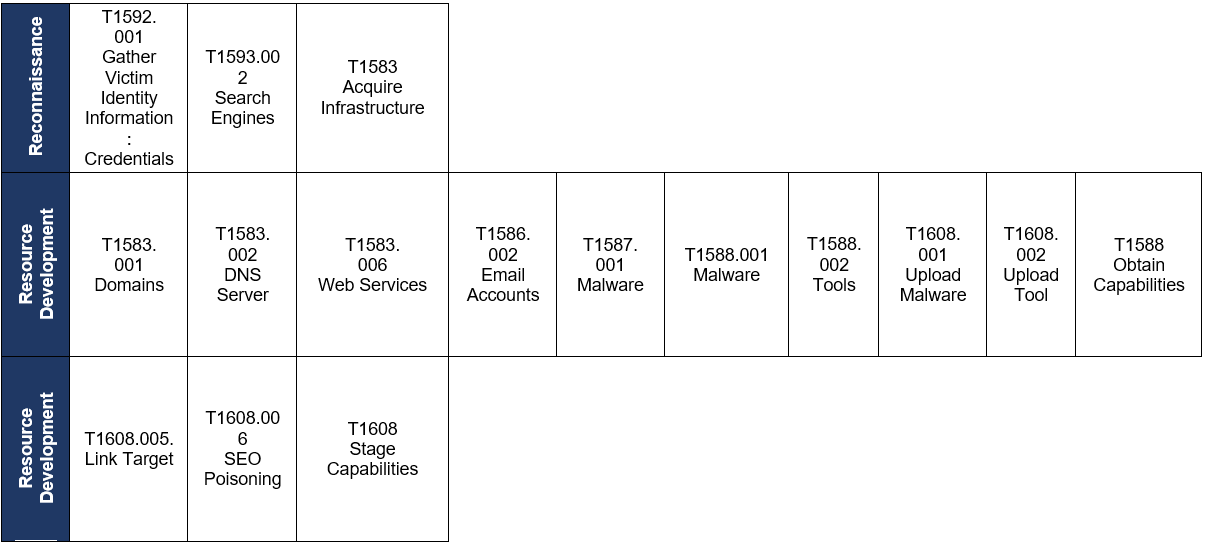
Table 1. PRE-ATT&CK Matrix
The following matrix of TTPs based on the MITRE Framework was obtained from the analysis of different BlackDog and BlackBelen campaigns.
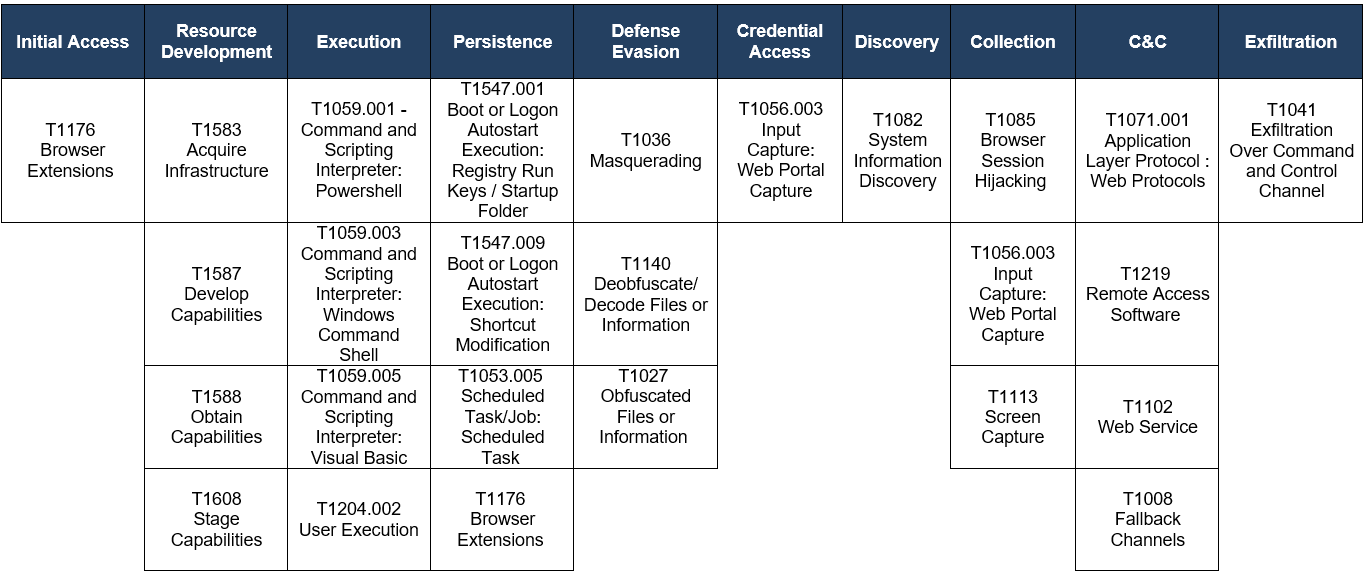
Table 2. MITRE ATT&CK Matrix
Conclusions
The Red WinterDog threat group is constantly modifying its malicious artifacts and the techniques used in its attacks, always with the objective of stealing banking information from users in Mexico, using one of the two malware families identified so far (BlackDog and BlackBelen), with the main technique being the use of Man in The Browser.
The main characteristic of this threat is to use malicious web browser extensions for the most popular ones, and distribute them through official Google Chrome and Edge stores, along with the analysis of trends from government agencies, to design their malvertising campaigns and the phishing sites used as initial vector. The ideal victims of Red WinterDog are those users and organizations that do not have EndPoint security tools to identify the installation of malicious browser add-ons or are not aware of the new techniques used in the threat landscape affecting Latin America.
SCILabs continues to monitor the activity of this cybercriminal group and provide IOCs to strengthen the security of our customers.
Recommendations
- Try to enter the addresses of the pages you want to visit directly in the address bar and not through search engine results.
- Conduct awareness campaigns about malicious advertising campaigns used to distribute this malware.
- Have strict policies regarding the use and installation of add-ons or extensions in the organization’s web browsers.
- Perform constant monitoring for malicious add-ons or extensions in your organization’s browsers that are not authorized.
- Look for Chrome browser shortcuts that use the –load-extension parameter to execute suspicious, malicious, or unauthorized code or extensions in your organization.
- Verify the legitimacy, source, and developer of extensions you authorize in your organization, even if they are in the official browser stores.
- Add the indicators of compromise reflected in this research to your security solutions.
IoCs
Hash SHA256
9A04E1EAA7A98677014D1379D0B972588A98EE0FF62BB70EE97AE26798A0DA92 C408596DF55AD041496D306D2F67494588B1780235356B74F616DAF1669E77C1 06EF9E6803F74A113146E41D988F74A4B83A35A86FF5CC7A991F1DD4C1A2C0E7 BFF33D296226786E00935EDFFD5443E3031B09C12BA7CCFE0647BAD4771B437A B17A1DD4F287AA069A74739AD71B2D57A6F45E7DEB26C7167A4CFD55E9B20D0C 97EE7591B48B97F6EC58424078D16DD152D5D09A1FE8BFD9554DF12B444191A0
Domains
PORTALDECONEXIONSEGURA[.]COM COMPLEMENTODESEGURIDADMX[.]COM HERRAMIENTASNET.COM[.]MX SRLTPZMX[.]COM HXXPS[:]//FACTURAMX[.]CLUB HXXPS[:]//FACTURACIONMEXICO[.]NET HCBCL9[.]BUZZ
URLs
HXXPS[:]//DRIVE[.]GOOGLE[.]COM/UC?EXPORT=DOWNLOAD&ID=1U830KFXKJB9XUCTMEGBDCTAPHEVSTENZ
Paths
%LOCALAPPDATA%\SEGURO.JS %APPDATA%\MICROSOFT\WINDOWS\START MENU\PROGRAMS\STARTUP\ %LOCALAPPDATA%/\MICROSOFT\WINDOWS\INETCACHE\IE\
